NIC Teaming with Cisco switch
did you configure "interface portgroup 1?"
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
It looks like i am missing the switchport trunk native vlan 4094
Are you using VLAN 4094 ?
ASKER
No I am not using vlan 4094.
On a Cisco switch the native vlan is 1 by default, and you can change it. It has to match on both sides but should NOT be a vlan you use for data. This is for the 802.1q aspect, not the channel itself but everything has to match. Channeling on cisco requires the virtual interface port-channel 1, where the interface number matches the port group you are using. The configuration you put on the virtual interface will flow to the physical ports. since you've already configured the physical ports, just make the attributes identical.
So if you are not using VLAN 4094, why would you add it ?
You need to check the Article I posted, to setup Load Balancing, and Port Channel!
You need to check the Article I posted, to setup Load Balancing, and Port Channel!
ASKER
the article says to add vlan 4094
ASKER
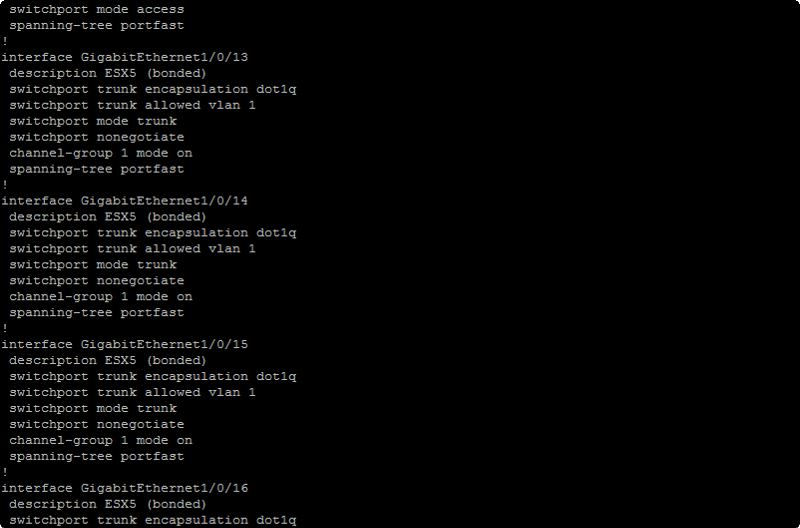
The following configuration works but can someone explain why the command:
switchport trunk native vlan 600
is necessary?
interface Port-channel1
switchport trunk encapsulation dot1q
switchport trunk native vlan 600
switchport trunk allowed vlan 10
switchport mode trunk
switchport nonegotiate
interface GigabitEthernet1/0/1
switchport trunk encapsulation dot1q
switchport trunk native vlan 600
switchport trunk allowed vlan 10
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
spanning-tree portfast
!
interface GigabitEthernet1/0/2
switchport trunk encapsulation dot1q
switchport trunk native vlan 600
switchport trunk allowed vlan 10
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
spanning-tree portfast
switchport trunk native vlan 600
is necessary?
interface Port-channel1
switchport trunk encapsulation dot1q
switchport trunk native vlan 600
switchport trunk allowed vlan 10
switchport mode trunk
switchport nonegotiate
interface GigabitEthernet1/0/1
switchport trunk encapsulation dot1q
switchport trunk native vlan 600
switchport trunk allowed vlan 10
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
spanning-tree portfast
!
interface GigabitEthernet1/0/2
switchport trunk encapsulation dot1q
switchport trunk native vlan 600
switchport trunk allowed vlan 10
switchport mode trunk
switchport nonegotiate
channel-group 1 mode on
spanning-tree portfast
do you have other devices on VLAN 600, that would be the only reason it's needed!
because all traffic on this trunk to ESXi, is going over VLAN 600.
which must mean other ports on this switch also have this VLAN!
because all traffic on this trunk to ESXi, is going over VLAN 600.
