N00b2015
asked on
Cannot change inherit permissions to Shared Folder in Powershell
I have the below script to create shared folders however, no matter what I do to change the " $HomeFolderACL.SetAccessRu
$Users=@()
$Results=@()
Import-Module ActiveDirectory
if (-not (Test-Path $Path))
{
write-error -Message "Cannot find path '$Path' because it does not exist."
return
}
if (-not (Test-Path $UserList))
{
write-error -Message "Cannot find '$UserList' because it does not exist."
return
}
else
{
$Users=Get-Content $UserList
}
#Check whether the input AD member is correct
if ($FullControlMember)
{
$FullControlMember|ForEach
if (-not(Get-ADObject -Filter 'Name -Like $_')){
$FullControlMember= $FullControlMember -notmatch $_; Write-Error -Message "Cannot find an object with name:'$_'"
}
}
}
$FullControlMember+="NT AUTHORITY\SYSTEM","BUILTIN
foreach($User in $Users)
{
$HomeFolderACL=Get-Acl $Path
$HomeFolderACL.SetAccessRu
$Result=New-Object PSObject
$Result|Add-Member -MemberType NoteProperty -Name "Username" -Value $User
if (Get-ADUser -Filter 'samaccountname -eq $User')
{
New-Item -ItemType directory -Path "$Path\$User"|Out-Null
#set acl to folder
$FCList=$FullControlMember
$FCList|ForEach-Object {
$ACL=New-Object System.Security.AccessCont
$HomeFolderACL.AddAccessRu
}
$FCList=$FullControlMember
$FCList|ForEach-Object {
$ACL=New-Object System.Security.AccessCont
$HomeFolderACL.AddAccessRu
}
Set-Acl -Path "$Path\$User" $HomeFolderACL
$Result|Add-Member -MemberType NoteProperty -Name "IsCreated" -Value "Yes"
$Result|Add-Member -MemberType NoteProperty -Name "Remark" -Value "N/A"
}
else
{
$Result|Add-Member -MemberType NoteProperty -Name "IsCreated" -Value "No"
$Result|Add-Member -MemberType NoteProperty -Name "Remark" -Value "Cannot fine an object with name:'$User'"
}
$Results+=$Result
}
#Generate a report
$Results|Export-Csv -NoTypeInformation -Path "$Path\Report.csv"
if ($?) {Write-Host "Please check the report for detail: '$Path\Report.csv'"}
$Users=@()
$Results=@()
Import-Module ActiveDirectory
if (-not (Test-Path $Path))
{
write-error -Message "Cannot find path '$Path' because it does not exist."
return
}
if (-not (Test-Path $UserList))
{
write-error -Message "Cannot find '$UserList' because it does not exist."
return
}
else
{
$Users=Get-Content $UserList
}
#Check whether the input AD member is correct
if ($FullControlMember)
{
$FullControlMember|ForEach
if (-not(Get-ADObject -Filter 'Name -Like $_')){
$FullControlMember= $FullControlMember -notmatch $_; Write-Error -Message "Cannot find an object with name:'$_'"
}
}
}
$FullControlMember+="NT AUTHORITY\SYSTEM","BUILTIN
foreach($User in $Users)
{
$HomeFolderACL=Get-Acl $Path
$HomeFolderACL.SetAccessRu
$Result=New-Object PSObject
$Result|Add-Member -MemberType NoteProperty -Name "Username" -Value $User
if (Get-ADUser -Filter 'samaccountname -eq $User')
{
New-Item -ItemType directory -Path "$Path\$User"|Out-Null
#set acl to folder
$FCList=$FullControlMember
$FCList|ForEach-Object {
$ACL=New-Object System.Security.AccessCont
$HomeFolderACL.AddAccessRu
}
$FCList=$FullControlMember
$FCList|ForEach-Object {
$ACL=New-Object System.Security.AccessCont
$HomeFolderACL.AddAccessRu
}
Set-Acl -Path "$Path\$User" $HomeFolderACL
$Result|Add-Member -MemberType NoteProperty -Name "IsCreated" -Value "Yes"
$Result|Add-Member -MemberType NoteProperty -Name "Remark" -Value "N/A"
}
else
{
$Result|Add-Member -MemberType NoteProperty -Name "IsCreated" -Value "No"
$Result|Add-Member -MemberType NoteProperty -Name "Remark" -Value "Cannot fine an object with name:'$User'"
}
$Results+=$Result
}
#Generate a report
$Results|Export-Csv -NoTypeInformation -Path "$Path\Report.csv"
if ($?) {Write-Host "Please check the report for detail: '$Path\Report.csv'"}
Try.. $HomeFolderACL.SetAccessRu
ASKER
Hi SubSun, sorry i should have mentioned the methods I've already tried. I have done that but it still doesn't work.
Both $HomeFolderACL.SetAccessRu
ASKER
Hmm, must be something I'm doing then. I'm also using version 3.0. I don't know if this would interfere however, I'am running powershell as a "run as other user" using my network admin credentials on my local machine. As i need to create folders onto a file server and not using the local powershell on that server. As it requires ad-modules and such.
You may try to assign permission on a test folder for a single user and see if you get same issue.
ASKER
Hi Subsun, i just did that and it did the same thing. Folders still inheriting permissions. I'm surprised that its working for you. Any ideas as I'm still stuck!
Thanks for your help so far.
Thanks for your help so far.
