Configure ZyWALL Firewall/Router to work with Cox CIDR and WAN IP
I have a small business network (~20 workstations and a few dozen VM-based servers) that is served by Cox Business. All machines on our LAN have private IP addresses (192.168.1.xx) although some have a 1:1 NAT mapping to static public IPs. Historically, we have paid Cox to provide us with a small number (~10) static IPs and configuring the network was a no-brainer. Having now moved to a new office however, Cox initially provided us with five (5) static IPs but has now informed us that they are taking away four (4) of the five (5) static IPs and replacing them with a CIDR block (in an entirely different subnet). I have read postings from others (both here on EE and elsewhere) who, like me , were confused as to how to configure their hardware to work with CIDR but their specific cases were slightly different than mine and they used different hardware). While I am happy that Cox has assigned me what appears to be a much larger pool of usable public addresses (29), I am unsure how to take advantage of them!
My particulars are as follows (IPs changed slightly from actuals):
Router/Firewall: ZyXEL ZyWALL 110 (part of the ZyWALL 100/200/300 family)
WAN Address: 28.175.185.216
WAN Network Mask: 255.255.255.240
WAN Gateway: 28.175.185.209
DNS1: 68.105.28.16
DNS2: 68.105.29.16
Customer Network: 174.80.25.128/27
Suggested Default Gateway: 174.80.25.129
Customer Netmask: 255.255.255.224
Usable CIDR IPs: 174.80.25.130 - 174.80.25.158
Broadcast IP: 174.80.25.159
I would like to keep all of my machines on the same private network and, where necessary, provide either 1:1 NATing or port mapping as needed.
Can someone please:
Explain the difference between my old approach (with dedicated static IPs, all in the same subnet) and the new CIDR approach with a block of IPs (in a different subnet from the assigned WAN IP).
Educate me on how best to configure my specific firewall/router to work with this new approach.
Thanks in advance for any-and-all assistance!
My particulars are as follows (IPs changed slightly from actuals):
Router/Firewall: ZyXEL ZyWALL 110 (part of the ZyWALL 100/200/300 family)
WAN Address: 28.175.185.216
WAN Network Mask: 255.255.255.240
WAN Gateway: 28.175.185.209
DNS1: 68.105.28.16
DNS2: 68.105.29.16
Customer Network: 174.80.25.128/27
Suggested Default Gateway: 174.80.25.129
Customer Netmask: 255.255.255.224
Usable CIDR IPs: 174.80.25.130 - 174.80.25.158
Broadcast IP: 174.80.25.159
I would like to keep all of my machines on the same private network and, where necessary, provide either 1:1 NATing or port mapping as needed.
Can someone please:
1.
Explain the difference between my old approach (with dedicated static IPs, all in the same subnet) and the new CIDR approach with a block of IPs (in a different subnet from the assigned WAN IP).
2.
Educate me on how best to configure my specific firewall/router to work with this new approach.
Thanks in advance for any-and-all assistance!
ASKER
noci:
Thanks for the quick reply. Your directions sound simple enough however I don't see any place to specify a range/block in the ZyWALL configuration screens:

In addition to the ZyXEL forums, I have searched the ZyWALL 110 User's Guide and Application Note docs but cannot find any reference to "secondary range" or "CIDR". Perhaps they call it something else? Do I have to create Virtual Interfaces for each-and-every IP address in the CIDR block instead? Also where would I specify the CIDR default gateway and broadcast IP params?
Thanks for the quick reply. Your directions sound simple enough however I don't see any place to specify a range/block in the ZyWALL configuration screens:
In addition to the ZyXEL forums, I have searched the ZyWALL 110 User's Guide and Application Note docs but cannot find any reference to "secondary range" or "CIDR". Perhaps they call it something else? Do I have to create Virtual Interfaces for each-and-every IP address in the CIDR block instead? Also where would I specify the CIDR default gateway and broadcast IP params?
ok you have the IP address & netmask field.
CIDR is a different netmask spec.
/32 = 255.255.255.255
/30 = 255.255.255.252 252 = (128 + 64 + 32 +16 + 8 + 4)
/28 = 255.255.255.240 240 = (128 + 64 +32 + 16)
/26 = 255.255.255.192 192 = (128 + 64)
/24 = 255.255.255.0
/16 =255.255.0.0
/8 = 255.0.0.0
/0 = 0.0.0.0
CIDR is a different netmask spec.
/32 = 255.255.255.255
/30 = 255.255.255.252 252 = (128 + 64 + 32 +16 + 8 + 4)
/28 = 255.255.255.240 240 = (128 + 64 +32 + 16)
/26 = 255.255.255.192 192 = (128 + 64)
/24 = 255.255.255.0
/16 =255.255.0.0
/8 = 255.0.0.0
/0 = 0.0.0.0
ASKER
noci:
Again, much appreciate the reply.
