DHCP Leases failing, Windows 2000 Server
We are running a Windows 2000 Server domain...still. I know it's wrong, but in a manufacturing/small business environment, if it runs, it stays. It's not my name on the building.
Since inception, we have had 64k ISDN, 128k ISDN, 1.5G T-1, and 3.0G T-1 for our internet service from various providers. In the past, it has always worked out well and without issue to put the default gateway (firewall to the outside IP address), in as the only DNS server, and then assign the DNS servers as provided by the ISP in the firewall. No problems for years.
We upgraded the firewall to new hardware, same brand, just the newest model. No DNS changes needed. Then we upgraded to broadband 20G service from the local cable company. BIG changes!
Having the IP address of the firewall no longer allowed connectivity. To gain back connectivity, we had to but the PDC in as the primary DNS server both in the Windows Server and the as a DNS provider in the firewall options. That regained the connectivity. It should be noted that we have the one PDC, and no backup controller. It should also be noted that the PDC has NO outside connectivity via firewall policy. Never has, never will.
Since that time, there are spotty and inconvenient INTERNAL DNS problems. All clients get their leases from a reservation in DHCP Management, hence IPs are fixed and never change. What happens is the clients lose the "trust" relationship with PDC and can no longer access network drives shared from the PDC. running IPCONFIG/ALL shows that they are getting the proper IP, subnet. and default gateway. Still, network drives are not available. The fix is to log off and log back in such that the batch file to mount drives runs again and establishes trust once more.
At first, it felt like a server licensing issue, but only 34 of 50 CALs are in use. Beyond that, I can think of nothing else that would cause this behavior, and all things being equal, this wasn't an issue until we connected to the broadband service. They provider offers no answers as they are nothing more than the "the plug" we get service from. The must being doing something differently with DNS and how they manage it such that it has impact or tries to over ride the PDC settings. I don't really know now unless it is an IPv6/IPv4 thing? Still using IPv4 internally, obviously.
I welcome any ideas on this one. In theory, we just changed from the water tower to the well, just as we had in the past with no internal changes needed other than DNS at the firewall level. Now this. Thanks.
Since inception, we have had 64k ISDN, 128k ISDN, 1.5G T-1, and 3.0G T-1 for our internet service from various providers. In the past, it has always worked out well and without issue to put the default gateway (firewall to the outside IP address), in as the only DNS server, and then assign the DNS servers as provided by the ISP in the firewall. No problems for years.
We upgraded the firewall to new hardware, same brand, just the newest model. No DNS changes needed. Then we upgraded to broadband 20G service from the local cable company. BIG changes!
Having the IP address of the firewall no longer allowed connectivity. To gain back connectivity, we had to but the PDC in as the primary DNS server both in the Windows Server and the as a DNS provider in the firewall options. That regained the connectivity. It should be noted that we have the one PDC, and no backup controller. It should also be noted that the PDC has NO outside connectivity via firewall policy. Never has, never will.
Since that time, there are spotty and inconvenient INTERNAL DNS problems. All clients get their leases from a reservation in DHCP Management, hence IPs are fixed and never change. What happens is the clients lose the "trust" relationship with PDC and can no longer access network drives shared from the PDC. running IPCONFIG/ALL shows that they are getting the proper IP, subnet. and default gateway. Still, network drives are not available. The fix is to log off and log back in such that the batch file to mount drives runs again and establishes trust once more.
At first, it felt like a server licensing issue, but only 34 of 50 CALs are in use. Beyond that, I can think of nothing else that would cause this behavior, and all things being equal, this wasn't an issue until we connected to the broadband service. They provider offers no answers as they are nothing more than the "the plug" we get service from. The must being doing something differently with DNS and how they manage it such that it has impact or tries to over ride the PDC settings. I don't really know now unless it is an IPv6/IPv4 thing? Still using IPv4 internally, obviously.
