Bandwidth Throttling over Site-to-Site VPN
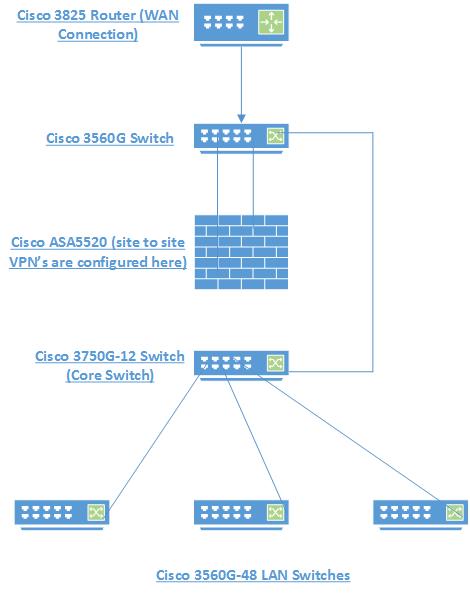
I have two office's, and both offices have a 100M internet circuit. The topology of both networks are identical, and I attached a network diagram. I want to use 50M of each circuit for transferring some SQL backups from office 1 to office 2. These two offices do have a site to site VPN configured between them on the ASA5520's. How would I limit the VPN traffic between these two sites to ensure I never went over 50M when transferring these SQL backups ? Would these be done on the ASA or my Cisco Router that connects to the ISP? Thanks.

ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks. Sorry I didn't reply sooner, I've been pulled away working on other things. So I would configure rate-limiting on both sides on the ASA firewalls correct? What I wasn't sure about, was if I should configure rate limiting on the 3750-12G, which is my core switch and has all VLANs configure on. In my diagram above, where you see the three 3560G-48 LAN switches, one of those is on VLAN 30. VLAN 30 traffic is where the SQL dumps are, that will be transferred over the VPN to the other location. Do I need to configure rate-limiting here as well, or just the ASA?
Just the ASA on both sides :)
Completely off topic, but there is absolutely no redundancy with single point of failures on every link in your network!
Have a read of this
http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Campus/campover.html
Have a read of this
http://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Campus/campover.html
ASKER
skipskip - Yes your comment was completely off topic. Thanks for pointing out the obvious:) It was designed like this on purpose, and there are procedures in place for link failure. If zero downtime was absolute critical at these locations, well a different design approach would of been taken. Please stay on topic next time.
ASKER
Thanks. This was the solution I used.
I believe policing will be the option you want (to ensure that the VPN pipe never exceeds a certain amount of BW).
Check this out:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa82/configuration/guide/config/conns_qos.html