Shark Attack
asked on
Failover config
Hello,
I have a question in regards to HSRP and IP SLA. What would be the difference if I implemented HSRP between the DSW1 and DSW2 instead of IP SLA on ASW1 and ASW2 for failover? Please see attached image.
IP SLA with tracking would tract my interfaces and if "down" it would failover to the other switch, isn't that what I would get from HSRP?
What would be the better case? HSRP or IP SLA with failover?
I will have EIGRP configured on the switches.
hsrp-nuggets.jpg
I have a question in regards to HSRP and IP SLA. What would be the difference if I implemented HSRP between the DSW1 and DSW2 instead of IP SLA on ASW1 and ASW2 for failover? Please see attached image.
IP SLA with tracking would tract my interfaces and if "down" it would failover to the other switch, isn't that what I would get from HSRP?
What would be the better case? HSRP or IP SLA with failover?
I will have EIGRP configured on the switches.
hsrp-nuggets.jpg
ASKER
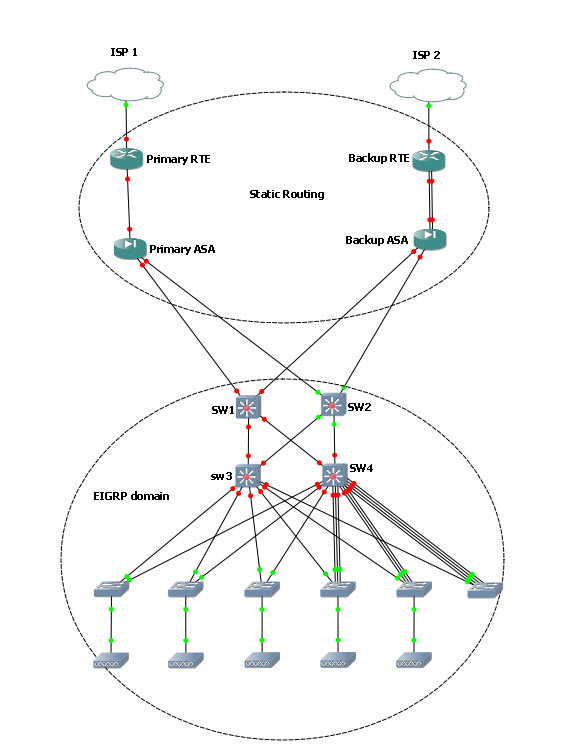
If you look at the below image, it's my actual structure that I will be implementing. EIGRP will be on all switches in the image including the Access layer switches which are L3's as well. Anything above SW1 and SW2 will run static routing.
SW1's interface to Primary ASA has different IP then the SW2's interface to backup ASA. So will EIGRP be sufficiant enough in this topology since I have 2 different ISP's and different IP schemes between the primary and backup ASA and router?
Here is what I want to accomplish:
1. I want SW3 and SW4 to re-route it's self in case SW1 or SW2 fails to it's respective switch. For ex. if SW1 fails, traffic will get re-routed to SW2. I am assuming this will actually be done via EIGRP at this particular stage.
2. If SW1 fails, I want traffic to get routed to SW2 and back to Primary ASA instead of Backup ASA. How would I accomplish that? IP SLA with tracking? HSRP?
3. If Primary ASA fails, traffic gets re-routed from SW1 to Backup ASA. How would I accomplish that? IP SLA with tracking? HSRP?
Also, one last thing, SW1 is a primary Switch, it has all VLans and it's IP's configured, I am running VTP, when I go to SW2 or SW4 for example, and I do show int vlan 5 let's say, its shows UP and UP but no ip address of the vlan is displayed (which is normal) But what happens if SW1 shuts down, all vlans show up and up but I am unable to ping any vlan. how could I ocnfigure vlans on another switch like SW2 so that if SW1 shuts down, I still have functional Vlans everywhere else?
thank you!
