Remote Desktop Farm - .local domain, Certificate issues
I have a 2012 R2 Remote Desktop Services farm configured. There are 4 Terminal servers, and they are load balanced. TS1, TS2, TS3, TS4.
TS1 is also the broker for the farm. This is a .local domain, so I cannot use a third party root CA for a certificate.
The issue: When I RDP to the collection name, "farm1.domain.local", it throws an untrusted certificate warning. I have installed Active Directory Cert Services, and set up my own CA.
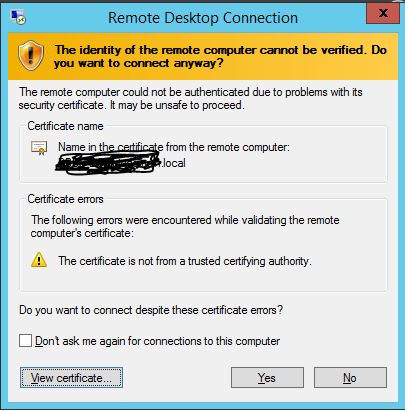
I need specific steps to create and install the proper certificates to make this farm function properly. I can't simply check the box that says, " Don't ask me again"
What I have tried, is exporting the certificate of each terminal server, and then using Group Policy to add it to the Trusted Root certificate authority, the problem is, then when users RDP to farm.domain.local, is says, certificate mismatch error, it says you are connecting to "farm1.domain.local", but the certificate shows "TS1.domain.local"
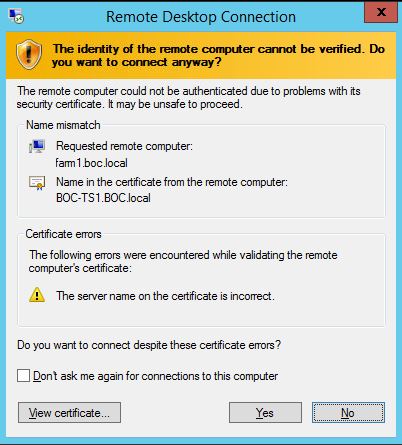
Users will connect mainly locally to the the farm1.domain.local, however, users may remote via the rdp gateway at some point to access the server. I am not sure how this will play a part yet.
Please see the screenshots attached, I have goggled this for days. Can anyone tell me the right way to do this? I need specific instruction on how to generate the certs, and where/how to install them.
Thanks!
TS1 is also the broker for the farm. This is a .local domain, so I cannot use a third party root CA for a certificate.
The issue: When I RDP to the collection name, "farm1.domain.local", it throws an untrusted certificate warning. I have installed Active Directory Cert Services, and set up my own CA.
I need specific steps to create and install the proper certificates to make this farm function properly. I can't simply check the box that says, " Don't ask me again"
What I have tried, is exporting the certificate of each terminal server, and then using Group Policy to add it to the Trusted Root certificate authority, the problem is, then when users RDP to farm.domain.local, is says, certificate mismatch error, it says you are connecting to "farm1.domain.local", but the certificate shows "TS1.domain.local"
Users will connect mainly locally to the the farm1.domain.local, however, users may remote via the rdp gateway at some point to access the server. I am not sure how this will play a part yet.
Please see the screenshots attached, I have goggled this for days. Can anyone tell me the right way to do this? I need specific instruction on how to generate the certs, and where/how to install them.
Thanks!
ASKER
Learnctx - Couple of questions -
Do I need to use the computer template on my internal CA to publish this template?
Do I create a certificate on each terminal server, and which store does it go in, personal or trusted root? Will clients trust the cert if it's just in the terminal servers cert snap in? or do I have to push this out to client computers too somehow?
Do I create a certificate on teach terminal server with the DNS name and CN name Farm1.boc.local, or do I need to somehow create 1 certificate with all the servers listed in the certificate and the farm1.boc.local ?
How do I get the
Do I need to use the computer template on my internal CA to publish this template?
Do I create a certificate on each terminal server, and which store does it go in, personal or trusted root? Will clients trust the cert if it's just in the terminal servers cert snap in? or do I have to push this out to client computers too somehow?
Do I create a certificate on teach terminal server with the DNS name and CN name Farm1.boc.local, or do I need to somehow create 1 certificate with all the servers listed in the certificate and the farm1.boc.local ?
How do I get the
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SAN:DNS=boc-ts1.boc.local&
You can also add the short names or IP addresses as well.
SAN:DNS=boc-ts1.boc.local&
This will generate a certificate which will validate for both DNS names.
See http://blogs.technet.com/b/askperf/archive/2014/01/24/certificate-requirements-for-windows-2008-r2-and-windows-2012-remote-desktop-services.aspx.
http://blogs.technet.com/b/isablog/archive/2011/10/09/how-to-generate-a-certificate-with-subject-alternative-names-san.aspx