Per your last response, I understand how a netmask is derived. That said, it is still unclear to me where I can enter the CIDR information (in its entirety) as it was supplied to me by Cox:
The range of CIDR addresses: 174.80.25.128/27
The default gateway associated with the above CIDR block: 174.80.25.129
The netmask associated with the above CIDR block: 255.255.255.224
The broadcast IP associated with the above CIDR block: 174.80.25.159
Does the ZyWALL 110 device even have a facility for specifying a range? If so, I don't see it. If not, if I want to take advantage of all of the available usable IPs in the CIDR block (174.80.25.130 - 174.80.25.158), do I need to explicitly define a Virtual Interface for each-and-every IP (i.e. 29 Virtual Interfaces - wan:1:1-wan1:29)?
FWIW, I tried creating a Virtual Interface for one of the IPs (174.80.25.130) but it didn't appear to work (could not ping machine 1:1 NATed to IP):
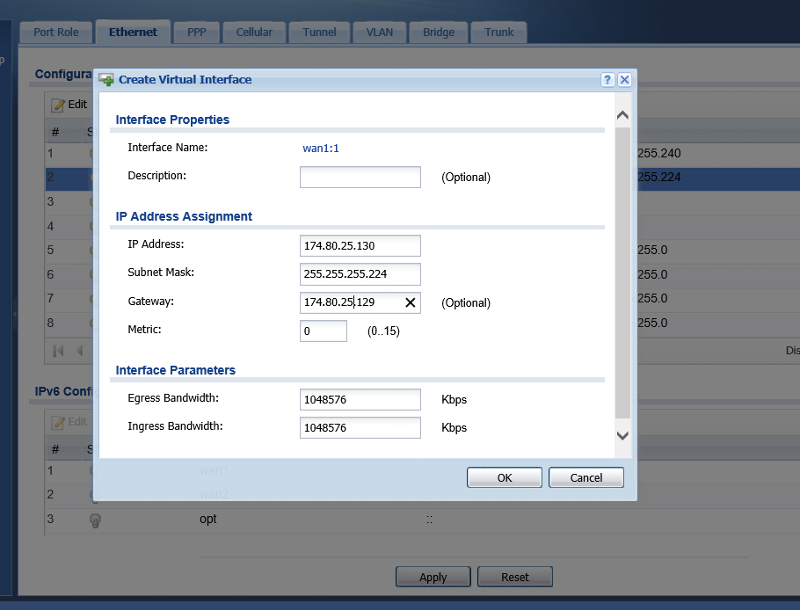
Sorry if I'm being dense. Please feel free to point out my stupidity... <grin> Thanks.
Again, much appreciate the reply.
Per your last response, I understand how a netmask is derived. That said, it is still unclear to me where I can enter the CIDR information (in its entirety) as it was supplied to me by Cox:
The range of CIDR addresses: 174.80.25.128/27
The default gateway associated with the above CIDR block: 174.80.25.129
The netmask associated with the above CIDR block: 255.255.255.224
The broadcast IP associated with the above CIDR block: 174.80.25.159
Does the ZyWALL 110 device even have a facility for specifying a range? If so, I don't see it. If not, if I want to take advantage of all of the available usable IPs in the CIDR block (174.80.25.130 - 174.80.25.158), do I need to explicitly define a Virtual Interface for each-and-every IP (i.e. 29 Virtual Interfaces - wan:1:1-wan1:29)?
FWIW, I tried creating a Virtual Interface for one of the IPs (174.80.25.130) but it didn't appear to work (could not ping machine 1:1 NATed to IP):

Sorry if I'm being dense. Please feel free to point out my stupidity... <grin> Thanks.
Now did you get the block as a replacement for the current address or in addition to the one WAN address....
(What happens is that your provider has setup your entire block as being routed over the original WAN link.
(Additional CIDR Block)
If you have 1 address on WAN and a 2nd CIDR block on a virtual interface, then normaly only the WAN default gateway applies for ALL routes. In some cases you can also use the Broadcast & Base address as an address.
If it is a replacement then the old address appearantly are droppen, then you don't need the virtual interface, but modify the WAN. (BTW, THis is not what i read from your original Q).
Virtual addresses should not be created per address.
A NAT routing entry should be created for that. (And obviously a Firewall rule to allow the traffic to that address on the WAN). Also a WAN -> Zywall rule would be needed including that CIDR address range to respond to Ping.
And you may need specific routing rules specifying outgoin NAT settings for traffic. (A 1:1 NAT rule would do that for you).
(What happens is that your provider has setup your entire block as being routed over the original WAN link.
(Additional CIDR Block)
If you have 1 address on WAN and a 2nd CIDR block on a virtual interface, then normaly only the WAN default gateway applies for ALL routes. In some cases you can also use the Broadcast & Base address as an address.
If it is a replacement then the old address appearantly are droppen, then you don't need the virtual interface, but modify the WAN. (BTW, THis is not what i read from your original Q).
Virtual addresses should not be created per address.
A NAT routing entry should be created for that. (And obviously a Firewall rule to allow the traffic to that address on the WAN). Also a WAN -> Zywall rule would be needed including that CIDR address range to respond to Ping.
And you may need specific routing rules specifying outgoin NAT settings for traffic. (A 1:1 NAT rule would do that for you).