I welcome any ideas on this one. In theory, we just changed from the water tower to the well, just as we had in the past with no internal changes needed other than DNS at the firewall level. Now this. Thanks.
use your router's dchp server and discard the dhcp role on the server
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
A little history is indicated. I took over this network back around 1999. Back then, it was being run with an NT4 domain controller with 9x and NT4 clients. I didn't know much then coming from a Mac environment, so I just migrated the routings used by the consultant, added some login scripts to mount network shares when moving to Windows 2000 Server. I don't recall if NT 4 server had forward/reverse lookup and full DNS capability or if it just passed that to the default gateway via the routing as described. I was happy to have AD and fixed IP addressing as administered in 2000 Server. So no, I have no idea why it has worked for as long as it has.
Thanks for the suggestion David, put I prefer not to give the DHCP role to the router as it is already working hard enough controlling the internal filtered internet and the unfiltered public wi-fi.
So maybe the switch to broadband has uncovered a longstanding improper configuration from the word go as Kevin suggests. Again, all things being equal, a change in the supplier of connectivity has never caused this problem. I failed to mention that new 20G service also comes from a fiber optic connection, not that it should matter, but maybe it does.
I'll leave this open for a bit more to cull any more ideas.
Thank you.
Thanks for the suggestion David, put I prefer not to give the DHCP role to the router as it is already working hard enough controlling the internal filtered internet and the unfiltered public wi-fi.
So maybe the switch to broadband has uncovered a longstanding improper configuration from the word go as Kevin suggests. Again, all things being equal, a change in the supplier of connectivity has never caused this problem. I failed to mention that new 20G service also comes from a fiber optic connection, not that it should matter, but maybe it does.
I'll leave this open for a bit more to cull any more ideas.
Thank you.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
"You mentioned that the DC has no outside connectivity. Does this mean that all types of traffic from the DC to the internet are blocked by the firewall? If so, can the DC at least use the firewall as a DNS server?"
Yes. That is how it was originally set up. The DC used the firewall IP as the router address and DNS forwarder. The IPCONFIG command on the clients return:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) 82566DM-2 Gigabit Network
on
Physical Address. . . . . . . . . : 00-21-5A-24-CA-6E
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.1.70
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.253
DHCP Server . . . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 192.168.1.1
192.168.1.253
Primary WINS Server . . . . . . . : 192.168.1.1
Lease Obtained. . . . . . . . . . : Sunday, October 12, 2014 8:44:58 AM
Lease Expires . . . . . . . . . . : Monday, October 20, 2014 8:44:58 AM
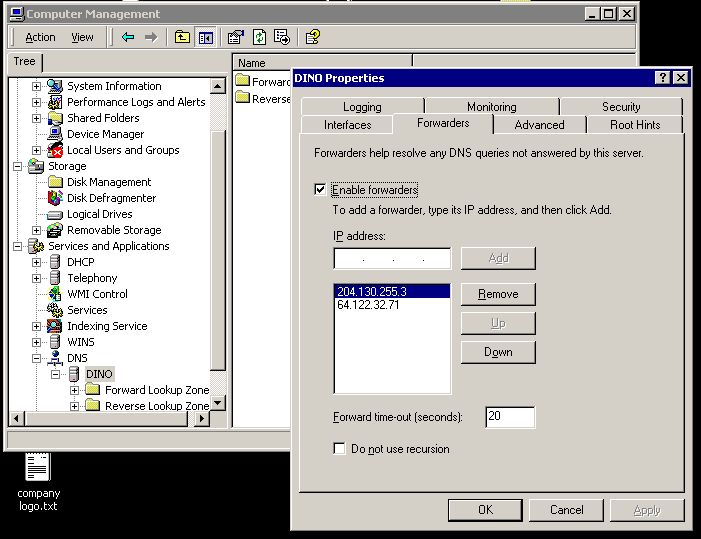
If I am understanding you, then I should remove the default gateway from the DNS server list from the DC. The attached file shows the DNS forwarders on the firewall side. "dino" is the DC. Be not confused by the status of Currently Assign Forwarders being "none." I questioned that one with the vendor, at that refers to other forwarders not seen in the list, if any. So I have two forwarders from the ISP, and the DC.
