Draft2007
asked on
Can only ping one way through ASA, NAT issue?
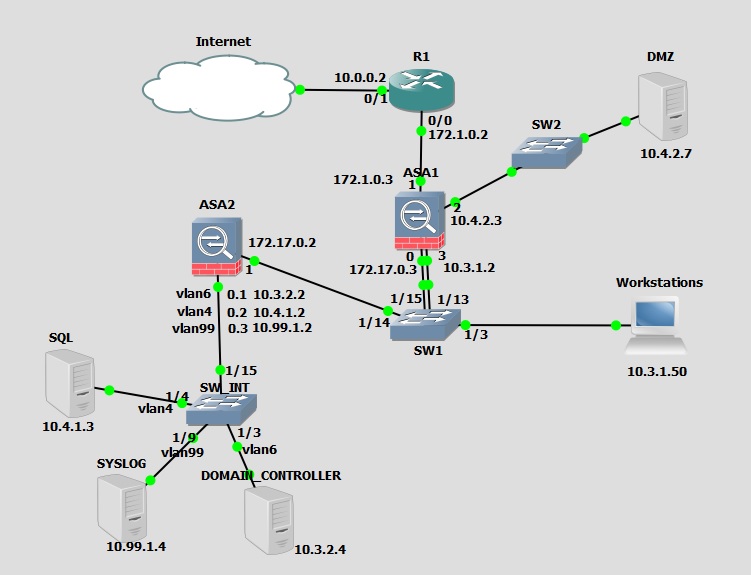
Hello, over the last couple of days I have been setting up a test network that I am going to use for penetration testing but have gotten stuck completing the final connection.
I have full connectivity between all areas of the network except the Workstation (10.3.1.50) cannot ping to any of the internal servers (Domain Controller, Syslog, SQL, etc). However, when issuing pings from the internal servers to the Workstation, all of them succeed. All of the OS Firewalls have been disabled no I am pretty sure that is not causing the problem. Any help or suggestions would be greatly appreciated.
Successful ping from Domain Controller (10.3.2.4) to Workstation (10.3.1.50)
http://s30.postimg.org/u5p5077xd/dcping.jpg
Failed ping from Workstation (10.3.1.50) to Domain Controller (10.3.2.4)
[img]http://s12.postimg.org/5vs7hddal/pingfail.jpg[/img]
ASA1 Configuration
ASA Version 8.4(2)
!
hostname ASA
enable password
!
interface GigabitEthernet0
nameif workstations
security-level 100
ip address 10.3.1.2 255.255.255.0
!
interface GigabitEthernet1
nameif outside
security-level 100
ip address 172.1.0.3 255.255.255.0
!
interface GigabitEthernet2
nameif DMZ
security-level 100
ip address 10.4.2.3 255.255.255.0
!
interface GigabitEthernet3
nameif inside
security-level 100
ip address 172.17.0.3 255.255.255.0
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network dmz-net
subnet 10.4.2.0 255.255.255.0
object network workstations
subnet 10.3.1.0 255.255.255.0
object network internal-out
subnet 172.17.0.0 255.255.255.0
access-list outside_access_in extended permit ip any any
pager lines 24
mtu workstations 1500
mtu outside 1500
mtu DMZ 1500
mtu inside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network dmz-net
nat (DMZ,outside) dynamic interface
object network workstations
nat (workstations,outside) dynamic interface
object network internal-out
nat (inside,outside) dynamic interface
access-group outside_access_in global
route outside 0.0.0.0 0.0.0.0 172.1.0.2 1
route outside 10.3.2.0 255.255.255.0 172.17.0.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh timeout 10
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
SW1 Configuration
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname VLAN_SW1
!
boot-start-marker
boot-end-marker
!
no aaa new-model
memory-size iomem 5
no ip routing
no ip icmp rate-limit unreachable
no ip cef
!
no ip domain lookup
!
multilink bundle-name authenticated
!
vtp mode transparent
archive
log config
hidekeys
!
vlan 3,6,99
!
ip tcp synwait-time 5
ip ssh version 1
!
interface FastEthernet0/0
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
switchport mode trunk
speed 100
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
switchport mode trunk
speed 100
!
interface FastEthernet1/15
switchport mode trunk
speed 100
!
interface Vlan1
no ip address
no ip route-cache
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 172.17.0.3
!
