hannibalsmith
asked on
Unable to see account lockout policy in GPMC
Hi,
I need to verify the settings and winning GPO for the domain account lockout policy. If I run group policy modelling or gpresult, I can get all other computer settings but NOT account lockout policy. here's what I've tried:
1) tested on PDC emulator (i.e. on two DCs and got the same result. One is 2003 R2 and one 2008 R2)
2) ran gpmc explicitly as administrator
3) tried scoping group policy modelling to both the entire domain and the computers container
I've probably tried other things, but it's been a long day :)
I can get the settings from net accounts /domain but I need to prove where the originated (I can do this by manually going through GPMC but I would like to see the results displayed in a report)
The settings ARE being applied, so this is purely a reporting issue of some kind
Forest functional level is 2003
hope someone can help!
I need to verify the settings and winning GPO for the domain account lockout policy. If I run group policy modelling or gpresult, I can get all other computer settings but NOT account lockout policy. here's what I've tried:
1) tested on PDC emulator (i.e. on two DCs and got the same result. One is 2003 R2 and one 2008 R2)
2) ran gpmc explicitly as administrator
3) tried scoping group policy modelling to both the entire domain and the computers container
I've probably tried other things, but it's been a long day :)
I can get the settings from net accounts /domain but I need to prove where the originated (I can do this by manually going through GPMC but I would like to see the results displayed in a report)
The settings ARE being applied, so this is purely a reporting issue of some kind
Forest functional level is 2003
hope someone can help!
Why haven't you ran rsop.msc ??
You should be able to drill right down to it with rsop
You should be able to drill right down to it with rsop
The "Default Domain Policy" holds the Account Lock policy. Have you treid gpresult /R >> c:\output.txt
Will.
Will.
ASKER
Hi, thank for the answers.
1)@dstewartjr RSOP.msc has known issues. It's not a tool I find reliable. I think it might be deprecated? That said, i'll try anything so thank you for your suggestion. I tried it and didn't get the results I need.
2) @Will in this case, it's not the default domain policy. That does have a lockout value threshold but it's not the one which is enforced. The enforced settings are coming from another policy. I can see the settings but I want to generate a report
3) @mcknife, thanks for the suggestion. tried that but still not getting them.
any other ideas?
1)@dstewartjr RSOP.msc has known issues. It's not a tool I find reliable. I think it might be deprecated? That said, i'll try anything so thank you for your suggestion. I tried it and didn't get the results I need.
2) @Will in this case, it's not the default domain policy. That does have a lockout value threshold but it's not the one which is enforced. The enforced settings are coming from another policy. I can see the settings but I want to generate a report
3) @mcknife, thanks for the suggestion. tried that but still not getting them.
any other ideas?
ASKER
hi there,
yes, that's what i''m looking for but it's not working on my DCs...
RSOP has known issues. I didn't say it never worked :)
when I run RSOP, I get 'not defined' where you see the values in your RSOP output.
yes, that's what i''m looking for but it's not working on my DCs...
RSOP has known issues. I didn't say it never worked :)
when I run RSOP, I get 'not defined' where you see the values in your RSOP output.
ASKER
do you get the same result when you run it as domain admin on your DC?
what about in group policy modelling?
what about in group policy modelling?
do you get the same result when you run it as domain admin on your DC?
Yup, same result
"group policy modelling?"
Honestly dont use that tool
ASKER
so, here's the output I get when i'm logged onto a system which has the GPO containing the account lockout settings applied to it. I've also tried on the FSMO holder and got the same result.
ASKER
it's a strange one. I can see that you're right but it's just not working for me. that's why i'm here. if it was easy, I wouldn't be :-D
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
thanks, I've already reviewed that one but ill give you the points for your assistance. i'm sure we'll work together again at some point!
there's some nutty filtering going on which is not visible from the GPMC. I'm dealing with a lot of environments and this one has a mix of all sorts of OS levels. thanks for the help!
there's some nutty filtering going on which is not visible from the GPMC. I'm dealing with a lot of environments and this one has a mix of all sorts of OS levels. thanks for the help!
ASKER
Dstewartjr offered a lot of help on this case
@Will in this case, it's not the default domain policy.That is exactly why it is not working then. Any password policy related settings NEED to be in the Default Domain Policy as i have stated already.
The only exception is when you are using PSO/Fine Grained Password Policies and you are applying them to a specific group or OU. To do this you need to have a FFL and DFL of 2008 or higher.
Any other situation it will not work. Has to be on the Default Domain Policy.
yes, that's what i''m looking for but it's not working on my DCs...This will not work because it is not set in the correct place.
Will.
I wouldn't close it yet. There cannot be some "nutty filtering" going on - or did you indeed filter the default domain policy not to apply to your DCs?
Or was "Authenticated Users" removed ???
ASKER
nope, authenticated users was in there.
I didn't filter the DCs out. I'm not sure what happened actually. I didn't set this site up. it's one of about 130 that I manage so i'll need to hunt around to be honest.
I'm going to look into it and if I find something i'll post so other people reading this know what happened.
really appreciate the help, guys!
I didn't filter the DCs out. I'm not sure what happened actually. I didn't set this site up. it's one of about 130 that I manage so i'll need to hunt around to be honest.
I'm going to look into it and if I find something i'll post so other people reading this know what happened.
really appreciate the help, guys!
