FireBall
asked on
should juniper make a mistake on process ?
We have made a few test about UDP flood attack
We have set up Screen UDP thresold limit to 50K and we have put a firewall term which block the ip address of attacker.
we have checked what if the term is working or not , it is working. Attacker pc could not ping the victim pc.
Then we start to UDP flood attack which directly send 40byte packets without hiding ip address of the attack machine.
Simply codes as given below.
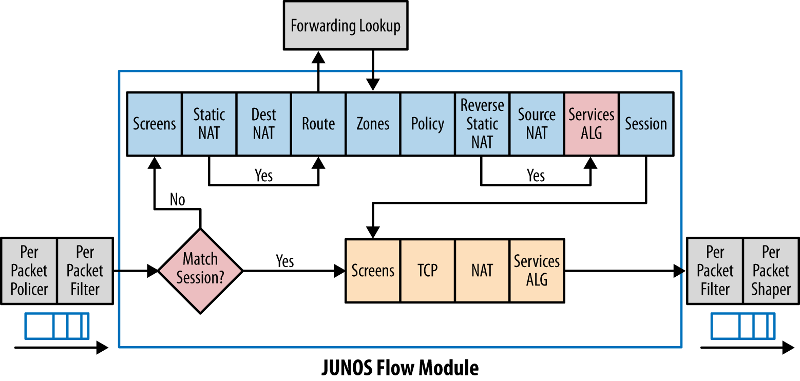
depending on the image given below, juniper must apply filter first then screen rules . so attacker will be blocked by the firewall term and session counter will not overflow the udp threshold.
But it does not happen. screen counter go on blocking why ?
We have set up Screen UDP thresold limit to 50K and we have put a firewall term which block the ip address of attacker.
we have checked what if the term is working or not , it is working. Attacker pc could not ping the victim pc.
Then we start to UDP flood attack which directly send 40byte packets without hiding ip address of the attack machine.
Simply codes as given below.
depending on the image given below, juniper must apply filter first then screen rules . so attacker will be blocked by the firewall term and session counter will not overflow the udp threshold.
But it does not happen. screen counter go on blocking why ?
xe-1/0/0 {
description Uplink;
unit 0 {
family inet {
rpf-check {
fail-filter rpf-filter;
mode loose;
}
filter {
input BlokKural;
output blocked.IP;
}
address 37.123.100.122/29;
}
}
}
policy-options {
prefix-list block.zeusCC {
43.255.180.0/24;
43.255.184.0/24;
43.255.190.0/24;
43.255.191.0/24;
61.168.229.0/24;
182.100.64.0/24;
182.100.67.0/24;
185.9.156.2/32;
218.65.24.0/24;
}
prefix-list unblock.zeusCC;
}
firewall {
family inet {
filter BlokKural {
term 1 {
from {
prefix-list {
block.zeusCC;
unblock.zeusCC except;
}
}
then {
count BlockedIP;
syslog;
discard;
}
}
term 2 {
from {
packet-length 0-30;
protocol udp;
}
then {
count jova;
log;
syslog;
discard;
}
}
term 500 {
then accept;
}
}

root@srx3600.spd.net.tr> show security screen statistics zone DisNetwork
Screen statistics:
IDS attack type Statistics
ICMP flood 0
UDP flood 590128
TCP winnuke 0
TCP port scan 0
ICMP address sweep 0
TCP sweep 0
UDP sweep 0
IP tear drop 0
TCP SYN flood 0
IP spoofing 0
ICMP ping of death 0
IP source route option 0
TCP land attack 0
TCP SYN fragment 0
TCP no flag 0
IP unknown protocol 0
IP bad options 0
IP record route option 0
IP timestamp option 0
IP security option 0
IP loose source route option 0
IP strict source route option 0
IP stream option 0
ICMP fragment 0
ICMP large packet 0
TCP SYN FIN 0
TCP FIN no ACK 0
Source session limit 0
TCP SYN-ACK-ACK proxy 0
IP block fragment 0
Destination session limit 0ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Open in new window
Open in new window