Shark Attack
asked on
Can't get L2L tunnel up
Hello All,
Can anyone tell me why I can't get this tunnel up? I have full IP connectivity between the Loopbacks. I am able to ping from R2 Loopbacks to R4's Loopbacks and vica versa but when i do show cry isakmp sa I get nothing. When I do packettracer in inside icmp 192.168.10.10 0 18.18.18.148 detail i get all allowed across. Seems like the vpn map is not even applied although I have them on interfaces and seems like it's matching. I provided an image of my network map and configs of the devices. I have created this scenario in GNS 3.
Thank you
ASA.txt
Router.txt
MAP.jpg
Can anyone tell me why I can't get this tunnel up? I have full IP connectivity between the Loopbacks. I am able to ping from R2 Loopbacks to R4's Loopbacks and vica versa but when i do show cry isakmp sa I get nothing. When I do packettracer in inside icmp 192.168.10.10 0 18.18.18.148 detail i get all allowed across. Seems like the vpn map is not even applied although I have them on interfaces and seems like it's matching. I provided an image of my network map and configs of the devices. I have created this scenario in GNS 3.
Thank you
ASA.txt
Router.txt
MAP.jpg
If you're doing a policy based VPN, you won't use loopbacks, you won't route the inside IPs of the other end and your crypto ACL should match at least for what you have on the ASA.
I haven't even taken a look at the router yet.
I haven't even taken a look at the router yet.
ASKER
Thanks, I have correct the errors. I have taken off the Loopbacks and have actual hosts on each end, I have taken off the routes you mentioned. My ACL matches exactly. Now, I can't ping each end though. I am sure routing might be screwed up between the asa and router but I tried few things but was unsuccessful, can you look now? I have attached new configs and map
Router.txt
ASA.txt
NewMap.jpg
Router.txt
ASA.txt
NewMap.jpg
your crypto ACL has to permit ICMP at both ends.
ASKER
I added the icmp permit to crypto maps. When I ping 192.168.10.10 from 19.19.19.19 for example I get the below:
R11#ping 192.168.10.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.10, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)
R11#trace 192.168.10.10
Type escape sequence to abort.
Tracing the route to 192.168.10.10
1 19.19.19.1 16 msec 20 msec 20 msec
2 5.5.5.1 36 msec 44 msec 44 msec
3 *
On R1 O have 0.0.0.0 0.0.0.0 interface f0/0 same on the other end. The asa is 0.0.0.0 0.0.0.0 outside int.
R11#ping 192.168.10.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 192.168.10.10, timeout is 2 seconds:
UUUUU
Success rate is 0 percent (0/5)
R11#trace 192.168.10.10
Type escape sequence to abort.
Tracing the route to 192.168.10.10
1 19.19.19.1 16 msec 20 msec 20 msec
2 5.5.5.1 36 msec 44 msec 44 msec
3 *
On R1 O have 0.0.0.0 0.0.0.0 interface f0/0 same on the other end. The asa is 0.0.0.0 0.0.0.0 outside int.
ASKER
atleast now i am getting debugs.
*Mar 1 03:07:13.179: ISAKMP (0:3): purging node -1424824910
*Mar 1 03:07:13.179: ISAKMP (0:3): purging node -297005755
*Mar 1 03:07:13.195: ISAKMP (0:4): retransmitting phase 1 MM_NO_STATE...
*Mar 1 03:07:13.195: ISAKMP (0:4): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Mar 1 03:07:13.195: ISAKMP (0:4): retransmitting phase 1 MM_NO_STATE
*Mar 1 03:07:13.199: ISAKMP (0:4): sending packet to 16.16.16.1 my_port 500 peer_port 500 (I) MM_NO_STATE
R1#
*Mar 1 03:07:23.163: ISAKMP: received ke message (3/1)
*Mar 1 03:07:23.163: ISAKMP (0:4): peer does not do paranoid keepalives.
*Mar 1 03:07:23.167: ISAKMP (0:4): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 03:07:23.171: ISAKMP (0:3): peer does not do paranoid keepalives.
