when installing applications does windows store who the identity of the user who instlled it?
Hi
In a scenario where admin rights are required to install software and the user has no admin rights, a user with the rights can right click on the setup and select 'run as a different user'... which allows you to install the application using another identity.
Is it possible to check who installed the said application? If so, how?
Thanks
In a scenario where admin rights are required to install software and the user has no admin rights, a user with the rights can right click on the setup and select 'run as a different user'... which allows you to install the application using another identity.
Is it possible to check who installed the said application? If so, how?
Thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Your screenshot shows that it knows you installed it? Well, it lists the source of the installer file (which used your temp directory), that's all, it could have been anyone, although this is at least an indicator.
No, softwares usually don't keep track themselves of who installed them. Identifying that will only be possible through installer logging like I showed for windows installer.
This is a security topic, I have looked into that years ago.
No, softwares usually don't keep track themselves of who installed them. Identifying that will only be possible through installer logging like I showed for windows installer.
This is a security topic, I have looked into that years ago.
Point taken. As I noted I do not know exactly where by application.
Here is the setup section for Companionlink that knows me as the owner of the product and I think also as the installer.
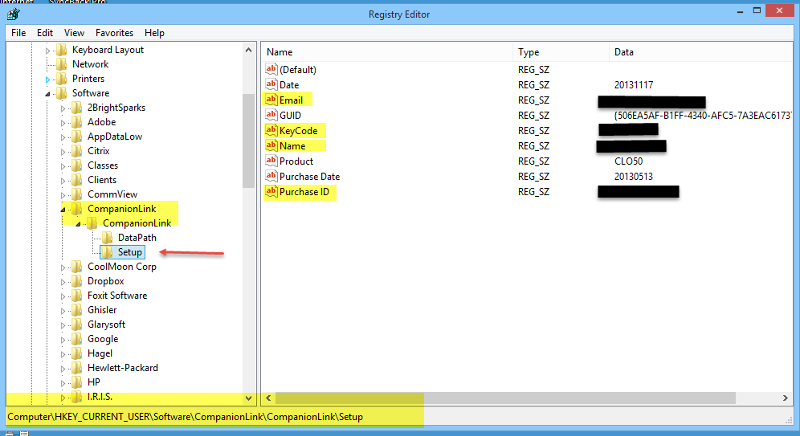
I install stuff in my Windows 7 or Windows 8 userid which is an administrator ID. When I log into Administrator and try to run some software, it barks at me because it needs to be registered again. Not all software but some.
Here is the setup section for Companionlink that knows me as the owner of the product and I think also as the installer.

I install stuff in my Windows 7 or Windows 8 userid which is an administrator ID. When I log into Administrator and try to run some software, it barks at me because it needs to be registered again. Not all software but some.
The info shown is what you provided voluntarily. It was not retrieved by setup programatically, so it cannot be used to find out what user installed something.
Also If I am not mistaken, the question actually means....
If USER A has to use elevated permissions by using RUNAS another user, can I tell what they installed?
The answer to that question is NO. The installer will only know about the elevated user and not about USER A.
If you open a command prompt by doing RUNAS another user, you are in effect logging into windows as that other user and opening a command prompt. It knows nothing of the USER A.
If USER A has to use elevated permissions by using RUNAS another user, can I tell what they installed?
The answer to that question is NO. The installer will only know about the elevated user and not about USER A.
If you open a command prompt by doing RUNAS another user, you are in effect logging into windows as that other user and opening a command prompt. It knows nothing of the USER A.
Right, Neilsr, that was what has been asked.
So the runas impersonation needs to be logged, too - "who impersonated the admin" is the big question. That will be answered by windows security log. The default auditing settings don't log that, I think, at least not on standalone computers.
So enable "audit logon events" in secpol.msc ->local policies ->audit policy
Then, you will find log entries for impersonation events, just search for "impersonation".
But, it's not that easy. If the weak user uses runas.exe, it will be logged, you can easily see that it was weakuser who impersonated adminuser. But: If he just starts a setup and the UAC prompts for admin credentials, then it is not the user himself who invokes the impersonation but it is the system account (pcname$), because the UAC prompt is started by the OS itself. So then you will not be able to see directly who impersonates the adminuser. So your solution will be:
Enable the aforementioned logging and look for impersonation events. Then find out who was logged in at the time the impersonation event took place.
So the runas impersonation needs to be logged, too - "who impersonated the admin" is the big question. That will be answered by windows security log. The default auditing settings don't log that, I think, at least not on standalone computers.
So enable "audit logon events" in secpol.msc ->local policies ->audit policy
Then, you will find log entries for impersonation events, just search for "impersonation".
But, it's not that easy. If the weak user uses runas.exe, it will be logged, you can easily see that it was weakuser who impersonated adminuser. But: If he just starts a setup and the UAC prompts for admin credentials, then it is not the user himself who invokes the impersonation but it is the system account (pcname$), because the UAC prompt is started by the OS itself. So then you will not be able to see directly who impersonates the adminuser. So your solution will be:
Enable the aforementioned logging and look for impersonation events. Then find out who was logged in at the time the impersonation event took place.
And that's no use to you unless you are checking the logs all the time or have a
Mechanism for storing the log permanently.
It is no good to you six months time asking "Who installed xyz on that machine?"
Mechanism for storing the log permanently.
It is no good to you six months time asking "Who installed xyz on that machine?"
You don't check the logs manually but setup event triggers. Those trigger tasks that use powershell to filter and send alerts. Try it, works wonderful. Can be deployed via GPO, too.
ASKER
thanks ;o)
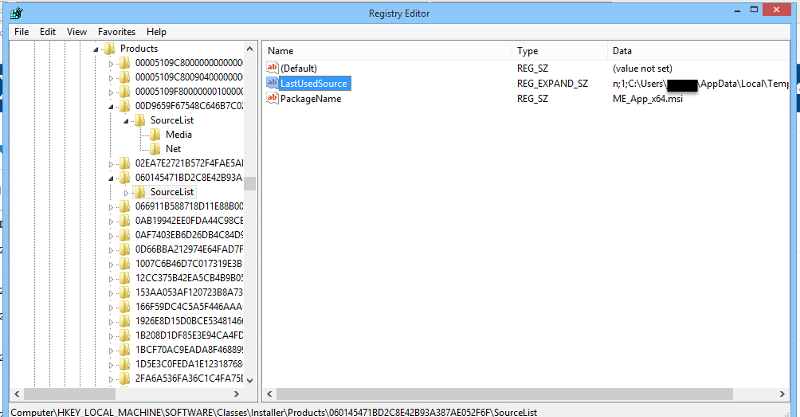
Other software I have know the installer and the user.
I am not sure how you can find it (the values are probably all over the registry).