Certificate Authority "CA"
I want to be able to do the following, I have never setup a "CA" and would like info as to the best way of doing it.
I have setup just to practice on a VM Srv the CA role, and I have setup templates ect...
I want to be able to do the following.
I have (2) VLans on the network, one for the staff users and one for the tech users.
Both VLans can talk to each other if thy need .
The tech users are 12 workstations that are used to program cell phones.
Our in house programers will be creating programs for the tech users to be able to use on there workstations.
He is concern with one of the tech users being able to download the program and take it off site and using it.
Here is what I would like to do.
when the programer creates a program I like to be able to encrypt it with certificate, at the same time the tech user will have to be able to go into the share folder and drag it to there desktop.
In short, I want to be able to encrypt a file, folder or program and allow the tech user to use it when still protecting it in the even that it is taken off site.
What would be the best way to accomplish this?
I have setup just to practice on a VM Srv the CA role, and I have setup templates ect...
I want to be able to do the following.
I have (2) VLans on the network, one for the staff users and one for the tech users.
Both VLans can talk to each other if thy need .
The tech users are 12 workstations that are used to program cell phones.
Our in house programers will be creating programs for the tech users to be able to use on there workstations.
He is concern with one of the tech users being able to download the program and take it off site and using it.
Here is what I would like to do.
when the programer creates a program I like to be able to encrypt it with certificate, at the same time the tech user will have to be able to go into the share folder and drag it to there desktop.
In short, I want to be able to encrypt a file, folder or program and allow the tech user to use it when still protecting it in the even that it is taken off site.
What would be the best way to accomplish this?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Either running the program through remote app / remote desktop , (remote app preferred) or for you to implement ADRMS (Active directory Rights Management Services). Your idea is way too cumbersome as the program will have to be in 2 parts (check for a valid key and then decrypt the main program) and then execute the main program.. once the main program is decrypted it is open to being emailed or sneakernetter out..
ASKER
bboa...
i want the teh users to be able to open the file while at the office on there computer, but not to be to able to put the file on a USB drive and open at home or on some other computer.
i want the teh users to be able to open the file while at the office on there computer, but not to be to able to put the file on a USB drive and open at home or on some other computer.
ASKER
david,
i see what you mean
i see what you mean
Crazy glue fixes the sneaker-net problem permanently. With Group policy you can disable USB drives completely, disallow writing to removable media.. Stopping the user from emailing it home is another issue.. or say uploading it to mozy/onedrive is another item.. ADRMS if the user only has READ/Execute permittions while physically connected to the domain the file cannot be copied AT ALL (if so configured)
ASKER
David,
you make a good case...
I think I will include use it.
I still have a problem where if I encrypt a file with user "TDoe" I want user "KDoe" to be able to open it.
I tried exporting the private key from TDoe and importing it into KDoe, but KDoe still can't open TDoe file.
Why?
What I'm i doing worng?
you make a good case...
I think I will include use it.
I still have a problem where if I encrypt a file with user "TDoe" I want user "KDoe" to be able to open it.
I tried exporting the private key from TDoe and importing it into KDoe, but KDoe still can't open TDoe file.
Why?
What I'm i doing worng?
you have to encrypt it with EVERY USERS public key and your private key that you want to be able to access the file, each of these users must have a copy of your public key.
ASKER
David...
I setup the ADCA
I created a dummy user (jdoe)
I went into the templates, duplicated the users template, renamed it "MVP User".
I logged on with jode and requested a certificate.
So far everything is correct.
From the admin account I created a text file and encrypted it, when I try to add the user jdoe I can't (see snap shoots)
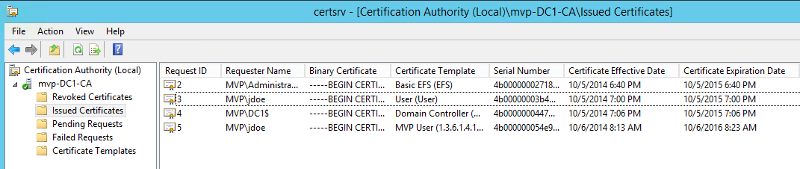
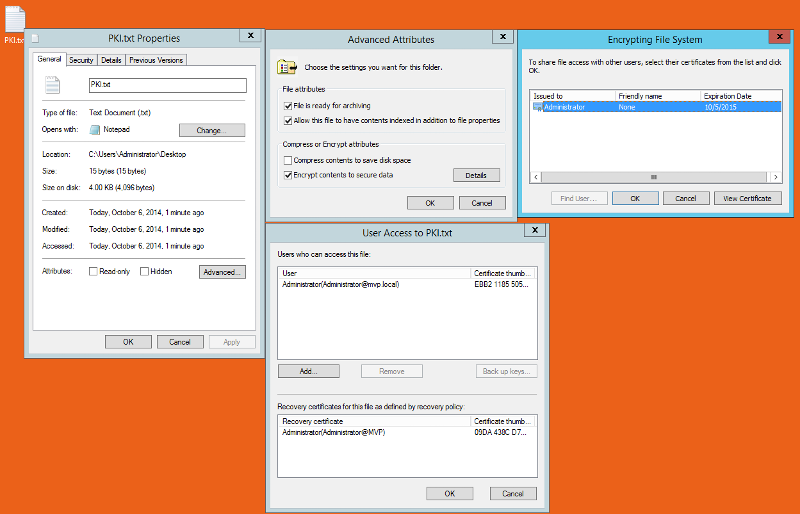
I'm I just doing something wrong? if so what is it?
Thanks
I setup the ADCA
I created a dummy user (jdoe)
I went into the templates, duplicated the users template, renamed it "MVP User".
I logged on with jode and requested a certificate.
So far everything is correct.
From the admin account I created a text file and encrypted it, when I try to add the user jdoe I can't (see snap shoots)


