Backdoor Trojan? Calling Russia constantly.
Hi experts,
I am not one to open attachments, and I didn't. I don't hang around in obviously infected websites. But, during a flurry of Google searches and research on carbon monoxide detectors and meters,
I run ESET Business Edition on my computer for Real Time scanning and weekly scans. It also, obviously, detects malware as they occur, although it didn't detect this. I just happened to have MBAM running (not doing any real time scanning or scheduled scanning -- just there).
It started blocking multiple attempts to access the Internet to sites which were in Russia. I disconnected it from the network and ran MBAM, SAS and ESET scans, all of which only found PUPs.
I have not tried any root kit scans. I am not sure what to do next. This is Win 7 Pro on a domain run by SBS 2008.
Any help would be appreciated.
Bert

I am not one to open attachments, and I didn't. I don't hang around in obviously infected websites. But, during a flurry of Google searches and research on carbon monoxide detectors and meters,
I run ESET Business Edition on my computer for Real Time scanning and weekly scans. It also, obviously, detects malware as they occur, although it didn't detect this. I just happened to have MBAM running (not doing any real time scanning or scheduled scanning -- just there).
It started blocking multiple attempts to access the Internet to sites which were in Russia. I disconnected it from the network and ran MBAM, SAS and ESET scans, all of which only found PUPs.
I have not tried any root kit scans. I am not sure what to do next. This is Win 7 Pro on a domain run by SBS 2008.
Any help would be appreciated.
Bert
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks John and andreas,
Appreciate the quick response. As I do these things, may I be informed of some general information? For instance, I would guess that the computer's Trojan or whatever has tried to reach around four different IP addresses. Given they were blocked, I feel safe. On the other hand, I can't know for sure that MBAM would have stopped all.
During any of these suggestions where I need to download something, should I download it from a non-infected PC and transfer it with a flash drive or something? I mean the longer the malware has to try to find the mothership (if that is the correct term), the more likely it will find it.
If a backdoor is opened on some port, can then the perpetrator place a virus that will be triggered down the road that is undetected? I know the phrase "One infected, always suspected." Ironically, I made an image backup that morning.
Appreciate the quick response. As I do these things, may I be informed of some general information? For instance, I would guess that the computer's Trojan or whatever has tried to reach around four different IP addresses. Given they were blocked, I feel safe. On the other hand, I can't know for sure that MBAM would have stopped all.
During any of these suggestions where I need to download something, should I download it from a non-infected PC and transfer it with a flash drive or something? I mean the longer the malware has to try to find the mothership (if that is the correct term), the more likely it will find it.
If a backdoor is opened on some port, can then the perpetrator place a virus that will be triggered down the road that is undetected? I know the phrase "One infected, always suspected." Ironically, I made an image backup that morning.
You should be quite safe download Process Explorer to the problem PC. It is a simple program and just runs (no installation of any consequence).
Keep your image handy in case you need it.
Keep your image handy in case you need it.
ASKER
Thanks. I just meant isn't it safer to keep the "infected PC" isolated from the LAN by disabling the NIC. I guess I am not quite sure what someone in Russia does once they have a backdoor open. Can they take over the computer, then access the server, etc.?
When back doors exist, yes, they can steal information from your computers. So the quicker you act, the better.
ASKER
I have installed the Process Explorer. There are many processes especially when compared to the one that comes with Windows. So, not sure which one I am looking for. They do give descriptions, but my guess is the Russians would have it sound rule.
If the process has a strange name that may be it (alphanumeric). Otherwise look in programs and features for programs you did not install.
Also (less likely) look for an add-in in Internet Explorer.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
It might be cleaned up, but then why would the website attacks continue?
ASKER
Thanks for the feedback. I was waiting a bit, because I ran the MBAM rootkit device. It was kind of weird, because it tried to install and said their was a rootkit (why the hell I didn't write down the name -- started with an "a"). I am sure that is very helpful. Suggested I click on No. But, I installed and ran the scanner. I haven't had an attempt for over two hours.
Unfortunately, I checked and block malicious websites wasn't checked anymore on MBAM. But, I set it back an hour ago and nothing. Now the question I have, and I a rookie at this is the following. If this malware was sending requests to the Russians (another cold war) but kept getting blocked, would it not continue indefinitely? But, if one got through allowing the hacker to open a port for its use, would the malware know enough to stop trying. In other words MBAM's not blocking anything is a good thing -- I mean no attempts are occurring, because the malware is gone or a bad thing if it isn't trying.
I did use Gibson's Research Corporation. Everything looks good except it states that 25, 443 and 987 are open. Those would be SMTP, SSL and SharePoint, correct? I don't know what they would do with this. Are they supposed to appear open. I get very confused with GRC. I mean it is open with https anyway.
Thanks.
Unfortunately, I checked and block malicious websites wasn't checked anymore on MBAM. But, I set it back an hour ago and nothing. Now the question I have, and I a rookie at this is the following. If this malware was sending requests to the Russians (another cold war) but kept getting blocked, would it not continue indefinitely? But, if one got through allowing the hacker to open a port for its use, would the malware know enough to stop trying. In other words MBAM's not blocking anything is a good thing -- I mean no attempts are occurring, because the malware is gone or a bad thing if it isn't trying.