SW1's interface to Primary ASA has different IP then the SW2's interface to backup ASA. So will EIGRP be sufficiant enough in this topology since I have 2 different ISP's and different IP schemes between the primary and backup ASA and router?
Here is what I want to accomplish:
1. I want SW3 and SW4 to re-route it's self in case SW1 or SW2 fails to it's respective switch. For ex. if SW1 fails, traffic will get re-routed to SW2. I am assuming this will actually be done via EIGRP at this particular stage.
2. If SW1 fails, I want traffic to get routed to SW2 and back to Primary ASA instead of Backup ASA. How would I accomplish that? IP SLA with tracking? HSRP?
3. If Primary ASA fails, traffic gets re-routed from SW1 to Backup ASA. How would I accomplish that? IP SLA with tracking? HSRP?
Also, one last thing, SW1 is a primary Switch, it has all VLans and it's IP's configured, I am running VTP, when I go to SW2 or SW4 for example, and I do show int vlan 5 let's say, its shows UP and UP but no ip address of the vlan is displayed (which is normal) But what happens if SW1 shuts down, all vlans show up and up but I am unable to ping any vlan. how could I ocnfigure vlans on another switch like SW2 so that if SW1 shuts down, I still have functional Vlans everywhere else?
thank you!

Looking at this quickly I'd probably do IP SLA at SW1 and SW2, using Primary ASA as the default route, switching to the Backup. The rest can be left to EIGRP.
You can't do HSRP between SW1 and SW2 (not nicely anyway) because you don't have a layer-2 link directly between them. You'd have to use a trunk via the distribution switches if you really wanted to do it but that may not be possible if the links between core (SW1 and SW2) and distribution (SW3 and SW4) are purely routed links. The same can be said for the distribution<->access links. I'd only use HSRP where I can't manipulate routing (or where you can't directly dynamically influence routing at the adjacent devices), or where layer-2 is the only option.
If SW1 fails, EIGRP will tell SW3 and SW4 to use SW2 as the only candidate for unknown (external) routes. SW2 will know that the Primary ASA is still up and will route all internet-bound traffic that way. The same can be said for a failure at SW2, but obviously SW1 is the only candidate for external routing.
If the primary ASA fails SW1 will drop the default route to the primary and send traffic to the backup ASA. SW2 will do the same. When the primary ASA comes back IP SLA will reinstate the original route via the primary ASA.
The access switches just need to use EIGRP. They only have 2 route choices and it would probably be a good thing to just let EIGRP do ECLB (enabled by default on equal-cost routes). That provides redundancy and load-balancing straight from the off.
You can't do HSRP between SW1 and SW2 (not nicely anyway) because you don't have a layer-2 link directly between them. You'd have to use a trunk via the distribution switches if you really wanted to do it but that may not be possible if the links between core (SW1 and SW2) and distribution (SW3 and SW4) are purely routed links. The same can be said for the distribution<->access links. I'd only use HSRP where I can't manipulate routing (or where you can't directly dynamically influence routing at the adjacent devices), or where layer-2 is the only option.
If SW1 fails, EIGRP will tell SW3 and SW4 to use SW2 as the only candidate for unknown (external) routes. SW2 will know that the Primary ASA is still up and will route all internet-bound traffic that way. The same can be said for a failure at SW2, but obviously SW1 is the only candidate for external routing.
If the primary ASA fails SW1 will drop the default route to the primary and send traffic to the backup ASA. SW2 will do the same. When the primary ASA comes back IP SLA will reinstate the original route via the primary ASA.
The access switches just need to use EIGRP. They only have 2 route choices and it would probably be a good thing to just let EIGRP do ECLB (enabled by default on equal-cost routes). That provides redundancy and load-balancing straight from the off.
1. I want SW3 and SW4 to re-route it's self in case SW1 or SW2 fails to it's respective switch. For ex. if SW1 fails, traffic will get re-routed to SW2. I am assuming this will actually be done via EIGRP at this particular stage.Yes, EIGRP can do that for you.