*Mar 1 03:07:23.175: ISAKMP (0:4): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 03:07:23.175: ISAKMP (0:4): deleting node -1842580298 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
*Mar 1 03:07:23.179: ISAKMP (0:4): deleting node -917118891 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
*Mar 1 03:07:23.179: ISAKMP (0:4): Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 1 03:07:23.183: ISAKMP (0:4): Old State = IKE_I_MM1 New State = IKE_DEST_SA
*Mar 1 03:07:23.183: ISAKMP (0:3): purging SA., sa=82B1F78C, delme=82B1F78C
*Mar 1 03:07:23.207: ISAKMP: received ke message (1/1)
*Mar 1 03:07:23.207: ISAKMP (0:0): SA request profile is (NULL)
*Mar 1 03:07:23.207: ISAKMP: local port 500, remote port 500
*Mar 1 03:07:23.211: ISAKMP: set new node 0 to QM_IDLE
*Mar 1 03:07:23.215: ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 82B1F78C
*Mar 1 03:07:23.215: ISAKMP (0:5): Can not start Aggressive mode, trying Main mode.
*Mar 1 03:07:23.215: ISAKMP: Looking for a matching key for 16.16.16.1 in default : success
*Mar 1 03:07:23.215: ISAKMP (0:5): found peer pre-shared key matching 16.16.16.1
*Mar 1 03:07:23.219: ISAKMP (0:5): constructed NAT-T vendor-07 ID
*Mar 1 03:07:23.219: ISAKMP (0:5): constructed NAT-T vendor-03 ID
*Mar 1 03:07:23.219: ISAKMP (0:5): constructed NAT-T vendor-02 ID
*Mar 1 03:07:23.223: ISAKMP (0:5): Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 1 03:07:23.223: ISAKMP (0:5): Old State = IKE_READY New State = IKE_I_MM1
*Mar 1 03:07:23.227: ISAKMP (0:5): beginning Main Mode exchange
*Mar 1 03:07:23.227: ISAKMP (0:5): sending packet to 16.16.16.1 my_port 500 peer_port 500 (I) MM_NO_STATE
*Mar 1 03:07:13.179: ISAKMP (0:3): purging node -1424824910
*Mar 1 03:07:13.179: ISAKMP (0:3): purging node -297005755
*Mar 1 03:07:13.195: ISAKMP (0:4): retransmitting phase 1 MM_NO_STATE...
*Mar 1 03:07:13.195: ISAKMP (0:4): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Mar 1 03:07:13.195: ISAKMP (0:4): retransmitting phase 1 MM_NO_STATE
*Mar 1 03:07:13.199: ISAKMP (0:4): sending packet to 16.16.16.1 my_port 500 peer_port 500 (I) MM_NO_STATE
R1#
*Mar 1 03:07:23.163: ISAKMP: received ke message (3/1)
*Mar 1 03:07:23.163: ISAKMP (0:4): peer does not do paranoid keepalives.
*Mar 1 03:07:23.167: ISAKMP (0:4): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 03:07:23.171: ISAKMP (0:3): peer does not do paranoid keepalives.
*Mar 1 03:07:23.175: ISAKMP (0:4): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 03:07:23.175: ISAKMP (0:4): deleting node -1842580298 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
*Mar 1 03:07:23.179: ISAKMP (0:4): deleting node -917118891 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
*Mar 1 03:07:23.179: ISAKMP (0:4): Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 1 03:07:23.183: ISAKMP (0:4): Old State = IKE_I_MM1 New State = IKE_DEST_SA
*Mar 1 03:07:23.183: ISAKMP (0:3): purging SA., sa=82B1F78C, delme=82B1F78C
*Mar 1 03:07:23.207: ISAKMP: received ke message (1/1)
*Mar 1 03:07:23.207: ISAKMP (0:0): SA request profile is (NULL)
*Mar 1 03:07:23.207: ISAKMP: local port 500, remote port 500
*Mar 1 03:07:23.211: ISAKMP: set new node 0 to QM_IDLE
*Mar 1 03:07:23.215: ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 82B1F78C
*Mar 1 03:07:23.215: ISAKMP (0:5): Can not start Aggressive mode, trying Main mode.