Thank you.
forwarders.jpg
Yes. That is how it was originally set up. The DC used the firewall IP as the router address and DNS forwarder. The IPCONFIG command on the clients return:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) 82566DM-2 Gigabit Network
on
Physical Address. . . . . . . . . : 00-21-5A-24-CA-6E
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.1.70
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.253
DHCP Server . . . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 192.168.1.1
192.168.1.253
Primary WINS Server . . . . . . . : 192.168.1.1
Lease Obtained. . . . . . . . . . : Sunday, October 12, 2014 8:44:58 AM
Lease Expires . . . . . . . . . . : Monday, October 20, 2014 8:44:58 AM
If I am understanding you, then I should remove the default gateway from the DNS server list from the DC. The attached file shows the DNS forwarders on the firewall side. "dino" is the DC. Be not confused by the status of Currently Assign Forwarders being "none." I questioned that one with the vendor, at that refers to other forwarders not seen in the list, if any. So I have two forwarders from the ISP, and the DC.
Thank you.
forwarders.jpg
If I am understanding you, then I should remove the default gateway from the DNS server list from the DC.That's correct, and it should be removed from the DNS server list on everything else in the domain as well. In addition, the DC should be removed from the firewall's DNS forwarder list (it should only be forwarding to outside DNS servers).
ASKER
Leave the router's address in option 003; that option assigns a default gateway to DHCP clients, which they need in order to access anything beyond the local network. Remove it from option 006, though.
ASKER
I will attempt this solution Friday morning on low traffic.
Thank you.
I did not see any WINS configurations in the DC Management Console, so I assume the ipconfig command is picking the DC up as the primary WINS server by default.
I'll update accordingly with you upon completion.
Many thanks.
Thank you.
I did not see any WINS configurations in the DC Management Console, so I assume the ipconfig command is picking the DC up as the primary WINS server by default.
I'll update accordingly with you upon completion.
Many thanks.
I did not see any WINS configurations in the DC Management Console, so I assume the ipconfig command is picking the DC up as the primary WINS server by default.Check the properties of the server's network adapter. I don't recall exactly where WINS servers are configured in Windows 2000, but on my Win7 machine, I can find the WINS server list by selecting TCP/IPv4, clicking Properties, clicking Advanced, and selecting the WINS tab.
ASKER
WINS is found under the Advanced Properties. Nothing entered in there. I have attached the base properties for you to see.
I did notice something else in the DC DNS that I'm not sure is a problem. You tell me. It has been my habit when replacing machines to keep the IP address the same by changing the Mac address in the DHCP reservations to reflect the identification of a the new machines. That saves me from having IPs in excess of that allowed by the scope as well as firewall assignments.
When I look inside the forward/reverse lookup zones on the DC, I am seeing the the DNS has forgotten NOTHING. Every machine that has ever been attached to the domain has a record. That means there are duplicate IP addresses in the lookup record. Is that a problem?
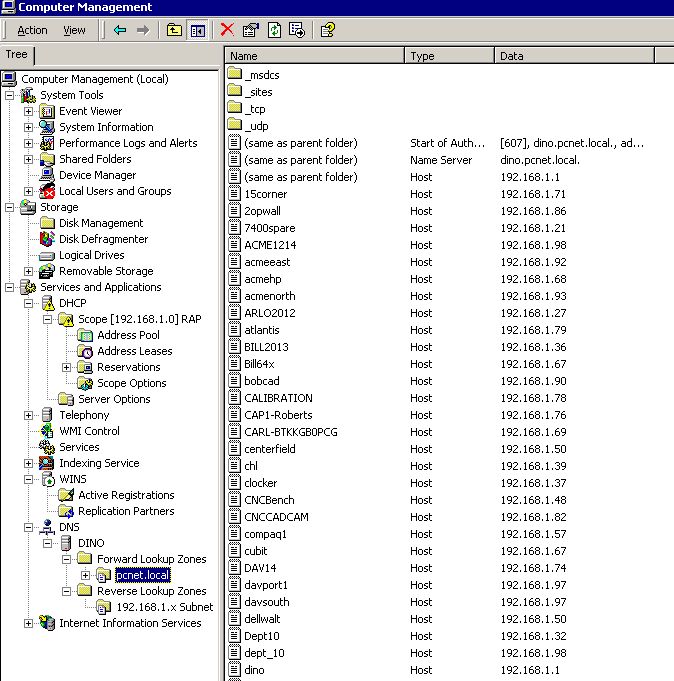
I did notice something else in the DC DNS that I'm not sure is a problem. You tell me. It has been my habit when replacing machines to keep the IP address the same by changing the Mac address in the DHCP reservations to reflect the identification of a the new machines. That saves me from having IPs in excess of that allowed by the scope as well as firewall assignments.