no ip http server
no ip http secure-server
!
no cdp log mismatch duplex
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
end
ASA2 Configuration
ASA Version 8.4(2)
!
hostname ASA2
!
interface GigabitEthernet0
no nameif
no security-level
no ip address
!
interface GigabitEthernet0.1
vlan 6
nameif vlan6
security-level 100
ip address 10.3.2.2 255.255.255.0
!
interface GigabitEthernet0.2
vlan 4
nameif vlan4
security-level 100
ip address 10.4.1.2 255.255.255.0
!
interface GigabitEthernet0.3
vlan 99
nameif vlan99
security-level 100
ip address 10.99.1.2 255.255.255.0
!
interface GigabitEthernet1
nameif outside
security-level 100
ip address 172.17.0.2 255.255.255.0
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network core-servers
subnet 10.3.2.0 255.255.255.0
object network dist-servers
subnet 10.4.1.0 255.255.255.0
object network management
subnet 10.99.1.0 255.255.255.0
object network workstations
subnet 10.3.1.0 255.255.255.0
access-list outside_access_in extended permit ip any any
pager lines 24
mtu vlan6 1500
mtu vlan4 1500
mtu vlan99 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network core-servers
nat (vlan6,outside) dynamic interface
object network dist-servers
nat (vlan4,outside) dynamic interface
object network management
nat (vlan99,outside) dynamic interface
access-group outside_access_in global
route outside 0.0.0.0 0.0.0.0 172.17.0.3 1
route outside 10.3.1.0 255.255.255.0 172.17.0.3 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 10.99.1.0 255.255.255.0 vlan99
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh 10.99.1.0 255.255.255.0 vlan99
ssh timeout 10
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:9eae54d930f
: end
SW_INT Configuration
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname SW_INT
!
boot-start-marker
boot-end-marker
!
no aaa new-model
memory-size iomem 5
no ip routing
no ip icmp rate-limit unreachable
no ip cef
!
no ip domain lookup
!
multilink bundle-name authenticated
!
vtp mode transparent
archive
log config
hidekeys
!
vlan 3-4,6,99
!
ip tcp synwait-time 5
ip ssh version 1
!
interface FastEthernet0/0
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
switchport access vlan 6
duplex full
speed 100
!
interface FastEthernet1/4
switchport access vlan 4
duplex full
speed 100
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
switchport access vlan 99
duplex full
speed 100
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
!
interface FastEthernet1/15
switchport mode trunk
!
interface Vlan1
no ip address
no ip route-cache
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
no cdp log mismatch duplex
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
end
I have full connectivity between all areas of the network except the Workstation (10.3.1.50) cannot ping to any of the internal servers (Domain Controller, Syslog, SQL, etc). However, when issuing pings from the internal servers to the Workstation, all of them succeed. All of the OS Firewalls have been disabled no I am pretty sure that is not causing the problem. Any help or suggestions would be greatly appreciated.

Successful ping from Domain Controller (10.3.2.4) to Workstation (10.3.1.50)
http://s30.postimg.org/u5p5077xd/dcping.jpg
Failed ping from Workstation (10.3.1.50) to Domain Controller (10.3.2.4)
[img]http://s12.postimg.org/5vs7hddal/pingfail.jpg[/img]
ASA1 Configuration
ASA Version 8.4(2)
!
hostname ASA
enable password
!
interface GigabitEthernet0
nameif workstations
security-level 100
ip address 10.3.1.2 255.255.255.0
!
interface GigabitEthernet1
nameif outside
security-level 100
ip address 172.1.0.3 255.255.255.0
!
interface GigabitEthernet2
nameif DMZ
security-level 100
ip address 10.4.2.3 255.255.255.0
!
interface GigabitEthernet3
nameif inside
security-level 100
ip address 172.17.0.3 255.255.255.0
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network dmz-net
subnet 10.4.2.0 255.255.255.0
object network workstations
subnet 10.3.1.0 255.255.255.0
object network internal-out
subnet 172.17.0.0 255.255.255.0
access-list outside_access_in extended permit ip any any
pager lines 24
mtu workstations 1500
mtu outside 1500
mtu DMZ 1500
mtu inside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network dmz-net
nat (DMZ,outside) dynamic interface
object network workstations
nat (workstations,outside) dynamic interface
object network internal-out
nat (inside,outside) dynamic interface
access-group outside_access_in global
route outside 0.0.0.0 0.0.0.0 172.1.0.2 1
route outside 10.3.2.0 255.255.255.0 172.17.0.2 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh timeout 10
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
SW1 Configuration
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname VLAN_SW1
!
