Monitor Capture command
I have this version of IOS:
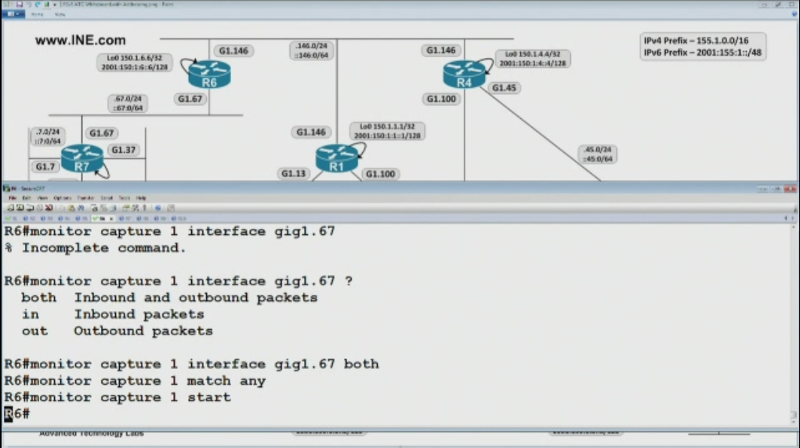
However when I run the monitor capture command, I do not see what is shown in the screenshot. I mean I cannot type monitor capture 1 Interface .....
R1#sh version | include Version
Cisco IOS Software, 7200 Software (C7200-ADVIPSERVICESK9-M), Version 15.0(1)M, RELEASE SOFTWARE (fc2)
BOOTLDR: 7200 Software (C7200-ADVIPSERVICESK9-M), Version 15.0(1)M, RELEASE SOFTWARE (fc2)
6 slot VXR midplane, Version 2.1
R1#However when I run the monitor capture command, I do not see what is shown in the screenshot. I mean I cannot type monitor capture 1 Interface .....
R1#monitor capture ?
buffer Control Capture Buffers
point Control Capture PointsSOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
7200 series , IOS 15.0.1
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I initially thought the configuration was on an ASA
The wireshark reference applies to low end devices that don't support Embedded Packet Capture.
The capture needs to be created first and based on the command syntax, "1" is supposed to be the capture name. In the IOS version used, name is not an option after "monitor capture...". The only available options are buffer and point.
The wireshark reference applies to low end devices that don't support Embedded Packet Capture.
The capture needs to be created first and based on the command syntax, "1" is supposed to be the capture name. In the IOS version used, name is not an option after "monitor capture...". The only available options are buffer and point.
ASKER
I guess it is IOS version
ASKER
Thank you Guys!
ASKER
Open in new window