I did use Gibson's Research Corporation. Everything looks good except it states that 25, 443 and 987 are open. Those would be SMTP, SSL and SharePoint, correct? I don't know what they would do with this. Are they supposed to appear open. I get very confused with GRC. I mean it is open with https anyway.
Thanks.
Ports 25 and 995 are mail ports. 987 is for SharePoint it you are using it. 443 is for https which we use. So these are normal and you could be fine now.
ASKER
Thanks John. Yes, you are correct about the ports. But, why does Steve get all bent out of shape when his probes find them open. I suppose you would use port 443 to send packets to a site such as CitiBank. Your router would then accept the reply. So, this would have been the case with GRC as it is HTTPS during the entire connection, but who am I to argue with Steve Gibson.
I don't know why SharePoint's port would always be open. Again, this is info provided by GRC. I can connect to SharePoint from outside the network using SSL, but it is mostly used for internal use hence the term company web.
This is where I falter a bit. Port 3389 which used to be used mainly for RDP is now handled by the server's RD Gateway. Port 3389 was probed many, many times daily so I don't quite get the difference between 3389's risk and 25's risk.
I don't know why SharePoint's port would always be open. Again, this is info provided by GRC. I can connect to SharePoint from outside the network using SSL, but it is mostly used for internal use hence the term company web.
This is where I falter a bit. Port 3389 which used to be used mainly for RDP is now handled by the server's RD Gateway. Port 3389 was probed many, many times daily so I don't quite get the difference between 3389's risk and 25's risk.
You are correct about 3389. 25 is an unsecured SMTP port for POP3 email.
ASKER
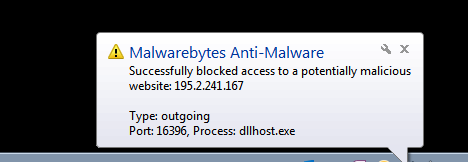
It's interesting, because the log files of MBAM show about ten ports that were used as outgoing with either a dllhost.exe process or wextract.exe process. When I specifically probe them to see if they are open, they are stealthed. Again, according to Steve Gibson.
There isn't much more I can do from here. The ports you are naming are normal. GRC just notes these for your information.
If you want to see traffic in and out, you can use something like Wire Shark (free) or Comm View (paid) which are packet sniffers.
If you want to see traffic in and out, you can use something like Wire Shark (free) or Comm View (paid) which are packet sniffers.
ASKER
Well, I entered and probed every port used by this Trojan. They are all closed. I am assuming that if they were backdoors, they would show as open. I am hoping everything is fine. MBAM (which is not even my main A/V -- I generally use it when I am looking for something) is what stopped everything -- we hope. Of course, maybe it is 5 ms quicker than ESET.
I am going to go with the assumption (I know) that the malicious program is no longer there and not that it worked and no longer needs to do anything.
I am going to keep the question open until at least tomorrow in case something changes.
I am going to go with the assumption (I know) that the malicious program is no longer there and not that it worked and no longer needs to do anything.
I am going to keep the question open until at least tomorrow in case something changes.
I am assuming that if they were backdoors, they would show as open. Probably. Since no more web attack notices, I think you are fine. My earlier responses were geared to the web attack notices. Let us see what tomorrow brings.
Actually there shouldbe no listening ports open. For usage of the web and e-mail we use OUTgoing connections to the servers on those porst. The GRC-Scan detects runing SERVER ports on your IP you are comming from.
But depending on your setup this also can be caused by OTHER users (if you are behind a Carrier Grade NAT, e.g. in Germany on cable networks)
But if you have your OWN public IP then these ports should definitely CLOSEd and not open they should only be open if you RUN a web-server and mailserver.
Port 25 isnt for POP its for SMTP only.
So please check your system including your router again, maybe those ports are opened by your router as it provides web-administration and or mail-services.
Open ports on windows you can see with the command
netstat -an|more
the ports open are labeld with listening. If there is port 25 and the othermentioned ports open, then its your windows box.
If the ports arent shown open they still could be opened by a rootkit, which HIDES the output from netstat.
In this case your should perform a portscan from another device on your network to the machine with the suspected malware.
But depending on your setup this also can be caused by OTHER users (if you are behind a Carrier Grade NAT, e.g. in Germany on cable networks)
But if you have your OWN public IP then these ports should definitely CLOSEd and not open they should only be open if you RUN a web-server and mailserver.
Port 25 isnt for POP its for SMTP only.
So please check your system including your router again, maybe those ports are opened by your router as it provides web-administration and or mail-services.
Open ports on windows you can see with the command
netstat -an|more
the ports open are labeld with listening. If there is port 25 and the othermentioned ports open, then its your windows box.
If the ports arent shown open they still could be opened by a rootkit, which HIDES the output from netstat.
In this case your should perform a portscan from another device on your network to the machine with the suspected malware.
First I did not want to participate, but this has grown a funny thread!
