compdigit44
asked on
Windows 2008 Certificate Services - Key Recovery Agent
I am in the process of planning my roll out of user certificates with auto-enrollment and have the following questions about the Key Recovery Agent.
1) The KRA, can only recovery key to certificates that were issue after the KRA was setup and not ones that were issued before correct?
2) Should the KRA be plublished in AD?
3) Is it ok to use Auto-Enrollment to issue the cert to my security group only?
4) Any special Request Handling setting I should select?
5) When and how woud I use the KRA? I never had to use it before
1) The KRA, can only recovery key to certificates that were issue after the KRA was setup and not ones that were issued before correct?
2) Should the KRA be plublished in AD?
3) Is it ok to use Auto-Enrollment to issue the cert to my security group only?
4) Any special Request Handling setting I should select?
5) When and how woud I use the KRA? I never had to use it before
ASKER
Thanks....
So the KRA have no baring on user issued certificates?????
I am confused by your responce to my auto-enrollment questoin
So the KRA have no baring on user issued certificates?????
I am confused by your responce to my auto-enrollment questoin
please read the reference articles provided. auto-enrollment depends upon corporate policy and your certificate policy which is really important if you are using pki with other companies
ASKER
If a KRA is set to enroll and not auto-enroll would they be able to recover a Key if they had not request a KRA certificate?
Users are not protected by key archival until they have enrolled for a certificate that has key recovery enabled. If they have identical certificates that were issued before key recovery was enabled, they are not covered by key archival. Clients must be re-enrolled to receive a certificate that is based on the changed template if they already have a valid certificate that is based on the old template.
you have to create the EFS template to include KRA using the EFS template.
https://www.youtube.com/watch?v=XCXXNdCgzNk
https://www.youtube.com/watch?v=K_fN9cuqhRc
ASKER
OK got it now.... for the certificates based on the user certificate template, the key recovery agent can or cannot do any thing???
the older certificates a KRA can do nothing the data is lost only data encrypted with certificates that have the kra properties is recoverable using a KRA
ASKER
WHen selecting auto-enroll for the KRA I noticed the request still goes to pend and does not automatically issue it.
ALso I still do not see the KRA cert listed in my personal store
ALso I still do not see the KRA cert listed in my personal store
are you a kra agent? or not?
ASKER
OK... I figure out my problem ... first time user error...
I do see my KRA cert listed under personal now....
ON a domain is the only good per workstation though? Or once the KRA is register on the server it is good domain wide
I do see my KRA cert listed under personal now....
ON a domain is the only good per workstation though? Or once the KRA is register on the server it is good domain wide
ASKER
Our Security Dept has been grant the KRA rights. This group has 10 users. I see all of their KRA certs listed under, pending but now see this is going to happen each time they log into a workstation.....So in order to recover a key the KRA cert needs to be present on the workstation???? I know under the properties of the CA i need to go the the REcovery Agents tab and select each cert...
Am I doing everything correct??
Am I doing everything correct??
ASKER
OK I think I see me problem.. but wanted to run this by the Certificate Experts..
I am using issueing "user" certificates with the signature / encryption usage and not EFS.
A user cert verifies a user is who they said their are and is not really encrypting anything which is why I have problems issues the cert when I select allow archive of private keys.
Does this sound right
I am using issueing "user" certificates with the signature / encryption usage and not EFS.
A user cert verifies a user is who they said their are and is not really encrypting anything which is why I have problems issues the cert when I select allow archive of private keys.
Does this sound right
ASKER
Here is more information: The user template is set for Windows 2003 and not Windows 2008 and according to the following artricle I should be able to archive the key when the Request Handeling is set to Signature and Encryption yet I am not able to...
https://technet.microsoft.com/en-us/library/cc725621%28v=ws.10%29.aspx
Excerpt from link....
The certificate purpose setting will determine whether key archival can be enabled for a certificate template. Key archival is only possible if the certificate purpose is set to Encryption or Signature and encryption. The recovery of a private key for digitally signing information may result in identity theft and is not supported. Key archival is not supported by most smart card CSPs.
https://technet.microsoft.com/en-us/library/cc725621%28v=ws.10%29.aspx
Excerpt from link....
The certificate purpose setting will determine whether key archival can be enabled for a certificate template. Key archival is only possible if the certificate purpose is set to Encryption or Signature and encryption. The recovery of a private key for digitally signing information may result in identity theft and is not supported. Key archival is not supported by most smart card CSPs.
if a user right clicks on a file / folder then chooses encrypt they are using the Encrypting File System (EFS)
ASKER
Thank you for the reply...
Here is where I am confused...
User template has been cloned, publishd and user are receiving this when they login which is perfect.. The request handeling is set to signature and Encryption.
We are only use certificate to verify the user identiy. IS a key recovery agent even needed. WHen I enable archive key it user can not enroll for the cert yet when I remove this check box user can enroll for it
Here is where I am confused...
