how to identify first time user and a registered user
I'm working on a database design for a credit card processing web application. We are using single sign-on to authenticate users, so the username and password will not be stored in the database schema. What I'm trying to determine right now is when a user logs in if they are a first-time user or if they are a registered user. I have a contact table and I was thinking I could just add a new column to the contact table "registeredUser" that is a bit datatype. But, I'm wondering if this is limiting and if there was a better design choice. Please see the attached database diagram.
Thanks for any help from any database experts out there.
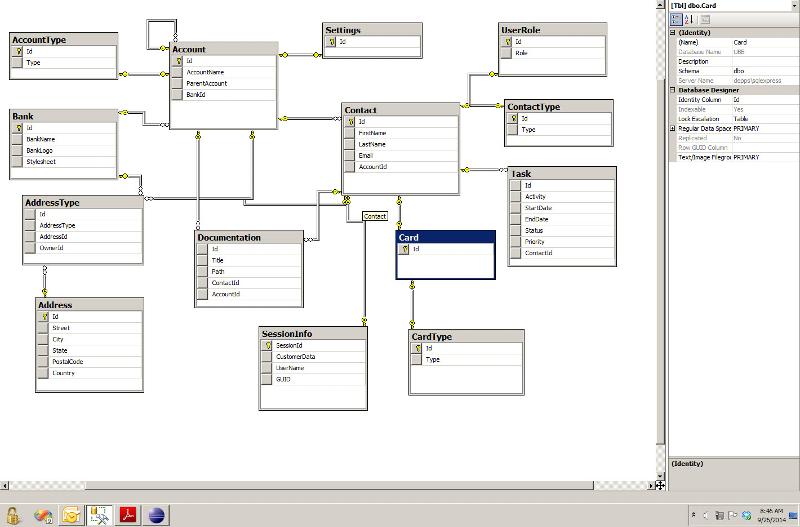
Thanks for any help from any database experts out there.

How can a user log in if isn't registered?
ASKER
They can login thru single sign-in, but they won't have specific permissions in the application until after they have gone thru the first time registration process. Perhaps using the term register is misleading. Basically, I need to differentiate between a first time user and a user that has gone thru the first-time registration process in the application. Does that help explain?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.