When I look inside the forward/reverse lookup zones on the DC, I am seeing the the DNS has forgotten NOTHING. Every machine that has ever been attached to the domain has a record. That means there are duplicate IP addresses in the lookup record. Is that a problem?


When I look inside the forward/reverse lookup zones on the DC, I am seeing the the DNS has forgotten NOTHING. Every machine that has ever been attached to the domain has a record. That means there are duplicate IP addresses in the lookup record. Is that a problem?It could be, in that some names may resolve to the wrong address. The best way to resolve this is to implement DNS aging and scavenging, which will allow a DNS server to periodically scan the records in its zones and remove ones that are older than a certain threshold. That article refers to 2003, but I believe the process for implementing it was the same in 2000. More information about how aging and scavenging work is available here.
ASKER
Thank you.
ASKER
Ah, what a tangle, what a cluster. But I think we are good now.
Talk about the perfect storm. I came in early to apply the suggested changes, all seemed well. Then, the bottom dropped out of the connectivity. I decided to put everything back as it was. Still nothing. Wireless hasn't missed a beat though.
I called the ISP, and as luck would have it, yes there was an outage, and they weren't too sure if our node was part of it. We went over the configurations, and sure enough, one of their DNS numbers had changed.
I decided to remove the DC from the firewall forwarders as well as removing the inside firewall IP from the DC DNS server list. Then I find some, but not all clients have regained connectivity. Then, I decided to add the ISP's DNS servers and the Google (8.8.8.8) public DNS server in the DC DNS server list as 2, 3, 4, behind the DC. Nothing changed.
Not seeing the forest for the trees. Even in the 21st century, all roads lead to a command prompt. As it works out, some machines were reaching the end of their DHCP default lease, others were not. ipconfig/release, renew finally got the new DNS schema working! Some, but not all the Win 7 clients picked up the changes unilaterally. Kind of reminds me back in the NT 4 server days when the first Win 2000 clients tried to be the master browser.
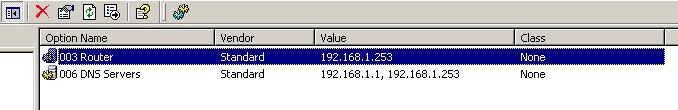
Time will tell if this solves the problem of disconnected network drives. I think so. I think having the the firewall IP in both the 003 Router and 006 DNS server list may have been the problem. Thanks to all. Below is how things are connecting up now.
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) 82566DM-2 Gigabit Network
onnection
Physical Address. . . . . . . . . : 00-21-5A-24-CA-6E
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.1.70
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.253
DHCP Server . . . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 192.168.1.1
97.64.168.10
97.64.183.163
8.8.8.8
Primary WINS Server . . . . . . . : 192.168.1.1
Lease Obtained. . . . . . . . . . : Friday, October 17, 2014 10:53:34 A
Lease Expires . . . . . . . . . . : Saturday, October 25, 2014 10:53:34
AM
Talk about the perfect storm. I came in early to apply the suggested changes, all seemed well. Then, the bottom dropped out of the connectivity. I decided to put everything back as it was. Still nothing. Wireless hasn't missed a beat though.