2. If SW1 fails, I want traffic to get routed to SW2 and back to Primary ASA instead of Backup ASA. How would I accomplish that? IP SLA with tracking? HSRP?Since you are using EIGRP in your network everywhere, there is one more problem left to solve here - problem how to advertize default route, so that other switches in network can send traffic to internet.
3. If Primary ASA fails, traffic gets re-routed from SW1 to Backup ASA. How would I accomplish that? IP SLA with tracking? HSRP?
I guess that SW1 and SW2 can both advertize default network, and when packets reach to SW1 or SW2 static route with tracking will do it's job, or this can be achieved by redistributing default static routes on SW1 and SW2 (or perhaps route maps).
Also, one last thing, SW1 is a primary Switch, it has all VLans and it's IP's configured, I am running VTP, when I go to SW2 or SW4 for example, and I do show int vlan 5 let's say, its shows UP and UP but no ip address of the vlan is displayed (which is normal) But what happens if SW1 shuts down, all vlans show up and up but I am unable to ping any vlan. how could I ocnfigure vlans on another switch like SW2 so that if SW1 shuts down, I still have functional Vlans everywhere else?But, here is where I am confused.
You have VLANs everywhere and you have EIGRP everywhere??? Does this mean that you are using EIGRP to detect failing switch and nothing else??? EIGRP is L3 protocol, VLAN is L2.
I guess the simple logic should be where VLAN ends, EIGRP begins.
For detecting failing switch (or port that is connecting two switches) you do that by EIGRP if you have L3 topology in your network, or you do that by STP, RSTP or MSTP if you are using L2 topology in your network.
EIGRP or STP (RSTP, MSTP) will automatically find alternate path but don't forget that with STP you have 30 sec timeout by default if topology changes, so if you have newer switches use RSTP or MSTP (or you need to tune STP).
ASKER
I dont have EIGRP running in the whole network. I only have EIGRP in the switch infrastructure. I have over 100 tunnels on the asa above the switches, I dont want to implement EIGRP to the firewalls because I dont want EIGRP to go over the tunnel and create issues. I dont even care about EIGRP, I dont even need to implemented, my main concern is if SW1 fails, then it's over no matter what I have. SW1 is running vlans as a server switch, if it drops, I have absolutely no network connectivity. Anything below SW1 and SW2 is using vlans across all switches for communication. there are no L3 ports there.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
You said earlier even access switches run IP routing.
Now you're saying it's L2 down to the access-layer.
Which is it?
EIGRP will be on all switches in the image including the Access layer switches which are L3's as well.
Now you're saying it's L2 down to the access-layer.
Anything below SW1 and SW2 is using vlans across all switches for communication. there are no L3 ports there.
Which is it?
ASKER
alright, HSRP with IP SLA will do. Thats what I thought, I just needed to confirm.
ASKER
all the switches, SW1, 2, 3 and 4 are all running VLANS accross, including the access layer switches. Everything above SW1 and 2 will be have L3 routing. no vlans there. I dont know, maybe I mistyped.
So why extend the VLANs all the way up to SW1 and SW2? Why not just use a traditional core-dist-access model and route between core-dist? HSRP at each SVI at SW3 and SW4 will provide redundancy for access VLANs but you'll need a L2 link directly between SW3 and SW4 for it to be efficient. That way you still use IP SLA as I explained earlier and the dist switches get dynamic routing from EIGRP.
ASKER
can you explain?
- so, i should have L3 links between the core and dist switches?
- keep vlans only on dist. and access switches
-connect sw3 and 4 together for HSRP
- on SW3 and 4 I have 2 going to each sw1 and 2, I put those two links on a native vlan so I dont have to use different subnets. If I do routed ports, I would need to use 2 different subnets. for ex. SW1 native vlan is 100.1 SW2 is 100.2 SW3 100.4 I use trunks across routing via the native vlan.
Could you explain or draw out a map showing what I should do? thanks
- so, i should have L3 links between the core and dist switches?
