Cannot Sign into Lync 2010
in my LAB, I have installed Lync 2010 on Windows 2012 R2. I have added and enabled a domain user in Lync Control Panel.
I do not have Exchange server installed in my LAB, but the user email address field in AD is test@test.local
I installed Link client in windows 7, but when I sign in as test@test.local , or as any other domain user that I have enabled on Lync control panel, I get the message shown below:
Any help will be very much appreciated.
Thank you
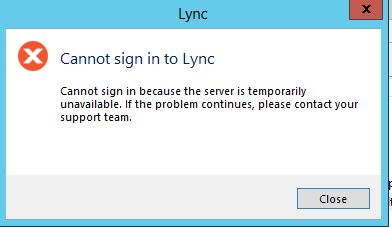 ==========================
==========================
I have added sip.Test.local "A" record in DNS. Now I am getting different message, the one shown below:
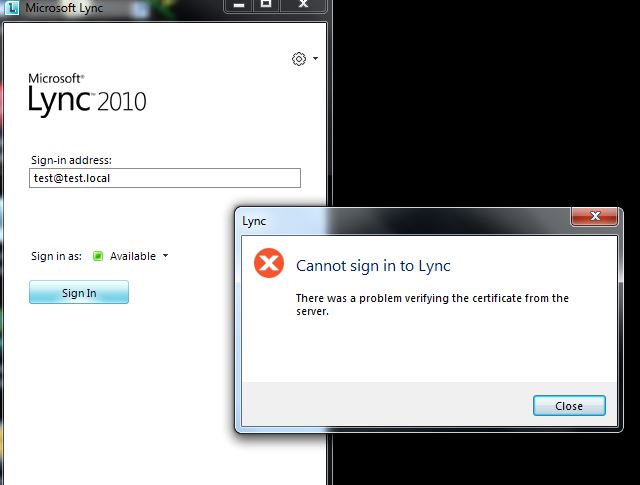
I do not have Exchange server installed in my LAB, but the user email address field in AD is test@test.local
I installed Link client in windows 7, but when I sign in as test@test.local , or as any other domain user that I have enabled on Lync control panel, I get the message shown below:
Any help will be very much appreciated.
Thank you
I have added sip.Test.local "A" record in DNS. Now I am getting different message, the one shown below:
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
You need to export the CA certificate from your certification authority server and added to your client PC. It seems the client you're using is not domain joined so Lync will not trust the connection to it.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Md. Mojahid
You are correct.. I have installed Windows Certificate in Lync Server, then exported it to a file, then from each client I imported the Certificate to "Trusted Root Certificates Authorities" store.
If you import it to personal store it will not work. in my case in Lync Server as well as in Lync Clients the certificate is in
"Trusted Root Certificates Authorities" store.
It Worked ...and users can sign in to Lync now...
However, everything was done manual. In real world how does the certificate got copied to each windows client ?
I know that it is something that can be done through GPO or a Script...I am trying to find if there is a way doing that without resorting to GPO or Script.
Any idea ??
You are correct.. I have installed Windows Certificate in Lync Server, then exported it to a file, then from each client I imported the Certificate to "Trusted Root Certificates Authorities" store.
If you import it to personal store it will not work. in my case in Lync Server as well as in Lync Clients the certificate is in
"Trusted Root Certificates Authorities" store.
It Worked ...and users can sign in to Lync now...
However, everything was done manual. In real world how does the certificate got copied to each windows client ?
I know that it is something that can be done through GPO or a Script...I am trying to find if there is a way doing that without resorting to GPO or Script.
Any idea ??
No, Normally in corporations users are joined to the domain which Lync is part of and that installs all the required "internal" certificates for Lync.
In other scenarios which Lync is connected from personal laptops or externally. Lync can be configured to use public DNS to connect directly to the Edge server instead of Front end but you will need to have 3rd party Public certificate installed on Edge server and all firewall rules related to the Edge must be configured too.
In other scenarios which Lync is connected from personal laptops or externally. Lync can be configured to use public DNS to connect directly to the Edge server instead of Front end but you will need to have 3rd party Public certificate installed on Edge server and all firewall rules related to the Edge must be configured too.
ASKER
Mohammed Hamada
In my LAB I have windows domain and Lync Server as well as Lync clients are all members of the domain, but I still had to export and import the certificate file from Lync server to Lync clients to get it to work...
