Fix Certificate Errors once and for all in a straightforward manner?
I do understand the purpose of certificates. But there are times when they make no sense.
For example, if I intend to access my own router or firewall using https or a service on my own workstation, then I have a pretty good idea what I'm communicating with. But, yet, I get certificate errors.
Yes, I can ignore them but then some of my scanning software will still generate "vulnerabilities".
How can one get rid of these errors when it's warranted?
For example, if I intend to access my own router or firewall using https or a service on my own workstation, then I have a pretty good idea what I'm communicating with. But, yet, I get certificate errors.
Yes, I can ignore them but then some of my scanning software will still generate "vulnerabilities".
How can one get rid of these errors when it's warranted?
ASKER
OK. Access an RV042 using SSL. You get a certificate error.
I don't know how to fix that.....
I don't know how to fix that.....
Ok so this sounds like you are saying the router is responding with it's own certificate instead of the certificate on the endpoint ?
If so you might want to give the cisco forums a quick check, for some people they switched off https access to the router and that stopped the router from handing out the wrong certificate.
It would take a much clearer look at what exactly you are facing to help you to resolve this.
Some more details, such as what you are trying to access and if it is that you are getting the router certificate and not the endpoint certificate etc would help.
If so you might want to give the cisco forums a quick check, for some people they switched off https access to the router and that stopped the router from handing out the wrong certificate.
It would take a much clearer look at what exactly you are facing to help you to resolve this.
Some more details, such as what you are trying to access and if it is that you are getting the router certificate and not the endpoint certificate etc would help.
ASKER
ASKER
I just learned something new about the RV042. There's an obscure place where one can generate a new certificate.
It's located in VPN/VPN Client Access and I've read that it can be used for HTTPS.
Well, I've succeeded in creating a new certificate and I can see that the dates are current on it.
But, now I don't know what to do with it if I'm going to avoid the "problem" described.
I've exported it onto a client computer.
I've changed the exported file extension from .zip (which seems to not really be .zip as 7zip doesn't recognize it) and changed the extension (as suggested by others) to various things but none seem to work to Import the Certificate into Internet Explorer as an example.
I'd really be looking for instructions re: how to do this. I've found precious little information.
It's located in VPN/VPN Client Access and I've read that it can be used for HTTPS.
Well, I've succeeded in creating a new certificate and I can see that the dates are current on it.
But, now I don't know what to do with it if I'm going to avoid the "problem" described.
I've exported it onto a client computer.
I've changed the exported file extension from .zip (which seems to not really be .zip as 7zip doesn't recognize it) and changed the extension (as suggested by others) to various things but none seem to work to Import the Certificate into Internet Explorer as an example.
I'd really be looking for instructions re: how to do this. I've found precious little information.
Hi Fred,
This may not be the case in your situation but there have been several times when this is caused by the date and time change on your PC.
For instance, on the status bar, far right on your PC where time is displayed, sometimes, the clock is wrong.
Once you set it to current date and time, it solves the certificate issue.
Again, this may not apply to your situation but it is worth a look.
This may not be the case in your situation but there have been several times when this is caused by the date and time change on your PC.
For instance, on the status bar, far right on your PC where time is displayed, sometimes, the clock is wrong.
Once you set it to current date and time, it solves the certificate issue.
Again, this may not apply to your situation but it is worth a look.
Hi Fred-
I work with certificates all of the time and I'm confident that I can help here, or at least explain what's going on. Candidly though, I don't know the RV042 router's internals.
I'm going to tackle the 3 warnings in your screenshot a bit out of order:
There are certificates that have alternate names (Subject Alternative Name - SANs), but its' doubtful that the internal certificate generator on your router will create them. You could PAY for one from a provider or make your own using OpenSSL (which from the sound of things, respectfully, isn't something that you're ready for yet).
And last:
Hope this at least explains things a bit.
I work with certificates all of the time and I'm confident that I can help here, or at least explain what's going on. Candidly though, I don't know the RV042 router's internals.