*Mar 1 03:07:23.215: ISAKMP: Looking for a matching key for 16.16.16.1 in default : success
*Mar 1 03:07:23.215: ISAKMP (0:5): found peer pre-shared key matching 16.16.16.1
*Mar 1 03:07:23.219: ISAKMP (0:5): constructed NAT-T vendor-07 ID
*Mar 1 03:07:23.219: ISAKMP (0:5): constructed NAT-T vendor-03 ID
*Mar 1 03:07:23.219: ISAKMP (0:5): constructed NAT-T vendor-02 ID
*Mar 1 03:07:23.223: ISAKMP (0:5): Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Mar 1 03:07:23.223: ISAKMP (0:5): Old State = IKE_READY New State = IKE_I_MM1
*Mar 1 03:07:23.227: ISAKMP (0:5): beginning Main Mode exchange
*Mar 1 03:07:23.227: ISAKMP (0:5): sending packet to 16.16.16.1 my_port 500 peer_port 500 (I) MM_NO_STATE
Let's start with the ASA:
You have this crypto ACL:
access-list LIST extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST extended permit ip 192.168.10.0 255.255.255.0 19.19.19.0 255.255.255.0
There should be one entry from your inside subnet to their inside subnet. You have it going both ways and that's wrong.
Also, I don't see where either 192.168.10.2/24 or 19.19.19.0/24 exist on the ASA.
You have this crypto ACL:
access-list LIST extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST extended permit ip 192.168.10.0 255.255.255.0 19.19.19.0 255.255.255.0
There should be one entry from your inside subnet to their inside subnet. You have it going both ways and that's wrong.
Also, I don't see where either 192.168.10.2/24 or 19.19.19.0/24 exist on the ASA.
ASKER
and on asa debug
Nov 30 00:48:51 [IKEv1 DEBUG]: IP = 16.16.16.2, IKE SA MM:d6df9aa9 terminating: flags 0x01000022, refcnt 0, t uncnt 0
Nov 30 00:48:51 [IKEv1 DEBUG]: IP = 16.16.16.2, sending delete/delete with reason message
Nov 30 00:48:51 [IKEv1]: IP = 16.16.16.2, Removing peer from peer table failed, no match!
Nov 30 00:48:51 [IKEv1]: IP = 16.16.16.2, Error: Unable to remove PeerTblEntry
Nov 30 00:48:51 [IKEv1 DEBUG]: IP = 16.16.16.2, IKE SA MM:d6df9aa9 terminating: flags 0x01000022, refcnt 0, t uncnt 0
Nov 30 00:48:51 [IKEv1 DEBUG]: IP = 16.16.16.2, sending delete/delete with reason message
Nov 30 00:48:51 [IKEv1]: IP = 16.16.16.2, Removing peer from peer table failed, no match!
Nov 30 00:48:51 [IKEv1]: IP = 16.16.16.2, Error: Unable to remove PeerTblEntry
ASKER
OK, here is my ASA crypto acl
access-list LIST line 1 extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST line 2 extended permit icmp any any
Here is the routers
Extended IP access list LIST
10 permit ip 192.168.10.0 0.0.0.255 19.19.19.0 0.0.0.255
30 permit icmp any any (11 matches)
The 19.19.19.0 network is on the routers end and the 192.168.10.0 is at the asa's side.
The R4 has int 192.168.10.1 going to 192.168.10.10(host)
access-list LIST line 1 extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST line 2 extended permit icmp any any
Here is the routers
Extended IP access list LIST
10 permit ip 192.168.10.0 0.0.0.255 19.19.19.0 0.0.0.255
30 permit icmp any any (11 matches)
The 19.19.19.0 network is on the routers end and the 192.168.10.0 is at the asa's side.
The R4 has int 192.168.10.1 going to 192.168.10.10(host)
ASKER
This is how I have this configured.
192.168.10.10 > 192.168.10.1 > 9.9.9.2 >9.9.9.1 >16.16.16.1 || 16.16.16.2 < 5.5.5.1 <5.5.5.2 < 19.19.19.1 <19.19.19.19
192.168.10.10 > 192.168.10.1 > 9.9.9.2 >9.9.9.1 >16.16.16.1 || 16.16.16.2 < 5.5.5.1 <5.5.5.2 < 19.19.19.1 <19.19.19.19
ASKER
Also, my isakmp phase 1 on the router comes up momentarily but no on the ASA
Router1#show crypto isakmp sa
dst src state conn-id slot
16.16.16.1 16.16.16.2 MM_NO_STATE 1 0 (deleted)
Router1#show crypto isakmp sa
dst src state conn-id slot
16.16.16.1 16.16.16.2 MM_NO_STATE 1 0 (deleted)
The problem that I'm having with all of this is that none of your subnets for the inside interfaces and the subnets in the crypto ACL match.
