Validation Rule
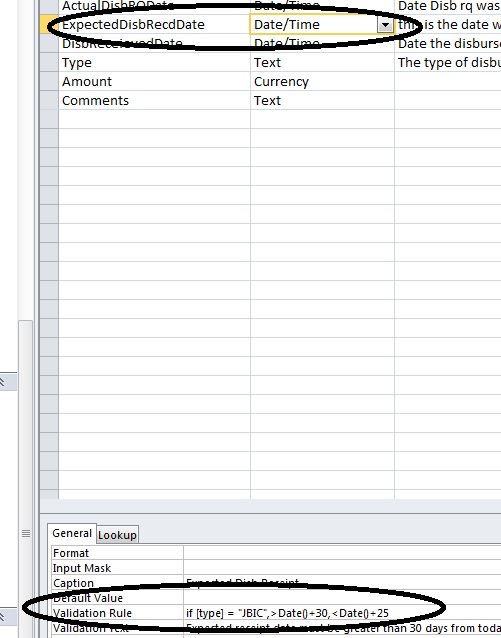
Experts, in a validation rule, can I refer to field within the table? I am referring to [Type] within the field [ExpectedDisbRecdDate]. Not sure if a rule like this is better placed in a form.
for example:
if [type] = "JBIC",>Date()+30,<Date()+
the error I get is "enclose text data in quotes"
thanks
for example:
if [type] = "JBIC",>Date()+30,<Date()+
the error I get is "enclose text data in quotes"
thanks

if you are using A2010 or greater, data macro may work for you..
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
thank you. I will try the validation rule at the form level.
try something like this
IIf([type]="JBIC",>Date()+