Ping ASA firewall Outside interface
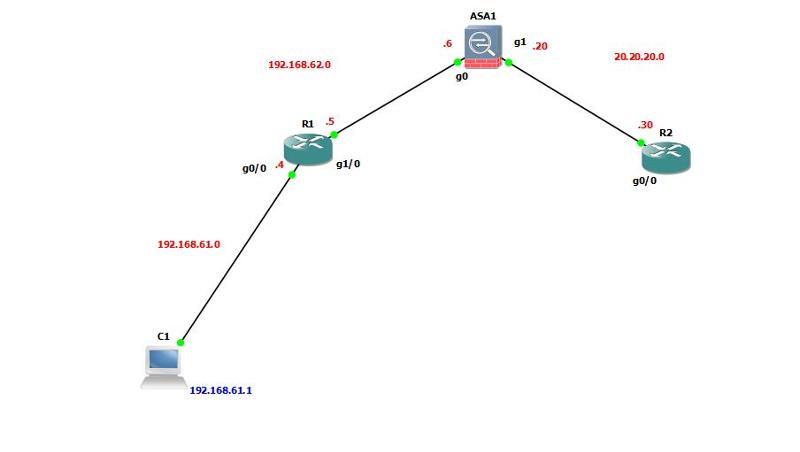
on the topology shown below, I can ping from the computer(192.168.61.1) all the way to inside interface of ASA 192.168.62.6.
However I cannot ping neither from the computer nor from router1 to outside interface of ASA(20.20.20.20)
Anything missing ?
Thank you
below is the routing table of R1 and ASA
However I cannot ping neither from the computer nor from router1 to outside interface of ASA(20.20.20.20)
Anything missing ?
Thank you
below is the routing table of R1 and ASA
R1#sh ip route
Gateway of last resort is 192.168.62.6 to network 0.0.0.0
C 192.168.62.0/24 is directly connected, GigabitEthernet1/0
C 192.168.61.0/24 is directly connected, GigabitEthernet0/0
S* 0.0.0.0/0 [1/0] via 192.168.62.6
R1#ciscoasa# sh route
Gateway of last resort is not set
C 192.168.62.0 255.255.255.0 is directly connected, inside
S 192.168.61.0 255.255.255.0 [1/0] via 192.168.62.5, inside
C 20.20.20.0 255.255.255.0 is directly connected, outsideASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
access-group ACL-OUTSIDE in interface outside
There's no corresponding ACL.
ASKER
There is a line in the code:
access-list ACL-OUTSIDE extended permit icmp any any
access-list ACL-OUTSIDE extended permit icmp any any
Sorry. Not enough caffeine today.
And I also realized you're trying to ping the outside interface of the ASA. That won't work. You should, however, be able to ping 20.20.20.30
And I also realized you're trying to ping the outside interface of the ASA. That won't work. You should, however, be able to ping 20.20.20.30
ASKER
Sorry. Not enough caffeine today.Nap Time...
I cannot ping 20.20.20.30 ...
I have added another ACL, but still cannot ping:
access-list ACL-OUTSIDE extended permit icmp any any
access-list ACL-INSIDE extended permit icmp any any
access-group ACL-INSIDE out interface inside
access-group ACL-OUTSIDE in interface outside
ASKER
I wonder if it needs NAT?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I thought ACL will be enough...
I am not sure how NAT should be configured in this case
I am not sure how NAT should be configured in this case
ASKER
Packet Tracer show ICMP packets allowed but, when I ping from the router I do not get the reply.
I have added loop back on R2 with IP=30.30.30.30 , I can ping it from ASA but cannot ping it from R1
However when I trace( through Packet Tracer) from R1 Gig0/0 interface( facing computer C1) to Loopback interface of R2 (30.30.30.30), it shows Packet allowed.