If your inside interface on the ASA is 9.9.9.0/24, then *that* subnet needs to be permitted in the ACL to the inside subnet at the other end of the tunnel.
If your inside interface on the ASA is 9.9.9.0/24, then *that* subnet needs to be permitted in the ACL to the inside subnet at the other end of the tunnel.
ASKER
9.9.9.0 is the inside. So it should be more like this?
ASA
access-list LIST line 1 extended permit icmp any any (hitcnt=0) 0x76474e5f
access-list LIST line 2 extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
ROUTER
Extended IP access list LIST
30 permit icmp any any (38 matches)
40 permit ip 9.9.9.0 0.0.0.255 19.19.19.0 0.0.0.255
ASA
access-list LIST line 1 extended permit icmp any any (hitcnt=0) 0x76474e5f
access-list LIST line 2 extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
ROUTER
Extended IP access list LIST
30 permit icmp any any (38 matches)
40 permit ip 9.9.9.0 0.0.0.255 19.19.19.0 0.0.0.255
and where do the 19.19.19.0/24 and 192.168.10.0/24 subnets come into play?
ASKER
I added these, am I still missing something?
ASA
access-list LIST line 1 extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST line 3 extended permit ip 5.5.5.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST line 2 extended permit icmp any any
Router
Extended IP access list LIST
10 permit ip 192.168.10.0 0.0.0.255 19.19.19.0 0.0.0.255
30 permit icmp any any
40 permit ip 9.9.9.0 0.0.0.255 19.19.19.0 0.0.0.255
ASA
access-list LIST line 1 extended permit ip 19.19.19.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST line 3 extended permit ip 5.5.5.0 255.255.255.0 192.168.10.0 255.255.255.0
access-list LIST line 2 extended permit icmp any any
Router
Extended IP access list LIST
10 permit ip 192.168.10.0 0.0.0.255 19.19.19.0 0.0.0.255
30 permit icmp any any
40 permit ip 9.9.9.0 0.0.0.255 19.19.19.0 0.0.0.255
On the ASA, I see two subnets:
16.16.16.0/24
9.9.9.0.24
The first cannot be a part of the encryption domain since it's also the peer IP.
I don't see 5.5.5.0/24 or 19.19.19.0/24 configured anywhere on the ASA.
On the router, I see two subnets:
16.16.16.0/24
5.5.5.0/24
The first cannot be a part of the encryption domain since it's also the peer IP
I don't see 192.168.10.0/24 or 9.9.9.0/24 configured anywhere on the router.
I would expect the ASA to look like this:
access-list ASA extended permit icmp 9.9.9.0 255.255.255.0 5.5.5.0 255.255.255.0
access-list ASA extended permit ip 9.9.9.0 255.255.255.0 5.5.5.0 255.255.255.0
I would expect the ROUTER to look like this:
ip access-list extended ROUTER
10 permit icmp 5.5.5.0 0.0.0.255 9.9.9.0 0.0.0.255
20 permit ip 5.5.5.0 0.0.0.255 9.9.9.0 0.0.0.255
You keep referring to subnets in your configurations that I do not see.
16.16.16.0/24
9.9.9.0.24
The first cannot be a part of the encryption domain since it's also the peer IP.
I don't see 5.5.5.0/24 or 19.19.19.0/24 configured anywhere on the ASA.
On the router, I see two subnets:
16.16.16.0/24
5.5.5.0/24
The first cannot be a part of the encryption domain since it's also the peer IP
I don't see 192.168.10.0/24 or 9.9.9.0/24 configured anywhere on the router.
