EA-170
asked on
New block of IP addresses - what to do with CISCOASA 5515
Hello,
Recently we just received a new block of IP addresses from our ISP. the ISP made the IP addresses available on the same interface that our other block on IP addresses are on but I am wondering what do I need to do on the firewall to make the new IPs useable.
I'm familiar with the ASA but stuff liek this I don't usually come across so if I can get some instructions on what I need to do that would be great. thanks!
Recently we just received a new block of IP addresses from our ISP. the ISP made the IP addresses available on the same interface that our other block on IP addresses are on but I am wondering what do I need to do on the firewall to make the new IPs useable.
I'm familiar with the ASA but stuff liek this I don't usually come across so if I can get some instructions on what I need to do that would be great. thanks!
ASKER
I should clarify - these new IPs are additional IPs to what we already have not for a new interface or service.
So it is our existing ISP service and we still have the same original public IPs xxx.xxx.123.123-142 but then they gave us an additional 5 IP addresses xxx.xxx.124.123-128 but not contiguous to our original IPs but on the same interface.
So I created a network object for the internal server and setup a NAT to xxx.xxx.124.123
So do I just need to add another another static route on the outside interface to include the new gateway for the new range of IP addresses: xxx.xxx.124.122 which is the gateway IP?
So there is one setup already on the outside interface to the original gateway of xxx.xxx.123.122 with a metric of 1.
So it is our existing ISP service and we still have the same original public IPs xxx.xxx.123.123-142 but then they gave us an additional 5 IP addresses xxx.xxx.124.123-128 but not contiguous to our original IPs but on the same interface.
So I created a network object for the internal server and setup a NAT to xxx.xxx.124.123
So do I just need to add another another static route on the outside interface to include the new gateway for the new range of IP addresses: xxx.xxx.124.122 which is the gateway IP?
So there is one setup already on the outside interface to the original gateway of xxx.xxx.123.122 with a metric of 1.
I'll just add to further illustrate:
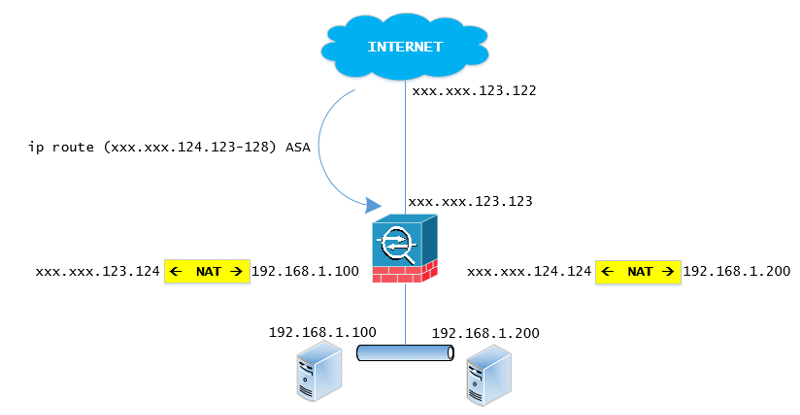

The key here is that the upstream router is already routing the new IP/subnets towards your ASA. You don't need to reconfigure the outside interface or use the new IP on the existing outside interface or add a new interface. Also, you dont need to configure another default route.
you would configure static NAT normally as you would as illustrated in the example below
object network OBJECT_INTERNAL_192.168.1.100
host 192.168.1.100
!
object network OBJECT_INTERNAL_192.168.1.200
host 192.168.1.200
!
object network OBJECT_EXTERNAL_xxx.xxx.123.124
host xxx.xxx.123.124
!
object network OBJECT_EXTERNAL_xxx.xxx.124.124
host xxx.xxx.124.124
!
!
nat (inside,outside) 1 source static OBJECT_INTERNAL_192.168.1.100 OBJECT_EXTERNAL_xxx.xxx.123.124
nat (inside,outside) 2 source static OBJECT_INTERNAL_192.168.1.200 OBJECT_EXTERNAL_xxx.xxx.124.124
OR if you are using object nat commands
object network OBJECT_INTERNAL_192.168.1.100
host 192.168.1.100
!
object network OBJECT_INTERNAL_192.168.1.100
nat (inside,outside) static xxx.xxx.123.124
!
!
!
!
object network OBJECT_INTERNAL_192.168.1.200
host 192.168.1.200
!
object network OBJECT_INTERNAL_192.168.1.200
nat (inside,outside) static xxx.xxx.124.124
The new block of IPs are already routed over the existing ISP link.
No need to add any route and you didn't need to create a network object for the internal server.
Since this is for existing services and nothing new then all you need to do is NAT translate to the new block of IPs.
No need to add any route and you didn't need to create a network object for the internal server.
Since this is for existing services and nothing new then all you need to do is NAT translate to the new block of IPs.