Following is the piece of code which I tested. Expected result it to have permission for SYSTEM, Administrators & TestUser on
\\ServerA\Temp\Test\TestUs
\\ServerA\Temp\Test\TestUs
$Path = "\\ServerA\Temp\Test"
$FullControlMember+="NT AUTHORITY\SYSTEM","BUILTIN\Administrators"
foreach($User in "TestUser")
{
$HomeFolderACL=Get-Acl $Path
$HomeFolderACL.SetAccessRuleProtection($true,$false)
$Result=New-Object PSObject
$Result|Add-Member -MemberType NoteProperty -Name "Username" -Value $User
if (Get-ADUser -Filter 'samaccountname -eq $User')
{
New-Item -ItemType directory -Path "$Path\$User"|Out-Null
#set acl to folder
$FCList=$FullControlMember+$User
$FCList|ForEach-Object {
$ACL=New-Object System.Security.AccessControl.FileSystemAccessRule($_,"Modify","ContainerInherit,ObjectInherit","None","Allow")
$HomeFolderACL.AddAccessRule($ACL)
}
$FCList=$FullControlMember
$FCList|ForEach-Object {
$ACL=New-Object System.Security.AccessControl.FileSystemAccessRule($_,"FullControl","ContainerInherit,ObjectInherit","None","Allow")
$HomeFolderACL.AddAccessRule($ACL)
}
Set-Acl -Path "$Path\$User" $HomeFolderACL
}
}ASKER
I've noticed you used ($User in "TestUser") instead of $Users as the default script?
That's just for testing.. There is not loop i this case as it's a single user, but I just wanted to put it with less modification.. :-)
ASKER
Ahh ok, good work ha :) .. Hmm. It's strange that it's working for you and not for me. I've tried many methods. Looking at your example path.. \\ServerA\Temp\Test\TestUs
You see the "Test" path folder. Did you add specific permissions on that folder then checked to see if it inherited on the "TestUser" folder? As mine did.
You see the "Test" path folder. Did you add specific permissions on that folder then checked to see if it inherited on the "TestUser" folder? As mine did.
In may case \\ServerA\Temp\Test folder already exist, and the script created TestUser folder inside the Test. It wont inherit the permissions even if I make any changes to the root folder.
Are you getting any error for the script?
Are you getting any error for the script?
ASKER
Hi, I don't get any errors which is strange. It just appears to work although permissions are inherited. It is strange it's working for you as both my tests did not.
Sorry, I am not able to reproduce the issue in anyway.. :-(.. Are getting same result for other servers or on your local computer?
Following is the simple code to disable the inheritance for a folder..

Following is the simple code to disable the inheritance for a folder..
$Folder = "C:\Temp\folder"
# Will remove the inheritance from parent
$ACL = get-acl $Folder
$ACL.SetAccessRuleProtection($true,$false)
Set-acl $Folder -aclobject $ACL
ASKER
It's ok, thanks for helping. I'm getting the same issue on the server AND my local machine.
Hmm.. that's really strange.. What is the OS?
ASKER
Windows 7 64bit
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you for your help! I will see what others might say.
ASKER
Hi Subsun,
Just a thought.. Could it be copying the permissions to the newly created folder? Normally when you disable inheritance from a folder you get an option to convert existing permissions or delete all (image below). Could this be possible? if so, is there a script i could add NOT to copy the permissions?
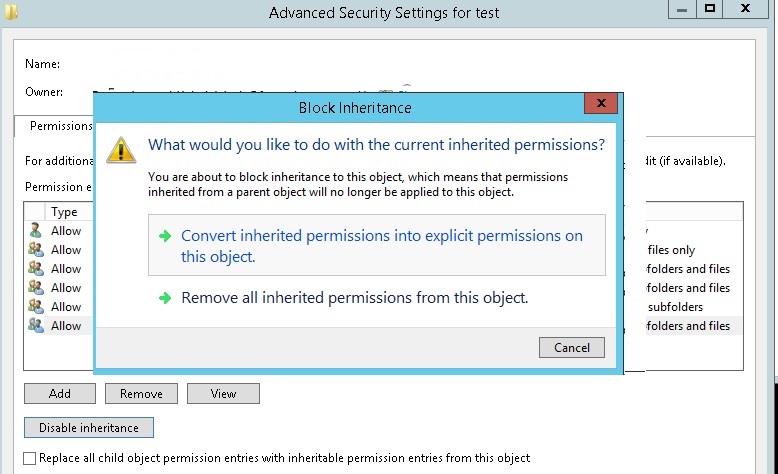
Thanks for your help as usual! :)
Just a thought.. Could it be copying the permissions to the newly created folder? Normally when you disable inheritance from a folder you get an option to convert existing permissions or delete all (image below). Could this be possible? if so, is there a script i could add NOT to copy the permissions?

Thanks for your help as usual! :)
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks.. Then I truly am stuck! I have no ideas why it's doing it!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
HI SubSun! I tested that code and it works.
ASKER
Got it!!
I removed the "$Path" from $HomeFolderACL=Get-Acl $Path (from the original script in this post) and all is working as it should!!!!
I removed the "$Path" from $HomeFolderACL=Get-Acl $Path (from the original script in this post) and all is working as it should!!!!
ASKER
I've requested that this question be closed as follows:
Accepted answer: 0 points for N00b2015's comment #a40591437
for the following reason:
Issue Resolved
Accepted answer: 0 points for N00b2015's comment #a40591437
for the following reason:
Issue Resolved
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
SubSun helped resolve the issue.
ASKER
Lol, yes you do. I'm new to this website, sorry about that. Thank you for helping me resolve.
no problem.. have a nice day!