ipcop firewall
so I have setup an old pc with ipcop and that went fine, however, this has exposed my poor understanding of firewall configuration which is the whole reason I setup ipcop in the first place. My setup is, the red interface ( which I think is the interface that will interact with the "outside world" - maybe it can be called the WAN ) has an IP address of 192.168.0.80. My green interface ( the internal, or LAN interface ) has an address of 192.168.0.75. Initially, just one of my computers will be using the firewall, until I work out the bugs, so this pc has an address of 192.168.0.100. My cable modem, aka my gateway is 192.168.0.1. Also, I have disabled the windows firewall.
So, I'm pretty sure the proper setup would be to have the firewall between my computer and the gateway.
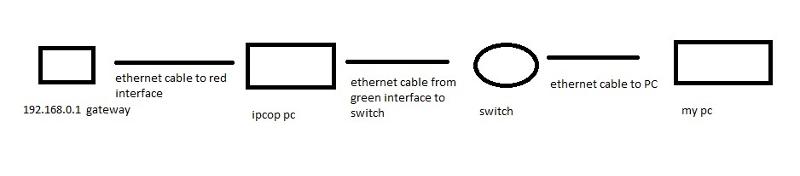
sorry for the crude drawing, all i have is MS paint. so that is my physical setup.
when I try to ping 192.168.0.80, 192.168.0.1 or 192.168.0.75, I cant get a response. I can't ping my gateway, so sure enough, i can't get out to the web. So possibly the ipcop firewall initially doesn't allow any traffic? which might explain why pings weren't working either. of course since I can't ping my red or green interface i can't get to the web interface to poke some holes in my firewall.
so I tried plugging the red, green, cable modem, and pc into the same switch, and then of course, i ping everything and get out to the web, and can get to the ipcop web interface to open the holes i need - presumably port 80 at the least.
I go to the web interface and I'm not sure how to open port 80. would it be just port forwarding? or is it a firewall rule to allow traffic from the red interface for port 80 to go to the green interface? Also, I tried creating a firewall rule, but i don't even know if i did it right. for instance would i allow traffic from the red interface coming from 192.168.0.1 to the green interface 192.168.0.75?
So, I'm pretty sure the proper setup would be to have the firewall between my computer and the gateway.

sorry for the crude drawing, all i have is MS paint. so that is my physical setup.
when I try to ping 192.168.0.80, 192.168.0.1 or 192.168.0.75, I cant get a response. I can't ping my gateway, so sure enough, i can't get out to the web. So possibly the ipcop firewall initially doesn't allow any traffic? which might explain why pings weren't working either. of course since I can't ping my red or green interface i can't get to the web interface to poke some holes in my firewall.
so I tried plugging the red, green, cable modem, and pc into the same switch, and then of course, i ping everything and get out to the web, and can get to the ipcop web interface to open the holes i need - presumably port 80 at the least.
I go to the web interface and I'm not sure how to open port 80. would it be just port forwarding? or is it a firewall rule to allow traffic from the red interface for port 80 to go to the green interface? Also, I tried creating a firewall rule, but i don't even know if i did it right. for instance would i allow traffic from the red interface coming from 192.168.0.1 to the green interface 192.168.0.75?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Your internal and external adapters are on the same subnet and that'll cause problems. The firewall will have no means to properly route traffic. Some firewalls offer transparent bridging between both network interfaces, but IPCop was not one of them last I checked. Even if they have added that feature, it'd be implemented in such a way that the two interfaces would not be configured in the way you describe. You'll really need to rethink your topology and address scheme.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
ok, i think the routing thing is correct, so i changed my red to 192.168.10.80 with a subnet of 255.255.0.0 ( I know - that probably isn't the correct subnet for that ip - I just wanted to make sure I wasn't in the same subnet ) and my green address is still 192.168.0.75. also on my ipcop machine I changed the gateway to 192.168.10.80 and i am using my isp's dns servers of 75.75.75.75. the ip setup on my computer is 192.168.0.100 subnet 255.255.255.0 gateway 192.168.0.75 dns 75.75.75.75
the rule i have in the firewall is outgoing - green - source 192.168.0.100 ( which is the ip of my computer ) red any:http - I am using the web interface, I have googled this and it seems most people are manually typing in stuff - but I know I'm not ready for that.
now in the firewall logs, there are a ton of
green reject lan-1 udp 192.168.0.100 port 137
and I can't get to any websites
could it be my firewall rule? or do i still have something wrong with the gateways or something like that?
the rule i have in the firewall is outgoing - green - source 192.168.0.100 ( which is the ip of my computer ) red any:http - I am using the web interface, I have googled this and it seems most people are manually typing in stuff - but I know I'm not ready for that.
now in the firewall logs, there are a ton of
green reject lan-1 udp 192.168.0.100 port 137
and I can't get to any websites
could it be my firewall rule? or do i still have something wrong with the gateways or something like that?
A subnet mask is not the same thing as a subnet. By defining the mask as 255.255.0.0, you've made the firewall think any 192.168.x.x is on the same adapter. So 192.168.0.x and 192.168.10.x *are* on the same subnet now. Which will still break routing. This isn't firewall knowledge. This is TCP/IP knowledge.
ASKER
ok, thank you for the description. but since i'm obviously not get the difference between subnet mask and a subnet. could you enlighten me on what I should do?
do you mean that my red address needs to be something completely different, say 172.16.10.1?
also, would there be a good description of the differences between subnet mask and the subnet? I ask these questions to learn things i don't know.