I'm going to tackle the 3 warnings in your screenshot a bit out of order:
The security certificate presented by this website has expired or is not yet validThat means the certificate has likely passed its expiration date. When you access the router via HTTPS now that you created a new cert, does the new certificate (the non-expired one that you just created) show? I know you still have warnings, but I want to know if the date warning has gone away. If the date warning hasn't gone away, then you (we) need to figure out how to tell the router to use this new certificate
The security certificate presented by this website was issued for a different website's addressWhen you created the new certificate, did it prompt you for a common name, cn, name or anything like that? If so, did you enter? The common name on the certificate MUST match the URl in your web browser (which I can't see in the screenshot). For example, if you're accessing your router internally https://192.168.1.1 the common name must be 192.168.1.1. if you have a host record (or dns record) internally called something like "myrouter" and it points to your internal ip for the rotuer, then https://myrouter/ would be another way to access it, but the certificate's common name must be myrouter. Likewise if you're accessing externally with a public IP address of 1.2.3.4, the common name must be 1.2.3.4. And last if you have your public IP in an external DNS server like myconnection.mydomain.com,
There are certificates that have alternate names (Subject Alternative Name - SANs), but its' doubtful that the internal certificate generator on your router will create them. You could PAY for one from a provider or make your own using OpenSSL (which from the sound of things, respectfully, isn't something that you're ready for yet).
And last:
The security certificate presented by this website was not issued by a trusted certificate authorityThat's right. You need to tell windows that you trust the signer of the certificate (add a certificate authority), in this case a self-signed certificate.
Hope this at least explains things a bit.
And it doesn't sound like the spot you found for creating a new certificate is right - it sounds like that would be the certificate for the VPN, not for HTTPS access to the router settings.
And while I'm thinking about it, here's another way to generate a self-signed certificate if for some reason your router doesn't let you
http://www.mobilefish.com/services/ssl_certificates/ssl_certificates.php
And while I'm thinking about it, here's another way to generate a self-signed certificate if for some reason your router doesn't let you
http://www.mobilefish.com/services/ssl_certificates/ssl_certificates.php
ASKER
The date/time is correct on both the PC and the router.
I know that it doesn't sound like the place to generate a new certificate is the most likely - as it's found in the VPN section of the router interface. Yet, that seems to be the only place and I have read that it does work for HTTPS as I mentioned initially. But, maybe it doesn't.... I'm not sure why they would be different though.
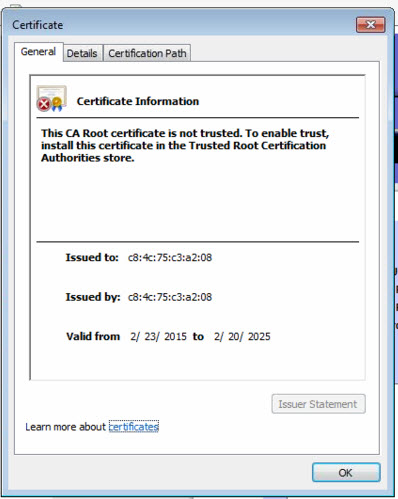
"The browser reports "This CA Root certificate is not trusted. To enable trust, install this certificate in the Trusted Root Certification Authorities store."
When I generate the certificate with the router, that seems to work.
When I export the certificate from the router, the file has a ".pem" extension.
I can import this file into the router as a certificate.
Then, if I move forward to install this certificate in the browser , using this .pem file, in the browser, I don't find that file extension on the list of possible choices.
The Issued to: and the Issued by: contents are the LAN MAC address of the router. (In this case I'm accessing the router via the LAN). I have to wonder if I would allow using the MAC address if it were being accessed from the WAN (i.e. internet) side? After all, MAC addresses can be spoofed.
Here's what I got from someone at Cisco:
1- You are trying to make any browser recognize the Web GUI of the router as a secure site.
2- To accomplish this you were trying to import the VPN certificate (.pem file) into your browser (Firefox)
3- You are concerned about security.
Assuming that the information above is correct, this is what you will need to do:
1- To make sure that every browser will recognize the Web GUI of the router as a secure site, you will need to go to a domain registrar (Certificate Authority) like GoDaddy and purchase a certificate for your router.
2- You will then import this certificate into your router so that when any person using any web browser tries to access it, they will pull the information from the certificate you purchased and will recognized the Web GUI of the router as an actual secure site
3- The .pem file is not a valid certificate for this purpose and, in any case, the certificate wouldn't need to be imported on the browser but on the router first.