I called the ISP, and as luck would have it, yes there was an outage, and they weren't too sure if our node was part of it. We went over the configurations, and sure enough, one of their DNS numbers had changed.
I decided to remove the DC from the firewall forwarders as well as removing the inside firewall IP from the DC DNS server list. Then I find some, but not all clients have regained connectivity. Then, I decided to add the ISP's DNS servers and the Google (8.8.8.8) public DNS server in the DC DNS server list as 2, 3, 4, behind the DC. Nothing changed.
Not seeing the forest for the trees. Even in the 21st century, all roads lead to a command prompt. As it works out, some machines were reaching the end of their DHCP default lease, others were not. ipconfig/release, renew finally got the new DNS schema working! Some, but not all the Win 7 clients picked up the changes unilaterally. Kind of reminds me back in the NT 4 server days when the first Win 2000 clients tried to be the master browser.
Time will tell if this solves the problem of disconnected network drives. I think so. I think having the the firewall IP in both the 003 Router and 006 DNS server list may have been the problem. Thanks to all. Below is how things are connecting up now.
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) 82566DM-2 Gigabit Network
onnection
Physical Address. . . . . . . . . : 00-21-5A-24-CA-6E
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.1.70
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.253
DHCP Server . . . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 192.168.1.1
97.64.168.10
97.64.183.163
8.8.8.8
Primary WINS Server . . . . . . . : 192.168.1.1
Lease Obtained. . . . . . . . . . : Friday, October 17, 2014 10:53:34 A
Lease Expires . . . . . . . . . . : Saturday, October 25, 2014 10:53:34
AM
The client IP configuration that you posted doesn't look like it should, in my opinion.
Your DHCP server should only hand out 192.168.1.1 as a DNS server. All other DNS servers for the clients should be removed. If your domain controller is supposed to not have Internet access, the domain controller should have no gateway configured and it should have only 192.168.1.253 as the DNS forwarder.
I recommend that the firewall use OpenDNS servers 208.67.222.222 and 208.67.220.220. That should provide you with reliable access to your internal servers.
Your DHCP server should only hand out 192.168.1.1 as a DNS server. All other DNS servers for the clients should be removed. If your domain controller is supposed to not have Internet access, the domain controller should have no gateway configured and it should have only 192.168.1.253 as the DNS forwarder.
I recommend that the firewall use OpenDNS servers 208.67.222.222 and 208.67.220.220. That should provide you with reliable access to your internal servers.
ASKER
"That's correct, and it should be removed from the DNS server list on everything else in the domain as well. In addition, the DC should be removed from the firewall's DNS forwarder list (it should only be forwarding to outside DNS servers)."
"Your DHCP server should only hand out 192.168.1.1 as a DNS server. All other DNS servers for the clients should be removed. If your domain controller is supposed to not have Internet access, the domain controller should have no gateway configured and it should have only 192.168.1.253 as the DNS forwarder."
I guess I am confused. I should have removed the gateway from 003 Router, but left it in as DNS forwarder? NO 003 Router at all?
"Your DHCP server should only hand out 192.168.1.1 as a DNS server. All other DNS servers for the clients should be removed. If your domain controller is supposed to not have Internet access, the domain controller should have no gateway configured and it should have only 192.168.1.253 as the DNS forwarder."
I guess I am confused. I should have removed the gateway from 003 Router, but left it in as DNS forwarder? NO 003 Router at all?
I guess I am confused. I should have removed the gateway from 003 Router, but left it in as DNS forwarder? NO 003 Router at all?The gateway address needs to stay in option 003 Router, or none of your DHCP clients will be able to get to the Internet (or to anything outside their local network, for that matter). You can remove the gateway address from the IPv4 properties of the DC's network adapter in order to prevent it from accessing the Internet, but if you've got it blocked in the firewall anyway, it's not absolutely necessary.
