SSL Certificates under SBS 2011 / Exchange 2010
I've picked up maintenance of a SBS2011 server which has Exchange 2010. I have a few certificates that are about to expire (all the remote.<FQDN>.com ones.
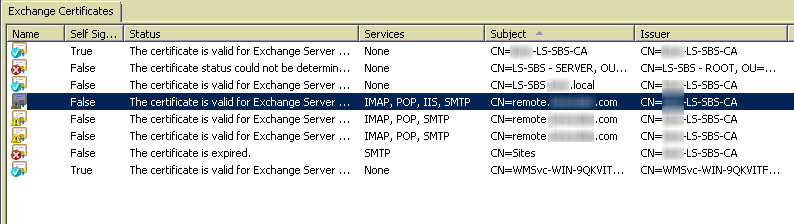
I tired to do a Get-exchangecertificate -thumbprint < > | new-exchangecertificate to replace it in powershell and that seemed to go fine. But the new certificate showed the subject of the cert as remote.<FQDN>.com and also issued by remote.<FQDN>.com as well. It also showed as self-signed, where the existing one does not and as being issued by <domain>-LS-SBS-CA (which is a self-signed certificate).
The new cert when opened also showed as not trusted (I'm assuming because the issued by was incorrect).
What am I doing wrong when I generate this new certificate?
Jim.

I tired to do a Get-exchangecertificate -thumbprint < > | new-exchangecertificate to replace it in powershell and that seemed to go fine. But the new certificate showed the subject of the cert as remote.<FQDN>.com and also issued by remote.<FQDN>.com as well. It also showed as self-signed, where the existing one does not and as being issued by <domain>-LS-SBS-CA (which is a self-signed certificate).
The new cert when opened also showed as not trusted (I'm assuming because the issued by was incorrect).
What am I doing wrong when I generate this new certificate?
Jim.
You arent doing anything wrong. Whats trusted isnt the cert, its the CA that issues the cert. You can find the issuing CA in the details of the cert. Theres a few ways that you can "trust" a CA. The easiest is doing it manually for just your own browser with you computers certificate store, but that will only fix you. The more complicated way is to issue a group AD policy which adds the issuing CA as trusted. You can google both ways on how to do it. Its pretty well documented.
http://social.technet.microsoft.com/wiki/contents/articles/13916.how-to-use-a-self-signed-certificate-in-exchange-2010.aspx
If you want a certificate issued by a certified authority which will not give you any warning to clients/users, you should buy one from GoDaddy, DigiCert, etc. Even if you issue a certify from your own CA which is not selfsigned, the users still will receive a warning, because your CA certifies is self signed and the warning will be that the CA cannot be verified :)
If you want a certificate issued by a certified authority which will not give you any warning to clients/users, you should buy one from GoDaddy, DigiCert, etc. Even if you issue a certify from your own CA which is not selfsigned, the users still will receive a warning, because your CA certifies is self signed and the warning will be that the CA cannot be verified :)
Comodo is also another good certified SSL vendor. I've used them and GoDaddy in the past and have no complaints about either.
IMO using Self signed certs in a production Exchange environment is not the best option.
IMO using Self signed certs in a production Exchange environment is not the best option.
ASKER
So if I didn't do anything wrong, then why do I end up with a self-signed certificate with the issue by and subject as the same?
Again, I'm looking to simply renew the existing certificates.
Jim.
Again, I'm looking to simply renew the existing certificates.
Jim.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I'll look through the link you posted.
The CA cert is set to expire in 2018.
Jim.
The CA cert is set to expire in 2018.
Jim.
The link helped me two month ago as I just said! It is very explicit and all the necessary steps are there. You cannot just right click and then press "renew certificate". The link is the right procedure ...
Best regards!
Best regards!
The best and easiest way is to install certificate services on a windows standalone server. Thne create the CSR using what ever way you want and submit that CSR to the Microsoft CA. So, what you did wrong was in the creation of your CSR. Create the CSR where the common name is the URL you want for the SSL cert, pretty much all of the other information is just that...informational. When creating the CSR set it to the byte length you want; pretty much whats standard these days is 1024 bytes, but 2048 isnt all that uncommon. When you go to purchase an SSL cert, thats where the byte length matters because the bigger one costs more... Dont ask me why... It doesnt "cost" the issuing CA anything more to issue the cert, but facts are facts and it costs more.
The place Ive gone to purchase certs is RapidSSL. Im not sure anyone else is more cost effective and still a trusted CA.
The place Ive gone to purchase certs is RapidSSL. Im not sure anyone else is more cost effective and still a trusted CA.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
While I certainly appreciate the advice that has been given, one again I will say that all I want to do for present is renew these certificates that are about to expire.
I realize that there are best practices that should be followed, like buying a 3rd party cert, but with just picking up this server, my intent is to do as little as possible at the moment in this area because I have so many other things going on.