**************************
I guess this sounds reasonable enough. But I'm not sure that a self-signed certificate won't do the job and am still trying to figure out how to do that.
I know that it doesn't sound like the place to generate a new certificate is the most likely - as it's found in the VPN section of the router interface. Yet, that seems to be the only place and I have read that it does work for HTTPS as I mentioned initially. But, maybe it doesn't.... I'm not sure why they would be different though.
"The browser reports "This CA Root certificate is not trusted. To enable trust, install this certificate in the Trusted Root Certification Authorities store."
When I generate the certificate with the router, that seems to work.
When I export the certificate from the router, the file has a ".pem" extension.
I can import this file into the router as a certificate.
Then, if I move forward to install this certificate in the browser , using this .pem file, in the browser, I don't find that file extension on the list of possible choices.
The Issued to: and the Issued by: contents are the LAN MAC address of the router. (In this case I'm accessing the router via the LAN). I have to wonder if I would allow using the MAC address if it were being accessed from the WAN (i.e. internet) side? After all, MAC addresses can be spoofed.
Here's what I got from someone at Cisco:
1- You are trying to make any browser recognize the Web GUI of the router as a secure site.
2- To accomplish this you were trying to import the VPN certificate (.pem file) into your browser (Firefox)
3- You are concerned about security.
Assuming that the information above is correct, this is what you will need to do:
1- To make sure that every browser will recognize the Web GUI of the router as a secure site, you will need to go to a domain registrar (Certificate Authority) like GoDaddy and purchase a certificate for your router.
2- You will then import this certificate into your router so that when any person using any web browser tries to access it, they will pull the information from the certificate you purchased and will recognized the Web GUI of the router as an actual secure site
3- The .pem file is not a valid certificate for this purpose and, in any case, the certificate wouldn't need to be imported on the browser but on the router first.
**************************
I guess this sounds reasonable enough. But I'm not sure that a self-signed certificate won't do the job and am still trying to figure out how to do that.
OK, to get the certificate trusted, you need the Certificate Authority (in this case with it self signed, the CA is the certificate itself) imported into the windows computer. Rename the .pem, to a .crt.
You should then be able to double click on it in Windows. You should then get an option to Install. That'll stop the warning about the untrusted Certificate Authority.
Your MAC address doesn't have anything to do with this. As I tried to describe before, if you access the router from the WAN (internet), you'lll need to use your pubic IP address or public hostname. You WILL get a certificate name mismatch warning. There's no way around this unless you put the public ip (or hostname if you have one) in the cert - but then you'll get the warning internally.
You should then be able to double click on it in Windows. You should then get an option to Install. That'll stop the warning about the untrusted Certificate Authority.
Your MAC address doesn't have anything to do with this. As I tried to describe before, if you access the router from the WAN (internet), you'lll need to use your pubic IP address or public hostname. You WILL get a certificate name mismatch warning. There's no way around this unless you put the public ip (or hostname if you have one) in the cert - but then you'll get the warning internally.
ASKER
Renaming the .pem to a .crt doesn't seem to work. Well, of course the change works but the file doesn't work for anything still.
"The file is invalid for use as the following :Security Certificate"
The MAC address is the CN in the certificate that's generated by the router for the LAN side. That's all that it has to do with this discussion. It did seem pertinent.
Thanks for the explanation re: WAN and LAN and the certificate.
In some ways I'd rather see the warning on the LAN side.
This whole adventure was started by trying to clean up penetration test results on the WAN side.
"The file is invalid for use as the following :Security Certificate"
The MAC address is the CN in the certificate that's generated by the router for the LAN side. That's all that it has to do with this discussion. It did seem pertinent.
Thanks for the explanation re: WAN and LAN and the certificate.
In some ways I'd rather see the warning on the LAN side.
This whole adventure was started by trying to clean up penetration test results on the WAN side.
if you rename the pem as .txt, can you open it?
It should look something like this:
You're probably seeing the certificate thumbprint (which can look like a mac address) in the cert FYI.
