Network Architecture
--
Questions
--
Followers
Top Experts
(See below for simplistic overview to what I believe we need to do)
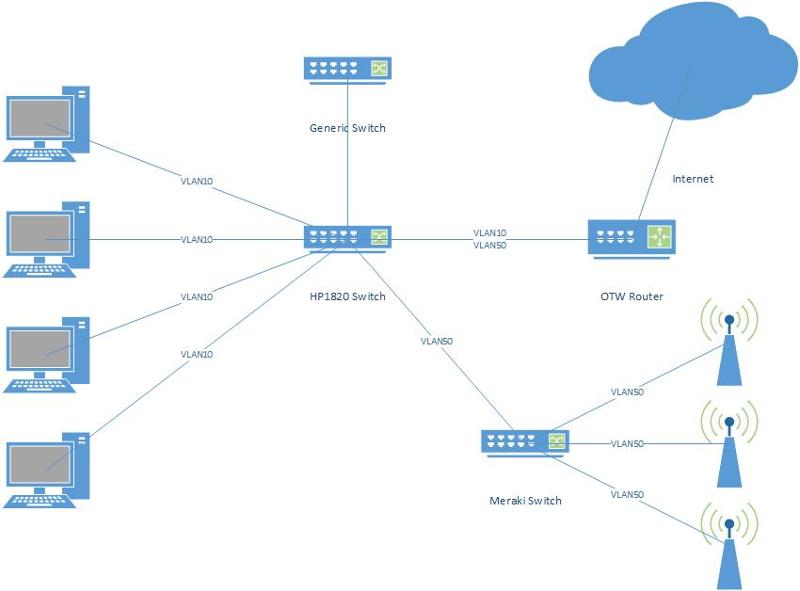
I know I need to tag the port that the wireless switch uplinks to the HP1820 switch and I'll need to tag the uplink port to the router for VLAN 10 and 50
however, I am not sure what I should do for the other ports on the switch. Should I leave them untagged including the uplink to the generic switch not capable of VLANing?
I also assume that I'll need to put some sort of restriction on the router to prevent routing between the VLAN's
Thanks
Zero AI Policy
We believe in human intelligence. Our moderation policy strictly prohibits the use of LLM content in our Q&A threads.
Should I tag the uplink to the generic switch as VLAN10 or untag in case the switch doesn't recognise VLAN packet headers???






EARN REWARDS FOR ASKING, ANSWERING, AND MORE.
Earn free swag for participating on the platform.
Network Architecture
--
Questions
--
Followers
Top Experts
Network design and methodology, also known as network architecture, is the design of a communication network. It is a framework for the specification of a network's physical components and their functional organization and configuration, its operational principles and procedures, as well as data formats used in its operation. In telecommunication, the specification of a network architecture may also include a detailed description of products and services delivered via a communications network, as well as detailed rate and billing structures under which services are compensated.