CnicNV
asked on
Allowing access to a single internal computer for a small block of public IP addresses using Cisco ASDM?
Hi, I am trying to use the Cisco ASDM to simply add a ACL (supported by a NAT) to allow traffic to and from a single internal IP to a select group of public IP addresses.
What is the best way to do this? Note I want to use the GUI. Command line is cool, but I don't use this thing enough to care to use the command line or internalize all of these commands. Plus, I like the GUI as I can better visualize the context of things I am trying to do and how they relate to existing things.
I can see in source for access rules, there is a default to any, but it looks like you can pick and tailor things. Of some of the options, it just lists a bunch of internal networks. Is there a way that I can manually add a public IP address network ID and corresponding network mask? IE to say, allow traffic to this internal server, but only from these IPs?
Thanks
What is the best way to do this? Note I want to use the GUI. Command line is cool, but I don't use this thing enough to care to use the command line or internalize all of these commands. Plus, I like the GUI as I can better visualize the context of things I am trying to do and how they relate to existing things.
I can see in source for access rules, there is a default to any, but it looks like you can pick and tailor things. Of some of the options, it just lists a bunch of internal networks. Is there a way that I can manually add a public IP address network ID and corresponding network mask? IE to say, allow traffic to this internal server, but only from these IPs?
Thanks
Do you have existing access-list configured on your inside interface? By default, all traffic coming from inside (higher security) going to outside (lower-security) are allowed. This is important to note since adding a specific access-list (ACL) on the inside interface will change this default behavior in that only implicitly specified traffic will be allowed and all all other traffic not specified will be filtered (drop).
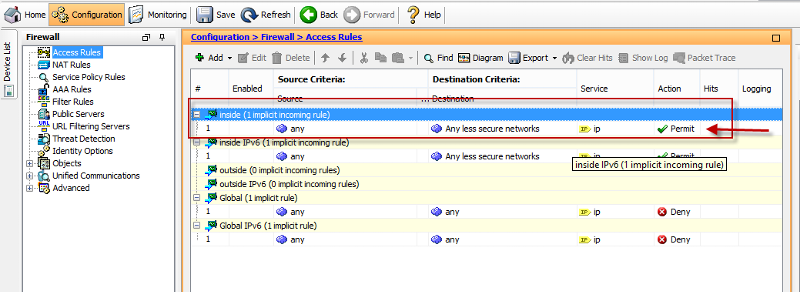 To add a specific rule just do the following:
To add a specific rule just do the following:
 A permit any any is added, but at this point consider putting a more specific ACL.
A permit any any is added, but at this point consider putting a more specific ACL.
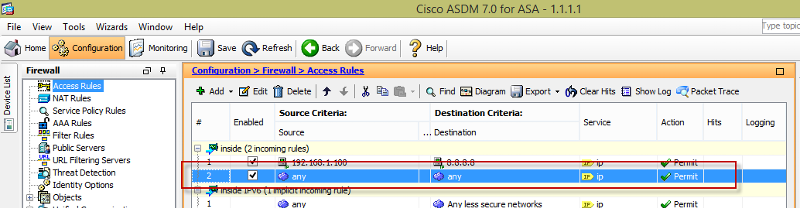 Hope this helps and let me know if you have further questions, I'll be glad to help out.
Hope this helps and let me know if you have further questions, I'll be glad to help out.