If you have made out a rootkit infection, restore your computer from your last known good image backup. If no image is at hand, backup your data, reinstall and restore your data after making sure that no file infector has worked on those files. There is no room for arguing. Bert is no expert at malware removal, so he is not in the position to try and clean it, nor will it be sufficient to follow the advice of experts (that themselves sometimes seem to be confusing listening ports with ports that your software uses at the remote server).
If you are interested in what infection that is, you should be able to rescan for that rootkit or look at the log of the previous scan. Also, you should be able to locate the executable that your screenshot shows (there is one with the same name belonging to windows, that won't be it). That executable can be uploaded to https://www.virustotal.com/ so that you get an idea of what it probably is.
If you have made out a rootkit infection, restore your computer from your last known good image backup. If no image is at hand, backup your data, reinstall and restore your data after making sure that no file infector has worked on those files. There is no room for arguing. Bert is no expert at malware removal, so he is not in the position to try and clean it, nor will it be sufficient to follow the advice of experts (that themselves sometimes seem to be confusing listening ports with ports that your software uses at the remote server).
If you are interested in what infection that is, you should be able to rescan for that rootkit or look at the log of the previous scan. Also, you should be able to locate the executable that your screenshot shows (there is one with the same name belonging to windows, that won't be it). That executable can be uploaded to https://www.virustotal.com/ so that you get an idea of what it probably is.
ASKER
Thanks McKnife,
You are correct that I am no expert with malware removal or detection. I, too, am confused with the port discussion. I do have Exchange so I guess that would account for SMTP or 25. 443 is open. There I am confused, because I thought you used either 80 (HTTP) or 443 (SSL). I can't account for SharePoint.
I do have a good image.
You are correct that I am no expert with malware removal or detection. I, too, am confused with the port discussion. I do have Exchange so I guess that would account for SMTP or 25. 443 is open. There I am confused, because I thought you used either 80 (HTTP) or 443 (SSL). I can't account for SharePoint.
I do have a good image.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks for waiting. I am doing the image. My issue is I don't always trust restores. It's not that they don't work; I do like the idea that they have all the files that can be mounted, but it seems so easy to just say image, and I get a bit nervous. I'm apologize.
Anyway, continuing to work on it. Christmas and all. By the way, Merry Christmas to everyone or Happy Holidays. Can't remember if I said that.
Anyway, continuing to work on it. Christmas and all. By the way, Merry Christmas to everyone or Happy Holidays. Can't remember if I said that.
ASKER
It would really be nice if you knew the virus was gone. I do think I removed it which is why I gave Gauthier points, albeit small. Prior to finding a root kit and removing it, I was getting calls to the Internet nearly every minute. After none. But, who's to say that didn't mean a different call to a different server using a different IP wasn't successful. Or maybe once it succeeded, it was programmed to stop trying other IP addresses.
As to the restore, it was fun as usual. I was kind of fortunate as I was planning on cloning my 250 GB Samsung SSD to a 1 TB one. So, I removed the SSD with the possible virus and installed the 1 TB SSD. I then tried to restore the image to the new SSD, and it continued to have errors and stop. So, I thought that maybe it needed to be formatted. I installed a copy of Win 7 Pro to it, then restored to that, and it workeed fine. I have a new image of Windows from laster Saturday. Given this is a client, there are no major changes. The log files of MBAM show nothing resembling a virus or the attempted connections to the Internet.
So, I guess I am in the clear. Is it not possible to do a bare metal restore of an image to a brand new SSD? I did try a deploy to new hardware, which did not work either.
Thanks.
Bert
As to the restore, it was fun as usual. I was kind of fortunate as I was planning on cloning my 250 GB Samsung SSD to a 1 TB one. So, I removed the SSD with the possible virus and installed the 1 TB SSD. I then tried to restore the image to the new SSD, and it continued to have errors and stop. So, I thought that maybe it needed to be formatted. I installed a copy of Win 7 Pro to it, then restored to that, and it workeed fine. I have a new image of Windows from laster Saturday. Given this is a client, there are no major changes. The log files of MBAM show nothing resembling a virus or the attempted connections to the Internet.
So, I guess I am in the clear. Is it not possible to do a bare metal restore of an image to a brand new SSD? I did try a deploy to new hardware, which did not work either.
Thanks.
Bert
Thank you, and I do hope you are clear. I keep myself behind a VPN hardware firewall and also a software firewall, so Russia never calls (thankfully).
ASKER
I am behind a Cisco and Windows firewall, but when what looks like a perfectly good website installs a Trojan, all ports going out are open by default. Personally, I think MBAM stopped all attempts.
but when what looks like a perfectly good website installs a Trojan, all ports going out are open by default
That is why we must always keep our guard up. Socially engineered website snare a lot of victims.
That is why we must always keep our guard up. Socially engineered website snare a lot of victims.
You also could remove the HDD hook it up to another PC and scan it there, but remember, that access to some folders may fail due tu NTFS ACLS and ownerships that arent matching. Chaganging those so that they will give access is posible but might damage your system or make the ACLs less restrictive.
So best is to scan from an anti-virus boot cd. Or boot a live linux CD setup a sambs-share export the whole HDD and scan that share from another PC. This is slow as its running over the LAN but the scanner might be better than the one on the live CD.