Powershell script to pull all AD accounts from a specified OU and add them as member into a Security Group
Is there a Powershell script that can pull all the users AD account from an OU and add them to a specific Security Group? I want to automate this and not have to rely on each site helpdesk to add manually as a member of this group when setting up a new user. A lot of time they forget so best way is having this scheduled to run daily.
ASKER
No this did not work.
What specifically did not work ?
I am hoping you actually put in the right values for the OU and for the groupname ?
I am hoping you actually put in the right values for the OU and for the groupname ?
Try this:
Get-ADUser -SearchBase 'OU=Users,OU=Company,DC=domain,DC=com' -Filter * | % { Add-ADGroupMember 'Name of Security Group' -Members $_ }
To elaborate, here's a screenshot of the properties of a Security Group where I changed it's name but not the pre-Windows 2000 name
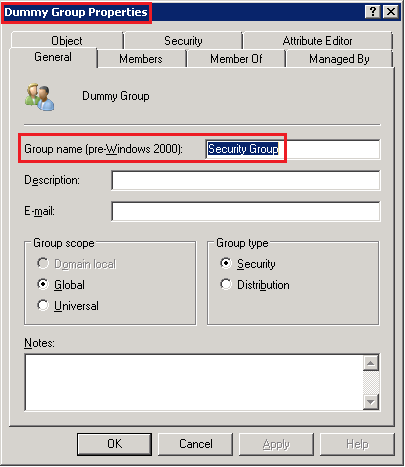 If you look at the top bar, you'll see that I've named the group Dummy Group. If I then attempt to run the above script and use the group name Dummy Group then PowerShell will spit out an error for each and every user in the OU.
If you look at the top bar, you'll see that I've named the group Dummy Group. If I then attempt to run the above script and use the group name Dummy Group then PowerShell will spit out an error for each and every user in the OU.
If I change the script to use the group name Security Group then it will work as expected and add all the users within the OU to the group.
Hope this clears things up.
 If you look at the top bar, you'll see that I've named the group Dummy Group. If I then attempt to run the above script and use the group name Dummy Group then PowerShell will spit out an error for each and every user in the OU.
If you look at the top bar, you'll see that I've named the group Dummy Group. If I then attempt to run the above script and use the group name Dummy Group then PowerShell will spit out an error for each and every user in the OU. If I change the script to use the group name Security Group then it will work as expected and add all the users within the OU to the group.
Hope this clears things up.
ASKER
VB ITS ... this worked!! Can you tell me if you know how to pull multiple OU's into one single security group?
I am not sure what would have worked in the script VBITS provided that would not in mine since they are exactly the same thing ?
Are you asking to have the members of multiple OUs added to a single security group ?
If so, you can either populate a text file with all the OUs and simply pipe into a foreach loop.
Are you asking to have the members of multiple OUs added to a single security group ?
If so, you can either populate a text file with all the OUs and simply pipe into a foreach loop.
ASKER
becraig,
Your script gave me multiple errors. Can you give me an example of what you're stating to populate all the OU's?
Your script gave me multiple errors. Can you give me an example of what you're stating to populate all the OU's?
you can get all OUs using Get-ADOrganizationalUnit
e.g :
Get-ADOrganizationalUnit -Filter 'Name -like "*"' | FT Name, DistinguishedName -A
More info:
http://ss64.com/ps/get-adorganizationalunit.html
e.g :
Get-ADOrganizationalUnit -Filter 'Name -like "*"' | FT Name, DistinguishedName -A
More info:
http://ss64.com/ps/get-adorganizationalunit.html
ASKER
That's not really helping me if there's no real examples that can be scripted and tested.
There are 3 examples on the page I provided the link to, but let me post them here:
Examples
Get all the Organizational Units in the domain:
PS C:\>
Gets the Organizational Unit with DistinguishedName 'OU=Sydney,OU=Demo,DC=SS64
PS C:\>
Gets OUs underneath the 'Sydney' Organizational Unit using an LDAP filter:
PS C:\>
Examples
Get all the Organizational Units in the domain:
PS C:\>
Get-ADOrganizationalUnit -Filter 'Name -like "*"' | FT Name, DistinguishedName -AGets the Organizational Unit with DistinguishedName 'OU=Sydney,OU=Demo,DC=SS64
PS C:\>
Get-ADOrganizationalUnit -Identity 'OU=Sydney,OU=Demo,DC=SS64,DC=COM' | FT Name,Country,PostalCode,City,StreetAddress,State -AGets OUs underneath the 'Sydney' Organizational Unit using an LDAP filter:
PS C:\>
Get-ADOrganizationalUnit -LDAPFilter '(name=*)' -SearchBase 'OU=Sydney,OU=Demo,DC=SS64,DC=COM' -SearchScope OneLevel | FT Name,Country,PostalCode,City,StreetAddress,StateASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Open in new window