I'm I just doing something wrong? if so what is it?
Thanks
mvpjoe needs an efs basic certificate
good reading material
http://www.windowsecurity.com/articles-tutorials/windows_2003_security/Implementing-EFS-Windows-Server-2003-Domain.html
http://edmckinzie.wordpress.com/2008/07/15/efs-using-internal-pki-certificates-recovery-agent-certificates/
http://windowsitpro.com/security/leveraging-efs-your-pki
http://www.windowsecurity.com/articles-tutorials/windows_2003_security/Implementing-EFS-Windows-Server-2003-Domain.html
http://edmckinzie.wordpress.com/2008/07/15/efs-using-internal-pki-certificates-recovery-agent-certificates/
http://windowsitpro.com/security/leveraging-efs-your-pki
ASKER
David,
I understand what you are asking me to do, but if I may ask. the users temple says that they can encrypt...
Is it just that, only encrypt???
I will add the efs basic temp to the jdoe user.
Will let you know how it goes.
I understand what you are asking me to do, but if I may ask. the users temple says that they can encrypt...
Is it just that, only encrypt???
I will add the efs basic temp to the jdoe user.
Will let you know how it goes.
ASKER
David,
I added the basic efs cert to jdoe, I create a duplicate (MVP Basic EFS) went into jode account , requested the cert...
the problem that I'm having is when I'm in the admin account from which I encrypted the file I can't seem to be able to add jdoe....
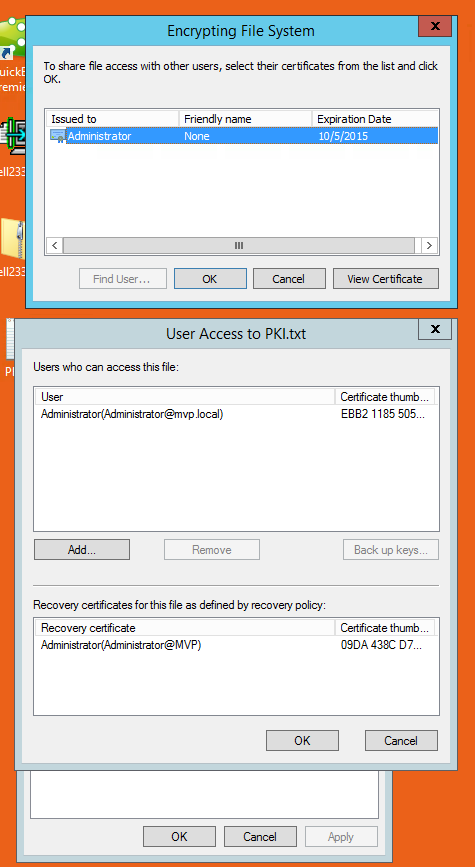
see how find user is grayed out....
from the user jdoe can view all his cert.
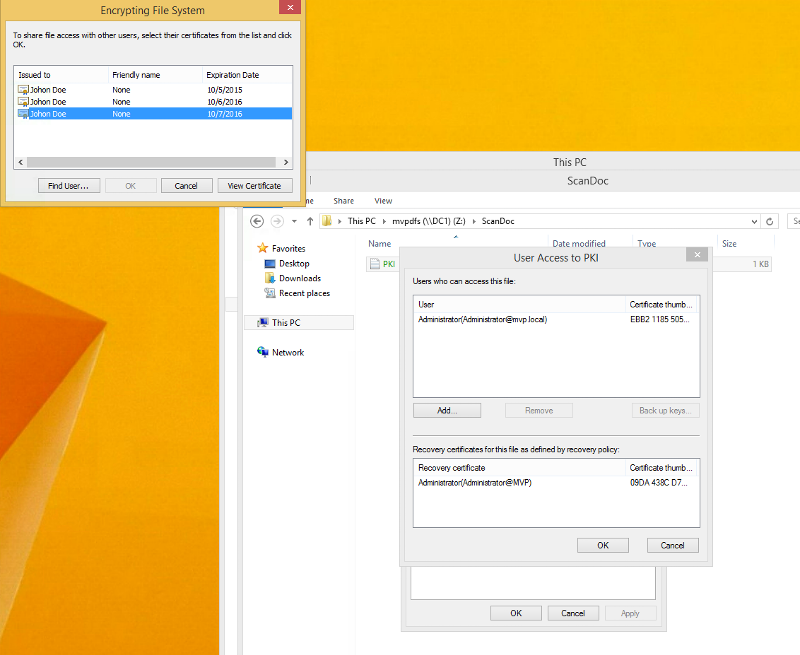
any idea what could be preventing me from adding the user jdoe to the encrypted file from the administrative account?
Thanks
I added the basic efs cert to jdoe, I create a duplicate (MVP Basic EFS) went into jode account , requested the cert...
the problem that I'm having is when I'm in the admin account from which I encrypted the file I can't seem to be able to add jdoe....

see how find user is grayed out....
from the user jdoe can view all his cert.

any idea what could be preventing me from adding the user jdoe to the encrypted file from the administrative account?
Thanks
you need to add their public key to your keystore, view certificate then import it.. you will only get the public part of the key.
it seems i just clarified your requirements and didn't follow up giving the solution. the points and grade should go to David please.
ASKER
David,
BBAO is correct, I inmy hurry I clicked on the wrong name, I did mean to click on your name.
I'm sorry.
How can I fix it????
BBAO is correct, I inmy hurry I clicked on the wrong name, I did mean to click on your name.
I'm sorry.
How can I fix it????