which must mean other ports on this switch also have this VLAN!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
C4H3750G-24#sh int trunk
Port Mode Encapsulation Status Native vlan
Gi1/0/21 on 802.1q trunking 1
Gi1/0/22 on 802.1q trunking 1
Gi1/0/23 on 802.1q trunking 1
Gi1/0/24 on 802.1q trunking 1
Po1 on 802.1q trunking 600
Port Vlans allowed on trunk
Gi1/0/21 1,50,150
Gi1/0/22 1,50,150
Gi1/0/23 1,50,150
Gi1/0/24 1,50,150
Po1 1
Port Vlans allowed and active in management domain
Gi1/0/21 1,50,150
Gi1/0/22 1,50,150
Gi1/0/23 1,50,150
Gi1/0/24 1,50,150
Po1 1
Port Vlans in spanning tree forwarding state and not pruned
Gi1/0/21 1,50,150
Gi1/0/22 1,50,150
Gi1/0/23 1,50,150
Gi1/0/24 1,50,150
Po1 1
Port Mode Encapsulation Status Native vlan
Gi1/0/21 on 802.1q trunking 1
Gi1/0/22 on 802.1q trunking 1
Gi1/0/23 on 802.1q trunking 1
Gi1/0/24 on 802.1q trunking 1
Po1 on 802.1q trunking 600
Port Vlans allowed on trunk
Gi1/0/21 1,50,150
Gi1/0/22 1,50,150
Gi1/0/23 1,50,150
Gi1/0/24 1,50,150
Po1 1
Port Vlans allowed and active in management domain
Gi1/0/21 1,50,150
Gi1/0/22 1,50,150
Gi1/0/23 1,50,150
Gi1/0/24 1,50,150
Po1 1
Port Vlans in spanning tree forwarding state and not pruned
Gi1/0/21 1,50,150
Gi1/0/22 1,50,150
Gi1/0/23 1,50,150
Gi1/0/24 1,50,150
Po1 1
ASKER
There is no vlan 600. The network currently consists of only vlan 1. We are in the process of adding vlans 10(servers), 50(workstations), and 150(voice). vlan 600 was added in an effort to get the esx teamed nics to communicate with the switch. the article used 4094, I didn't know if the number mattered. This network grew from a developmental project to a now production network and switch architecture and security was never a thought. So now we see the poor design and are trying to fix it. We have purchased new switches and will be migrating soon. I am trying to understand the configuration on the switches before it is moved so I can migrate as smoothly as possible. I am trying to learn networking and run the business in an effort to keep costs down so thank you for your help.
You must have 600 configured somewhere on your physical switches.
As all traffic entering the physical switch from ESXi, is untagged on VLAN 600, which will then be sent to other network switches.
There is no requirement for VLANs unless you are using them, e.g. teaming/load balancing is nothing to do with VLANs.
As all traffic entering the physical switch from ESXi, is untagged on VLAN 600, which will then be sent to other network switches.
There is no requirement for VLANs unless you are using them, e.g. teaming/load balancing is nothing to do with VLANs.
ASKER
If Cisco uses 1 as the native vlan, why is it necessary to add the command (switchport trunk native vlan 600) to the port channel and the interfaces in the port group? Without that command traffic was not passing. 600 was simply a number that was chosen out of the air for no particular reason. Like I stated earlier, the article chose 4094.
4094, should not be used either.
if 600 was just chosen and it worked.....
this is not defined anywhere else ? on any other port ?
if 600 was just chosen and it worked.....
this is not defined anywhere else ? on any other port ?
ASKER
Attached is the configuration of the 3750 switch. There are 2 other 2900 switches connected to this switch as well but there is only the default vlan 1 on them. The ESX servers only have vlan 1 as well. 600 is defined on the ports that are part of the port group.
sh-run-04012015.txt
sh-run-04012015.txt
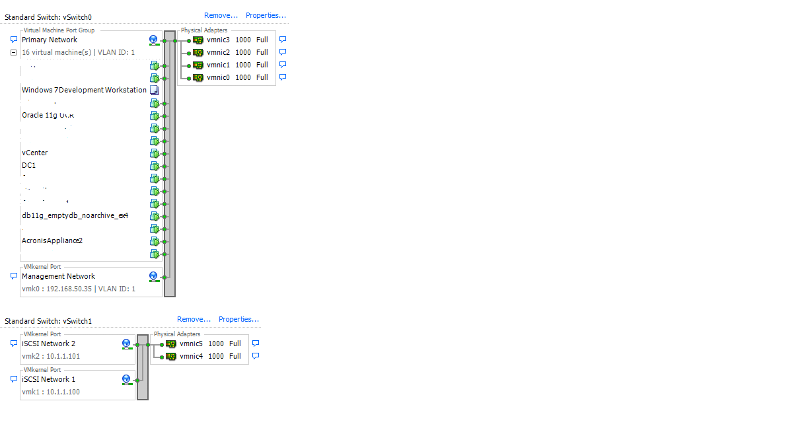
Can you upload a screenshot of your vSwitch configuration.
VLAN 1 should not be used in VMware vSphere.
VLAN 1 should not be used in VMware vSphere.
Okay first things, remove the VLAN Tag of 1, on the portgroups, and remove all other VLAN Tags.
Do not use 1. It's special.
Then do you need to use vLANs ?
Do not use 1. It's special.
Then do you need to use vLANs ?
ASKER
I need a vlan for my data and another for the IP voice system we are installing shortly. I wanted a vlan for the servers and another for workstations.
10 servers
50 workstations
150 voice
10 servers
50 workstations
150 voice
okay, so create three virtual machine portgroups
Servers with Tag of 10
Workstations with Tag of 50
Voice with a Tag of 50
and then you will need to specify all those on the trunks.
But all those Servers, Workstations and Voice devices WILL NOT be able to communicate unless your switch or routers can do inter vlan routing!