- keep vlans only on dist. and access switches
-connect sw3 and 4 together for HSRP
- on SW3 and 4 I have 2 going to each sw1 and 2, I put those two links on a native vlan so I dont have to use different subnets. If I do routed ports, I would need to use 2 different subnets. for ex. SW1 native vlan is 100.1 SW2 is 100.2 SW3 100.4 I use trunks across routing via the native vlan.
Could you explain or draw out a map showing what I should do? thanks
Sure, but first can you tell us what the intended purpose of each switch (1-4) is, from your perspective? Are you looking at SW1 and SW2 as core switches and SW3 and SW4 as distribution switches, or are you looking at SW3 and SW4 being the cores and SW1 and SW2 being simple switches to connect the ASAs to SW3 and SW4?
Or something else??
Or something else??
ASKER
So, my current network is this, (before i implemented SW2 and SW4)
SW1 as a Core and SW3 as distribution switch and then the Access layer switches below. The issue is, I have no failover whats so ever, if the core switch goes down, I have nothing in terms of backup to the ASA's out to internet. Same thing to Dist. switch, if it fails I have no failover to Core switch.
So, I added SW2 which serves as back up to Core(sw1) and I added SW4 which is back up to SW3, So now I have full redundancy out to the firewalls, SW2 and SW4 serving as backup to their respective switches. SW2 and SW4 never existed, I added them to the mix.
I crisscross connected them as you see in the above image. I thought that would give me perfect redundancy scenario. So, SW3 and 4 are distribution switches, and SW1 and 2 are my core. I can implement this anyway I like, L2 and L3 links, EIGRP, HSRP with IP SLA. I just dont know how I should mix these up and at which layer(core?dist?
Does that help?
SW1 as a Core and SW3 as distribution switch and then the Access layer switches below. The issue is, I have no failover whats so ever, if the core switch goes down, I have nothing in terms of backup to the ASA's out to internet. Same thing to Dist. switch, if it fails I have no failover to Core switch.
So, I added SW2 which serves as back up to Core(sw1) and I added SW4 which is back up to SW3, So now I have full redundancy out to the firewalls, SW2 and SW4 serving as backup to their respective switches. SW2 and SW4 never existed, I added them to the mix.
I crisscross connected them as you see in the above image. I thought that would give me perfect redundancy scenario. So, SW3 and 4 are distribution switches, and SW1 and 2 are my core. I can implement this anyway I like, L2 and L3 links, EIGRP, HSRP with IP SLA. I just dont know how I should mix these up and at which layer(core?dist?
Does that help?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
this looks whole lot cleaner and makes more sense to do. Seems like I had an overkill previously.
SW1 is a core SW and it has all VLANs running, and configured as server for VTP, if thats witch shuts down, do I still have connectivity between all vlans? i initially thought, since SW1 is configured with all the vlans and its respective IP address that once the switch goes inactive, there in no routing or this is something HSRP will help me with?
SW1 is a core SW and it has all VLANs running, and configured as server for VTP, if thats witch shuts down, do I still have connectivity between all vlans? i initially thought, since SW1 is configured with all the vlans and its respective IP address that once the switch goes inactive, there in no routing or this is something HSRP will help me with?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
this is awesome. thanks man!
If you configure EIGRP on switches then you don't have need for IP SLA with tracking, EIGRP will perform the same job as IP SLA with tracking, EIGRP will dynamically change routes in routing table on all devices if network topology is changed.
HSRP you need on DSW1 and DSW2 only if your VLANS from ASW1 and ASW2 are extended to DSW1 and DSW2, or at least DSW1 and DSW2 have same VLANS. HSRP changes MAC address of default gateway IP address, so that is referred to L2 topology.
If you use EIGRP everywhere (on switches and router), and VLANS are not extended between switches - in that case EIGRP is sufficient, no need for HSRP or IP SLA with tracking.
So, like I already wrote usage of EIGRP, IP SLA and HSRP depends on actual implementation.
However, you still have single point of failure - Router R4.