I would expect the ASA to look like this:
access-list ASA extended permit icmp 9.9.9.0 255.255.255.0 5.5.5.0 255.255.255.0
access-list ASA extended permit ip 9.9.9.0 255.255.255.0 5.5.5.0 255.255.255.0
I would expect the ROUTER to look like this:
ip access-list extended ROUTER
10 permit icmp 5.5.5.0 0.0.0.255 9.9.9.0 0.0.0.255
20 permit ip 5.5.5.0 0.0.0.255 9.9.9.0 0.0.0.255
You keep referring to subnets in your configurations that I do not see.
ASKER
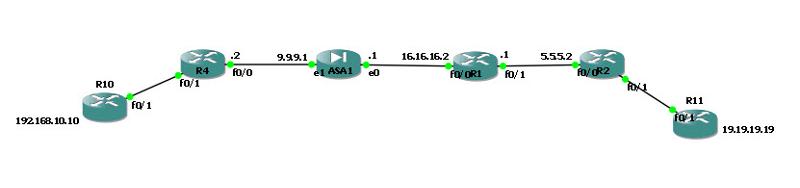
I only showed you the configs of the ASA and the router that has the tunnel on. Did you look at the network map I attached? I also inserted the above image of it, There are two networks on the inside of the ASA. One network connect a ASA to router and then there is another network connecting that router to another network, The F0/1 on R4 is 192.168.10.1, R2 on the other end is 18.18.18.1 going to 18.18.18.2
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
thanks, unfortunately, I still can't get the tunnel up though.
here is what i get on the routers isakmp and debug
R1#show crypto isakmp sa
dst src state conn-id slot
16.16.16.2 9.9.9.1 MM_NO_STATE 3 0
16.16.16.2 9.9.9.1 MM_NO_STATE 2 0 (deleted)
*Mar 1 01:17:31.271: ISAKMP (0:1): retransmitting phase 1 MM_NO_STATE...
*Mar 1 01:17:31.271: ISAKMP (0:1): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Mar 1 01:17:31.275: ISAKMP (0:1): retransmitting phase 1 MM_NO_STATE
*Mar 1 01:17:31.275: ISAKMP (0:1): sending packet to 16.16.16.1 my_port 500 peer_port 500 (I) MM_NO_STATE
R1#
*Mar 1 01:17:41.219: ISAKMP: received ke message (3/1)
*Mar 1 01:17:41.219: ISAKMP (0:1): peer does not do paranoid keepalives.
*Mar 1 01:17:41.223: ISAKMP (0:1): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 01:17:41.227: ISAKMP (0:1): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 01:17:41.231: ISAKMP (0:1): deleting node -1746173240 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
*Mar 1 01:17:41.231: ISAKMP (0:1): deleting node 112806183 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
R1#
*Mar 1 01:17:41.235: ISAKMP (0:1): Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 1 01:17:41.235: ISAKMP (0:1): Old State = IKE_I_MM1 New State = IKE_DEST_SA
ASA
DEBUG
Nov 30 00:02:53 [IKEv1 DEBUG]: IP = 16.16.16.2, IKE MM Initiator FSM error history (struct &0xd89d4c50) <state>, <event>: MM_DONE, EV_ERROR-->MM_WAIT_MSG2, EV_RETRY-->MM_WAIT_MSG2, EV_TIMEOUT-->MM_WAIT_MSG2,
Nov 30 00:02:53 [IKEv1 DEBUG]: IP = 16.16.16.2, IKE SA MM:81ed1904 terminating: flags 0x01000022, refcnt 0, tuncnt 0
Nov 30 00:02:53 [IKEv1 DEBUG]: IP = 16.16.16.2, sending delete/delete with reason message
Nov 30 00:02:53 [IKEv1]: IP = 16.16.16.2, Removing peer from peer table failed, no match!
Nov 30 00:02:53 [IKEv1]: IP = 16.16.16.2, Error: Unable to remove PeerTblEntry
We can work on this on Monday I have to leave the office. I am not sure what else could it be.
here is what i get on the routers isakmp and debug
R1#show crypto isakmp sa
dst src state conn-id slot
16.16.16.2 9.9.9.1 MM_NO_STATE 3 0
16.16.16.2 9.9.9.1 MM_NO_STATE 2 0 (deleted)
*Mar 1 01:17:31.271: ISAKMP (0:1): retransmitting phase 1 MM_NO_STATE...
