Big malware/virus issue. Cannot clean it.
I have a customer with a small LAN. 2 PCs, 2 MacBook Pros. All computers, both PCs and MacBooks, have hijacked browsers, as of this afternoon. When they go to any web site, even their own, clicking any link will open a malware site (for example, the one that gives you an 800 number to call, also reimageplus.com, all the usual suspects.
I have used all the standard tools, all removing things. The tools I've used on PC: MalwareBytes, RogueKiller, TDSSKiller, SuperAntiSpyware, ADWCleaner.
There are no suspicious programs in Control Panel Programs, esp. sorted by date.
The browser hijacking is unaffected by all of these tools.
Anyone else experience any recent malware/viruses that are as brutal as this infection?
I have used all the standard tools, all removing things. The tools I've used on PC: MalwareBytes, RogueKiller, TDSSKiller, SuperAntiSpyware, ADWCleaner.
There are no suspicious programs in Control Panel Programs, esp. sorted by date.
The browser hijacking is unaffected by all of these tools.
Anyone else experience any recent malware/viruses that are as brutal as this infection?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Agree with the above - sounds like DNS server was hijacked... not the individual PCs. Cross platform malware is rare if it exists at all.
Have you checked for root kits? Check out this article:
https://www.experts-exchange.com/articles/2245/Anti-rootkit-software.html
Also check for Browser Helper Objects using SPYBHORemover from securityxploded.com.
https://www.experts-exchange.com/articles/2245/Anti-rootkit-software.html
Also check for Browser Helper Objects using SPYBHORemover from securityxploded.com.
ASKER
Andreas (and others), you are right: the DNS settings in the Netgear router had been changed. Thanks for that great tip.
Wondering how this happened, as the router admin password is quite strong. Is this kind of change possible only if someone can log on to the router, or is there another way to affect the DNS settings on a router without logging in?
Wondering how this happened, as the router admin password is quite strong. Is this kind of change possible only if someone can log on to the router, or is there another way to affect the DNS settings on a router without logging in?
A few years ago there was a cross platform malware called DNSChanger or something like that. You may want to look into it.
You can read about it on Trend Micro's site (one source): http://www.trendmicro.com/vinfo/us/threat-encyclopedia/web-attack/125/how-dns-changer-trojans-direct-users-to-threats
You can read about it on Trend Micro's site (one source): http://www.trendmicro.com/vinfo/us/threat-encyclopedia/web-attack/125/how-dns-changer-trojans-direct-users-to-threats
Maybe a CSRF attack. Maybe one your your PCs had a logged in browser window to the router. Then a visit to a malicious webpage may remote control the routers admin interface.
Or the router has a security holes/backdoors, like recently some d-links.
Or the router has a security holes/backdoors, like recently some d-links.
Do you know what the incorrect DNS setting was on the router? If it was in any of the following ranges it is a good indication that you were affected by DNSChanger:
64.28.176.0 to 64.28.191.255
67.210.0.0 to 67.210.15.255
77.67.83.0 to 77.67.83.255
85.255.112.0 to 85.255.127.255
93.188.160.0 to 93.188.167.255
213.109.64.0 to 213.109.79.255
64.28.176.0 to 64.28.191.255
67.210.0.0 to 67.210.15.255
77.67.83.0 to 77.67.83.255
85.255.112.0 to 85.255.127.255
93.188.160.0 to 93.188.167.255
213.109.64.0 to 213.109.79.255
Netgear has a problem with their security, one partial remediation is to disable remote management of the router, and as always ensure that the router has the latest update applied
http://www.hotforsecurity.com/blog/got-a-netgear-wireless-router-youve-got-a-security-problem-11429.html
http://www.hotforsecurity.com/blog/got-a-netgear-wireless-router-youve-got-a-security-problem-11429.html
if your router is on the supported list I'd suggest using DD-WRT to replace the existing firmware.https://www.dd-wrt.com/site/support/router-database
Since you have already run a few scans..I'd do a few preliminary steps and depending on the severity of malware hit them at the source, Internet options, windows and hidden files and folders. Once they are removed then test your browser and run some deeper scans with the tools you've tried. Some malware deliberately prevent certain security tools from detecting them that's why disabling access from the internet first door..