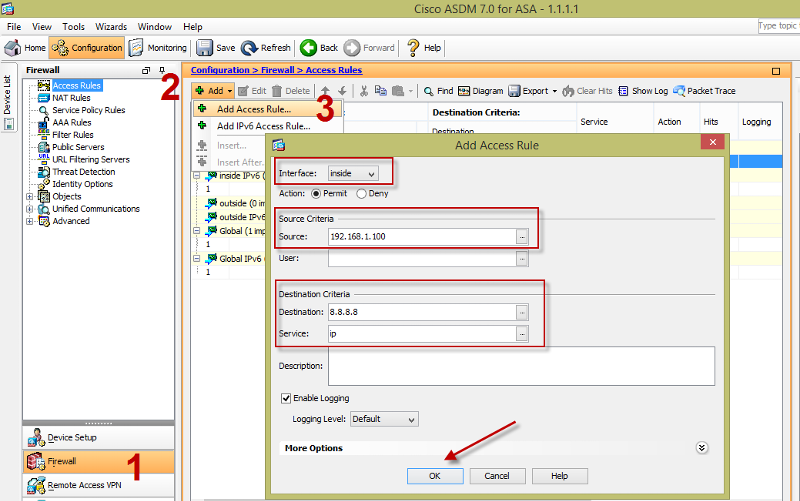
 To add a specific rule just do the following:
To add a specific rule just do the following:
specify interface
specify source, this can be a specific host or a subnet
specify destination, this can be a specific host or a subnet
specify port, you can be granular by specifying tcp/80, or tcp/443, depending on your need
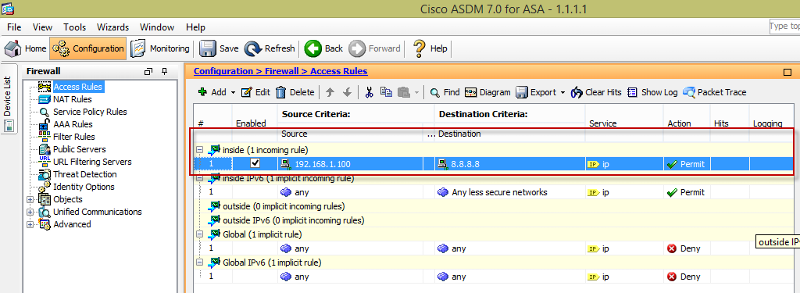
Notice below that after adding the ACL the default allow is now gone. This can cause issue if you don't specify another ACL allowing traffic for other source and destination: A permit any any is added, but at this point consider putting a more specific ACL.
A permit any any is added, but at this point consider putting a more specific ACL. Hope this helps and let me know if you have further questions, I'll be glad to help out.
Hope this helps and let me know if you have further questions, I'll be glad to help out.
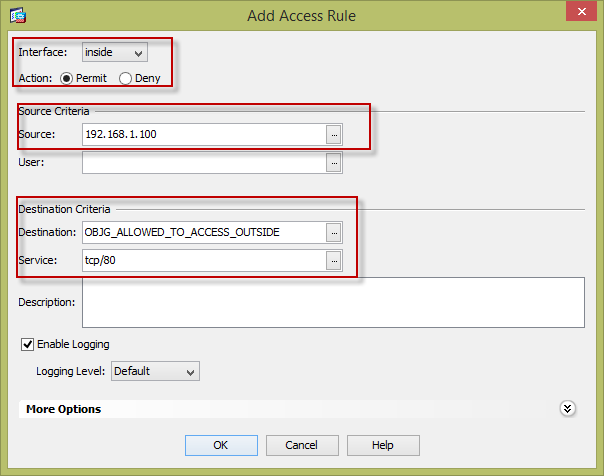
You can also use an object-group instead of specifying individual IP address. First create an object-group as shown below.
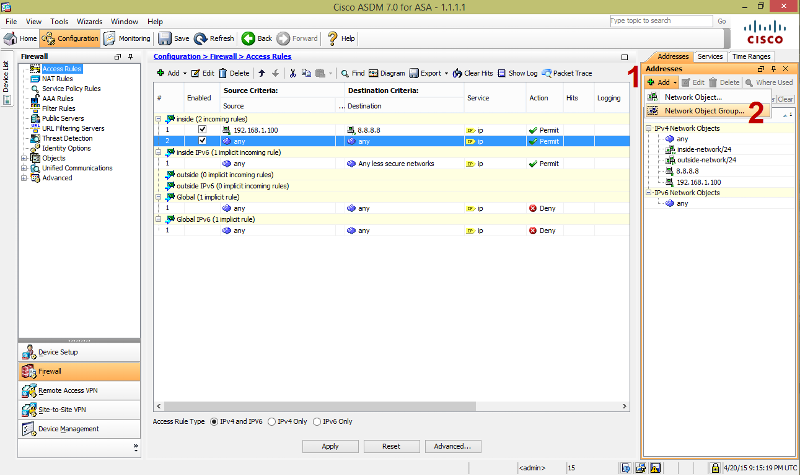 Place a name for your object-group and specify what IPs are inside the object group. You can specify either by host, range, or network as shown below.
Place a name for your object-group and specify what IPs are inside the object group. You can specify either by host, range, or network as shown below.