Food for thought re internal vs external name as CN:
If you use your public IP address, fine, but if you're on a DHCP public network where your public IP can change, you'd need to recreate the certificate every time your IP changes
If you would prefer to use your.domainname.com, that would be ok, but you'd need to make sure that DNS points to the correct IP for that. Another downside is that hackers could see what domain name your router is associated with. Not a big concern, but I'd rather have a little more security through obscurity.
Plus, if you use your internal IP, you'd still get a warning, but just of a CN mismatch. The CA would still be trusted.
It should look something like this:
-----BEGIN CERTIFICATE-----
MIIDPjCCAiag3svv4wIDITFNMA0GCSqGSIb3DQE1BQUAMGIxAjAUBgNVBAMMDUxW
IFNTTCBWUE4gQ0ExCzAJBgNVBAgMAk5KMQswCQYDVQQGEwJVUzEuMCwGA1UECgwl
...................E09vdAsgz5O2u4trCv7bM0qyRiPDQvKKgmNbbC3qUFXzv
9rWdwXRx+JlkfBat6Ds4oizJ4XunkL4TYZuM1111APvMsug+uwqe7WtG0ki3Qj5d
jHI5Qik49fjaijioj94j4k2lkaaR3Y
-----END CERTIFICATE-----You're probably seeing the certificate thumbprint (which can look like a mac address) in the cert FYI.
Food for thought re internal vs external name as CN:
If you use your public IP address, fine, but if you're on a DHCP public network where your public IP can change, you'd need to recreate the certificate every time your IP changes
If you would prefer to use your.domainname.com, that would be ok, but you'd need to make sure that DNS points to the correct IP for that. Another downside is that hackers could see what domain name your router is associated with. Not a big concern, but I'd rather have a little more security through obscurity.
Plus, if you use your internal IP, you'd still get a warning, but just of a CN mismatch. The CA would still be trusted.
ASKER
It's the MAC address all right! Seems a bit strange but that's what it is.
When I change the .pem to .txt, I get something similar that starts with:
-----BEGIN PRIVATE KEY-----
BLAH BLAH BLAH
Then only after that do I see what you've shown
I presume this has to do with the VPN context of it. Does that make sense?
The WANs have static public IPs.
When I change the .pem to .txt, I get something similar that starts with:
-----BEGIN PRIVATE KEY-----
BLAH BLAH BLAH
Then only after that do I see what you've shown
I presume this has to do with the VPN context of it. Does that make sense?
The WANs have static public IPs.
No idea why the mac address would appear. It's not in the subject name is it?
Get rid of the private key part. That's only needed on the router. Save only the bits between and including the begin and end certificate to a crt file. Then open that and install the certificate. If that's the certificate that's used on the router, you shouldn't get the certificate authority warning, which just gets us down to the subject name.
Once you decide on the subject name, it'll create a new self-signed certificate for which you'll need to redo the above process to trust that certificate authority.
If you're given the option to select the length of the certificate, give it a couple years so you don't have to redo this any time soon.
Get rid of the private key part. That's only needed on the router. Save only the bits between and including the begin and end certificate to a crt file. Then open that and install the certificate. If that's the certificate that's used on the router, you shouldn't get the certificate authority warning, which just gets us down to the subject name.
Once you decide on the subject name, it'll create a new self-signed certificate for which you'll need to redo the above process to trust that certificate authority.
If you're given the option to select the length of the certificate, give it a couple years so you don't have to redo this any time soon.
ASKER
Thanks! I did all that and:
"The personal certificate can't be installed because you do not own the corresponding private key which was created when the certificate was requested." (Firefox)
Internet Explorer doesn't provide for importing .crt files at all it appears.
"The personal certificate can't be installed because you do not own the corresponding private key which was created when the certificate was requested." (Firefox)
Internet Explorer doesn't provide for importing .crt files at all it appears.
A couple things:
1) You're NOT importing a personal certificate. Personal certificates are used for you to sign things and need the private key (that's how public / private certificates work). You want to import the certificate, only the public certificate which is what I had you create by removing the private key, as a certification authority or trusted signer. Telling windows/IE and/or Firefox that you trust this certificate to be the issuer of other certificates
2) You don't import the certificate into IE. IE pulls from the windows certificate store. If you double click on a certificate from Windows Explorer (not IE, but the file manager) if should give you the option to install it. You then select the certificate store that you want to import it into, which in this case would be "Trusted Certification Authorities" or something like that.