I've been able to fix networking issues, but haven't understood this for a long time, so I am actually very interest in what you are saying.
do you mean that my red address needs to be something completely different, say 172.16.10.1?
also, would there be a good description of the differences between subnet mask and the subnet? I ask these questions to learn things i don't know.
I've been able to fix networking issues, but haven't understood this for a long time, so I am actually very interest in what you are saying.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
so, 192.168.0.x is a subnet, the 192.168.0 is the network and x is the host. and 192.168.10 would be a different subnet? I ask because i have some knowledge of this, but I guess I have never seen it described were because of the 3rd octet being different, it is a different subnet. I honestly didn't know that, but have seen the thing where like i said, 192.168.0 is the network portion. I think i saw that in subnetting.
it's crazy to me to think that i was taught some subnetting, but not this. I hope this doesn't sound like I'm trying to challenge what you are saying, because i'm not. It's more that even though i have been exposed to some networking knowledge, somehow i missed this. but it seems like a very important point. I am actually very happy you said this, because it exposes a large gap of knowledge i have, in which, had i know this, i think the networking "picture" would have been clearer for me.
well, thank you for what you said. i will try the red interface as 192.168.10.80, and the green as 192.168.0.75
it's crazy to me to think that i was taught some subnetting, but not this. I hope this doesn't sound like I'm trying to challenge what you are saying, because i'm not. It's more that even though i have been exposed to some networking knowledge, somehow i missed this. but it seems like a very important point. I am actually very happy you said this, because it exposes a large gap of knowledge i have, in which, had i know this, i think the networking "picture" would have been clearer for me.
well, thank you for what you said. i will try the red interface as 192.168.10.80, and the green as 192.168.0.75
Subnet masks define where the subnet vs the host ID lies. With a mask of 255.255.255.0, the third octet is indeed a part of the subnet, so when it changes, it is a different subnet. With 255.255.0.0, it is part of the host ID, so changing it does *not* change the subnet. And while octets server as common and convenient boundaries, it isn't required. A subnet mask of 255.255.248.0 would break the third octet into small groups, where a few sequential numbers are in the same subnet, but not the entire octet.
ASKER
THANK YOU!! with knowledge comes power! that gaping hole in my networking knowledge was definitely a problem. after thinking about what you said. i looked at the ipcop IP setup. what I needed to do was put the red interface on the same subnet as the gateway. I was missing that before, so, on the ipcop machine, the red interface is 192.168.0.80 subnet 255.255.255.0, and the gateway is 192.168.0.1 ( 192.168.0.1is also the address of my cable modem - internally ) and the green interface is 192.168.10.75 subnet 255.255.255.0. then I changed my computer to 192.168.10.100 subnet 255.255.255.0. with a gateway of 192.168.10.75
I am NOW able to get out to the internet.
I'm trying not to beat a dead horse, but I can't believe i haven't seen this before, despite working on networks for a long time! I would clarify, that when i say working on networks, i was doing the standard stuff of pinging gateways to make sure a computer could reach the gateway, then pinging an internet address such as www.yahoo.com, to make sure dns worked. I obviously was only scratching the surface.
I am NOW able to get out to the internet.
I'm trying not to beat a dead horse, but I can't believe i haven't seen this before, despite working on networks for a long time! I would clarify, that when i say working on networks, i was doing the standard stuff of pinging gateways to make sure a computer could reach the gateway, then pinging an internet address such as www.yahoo.com, to make sure dns worked. I obviously was only scratching the surface.
ASKER
another oldie but a goodie is, "it's always something"
So, I'm getting out to the internet, and I know I'm going through ipcop because the green interface is the my gateway. out of curiosity i removed all firewall rules, and i'm still getting out to the internet. I'm guessing this means that by default ipcop allows port 80? if so, that is pretty disappointing. I thought the best practice was to not allow anything by default, and open ports as needed.
I'm confused again though, because wouldn't there be somewhere in the firewall rules about allowing http traffic, because I didn't see anything. I don't think i have anything in the port forwarding either, but i thought port forwarding was allowing request into the network. So for instance, a request from the "outside world" for port 80 to a computer in my network.
I'm pretty sure something is being blocked by ipcop though, because at work we use Citrix to remotely access our files and stuff like that. And before ipcop, i could use Citrix without a problem. Now that ipcop is running, I can't access Citrix. So, I'll find what holes I need to open for Citrix, but I'm just surprised that internet traffic is working.
So, I'm getting out to the internet, and I know I'm going through ipcop because the green interface is the my gateway. out of curiosity i removed all firewall rules, and i'm still getting out to the internet. I'm guessing this means that by default ipcop allows port 80? if so, that is pretty disappointing. I thought the best practice was to not allow anything by default, and open ports as needed.
I'm confused again though, because wouldn't there be somewhere in the firewall rules about allowing http traffic, because I didn't see anything. I don't think i have anything in the port forwarding either, but i thought port forwarding was allowing request into the network. So for instance, a request from the "outside world" for port 80 to a computer in my network.
I'm pretty sure something is being blocked by ipcop though, because at work we use Citrix to remotely access our files and stuff like that. And before ipcop, i could use Citrix without a problem. Now that ipcop is running, I can't access Citrix. So, I'll find what holes I need to open for Citrix, but I'm just surprised that internet traffic is working.
Ipcop's default is outbound traffic is allowed unless specifically configured otherwise, as documented here.
http://www.ipcop.org/2.0.0/en/admin/html/firewall-traffic.html
http://www.ipcop.org/2.0.0/en/admin/html/firewall-traffic.html
ASKER
thank you for the help. at this point i have to play with the firewall rules, but it's running now which was what i was trying to do.