In my LAB I have windows domain and Lync Server as well as Lync clients are all members of the domain, but I still had to export and import the certificate file from Lync server to Lync clients to get it to work...
It might be the Certification Authority you're using is not in the domain controller itself. How did you deploy Lync server?
ASKER
On Lync Server which is member of the domain, I followed the step by step from this Link:
http://careexchange.in/how-to-install-certificate-authority-on-windows-server-2012/
http://careexchange.in/how-to-install-certificate-authority-on-windows-server-2012/
If you don't have the CA deployed before the client was joined to the domain it won't push the CA certificate to the clients unless you used GPO to do so. if the CA was deployed and you joined the client to the domain it will automatically take the certification authority on the client and you shouldn't have any issue connecting Lync client.
From what you're saying I think you have deployed the CA while deploying Lync so at that time i'm assuming that Client was already joined to the domain and therefore didn't get the CA certificate.
Anyway, Deploying CA using GPO is not that difficult really.. all you have to do is add the CA to the GPO, run Gpoupdate /force command and restart clients. once restart they'll get the new CA.
I will publish an article on my website on how to do so this weekend.
www.moh10ly.com
From what you're saying I think you have deployed the CA while deploying Lync so at that time i'm assuming that Client was already joined to the domain and therefore didn't get the CA certificate.
Anyway, Deploying CA using GPO is not that difficult really.. all you have to do is add the CA to the GPO, run Gpoupdate /force command and restart clients. once restart they'll get the new CA.
I will publish an article on my website on how to do so this weekend.
www.moh10ly.com
ASKER
--- What if I join Disjoin the client from the domain the rejoin it back to the domain.
---I also want to know the way I installed CA following this link : http://careexchange.in/how-to-install-certificate-authority-on-windows-server-2012/
if it is correct ?
I have seen examples of deploying CA in windows domain, and they each looked different
---I also want to know the way I installed CA following this link : http://careexchange.in/how-to-install-certificate-authority-on-windows-server-2012/
if it is correct ?
I have seen examples of deploying CA in windows domain, and they each looked different
-- Probably if you disjoin the client and rejoin it it'll get the certificate.
--- The link you posted is correct however, I'd really choose standalone CA not Enterprise for your scenario. See this snapshot
http://careexchange.in/wp-content/uploads/2012/11/image_thumb136.png
--- The link you posted is correct however, I'd really choose standalone CA not Enterprise for your scenario. See this snapshot
http://careexchange.in/wp-content/uploads/2012/11/image_thumb136.png
ASKER
That's correct..........in Windows 7 I removed the certificates from "Trusted Root Certificates Authorities" store, then Disjoined Windows 7 from the domain, I rebooted the computer then rejoined the computer to the domain then rebooted it... I managed to sign in to Lync 2010 successfully, then checked Certificates MMC and saw the certificate in Trusted Root Certificates Authorities
So it worked...which is perfect....I am just wondering in real world when you install CA in windows domain, whether you will have to disjoin all your PCs and Rejoin them to the domain or there is an easier way to accomplish this ???
Thanks
So it worked...which is perfect....I am just wondering in real world when you install CA in windows domain, whether you will have to disjoin all your PCs and Rejoin them to the domain or there is an easier way to accomplish this ???
Thanks
As I said if you have CA deployed already before the clients were joined to the domain and that this same CA was used to request and install the Certificates for Lync server then you wont have to do anything for the clients side. they will already have the CA certificate installed and all you need to do is just login.
No other configurations needed.
No other configurations needed.
ASKER
Mohammed Hamada
I understand what you are saying.
What I am trying to understand is , most of the environments they already have the domain and clients joined to the domain. Then later , they decide to use Certificates for a specific purpose.in our case it's for Lync purpose.
I do not think they will have to go to each PC disjoin/rejoin it to the domain, jus to make the Lync client able to sign in.
Though, at the first place, I am not sure why Lync client even requires Certificate if its usage is only internal(between domain users)
I understand what you are saying.
What I am trying to understand is , most of the environments they already have the domain and clients joined to the domain. Then later , they decide to use Certificates for a specific purpose.in our case it's for Lync purpose.
I do not think they will have to go to each PC disjoin/rejoin it to the domain, jus to make the Lync client able to sign in.
Though, at the first place, I am not sure why Lync client even requires Certificate if its usage is only internal(between domain users)
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Excellent !!! well explained....