3) to import into firefox, you need to goto options then, certificates, then click on view certificates. From there, select the authorities tab. Import the crt from there. It won't want the private key - that would be like it asking for one of the commercial certification authorities' private key.
I would suggest that you do a little research of public / private key infrastructure to get an understanding of all of the moving parts.. Here's a pretty good primer: http://searchsecurity.techtarget.com/tip/SSL-A-quick-primer
1) You're NOT importing a personal certificate. Personal certificates are used for you to sign things and need the private key (that's how public / private certificates work). You want to import the certificate, only the public certificate which is what I had you create by removing the private key, as a certification authority or trusted signer. Telling windows/IE and/or Firefox that you trust this certificate to be the issuer of other certificates
2) You don't import the certificate into IE. IE pulls from the windows certificate store. If you double click on a certificate from Windows Explorer (not IE, but the file manager) if should give you the option to install it. You then select the certificate store that you want to import it into, which in this case would be "Trusted Certification Authorities" or something like that.
3) to import into firefox, you need to goto options then, certificates, then click on view certificates. From there, select the authorities tab. Import the crt from there. It won't want the private key - that would be like it asking for one of the commercial certification authorities' private key.
I would suggest that you do a little research of public / private key infrastructure to get an understanding of all of the moving parts.. Here's a pretty good primer: http://searchsecurity.techtarget.com/tip/SSL-A-quick-primer
ASKER
Your instructions are fine and did help a lot.
I've succeeded in installing the certificate in the Windows certificate store it appears.
I'm still stuck with the situation that it's the MAC address instead of the IP address in the certificate it appears.
I don't know how to change that....
I've succeeded in installing the certificate in the Windows certificate store it appears.
I'm still stuck with the situation that it's the MAC address instead of the IP address in the certificate it appears.
I don't know how to change that....
Private message me a URL to check so I can see the certificate? Or post a redacted screenshot here?
ASKER
When you said MAC address, you meant MAC address! This is nuts and will absolutely NEVER work! Shocked that Cisco would generate a certificate like that. It'll never validate against the IP or hostname. Only option to make that work would be to have a subject alternate name.
What about generating your own certiciate using openssl or using the easy to follow http://www.mobilefish.com/services/ssl_certificates/ssl_certificates.php
Then you should be able to import that certificate to the firewall, and trust the issuer (you) with each browser (or WIndows if IE) that you use.
What about generating your own certiciate using openssl or using the easy to follow http://www.mobilefish.com/services/ssl_certificates/ssl_certificates.php
Then you should be able to import that certificate to the firewall, and trust the issuer (you) with each browser (or WIndows if IE) that you use.
ASKER
weinberk: Thank you for sticking with this "adventure"!
I don't want to use the easy on line method and I appreciate the advice to use OpenSSL.
In my case, there isn't going to be a domain name so I will be using an IP address.
OMG! Now I've once more been lured into the Linux world where nothing is "whole" but, rather, built of a sequence of tiny steps (detours) that one would very much like to avoid.
I downloaded the Windows bin files. Here's what I got running the .exe:
CAN’T OPEN CONFIG FILE: /USR/LOCAL/SSL/OPENSSL.CNF
Now, obviously there is no /USR folder on a Windows machine unless we create one. But that wasn't part of the formula.
And, there's no .cnf file to be found either.
Next, instructions that one might dig out for dealing with this issue are (normal Linux fare) sometimes wrong or in the wrong context.
Next, one *can* find an example .cnf file but then is left guessing about what things to change and what things to leave alone. Even the "examples" can't get away from NOT being examples and using "blanks" like: [put your State here] in stead of "Nevada" which would be an actual example. That may sound like a trivial complaint but taken across a file of 100 lines or more really isn't; further a neophyte has to guess that a "name" is where one would put "ipaddress", etc. [That's my best example because at least that's the one I think I understand!] A decision has to be made regarding each line: "Do I change this one or not?"
Then there's the issue of where to put the .cnf file once it's been constructed manually.
Maybe you know of a place that lays it out a bit better for Windows-based work?
I don't want to use the easy on line method and I appreciate the advice to use OpenSSL.
In my case, there isn't going to be a domain name so I will be using an IP address.