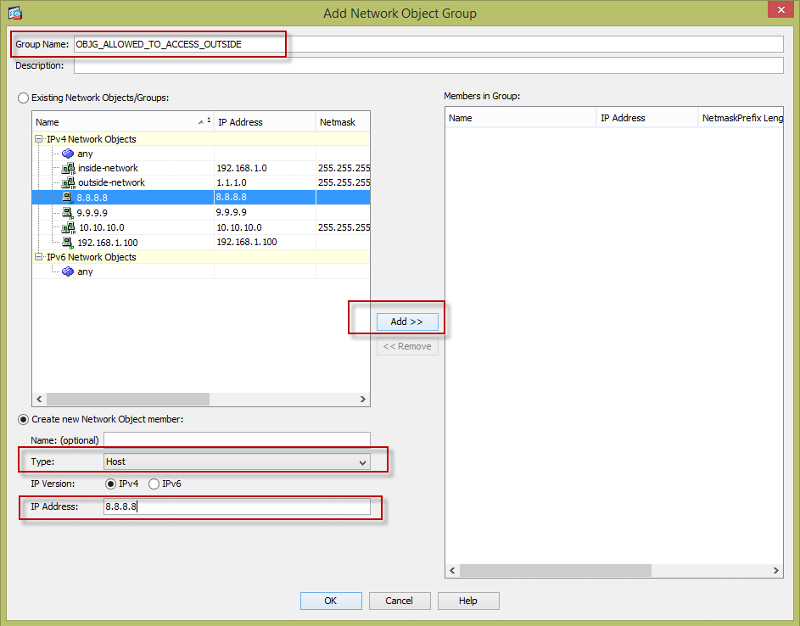
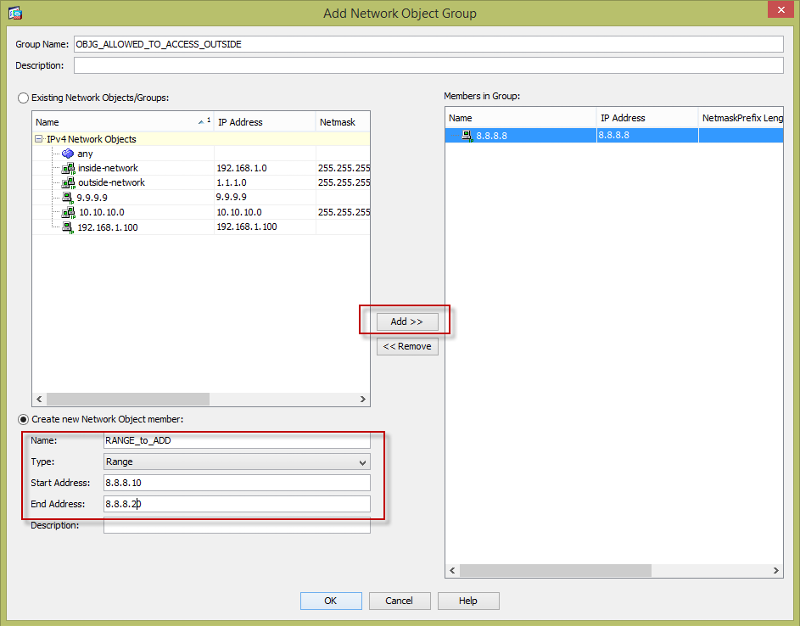
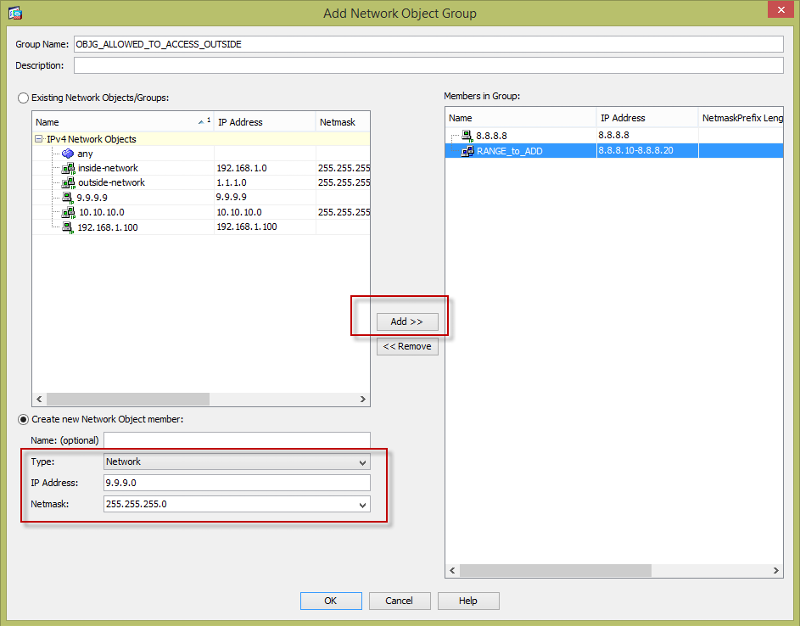 Then create an ACL using the configured object-group
Then create an ACL using the configured object-group
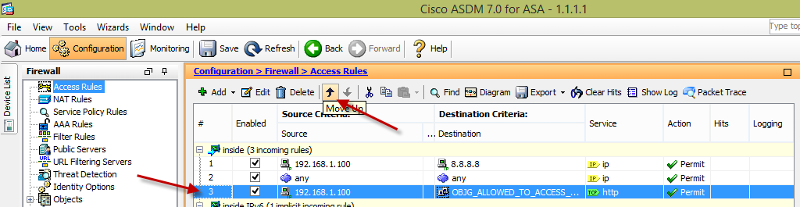
 You can move up/down the order of the ACL as shown below. This is important if you have deny ACLs, you'll need to move the allowed permit ACL on top of the deny to allow traffic.