ASKER
Thanks for both your replies and I guess what I find confusing that that I did create the NAT but the ISP is saying they are not detecting any traffic over the new gateway for the new block of IP addresses. Which I am not sure how to troubleshoot to verify their claim.
You can test the NAT yourself by using a spare network Interface. NAT from the spare Interface to just one of the new public IPs rather than an entire block. Use static NAT.
- The destination Interface will be the existing Interface which has your existing Public IP
- The translated address will be the new Public IP declared in the Network Objects. Ensure you declare the new public IP you are testing. e.g. xxx.xxx.124.125
- The source interface is the spare Interface you are testing with. (e.g. 192.168.100.254 /24)
Once you've set this up:
1. Hook up the spare Interface to a switch
2. Take a spare laptop and plug it into the switch
- IP e.g: 192.168.100.1
- Mask 255.255.255.0
- Gateway: 192.168.100.254
- DNS 8.8.8.8
3. Create the access rule for incoming traffic to 192.168.100.0
4. Test Internet (Configure your browser to automatic detection if needed)
5. If Internet works then go to Google and type "My IP". It should show you the new public IP you are NAT-ing to.
If you manage to make the above work, you will be able to figure out the NAT rules for your existing network. Basically, you want to NAT to the new range of addresses using the old existing NAT rule that NAT's to the the old block. The old existing NAT rule should include the new block that should be declared in the the Network Objects.
Hope this helps.
- The destination Interface will be the existing Interface which has your existing Public IP
- The translated address will be the new Public IP declared in the Network Objects. Ensure you declare the new public IP you are testing. e.g. xxx.xxx.124.125
- The source interface is the spare Interface you are testing with. (e.g. 192.168.100.254 /24)
Once you've set this up:
1. Hook up the spare Interface to a switch
2. Take a spare laptop and plug it into the switch
- IP e.g: 192.168.100.1
- Mask 255.255.255.0
- Gateway: 192.168.100.254
- DNS 8.8.8.8
3. Create the access rule for incoming traffic to 192.168.100.0
4. Test Internet (Configure your browser to automatic detection if needed)
5. If Internet works then go to Google and type "My IP". It should show you the new public IP you are NAT-ing to.
If you manage to make the above work, you will be able to figure out the NAT rules for your existing network. Basically, you want to NAT to the new range of addresses using the old existing NAT rule that NAT's to the the old block. The old existing NAT rule should include the new block that should be declared in the the Network Objects.
Hope this helps.
ASKER
Hi Szichen,
Thanks for the followup response. Since this firewall is at a co-location facility I am going to have schedule a trip out there but in the meantime I was re-reading you post and notice your comment about NAT translating the new block of IPs. I pretty much work out of the ASDM so just curious how I would go about doing the NAT translating the new block as I think that might be my issue...
Thanks for the followup response. Since this firewall is at a co-location facility I am going to have schedule a trip out there but in the meantime I was re-reading you post and notice your comment about NAT translating the new block of IPs. I pretty much work out of the ASDM so just curious how I would go about doing the NAT translating the new block as I think that might be my issue...
ASKER
I should clarify that last statement that we already have a network ojbect outside network with our existing range of IPs. do I modify that object to include the new range of IPs or do I create a new network ojbect with the new range and use that in the access rule/NAT rule for the internal server?
Hi EA-170,
Yes, I actually meant for you to do it this way i.e. delare the new range of IPs in the existing range - sorry if it wasn't clear. The testing bit is good to understand how the NAT-ing works.
Once you declare the new IPs in the existing range on the NAT rule and "Apply" the changes, there is nothing else that needs to be done.
Sorry forgot to ask if you still need to know how to make changes to the NAT rule through ASDM? Just look for an existing NAT rule with the the public IP range and add the new bloc to that range.
Yes, I actually meant for you to do it this way i.e. delare the new range of IPs in the existing range - sorry if it wasn't clear. The testing bit is good to understand how the NAT-ing works.
Once you declare the new IPs in the existing range on the NAT rule and "Apply" the changes, there is nothing else that needs to be done.
Sorry forgot to ask if you still need to know how to make changes to the NAT rule through ASDM? Just look for an existing NAT rule with the the public IP range and add the new bloc to that range.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Great! Thanks for the feedback.
ASKER
was able to resolve the issue from another source.
If you understand how NAT-ing works then all you need to do to make use of those public IPs is declare the new block of addresses in the network objects and add these to existing natting rules.
If the new block is for a new service on a new interface (on a new LAN) then a new NAT rule needs to be created for that new Interface and NATed to the new declared network objects for new block of public IP addresses.
If you are not sure, test the NAT rule on an unused Interface for Internet connection and check your IP once you get connectivity. Go to google and type "My IP". you should see an IP address that is from the new block the ISP gave you.
NOTE:
- The source interface is the Interface the traffic is coming from Internally
- The destination Interface is the existing Interface which has your old Public IP
- The translated address will be the new Public IP declared in the Network Objects.