Disabled SSLv2 and SSLv3 but Wireshark is still showing attempted SSL connections to Authorize.net
With the POODLE vulnerability, credit card gateway Authorize.NET has disabled support for SSLv3/SSLv2 and is requiring TLS to be used to connect to their service.
I'm running into an odd issue however. I have two web servers, both running the same web ecommerce application (Lagarde Storefront 6.8.0.3), our developer is adamant that the exact same code is running on both web servers (each site just has a different domain name)
Both servers have SSLv2 and SSLv3 disabled, and this is confirmed by https://www.poodlescan.com/
This is also confirmed by the registry:
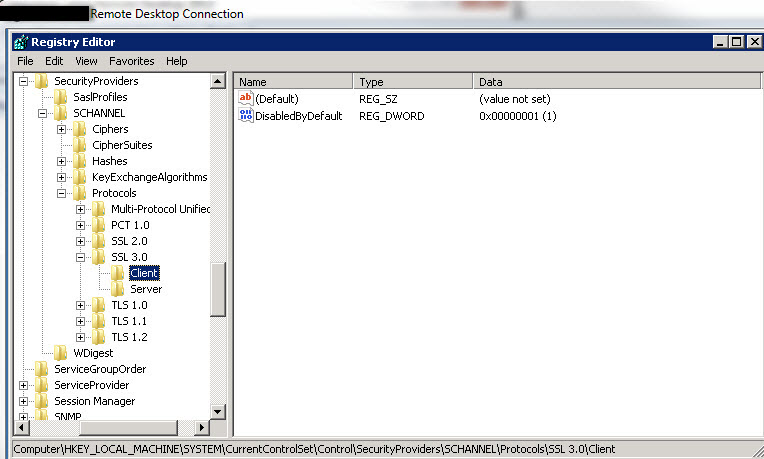
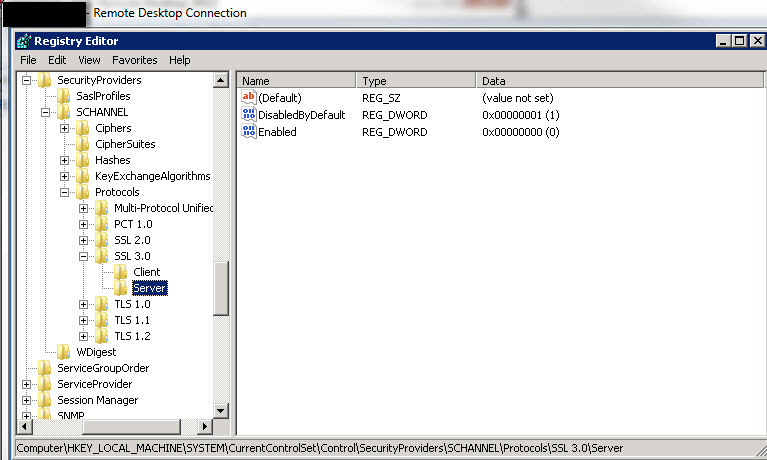
However, one site cannot process credit card transactions (Authorize.net is refusing or closing the connection), and I have confirmed different behavior via Wireshark.
One server is trying to connect using SSL v3, while the working server is using TLS:
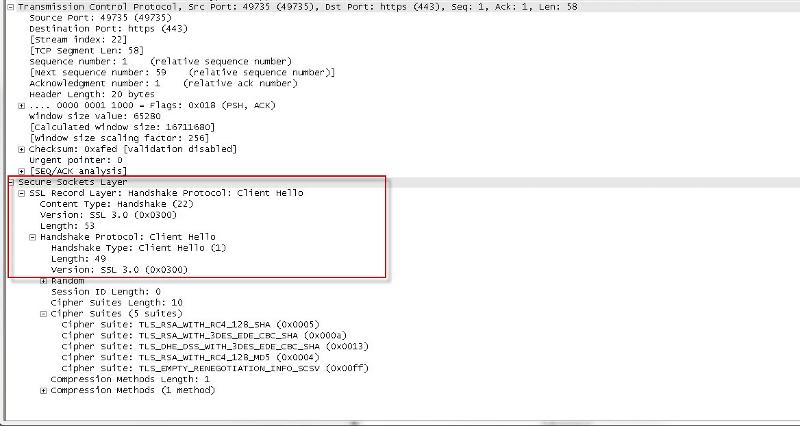
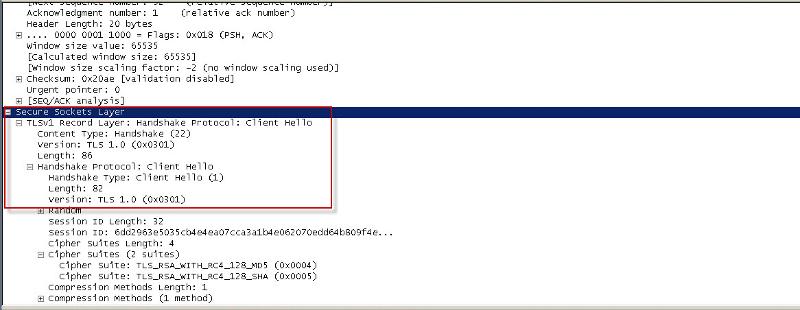
If the code is identical on both servers as the developer claims, and SSL v2 and SSL v3 is confirmed DISABLED on both servers, what could it possibly be on the one server that is trying to use SSL to connect? (if not the web application code)
The working server (using TLS) is running WIndows Server 2003 and the server trying to connect using SSL is a Server 2008 R2 server.
Any ideas what else I can check (server-side) that may be contributing to the connection attempting SSL rather than TLS?
Thanks
I'm running into an odd issue however. I have two web servers, both running the same web ecommerce application (Lagarde Storefront 6.8.0.3), our developer is adamant that the exact same code is running on both web servers (each site just has a different domain name)
Both servers have SSLv2 and SSLv3 disabled, and this is confirmed by https://www.poodlescan.com/
This is also confirmed by the registry:


However, one site cannot process credit card transactions (Authorize.net is refusing or closing the connection), and I have confirmed different behavior via Wireshark.
One server is trying to connect using SSL v3, while the working server is using TLS:


If the code is identical on both servers as the developer claims, and SSL v2 and SSL v3 is confirmed DISABLED on both servers, what could it possibly be on the one server that is trying to use SSL to connect? (if not the web application code)
The working server (using TLS) is running WIndows Server 2003 and the server trying to connect using SSL is a Server 2008 R2 server.
Any ideas what else I can check (server-side) that may be contributing to the connection attempting SSL rather than TLS?
Thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks, looks like that is only for Windows Server 2008 R2 and higher, so just noting that here for anyone else that finds this thread.
This is very useful however so thank you for that, even if manually making changes one can easily refer to the powershell code for the needed changes and it's nicely commented.
Appreciate it.
This is very useful however so thank you for that, even if manually making changes one can easily refer to the powershell code for the needed changes and it's nicely commented.
Appreciate it.
you're welcome
ASKER
For ASP.NET, putting something like this in the code will force the web application to use TLS for outgoing connections:
System.Net.ServicePointMan
What I still need to know is where in IIS6 and IIS7 to force this for the entire server so no coding changes are needed.
Thanks