Who ever originally setup this server did so with self-signed certs, and for the moment, that's what I'm looking to stick with.
All I need to do is renew the existing certs. Later on once the thing is cleaned up, I will address things that should have been done properly but were not.
I did some research on my own this weekend and as Jarda said, it looks like the "Fix my network wizard" is the way to go. I think however that's just a slick way of carrying out the manual steps in matrix8086's thread post.
What I've come to understand is that SBS2011 changed the way certs are handled from past versions (the remote.<domain>.com is now a leaf certificate), so what I've used in past and tried didn't give me the result needed.
Jim.
I realize that there are best practices that should be followed, like buying a 3rd party cert, but with just picking up this server, my intent is to do as little as possible at the moment in this area because I have so many other things going on.
Who ever originally setup this server did so with self-signed certs, and for the moment, that's what I'm looking to stick with.
All I need to do is renew the existing certs. Later on once the thing is cleaned up, I will address things that should have been done properly but were not.
I did some research on my own this weekend and as Jarda said, it looks like the "Fix my network wizard" is the way to go. I think however that's just a slick way of carrying out the manual steps in matrix8086's thread post.
What I've come to understand is that SBS2011 changed the way certs are handled from past versions (the remote.<domain>.com is now a leaf certificate), so what I've used in past and tried didn't give me the result needed.
Jim.
Jim - As I stated previously. The easiest way is to setup certificate services on a windows standalone server and create the cert. You can create the CSR on the that same windows server with certificate services, if you cant do it some where else.
Windows server 2003: https://msdn.microsoft.com/en-us/library/windows/desktop/aa376539%28v=vs.85%29.aspx
Windows Server 2008 and 2012: https://technet.microsoft.com/en-us/library/cc772393%28v=ws.10%29.aspx
You will have your self signed cert in no time this way...
Windows server 2003: https://msdn.microsoft.com/en-us/library/windows/desktop/aa376539%28v=vs.85%29.aspx
Windows Server 2008 and 2012: https://technet.microsoft.com/en-us/library/cc772393%28v=ws.10%29.aspx
You will have your self signed cert in no time this way...
ASKER
So here's the drill:
1. "Fix My Network" took care of the one cert for exchange (4th one down in my initial screenshot). Real easy. Ran for a few minutes, generated a new cert, assigned the services and I was done with that.
2. I deleted #4, #5, and #6, in the screen shot in EMC after doing step 1 and then exporting a copy just to be safe.
3. That left the "sites" certificate, which was expired. To resolve that, I:
a. Loaded the Certificates snap-in to MMC.
b. Drilled down to Personal>Certificates.
c. Right-clicked the expired certificate ("Sites").
d. All Tasks>Advanced Operations>Request New Certificate with the Same Key.
e. Followed the prompts to duplicate the expired key. In order to do this, I had to modify the permissions with certtmpl.msc adding Domain Controllers temporarily while I created the cert.
f. After successful certificate creation, deleted expired key.
g. Restarted IIS.
h. Went to EMC and assigned SMTP to the certificate. I did not overwrite the default SMTP certificate
Not sure if not overwriting was correct or not, but everything at this point seems to be working and functional.
Jim.
1. "Fix My Network" took care of the one cert for exchange (4th one down in my initial screenshot). Real easy. Ran for a few minutes, generated a new cert, assigned the services and I was done with that.
2. I deleted #4, #5, and #6, in the screen shot in EMC after doing step 1 and then exporting a copy just to be safe.
3. That left the "sites" certificate, which was expired. To resolve that, I:
a. Loaded the Certificates snap-in to MMC.
b. Drilled down to Personal>Certificates.
c. Right-clicked the expired certificate ("Sites").
d. All Tasks>Advanced Operations>Request New Certificate with the Same Key.
e. Followed the prompts to duplicate the expired key. In order to do this, I had to modify the permissions with certtmpl.msc adding Domain Controllers temporarily while I created the cert.
f. After successful certificate creation, deleted expired key.
g. Restarted IIS.
h. Went to EMC and assigned SMTP to the certificate. I did not overwrite the default SMTP certificate
Not sure if not overwriting was correct or not, but everything at this point seems to be working and functional.
Jim.
NIce work! This "Fix my network" is available only in SBS 2011? How about Windows 2008 Server and 2012 Server?
Thank you in advance!
Best regards!
Thank you in advance!
Best regards!
ASKER
"Fix My Network" is only available in SBS.
That's one of the things I've found with SBS and you see everywhere, which bears repeating (and I should have remembered), with SBS, you really want to use the wizards to get things done whenever you can.
Jim.
That's one of the things I've found with SBS and you see everywhere, which bears repeating (and I should have remembered), with SBS, you really want to use the wizards to get things done whenever you can.
Jim.