The gateway address should be removed from option 006 DNS Servers, because everything in the domain should use only the DC (192.168.1.1) for DNS. This means that 97.64.168.10, 97.64.183.163, and 8.8.8.8 should all be removed from the list of DNS servers below:
DNS Servers . . . . . . . . . . . : 192.168.1.1The reason the gateway address should be configured as a DNS forwarder is that this is the only way the DC will be able to answer queries for external names, since it has no direct access to the Internet; it can query the firewall, but it can't directly query anything beyond it.
97.64.168.10
97.64.183.163
8.8.8.8
The only thing that should change in that image above is that 192.168.1.253 should be removed from option 006 DNS Servers.
ASKER
This KB states:
"If the server is the first and only domain controller that you install in the domain, and the server runs DNS, configure the DNS client settings to point to that first server's IP address. For example, you must configure the DNS client settings to point to itself. Do not list any other DNS servers until you have another domain controller hosting DNS in that domain."
and
"Do not configure the DNS client settings on the domain controllers to point to your Internet Service Provider's (ISP's) DNS servers. If you configure the DNS client settings to point to your ISP's DNS servers, the Netlogon service on the domain controllers does not register the correct records for the Active Directory directory service. With these records, other domain controllers and computers can find Active Directory-related information. The domain controller must register its records with its own DNS server. "
Which makes sense to me, but in practice, failed to provide connectivity to the outside once the switch to the fiber service.
http://support.microsoft.com/kb/825036
"If the server is the first and only domain controller that you install in the domain, and the server runs DNS, configure the DNS client settings to point to that first server's IP address. For example, you must configure the DNS client settings to point to itself. Do not list any other DNS servers until you have another domain controller hosting DNS in that domain."
and
"Do not configure the DNS client settings on the domain controllers to point to your Internet Service Provider's (ISP's) DNS servers. If you configure the DNS client settings to point to your ISP's DNS servers, the Netlogon service on the domain controllers does not register the correct records for the Active Directory directory service. With these records, other domain controllers and computers can find Active Directory-related information. The domain controller must register its records with its own DNS server. "
Which makes sense to me, but in practice, failed to provide connectivity to the outside once the switch to the fiber service.
http://support.microsoft.com/kb/825036
ASKER
"The reason the gateway address should be configured as a DNS forwarder is that this is the only way the DC will be able to answer queries for external names, since it has no direct access to the Internet; it can query the firewall, but it can't directly query anything beyond it."
That's where I'm confused. There, it says should be a DNS forwarder, but then, it should be removed from 006?
"The only thing that should change in that image above is that 192.168.1.253 should be removed from option 006 DNS Servers."
That's where I'm confused. There, it says should be a DNS forwarder, but then, it should be removed from 006?
"The only thing that should change in that image above is that 192.168.1.253 should be removed from option 006 DNS Servers."
That's where I'm confused. There, it says should be a DNS forwarder, but then, it should be removed from 006?Exactly, because these are two different things:
Option 006 tells your DHCP clients which DNS servers to use. They should only use the DC, so 192.168.1.1 should be the only address in that option.
A DNS forwarder tells the DNS server (the DC) where to send queries that it can't answer (queries for internet names, for example). Since the DC can't send anything directly out to the Internet by policy but can send things as far as the router/firewall, 192.168.1.253 should be the only address configured as a forwarder.
With this configuration, clients will send all of their DNS queries (internal and external) to the DC. An internal query will be answered then and there, while an external query will be sent to the router, which will in turn send it to whatever external DNS server(s) it's configured to use. It'll get a response and send that response to the DC, which will in turn send it to the client that initiated the query. All the client knows - and all it needs to know - is that it should always query the DC, and the DC will get an answer. The client doesn't need to know how or where the DC gets that answer.
How to configure DNS forwarder.
http://technet.microsoft.com/en-us/library/cc773370(v=ws.10).aspx
http://technet.microsoft.com/en-us/library/cc773370(v=ws.10).aspx
ASKER
Now I think I see the problem, at last. It explains almost all the issues. I found where the forwarders are in DNS and NOT DHCP. That's where I was getting confused. I look at Forwarders in that Properties tab only to find two external IPs in there. One is the external gateway of our old ISP and the other a DNS server from our old ISP. I have NO idea how they got there! I suspect they had an internet outage while I was on vacation and these numbers were plugged in by a consultant or were put in there by my boss per ISP support. That would explain why plugging into new service caused this issue.