ASKER
@will
'That is exactly why it is not working then. Any password policy related settings NEED to be in the Default Domain Policy as i have stated already.'
sorry, just saw this now. I'm sure it's best practice, but the lockout policy which IS working on this domain is not set at the default domain policy. It's set at another policy. Do you have any documentation that states that domain lockout policy MUST be set at the default domain policy level?
'That is exactly why it is not working then. Any password policy related settings NEED to be in the Default Domain Policy as i have stated already.'
sorry, just saw this now. I'm sure it's best practice, but the lockout policy which IS working on this domain is not set at the default domain policy. It's set at another policy. Do you have any documentation that states that domain lockout policy MUST be set at the default domain policy level?
While at work, I had an idea. now at home, virtual test domain started, I could verify it. I guess you will find it most interesting. The following picture shows, that the command
net accounts /domain
when executed at the DC does not reflect the same as RSOP.msc and I guess that's what you have.
The cause is that the def dom pol is left unconfigured while the local policy secpol.msc (see top) IS configured.
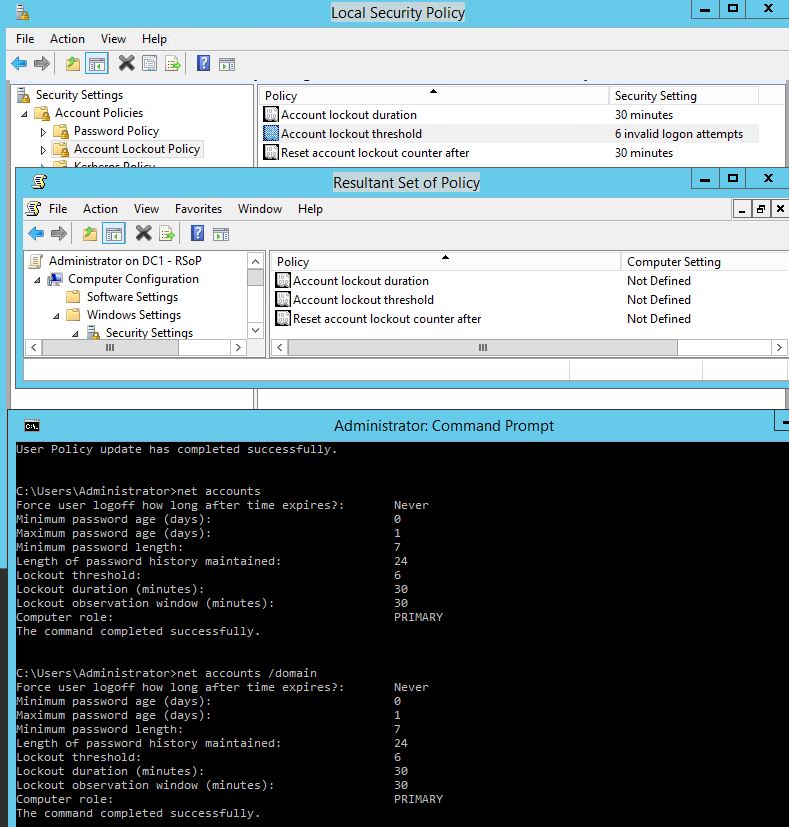
net accounts /domain
when executed at the DC does not reflect the same as RSOP.msc and I guess that's what you have.
The cause is that the def dom pol is left unconfigured while the local policy secpol.msc (see top) IS configured.
ASKER
that's very interesting. thank you, mcknife.
I've actually recreated the GPO from scratch and just copied the existing settings. It now works correctly so I suppose we were looking a policy corruption or maybe an attribute which wasn't quite right in adsiedit.
thanks for the info above, though. if I had more points to allocate, you'd certainly get them. I hadn't considered the interplay between default domain and local security. In my case, default domain did have values configured but the values received by clients were coming from another policy with those values configured as well.
I've actually recreated the GPO from scratch and just copied the existing settings. It now works correctly so I suppose we were looking a policy corruption or maybe an attribute which wasn't quite right in adsiedit.
thanks for the info above, though. if I had more points to allocate, you'd certainly get them. I hadn't considered the interplay between default domain and local security. In my case, default domain did have values configured but the values received by clients were coming from another policy with those values configured as well.
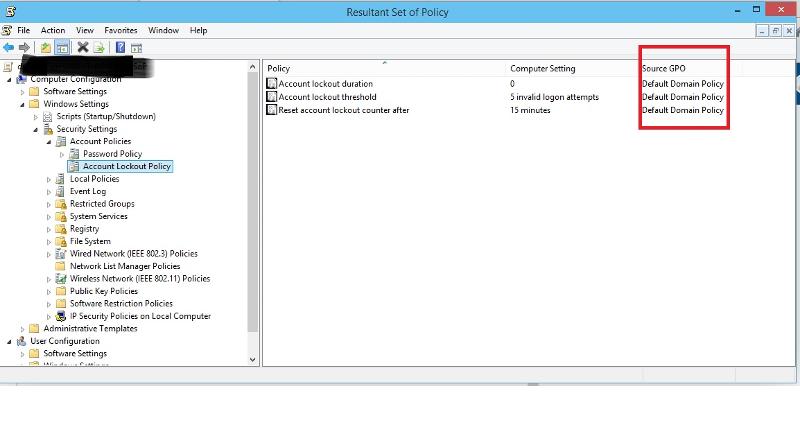
Do a
gpresult /h %temp%\result1.html
on your DC and then open %temp%\result1.html