OMG! Now I've once more been lured into the Linux world where nothing is "whole" but, rather, built of a sequence of tiny steps (detours) that one would very much like to avoid.
I downloaded the Windows bin files. Here's what I got running the .exe:
CAN’T OPEN CONFIG FILE: /USR/LOCAL/SSL/OPENSSL.CNF
Now, obviously there is no /USR folder on a Windows machine unless we create one. But that wasn't part of the formula.
And, there's no .cnf file to be found either.
Next, instructions that one might dig out for dealing with this issue are (normal Linux fare) sometimes wrong or in the wrong context.
Next, one *can* find an example .cnf file but then is left guessing about what things to change and what things to leave alone. Even the "examples" can't get away from NOT being examples and using "blanks" like: [put your State here] in stead of "Nevada" which would be an actual example. That may sound like a trivial complaint but taken across a file of 100 lines or more really isn't; further a neophyte has to guess that a "name" is where one would put "ipaddress", etc. [That's my best example because at least that's the one I think I understand!] A decision has to be made regarding each line: "Do I change this one or not?"
Then there's the issue of where to put the .cnf file once it's been constructed manually.
Maybe you know of a place that lays it out a bit better for Windows-based work?
Sorry on a long hiatus, it seems you have been getting a lot of very good help here:
From what I am reading you are at the stage where you simply want to import the exported .pem into the trusted root in windows so your browser will load the router interface without certificate errors ?
If so the steps above should do it.
Copy the begin and end certificate portion of the file save as a .crt or .cer file.
Go to run
mmc.exe
add remove snapin
Certificates
Computer account
Local Computer
Expand certificates
Expand Trusted Root Certification Authorities
Right click certificates
All tasks
Import
Point to the cer file you created and that should be it.
From what I am reading you are at the stage where you simply want to import the exported .pem into the trusted root in windows so your browser will load the router interface without certificate errors ?
If so the steps above should do it.
Copy the begin and end certificate portion of the file save as a .crt or .cer file.
Go to run
mmc.exe
add remove snapin
Certificates
Computer account
Local Computer
Expand certificates
Expand Trusted Root Certification Authorities
Right click certificates
All tasks
Import
Point to the cer file you created and that should be it.
There is also an online utility for converting certificate types if you have issues creating the public key from the pem file:
https://www.sslshopper.com/ssl-converter.html
https://www.sslshopper.com/ssl-converter.html
@becraig: not exactly what the OP needs. The cert that the firewall generated is using the MAC address for some crazy reason as the certificate name, so there will always be a name mismatch in the browser.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks for sticking with me on this!
It worked!
It worked!
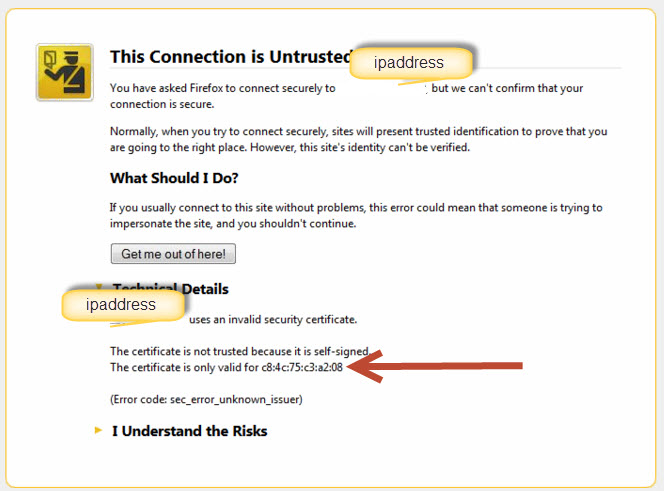
There are multiple reasons why you might be getting errors but the probability is high that there is something that needs to be fixed.
e.g
Name does not match: This is valid as you want to be sure you are talking to the correct device /endpoint
Not from a Trusted Publisher: This is also valid as you do not want someone to have their own CA and issue a certificate in your sites name or device name and intercept traffic which should be encrypted.
I am not sure which specific errors you are facing and having a better ides of your errors would help, however rest assured most SSL errors are valid and if you indicate the nature; we can help you to figure out how to best resolve to ensure your environment is as secure as possible.