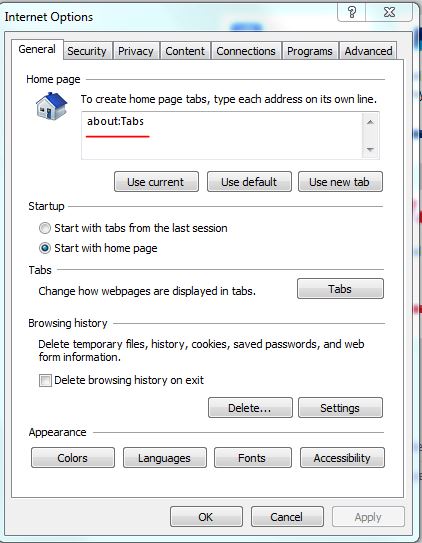
What I'd do is if using internet explorer set the homepage to about tabs
 Take the systems offline for starters.
Take the systems offline for starters.
Check your hosts files on windows dont know about Mac if they have a host file but in windows look in
C:\Windows\System32\driver
If windows x64 use the x64
open the hosts file with notepad untick to always use notepad
then delete anything below this line
 Look for any new programs in the start menu. and in the uninstall a program folder in control panel.
Look for any new programs in the start menu. and in the uninstall a program folder in control panel.
I use hijackthis scan to see what active, please install hyiackthis do a system scan and save a file make copy of this and post it back here please
http://sourceforge.net/projects/hjt/
http://www.bleepingcomputer.com/download/hijackthis/
I also use Ccleaner to delete cookies temp files and other internet related stuff. It's great but do be careful allowing it to delete everything it finds. Set up scan exceptions first. I'll post a guide
https://www.piriform.com/ccleaner
Guide to Ccleaner
http://www.technorms.com/5386/ccleaner-usage-guide
https://www.piriform.com/docs/ccleaner/ccleaner-settings
These are good for starters.
What I'd do is if using internet explorer set the homepage to about tabs
Check your hosts files on windows dont know about Mac if they have a host file but in windows look in
C:\Windows\System32\driver
If windows x64 use the x64
open the hosts file with notepad untick to always use notepad
then delete anything below this line
I use hijackthis scan to see what active, please install hyiackthis do a system scan and save a file make copy of this and post it back here please
http://sourceforge.net/projects/hjt/
http://www.bleepingcomputer.com/download/hijackthis/
I also use Ccleaner to delete cookies temp files and other internet related stuff. It's great but do be careful allowing it to delete everything it finds. Set up scan exceptions first. I'll post a guide
https://www.piriform.com/ccleaner
Guide to Ccleaner
http://www.technorms.com/5386/ccleaner-usage-guide
https://www.piriform.com/docs/ccleaner/ccleaner-settings
These are good for starters.
Can you please post model number and revision (if any) and firmmware version of your netgear router. So we can check if there are known holes for attackers to break in?
If you would like to not reveal that information, then do a research if your device can run dd-wrt and change to this firmware then. DD-WRT will be updated from time to time so you can keep your router safe over time.
If you would like to not reveal that information, then do a research if your device can run dd-wrt and change to this firmware then. DD-WRT will be updated from time to time so you can keep your router safe over time.
The question has either no comments or not enough useful information to be called an "answer".
Cant help any further if thread starter doesnt respond anymore to questions. So best would be to delete it if no response will be given.
OP should really consider changing to DD-WRT if its supported on its router, much more secure than most stock Firmwares and quite frequent updates.
Anither hint for the thread starter, you should change router password after firmware upgrade and dont save router password in any browser, neither as cookie or in the browsers password manager, and do not leave a router admin session logged on whilst online on other pages in same browser.
OP should really consider changing to DD-WRT if its supported on its router, much more secure than most stock Firmwares and quite frequent updates.
Anither hint for the thread starter, you should change router password after firmware upgrade and dont save router password in any browser, neither as cookie or in the browsers password manager, and do not leave a router admin session logged on whilst online on other pages in same browser.
almost all routers that have a USB port on them are affected with a current vulnerability. #1 rule is to disable management over the WAN. Unless the asker comes back the experts comments are for naught .. delete points not refunded
yu can test yourself for the NetUSB vulnerabilty if you portscan your router from the internet for port 20005 if you found it open and you didnt forwhard that port to an IP in your LAN NetUSB is most likely accessible from the internet and if you didnt installed a new firmware in the last few days, this netUSB port is vulnerable and can be attacked.
ASKER
Thank you Andreas. You were correct: a hijacked router, where the DNS settings had been altered.
To all of those who responded: I'm very sorry for my lack of response over the past month; I have been away, and actually thought I had settled this question before leaving!
To all of those who responded: I'm very sorry for my lack of response over the past month; I have been away, and actually thought I had settled this question before leaving!
Have a look at their DHCP server - maybe a router or server - and see what DNS it is assigning.
On a Windows PC go to a cmd prompt and type IPCONFIG /ALL. That will tell you the IP address of the DNS and the DHCP server.