User template has been cloned, publishd and user are receiving this when they login which is perfect.. The request handeling is set to signature and Encryption.
We are only use certificate to verify the user identiy. IS a key recovery agent even needed. WHen I enable archive key it user can not enroll for the cert yet when I remove this check box user can enroll for it
you don't need KRA in this scenario.. it is only used for EFS recovery
ASKER
SO I am correct that even though the certificate is set for signature an encryption, the fact it is a user set which is noted in the OID makes private key articling a moto point.
Why is this check box even an option on a user certificate
Why is this check box even an option on a user certificate
you can remove that option from your template.
ASKER
I undertand you can uncheck it but why is the check box even there
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I have read the article you posted and others and have made sure my KRA is setup on my CA the enabled key articla on my user template set for signature and encryption get the following messagte on my CA server....
Active Directory Certificate Services denied request 8685 because The request includes a private key for archival by the server, but key archival is not enabled for the specified certificate template. 0x80094810 (-2146875376). The request was for Domaine\UserABC. Additional information: Denied by Policy Module
This is a Windows 2008 CS but the template is based on 2003.
Any thought or suggestions. I even tried changing the template to encryption only and it made no difference
Active Directory Certificate Services denied request 8685 because The request includes a private key for archival by the server, but key archival is not enabled for the specified certificate template. 0x80094810 (-2146875376). The request was for Domaine\UserABC. Additional information: Denied by Policy Module
This is a Windows 2008 CS but the template is based on 2003.
Any thought or suggestions. I even tried changing the template to encryption only and it made no difference
ASKER
Thank you for the reply...
Here are the answers to your questions.
1) I do I have a valid KRA certificate issued of myself and is registered on the CA which the services have been stop and started on multiple times.
2) ON my user template the box to enable archive keys is checked. I have even tried switch the Request handling from Signature / Encryption to Encryption only and got the same results.
Could my versions of the template be an issue since it is based on Windows 2003? Maybe CSP's are missing?
Now do you see why I am so perplexed!!!!!! :-(
Thanks again for all of your help
Here are the answers to your questions.
1) I do I have a valid KRA certificate issued of myself and is registered on the CA which the services have been stop and started on multiple times.
2) ON my user template the box to enable archive keys is checked. I have even tried switch the Request handling from Signature / Encryption to Encryption only and got the same results.
Could my versions of the template be an issue since it is based on Windows 2003? Maybe CSP's are missing?
Now do you see why I am so perplexed!!!!!! :-(
Thanks again for all of your help
check the properties of the template.. the 2003 template is to distinguish it from REALLY ancient templates
pictures say a thousand words
pictures say a thousand words
ASKER
Thanks I checked my user template again and the archive keys "IS" selected
ASKER
Any thoughts or idea on why this is not working... even though all documentation states that it should
did you watch the youtube video's that I mentioned earlier?
ASKER
I have watched the vidoe and read all of the article you posted.
I was able to issue, enroll and register my KRA certificate on my CA. As soon as it enable archive key on my user cert if get the message I post earlier..
I am totally stumped on why this is now working..
My CA is a Windows 2008 R2 Enterprise Edition
I was able to issue, enroll and register my KRA certificate on my CA. As soon as it enable archive key on my user cert if get the message I post earlier..
I am totally stumped on why this is now working..
My CA is a Windows 2008 R2 Enterprise Edition
ASKER
It turns out that even though you are prompted to restart the CA services when registering a KRA certificate I had to restart the service via services.msc in order for the registered KRA to show as valid
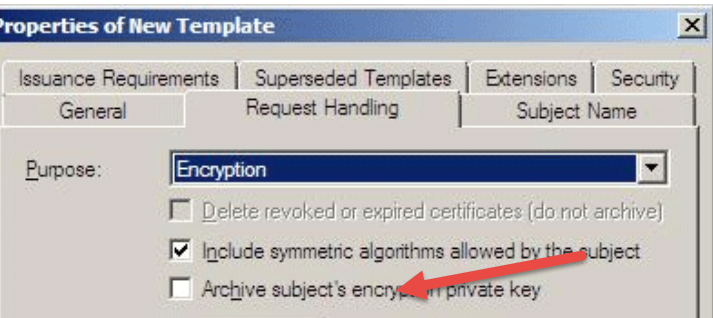
Correct This is for EFS certificates ONLY
2) Should the KRA be plublished in AD?
has to be
3) Is it ok to use Auto-Enrollment to issue the cert to my security group only?
??
4) Any special Request Handling setting I should select?
Not that I'm aware of
5) When and how woud I use the KRA? I never had to use it before
https://technet.microsoft.com/en-us/library/cc770588.aspx
https://technet.microsoft.com/en-us/library/cc730721.aspx