Disk cleanup
In the image below, after System Disk? cleanup, I am getting the following: (see the image below for the matching numbers)
1. Some description of files in question
2. Asking me if I want to delete them but I can remember why they are in my computer?
3. The list of files to be deleted if I click on Delete Files.
Question: Do you recognize what these files are? Shall I delete them?
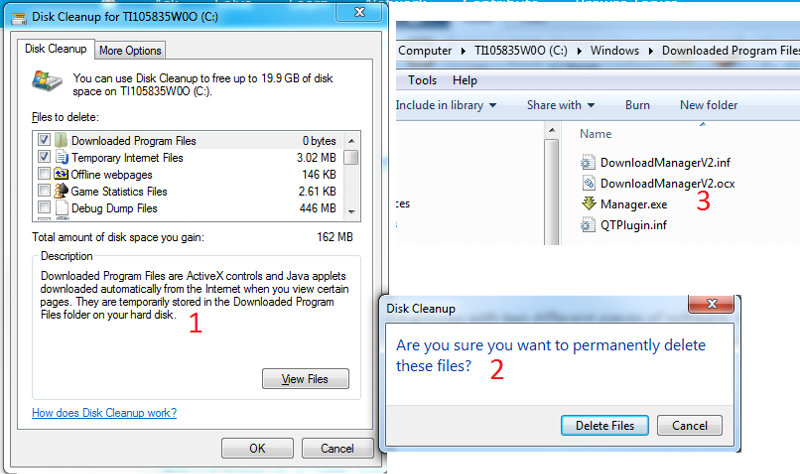
1. Some description of files in question
2. Asking me if I want to delete them but I can remember why they are in my computer?
3. The list of files to be deleted if I click on Delete Files.
Question: Do you recognize what these files are? Shall I delete them?

ASKER
Thank you John,
What other action I could follow to clean up my computer and make it run smoother? Do you have a list to give tom or suggest a link?
Thank you,
Mike
What other action I could follow to clean up my computer and make it run smoother? Do you have a list to give tom or suggest a link?
Thank you,
Mike
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thanks
eghetabas...
See John's very informative article Trouble-free computing - a basic approach
See John's very informative article Trouble-free computing - a basic approach
ASKER
Thank you NewVillageIT,
Sorry I closed the question too soon to split it.
Mike
Sorry I closed the question too soon to split it.
Mike
Probably run CCleaner https://www.piriform.com/ccleaner/download
and then Defraggler https://www.piriform.com/defraggler/download
The free versions are good enough.
and then Defraggler https://www.piriform.com/defraggler/download
The free versions are good enough.
No worries, eghtebas. I'm glad to help, still. Have a nice day...
ASKER
Space Oddity,
How one can trust these links? I have had so much problem with these kind of links. The fix one thing but download many unwanted stuff to your computer. How do you handle (or trust) them?
Mike
How one can trust these links? I have had so much problem with these kind of links. The fix one thing but download many unwanted stuff to your computer. How do you handle (or trust) them?
Mike
Download from Piriform itself. And always take care on installation. Watch out for any offers that the installation makes and decline always reading carefully.
And visit Gizmo's Tech Support Alert http://www.techsupportalert.com/ for good applications as well.
CNet is not to be trusted for downloads. File Hippo is going that way as well. SourceForge is usually OK.
And visit Gizmo's Tech Support Alert http://www.techsupportalert.com/ for good applications as well.
CNet is not to be trusted for downloads. File Hippo is going that way as well. SourceForge is usually OK.
ASKER
Thanks,
Mike
Mike
@eghtebas - Thanks and I was happy to help.
Disk Cleanup is Good Housekeeping.