So if I now understand completely, the ONLY DNS Forwarder in there should be the default gateway address, and then the public DNS servers can be configured on the firewall. You suggest Open DNS numbers as opposed to the ISP DNS servers? I think I'll use both as well as the Google public DNS Server as it seems that the only way you know when those addresses change is in the event of a failure. I guess it's good to have plenty of fall backs and fail safes.
Well...another Friday of touching all machines is ahead. To be clear, I will:
in DHCP:
003 Router 192.168.1.253 (default firewall gateway)
006 DNS 192.168.1.1 (DC IP address)
in DNS
Forwarder 192.168.1.253 (default firewall gateway)
in the firewall DNS:
Any public DNS servers I wish to use.
Correct now?
So if I now understand completely, the ONLY DNS Forwarder in there should be the default gateway address, and then the public DNS servers can be configured on the firewall. You suggest Open DNS numbers as opposed to the ISP DNS servers? I think I'll use both as well as the Google public DNS Server as it seems that the only way you know when those addresses change is in the event of a failure. I guess it's good to have plenty of fall backs and fail safes.
Well...another Friday of touching all machines is ahead. To be clear, I will:
in DHCP:
003 Router 192.168.1.253 (default firewall gateway)
006 DNS 192.168.1.1 (DC IP address)
in DNS
Forwarder 192.168.1.253 (default firewall gateway)
in the firewall DNS:
Any public DNS servers I wish to use.
Correct now?

Well...another Friday of touching all machines is ahead. To be clear, I will:Yep, that all sounds good!
in DHCP:
003 Router 192.168.1.253 (default firewall gateway)
006 DNS 192.168.1.1 (DC IP address)
in DNS
Forwarder 192.168.1.253 (default firewall gateway)
in the firewall DNS:
Any public DNS servers I wish to use.
Correct now?
ASKER
THANK YOU!
As it sits now, the public DNS forwaders in DHCP are over riding the forwarders in DNS. I assume...
Next time the boss says, "We had a problem while your were gone and "they" changed some things..."
As it sits now, the public DNS forwaders in DHCP are over riding the forwarders in DNS. I assume...
Next time the boss says, "We had a problem while your were gone and "they" changed some things..."
ASKER
Thank you again all! Happy place!
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) 82566DM-2 Gigabit Network
onnection
Physical Address. . . . . . . . . : 00-21-5A-24-CA-6E
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.1.70
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.253
DHCP Server . . . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 192.168.1.1
Primary WINS Server . . . . . . . : 192.168.1.1
Lease Obtained. . . . . . . . . . : Tuesday, October 21, 2014 10:53:35
M
Lease Expires . . . . . . . . . . : Wednesday, October 29, 2014 10:53:3
AM
Ethernet adapter Local Area Connection:
Connection-specific DNS Suffix . :
Description . . . . . . . . . . . : Intel(R) 82566DM-2 Gigabit Network
onnection
Physical Address. . . . . . . . . : 00-21-5A-24-CA-6E
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.1.70
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.253
DHCP Server . . . . . . . . . . . : 192.168.1.1
DNS Servers . . . . . . . . . . . : 192.168.1.1
Primary WINS Server . . . . . . . : 192.168.1.1
Lease Obtained. . . . . . . . . . : Tuesday, October 21, 2014 10:53:35
M
Lease Expires . . . . . . . . . . : Wednesday, October 29, 2014 10:53:3
AM
Looks perfect on the client.
ASKER
I'm very pleased. Many of the clients picked up the changes on their own. Those with active web sessions tied to the old DNS order did not.
I can't thank you enough for the guidance on this one.
I can't thank you enough for the guidance on this one.