boot-start-marker
boot-end-marker
!
no aaa new-model
memory-size iomem 5
no ip routing
no ip icmp rate-limit unreachable
no ip cef
!
no ip domain lookup
!
multilink bundle-name authenticated
!
vtp mode transparent
archive
log config
hidekeys
!
vlan 3,6,99
!
ip tcp synwait-time 5
ip ssh version 1
!
interface FastEthernet0/0
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
switchport mode trunk
speed 100
!
interface FastEthernet1/4
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
switchport mode trunk
speed 100
!
interface FastEthernet1/15
switchport mode trunk
speed 100
!
interface Vlan1
no ip address
no ip route-cache
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 172.17.0.3
!
no ip http server
no ip http secure-server
!
no cdp log mismatch duplex
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
end
ASA2 Configuration
ASA Version 8.4(2)
!
hostname ASA2
!
interface GigabitEthernet0
no nameif
no security-level
no ip address
!
interface GigabitEthernet0.1
vlan 6
nameif vlan6
security-level 100
ip address 10.3.2.2 255.255.255.0
!
interface GigabitEthernet0.2
vlan 4
nameif vlan4
security-level 100
ip address 10.4.1.2 255.255.255.0
!
interface GigabitEthernet0.3
vlan 99
nameif vlan99
security-level 100
ip address 10.99.1.2 255.255.255.0
!
interface GigabitEthernet1
nameif outside
security-level 100
ip address 172.17.0.2 255.255.255.0
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
same-security-traffic permit inter-interface
same-security-traffic permit intra-interface
object network core-servers
subnet 10.3.2.0 255.255.255.0
object network dist-servers
subnet 10.4.1.0 255.255.255.0
object network management
subnet 10.99.1.0 255.255.255.0
object network workstations
subnet 10.3.1.0 255.255.255.0
access-list outside_access_in extended permit ip any any
pager lines 24
mtu vlan6 1500
mtu vlan4 1500
mtu vlan99 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network core-servers
nat (vlan6,outside) dynamic interface
object network dist-servers
nat (vlan4,outside) dynamic interface
object network management
nat (vlan99,outside) dynamic interface
access-group outside_access_in global
route outside 0.0.0.0 0.0.0.0 172.17.0.3 1
route outside 10.3.1.0 255.255.255.0 172.17.0.3 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-reco
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
http server enable
http 10.99.1.0 255.255.255.0 vlan99
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh 10.99.1.0 255.255.255.0 vlan99
ssh timeout 10
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:9eae54d930f
: end
SW_INT Configuration
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname SW_INT
!
boot-start-marker
boot-end-marker
!
no aaa new-model
memory-size iomem 5
no ip routing
no ip icmp rate-limit unreachable
no ip cef
!
no ip domain lookup
!
multilink bundle-name authenticated
!
vtp mode transparent
archive
log config
hidekeys
!
vlan 3-4,6,99
!
ip tcp synwait-time 5
ip ssh version 1
!
interface FastEthernet0/0
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet0/1
no ip address
no ip route-cache
shutdown
duplex auto
speed auto
!
interface FastEthernet1/0
!
interface FastEthernet1/1
!
interface FastEthernet1/2
!
interface FastEthernet1/3
switchport access vlan 6
duplex full
speed 100
!
interface FastEthernet1/4
switchport access vlan 4
duplex full
speed 100
!
interface FastEthernet1/5
!
interface FastEthernet1/6
!
interface FastEthernet1/7
!
interface FastEthernet1/8
!
interface FastEthernet1/9
switchport access vlan 99
duplex full
speed 100
!
interface FastEthernet1/10
!
interface FastEthernet1/11
!
interface FastEthernet1/12
!
interface FastEthernet1/13
!
interface FastEthernet1/14
!
interface FastEthernet1/15
switchport mode trunk
!
interface Vlan1
no ip address
no ip route-cache
!
ip forward-protocol nd
!
!
no ip http server
no ip http secure-server
!
no cdp log mismatch duplex
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
end
ASKER
Thank you for your response.