ASKER
noci:
Per your question, our ISP is routing the CIDR block over the original WAN IP. That said, from your last posting, it appears that we need to create one Virtual Interface on WAN1. Not to beat this to death, but the Virtual Interface dialog doesn't appear to accept IP address ranges - just discrete IPs (see image from previous post). How do I specify the CIDR range? In your post, you state "In some cases you can also use the Broadcast & Base address as an address". In lieu of specifying the CIDR range, are you suggesting I try using one of these two address in the Virtual Interface instead? I'll give it a try...
With respect to the ping testing, I already created firewall/routing rules to enable pinging a public IP and having it return an echo if the corresponding 1:1 mapped private IP is up-and-running. I was already doing this without problems when I was using plain old static IPs in the same subnet as my WAN IP.
I will try re-configuring the Virtual Interface again using either the broadcast IP or base address and see if this fixes things.
Thanks again!
Per your question, our ISP is routing the CIDR block over the original WAN IP. That said, from your last posting, it appears that we need to create one Virtual Interface on WAN1. Not to beat this to death, but the Virtual Interface dialog doesn't appear to accept IP address ranges - just discrete IPs (see image from previous post). How do I specify the CIDR range? In your post, you state "In some cases you can also use the Broadcast & Base address as an address". In lieu of specifying the CIDR range, are you suggesting I try using one of these two address in the Virtual Interface instead? I'll give it a try...
With respect to the ping testing, I already created firewall/routing rules to enable pinging a public IP and having it return an echo if the corresponding 1:1 mapped private IP is up-and-running. I was already doing this without problems when I was using plain old static IPs in the same subnet as my WAN IP.
I will try re-configuring the Virtual Interface again using either the broadcast IP or base address and see if this fixes things.
Thanks again!
Ip address = 174.80.25.128
Netmask = 255.255.255.224
The description that this is the X/Y/Z Address range provided by... [ if you want to ]
And possibly bandwidth settings.
(the first two define the range from 174.80.25.128 - 174.80.25.159 [ inclusive ]. )
nothing else.
Netmask = 255.255.255.224
The description that this is the X/Y/Z Address range provided by... [ if you want to ]
And possibly bandwidth settings.
(the first two define the range from 174.80.25.128 - 174.80.25.159 [ inclusive ]. )
nothing else.
ASKER
Sorry for the long delay in responding. I have been dealing with a major health issue that arose in December of last year...
Per your last post, I was never able to configure my specific firewall device (ZyWALL 110) according to your recommendations and get it to work. I reached out multiple times to ZyXEL (via voice-mails, CSR ticket submissions and forum postings - no response). Needless to say, I am less than impressed with their customer service... <grrr>
Per your last post, I was never able to configure my specific firewall device (ZyWALL 110) according to your recommendations and get it to work. I reached out multiple times to ZyXEL (via voice-mails, CSR ticket submissions and forum postings - no response). Needless to say, I am less than impressed with their customer service... <grrr>
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
noci:
While I still cannot find any place in the 110's UI or their documentation that addresses specifying a CIDR block range, you have bent over backwards trying to help me and I won't string you along any further. I finally made contact with ZyXEL Support asking them the same questions posed here and they seem to be just as much in the dark as I am (not very reassuring). Regardless, I will continue to bang on them until they figure it out.
Thanks again for sticking with the thread as long as you did!
While I still cannot find any place in the 110's UI or their documentation that addresses specifying a CIDR block range, you have bent over backwards trying to help me and I won't string you along any further. I finally made contact with ZyXEL Support asking them the same questions posed here and they seem to be just as much in the dark as I am (not very reassuring). Regardless, I will continue to bang on them until they figure it out.
Thanks again for sticking with the thread as long as you did!
Well CIDR ranges need to be transposed to their netmask equivalences...
/1 = 128.0.0.0
/2 = 192.0.0.0
/3 = 224.0.0.0
/4 = 240.0.0.0
/5 = 248.0.0.0
/6 = 252.0.0.0
/7 = 254.0.0.0
/8 = 255.0.0.0
/16 = 255.255.0.0
/24 = 255.255.255.0
/32 = 255.255.255.255
/1 = 128.0.0.0
/2 = 192.0.0.0
/3 = 224.0.0.0
/4 = 240.0.0.0
/5 = 248.0.0.0
/6 = 252.0.0.0
/7 = 254.0.0.0
/8 = 255.0.0.0
/16 = 255.255.0.0
/24 = 255.255.255.0
/32 = 255.255.255.255
ASKER
FWIW, this is the response I just received from ZyXEL (sounds like they're admitting that the ZyWALL 110 does not not natively support CIDR block addressing):
Hello,
Unfortunately our devices is limited and we cannot accommodate the addresses with their suggested gateway. You would have to input each address under 1;1 NAT so you can map them to internal devices.
Please call our support center to better assist you at:
1-800-255-4101 Opt. 5
Select the right WAN interface(f.e. wan1), then create a virtual interface on it.
(you will then get: wan1:1 ..) and fill out the fields with ipaddress & netmask.
Also adjust the firewall rules accordingly (in case an interface is mentioned f.e. wan1 is not equal to wan1:1
Then use those address for NAT.