Servers with Tag of 10
Workstations with Tag of 50
Voice with a Tag of 50
and then you will need to specify all those on the trunks.
But all those Servers, Workstations and Voice devices WILL NOT be able to communicate unless your switch or routers can do inter vlan routing!
ASKER
When I removed the vlan1 tag from the port group I lost connectivity to the vm's. do I need to do something with the port group on the switch as well? I don't have the vlan1 tag on the other ESX servers. It is only on the ESX server that has the bonded nic's.
lets start simple, remove the teaming, and bonded nics, and just use a single access port on the switch, and no teaming at present.
no VLAN1.
how are other ESX servers configured.
no VLAN1.
how are other ESX servers configured.
I still think that somewhere, maybe in the initial ESXi host configuration, vlan 600 is assigned to ports. There is no reason on earth that vlan600 can be required on the switch unless it exists somewhere in the host or vm config.
you might try getting on the host console and see if you can find vlan600 in there somewhere.
you might try getting on the host console and see if you can find vlan600 in there somewhere.
ASKER
I removed the port group on the switch, teaming and vlan 1 from ESX. I still cannot find vlan 600 anywhere on the host or vm.
Okay, so you have now created a single vSwitch, with a single physical nic uplink, with no vLAN Tag.
Can the VMs ping the host?
Can the VMs ping the default gateway ?
Do you have a flat (e.g. no VLANs) or VLAN network ?
Can the VMs ping the host?
Can the VMs ping the default gateway ?
Do you have a flat (e.g. no VLANs) or VLAN network ?
ASKER
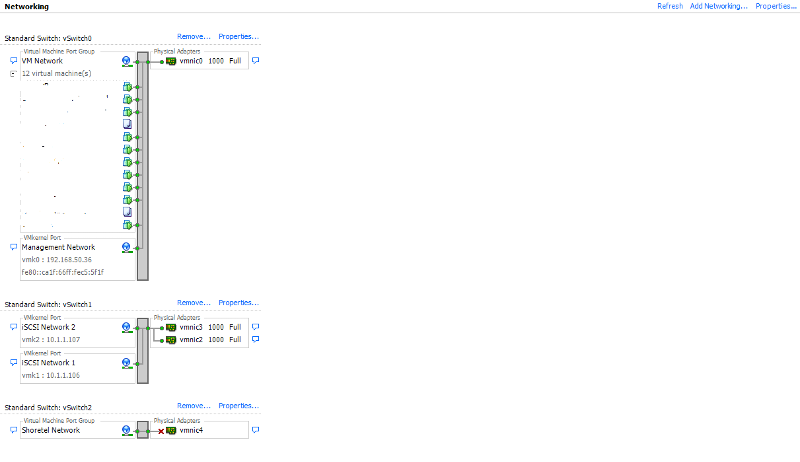
I had it all working on a single nic like you recommended then I recreated the port group with vlan 600 and it works! Everything is currently working on a flat network(vlan1). I have vlans created on the switch and would like to put all the vm's on the ESX host's into vlan 10. These are all of the servers on the network. the client pc's are all physical and will be part of vlan 50 and the IP phones in vlan 150. If I connect the ESX nic to a trunk port on the switch, do I simply edit the port group with vlan 10 on the ESX side? Is it necessary to create port groups for vlans 50 and 150 if there will be no vm's on them? The switch is configured to route to the vlans created.
Yes, create new portgroups with the VLAN Tag, e.g. 10, 50 and 150.
Do you have other virtual and physical servers, workstations, and devices, that are also on these VLANs on other physical switches ?
If Servers and Workstations needs to exchange data, this needs to be routed! - ?
where is this happening?
do you have physical servers and workstatoons currently working on these vLANS?
remember to create a trunk with at least two nics, and add these VLANS e.g. 10, 50, and 150
Do you have other virtual and physical servers, workstations, and devices, that are also on these VLANs on other physical switches ?
If Servers and Workstations needs to exchange data, this needs to be routed! - ?
where is this happening?
do you have physical servers and workstatoons currently working on these vLANS?
remember to create a trunk with at least two nics, and add these VLANS e.g. 10, 50, and 150
ASKER
I created the trunk with 2 nics and used the command "switchport trunk allowed vlan all ". The plan is to have a switch for workstations and assign access ports on vlan 50. A separate switch for IP phones and assign access ports on vlan 150. these switches will connect to 3750 switch via trunk port. ESX servers will connect to 3750 via trunk port as well. Routing is done on 3750 switch. This is probably a dumb question but, why do I need to create a port group with vlan 50 and 150 if there will be no vm's assigned to them?
Oh, if you have no VMs, there is no requirement to create a VLAN for them, but sometimes we do it, as it's nice to have for testing!
ASKER
Thank you both for your knowledge and patience.
No problems, that is what learning is all about.
A pleasure!
A pleasure!