You can move up/down the order of the ACL as shown below. This is important if you have deny ACLs, you'll need to move the allowed permit ACL on top of the deny to allow traffic.
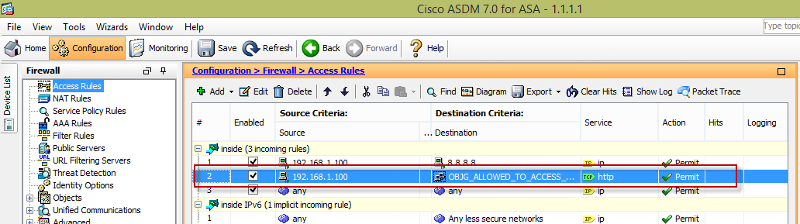
 Place a name for your object-group and specify what IPs are inside the object group. You can specify either by host, range, or network as shown below.
Place a name for your object-group and specify what IPs are inside the object group. You can specify either by host, range, or network as shown below.

 Then create an ACL using the configured object-group
Then create an ACL using the configured object-group You can move up/down the order of the ACL as shown below. This is important if you have deny ACLs, you'll need to move the allowed permit ACL on top of the deny to allow traffic.
You can move up/down the order of the ACL as shown below. This is important if you have deny ACLs, you'll need to move the allowed permit ACL on top of the deny to allow traffic.

ASKER
Your second post seems interesting. I tried to follow it and it threw up a bunch of errors, which I will post and anonymize later if required.
Generally the errors are of the syntax type, IE it doesn't seem to like my formatting, invalid marker detected at "description XYZ" and "subnet XYZ" and "invalid host name XYZ, INFO: A host name must start and end with a letter or digit, and have interior characters only letters, digits, or a hyphen"....Which it does, it's just a public IP address. It's strange that the command line would throw up these syntax and formatting issues if the ASDM GUI is the one executing the commands, its like Cisco would have sanity tested this. So I am thinking it's a logical error on my part.
So I am wondering if there error is occurring because I am trying to apply this to the outside interface and as a source, not as a destination. That is to say, a small range of public IPs are allowed to access a specific internal server.
Thanks.
Generally the errors are of the syntax type, IE it doesn't seem to like my formatting, invalid marker detected at "description XYZ" and "subnet XYZ" and "invalid host name XYZ, INFO: A host name must start and end with a letter or digit, and have interior characters only letters, digits, or a hyphen"....Which it does, it's just a public IP address. It's strange that the command line would throw up these syntax and formatting issues if the ASDM GUI is the one executing the commands, its like Cisco would have sanity tested this. So I am thinking it's a logical error on my part.
So I am wondering if there error is occurring because I am trying to apply this to the outside interface and as a source, not as a destination. That is to say, a small range of public IPs are allowed to access a specific internal server.
Thanks.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ok thanks for all of the info. Unfortunately currently I will be unable to play around with this all that much. Also I suspect I am having these syntax errors because of the version I am on, which is older than yours. So I would probably have to upgrade things before I could reasonably expect to get the same results as you.
But logically speaking, the information you have provided seem really good.
Thanks again.
But logically speaking, the information you have provided seem really good.
Thanks again.