I have applied the following access-lists to the inside interface (vlan6) and am still not able to ping from Workstation(10.3.1.50) to Domain Controller (10.3.2.4). I am able to ping from Workstation to ASA2 outside interface (172.17.02) so I know that it is at least reaching the ASA2.
ASA2
access-list workstations_icmp extended permit icmp any any
access-group workstations_imcp in interface vlan6
What has me really confused is that I can ping from the Web Server to the Workstation through ASA1 without any problems. This is essentially the same direction (from side interface down into an internal subinterface). In the ASA1 configuration, the only access-list that I have applied is the following:
access-list outside_access_in extended permit ip any any
access-group outside_access_in global
With this access list on ASA1 I am able to ping through both directions, yet I have the same exact access list on ASA2 but can only ping from internal to external systems.
I have applied the following access-lists to the inside interface (vlan6) and am still not able to ping from Workstation(10.3.1.50) to Domain Controller (10.3.2.4). I am able to ping from Workstation to ASA2 outside interface (172.17.02) so I know that it is at least reaching the ASA2.
ASA2
access-list workstations_icmp extended permit icmp any any
access-group workstations_imcp in interface vlan6
What has me really confused is that I can ping from the Web Server to the Workstation through ASA1 without any problems. This is essentially the same direction (from side interface down into an internal subinterface). In the ASA1 configuration, the only access-list that I have applied is the following:
access-list outside_access_in extended permit ip any any
access-group outside_access_in global
With this access list on ASA1 I am able to ping through both directions, yet I have the same exact access list on ASA2 but can only ping from internal to external systems.
you cannot ping internal to internal on ASA2? have you verified that the workstations are not blocking ICMP with [Windows] firewall?
ASKER
I am able to ping internal to internal (ex: between SQL and DC) in both directions. Also, each of the internal systems on ASA2 can reach the workstation but the workstation can't reach any of them. I have also verified numerous times that none of the Windows firewalls are turned on.
pinging internally to internally should just work. have you tried wireshark on workstation to see if the packets are reaching it?
ASKER
When looking at the packets on wireshark, there is no traffic sourced from 10.3.1.50 that reaches the link between ASA2 interface g0.1 and the Domain Controller when pinging the Domain Controller from the Workstation. The Workstation can reach ASA interface g1 just fine when pinging so I'm thinking the problem has to be related to the transfer between ASA2 g1 and ASA2 g0.1.
ASKER
To attempt to isolate the problem further, I switched out the SW1 with a standard SW that is not configurable (to eliminate all vlans) and moved the Domain controller from behind SW_INT to ASA2 g3. After configuring the ASA2 g3 to the same ip and nat config as it was previously configured with ASA2 g0.1 I am able to get the same connectivity out from Domain Controller to the Workstation and also to the DMZ. This has led me to believe that the issue is not VLAN related.
Traffic from the Domain Controller and other internal servers is natted to the outside (g1) interface and shows a source of 172.17.0.2 when pinging to the Workstation. Traffic from the Workstation is not natted to the ASA2 so I am wondering if maybe the problem is related to NAT? Also there is no NAT on the traffic in either direction between the Workstation and DMZ. Again, both the Workstation and DMZ can ping eachother but neither can ping internally into the Domain Controller.
I also ran debug icmp on both ASA1 and ASA2 during a failed ping from Workstation (10.3.1.50) to Domain(10.3.2.4)
ASA1

ASA2

Traffic from the Domain Controller and other internal servers is natted to the outside (g1) interface and shows a source of 172.17.0.2 when pinging to the Workstation. Traffic from the Workstation is not natted to the ASA2 so I am wondering if maybe the problem is related to NAT? Also there is no NAT on the traffic in either direction between the Workstation and DMZ. Again, both the Workstation and DMZ can ping eachother but neither can ping internally into the Domain Controller.
I also ran debug icmp on both ASA1 and ASA2 during a failed ping from Workstation (10.3.1.50) to Domain(10.3.2.4)
ASA1

ASA2

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you for your response. I was able to correct the issue by removing NAT from both of the ASAs and configuring EIGRP to map the correct routes. I now have full connectivity, thank you for your help!
if you want to allow it (and all traffic in is permitted), then you'll need to create and access-list permitting all IP and ICMP and apply it to the inside interface.