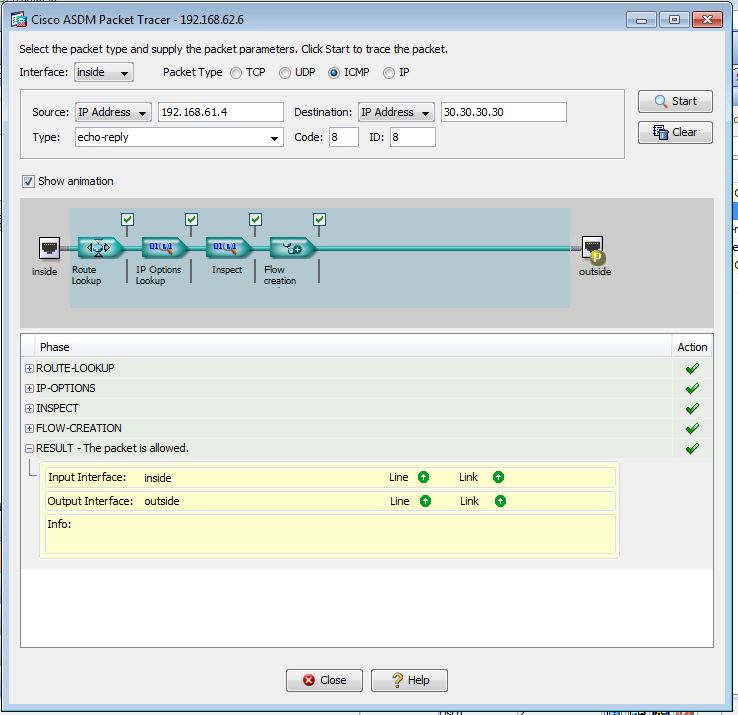
I have added loop back on R2 with IP=30.30.30.30 , I can ping it from ASA but cannot ping it from R1
However when I trace( through Packet Tracer) from R1 Gig0/0 interface( facing computer C1) to Loopback interface of R2 (30.30.30.30), it shows Packet allowed.
Packet Tracer show ICMP packets allowed but, when I ping from the router I do not get the reply.You have two routers. You need to specify which router. And what is the destination?
when I trace (through Packet Tracer) from R1 Gig0/0 interface (facing computer C1) to Loopback interface of R2 (30.30.30.30), it shows Packet allowed.Well that tells you the ASA is allowing the traffic. Which leads me to wonder if R2 has a route to the destination.
Have you tried pinging from the ASA but sourcing the traffic from g0?
ASKER
Don:
I found out the Solution, I had to use NAT and now I can ping from R1 to Loopback of R2
I flowed this link :http://resources.intenseschool.com/cisco-asa-in-gns3-network-connectivity-using-nat-rules/
I found out the Solution, I had to use NAT and now I can ping from R1 to Loopback of R2
R1#ping 30.30.30.30
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 30.30.30.30, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/31/64 ms
R1#I flowed this link :http://resources.intenseschool.com/cisco-asa-in-gns3-network-connectivity-using-nat-rules/
Good job!
ASKER
Just for whoever is running with the same issue:
in addition to using NAT , I had to enable ICMP inspection.
Both NAT and ICMP inspection were done through ASDM.
Below is full configuration of ASA for my Scenario :
in addition to using NAT , I had to enable ICMP inspection.
Both NAT and ICMP inspection were done through ASDM.
Below is full configuration of ASA for my Scenario :
ciscoasa(config)# sh run
: Saved
:
ASA Version 8.4(2)
!
hostname ciscoasa
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif inside
security-level 100
ip address 192.168.62.6 255.255.255.0
!
interface GigabitEthernet1
nameif outside
security-level 0
ip address 20.20.20.20 255.255.255.0
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
object network Inside-Network
subnet 192.168.62.0 255.255.255.0
pager lines 24
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
!
object network Inside-Network
nat (any,outside) dynamic interface
route outside 30.30.30.0 255.255.255.0 20.20.20.30 5
route inside 192.168.61.0 255.255.255.0 192.168.62.5 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
http server enable
http 192.168.61.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
webvpn
username cisco password 3USUcOPFUiMCO4Jk encrypted
!
class-map global-class
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global-policy
class global-class
inspect icmp
!
service-policy global-policy global
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:bfd051876e39938fe3ea3277e3d76877
: endASKER
Thank you Guys!!
ASKER
Open in new window