*Mar 1 01:17:31.271: ISAKMP (0:1): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Mar 1 01:17:31.275: ISAKMP (0:1): retransmitting phase 1 MM_NO_STATE
*Mar 1 01:17:31.275: ISAKMP (0:1): sending packet to 16.16.16.1 my_port 500 peer_port 500 (I) MM_NO_STATE
R1#
*Mar 1 01:17:41.219: ISAKMP: received ke message (3/1)
*Mar 1 01:17:41.219: ISAKMP (0:1): peer does not do paranoid keepalives.
*Mar 1 01:17:41.223: ISAKMP (0:1): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 01:17:41.227: ISAKMP (0:1): deleting SA reason "gen_ipsec_isakmp_delete but doi isakmp" state (I) MM_NO_STATE (peer 16.16.16.1) input queue 0
*Mar 1 01:17:41.231: ISAKMP (0:1): deleting node -1746173240 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
*Mar 1 01:17:41.231: ISAKMP (0:1): deleting node 112806183 error TRUE reason "gen_ipsec_isakmp_delete but doi isakmp"
R1#
*Mar 1 01:17:41.235: ISAKMP (0:1): Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Mar 1 01:17:41.235: ISAKMP (0:1): Old State = IKE_I_MM1 New State = IKE_DEST_SA
ASA
DEBUG
Nov 30 00:02:53 [IKEv1 DEBUG]: IP = 16.16.16.2, IKE MM Initiator FSM error history (struct &0xd89d4c50) <state>, <event>: MM_DONE, EV_ERROR-->MM_WAIT_MSG2, EV_RETRY-->MM_WAIT_MSG2, EV_TIMEOUT-->MM_WAIT_MSG2,
Nov 30 00:02:53 [IKEv1 DEBUG]: IP = 16.16.16.2, IKE SA MM:81ed1904 terminating: flags 0x01000022, refcnt 0, tuncnt 0
Nov 30 00:02:53 [IKEv1 DEBUG]: IP = 16.16.16.2, sending delete/delete with reason message
Nov 30 00:02:53 [IKEv1]: IP = 16.16.16.2, Removing peer from peer table failed, no match!
Nov 30 00:02:53 [IKEv1]: IP = 16.16.16.2, Error: Unable to remove PeerTblEntry
We can work on this on Monday I have to leave the office. I am not sure what else could it be.
ASKER
the source on the output of show crypto isa sa is 9.9.9.1 is that even right?
ASKER
resolved.
Forgot the "crypto isakmp enable OUTSIDE"
Forgot the "crypto isakmp enable OUTSIDE"
ASKER
I've requested that this question be closed as follows:
Accepted answer: 0 points for Zack Gil's comment #a40599608
for the following reason:
resolved.
Forgot the "crypto isakmp enable OUTSIDE"
Accepted answer: 0 points for Zack Gil's comment #a40599608
for the following reason:
resolved.
Forgot the "crypto isakmp enable OUTSIDE"
ASKER
also, the only ACL statements I needed were these
ASA
ciscoasa(config)# show access-l LIST
access-list LIST; 2 elements
access-list LIST line 1 extended permit icmp 192.168.10.0 255.255.255.0 19.19.19.0 255.255.255.0 (hitcnt=2)
access-list LIST line 2 extended permit ip 192.168.10.0 255.255.255.0 19.19.19.0 255.255.255.0
Router
R1(config)#do show access-l LIST
Extended IP access list LIST
70 permit icmp 19.19.19.0 0.0.0.255 192.168.10.0 0.0.0.255 (64 matches)
80 permit ip 19.19.19.0 0.0.0.255 192.168.10.0 0.0.0.255
ASA
ciscoasa(config)# show access-l LIST
access-list LIST; 2 elements
access-list LIST line 1 extended permit icmp 192.168.10.0 255.255.255.0 19.19.19.0 255.255.255.0 (hitcnt=2)
access-list LIST line 2 extended permit ip 192.168.10.0 255.255.255.0 19.19.19.0 255.255.255.0
Router
R1(config)#do show access-l LIST
Extended IP access list LIST
70 permit icmp 19.19.19.0 0.0.0.255 192.168.10.0 0.0.0.255 (64 matches)
80 permit ip 19.19.19.0 0.0.0.255 192.168.10.0 0.0.0.255
ASKER