Shark Attack
asked on
issues with GNS3 or top;ology?
I am having weird issues with GNS3 topology or maybe config issue. The below image shows my topology.
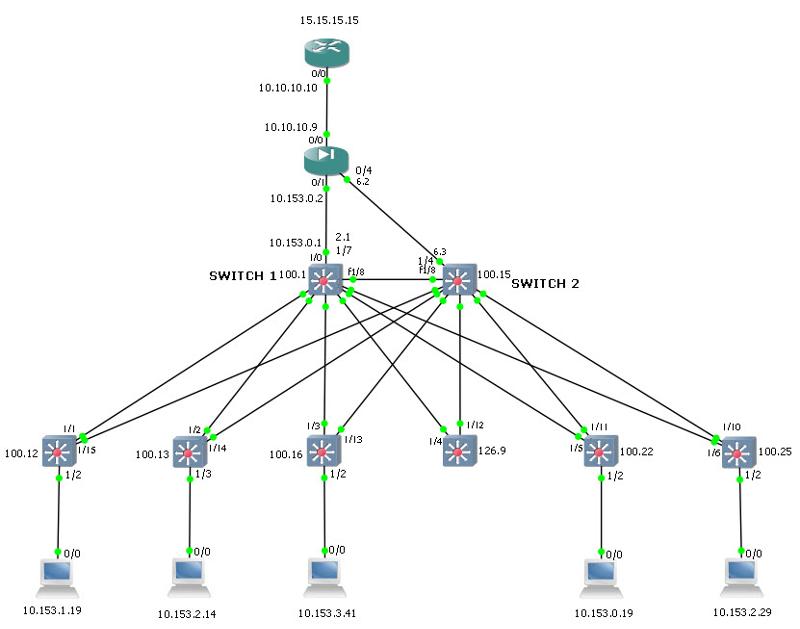 Whenever I turn all the devices ON, I can ping 15.15.15.15 from any host for ex from host 10.153.1.19 far left. At first, traceroute indicates that the route goes to 10.153.1.1 which is right and then to 10.10.10.10 but as you can see, after few traceroutes, it goes to 10.153.1.1. then 10.153.0.3 (0.3 is the SW2 VLAN svi 5.) Why it is hitting that switch at all? It's an HSRP switch. I have SVI configured for each vlan on the 2ND switch. I have vlans configured with virtual IP machine both sides. I have no idea why it hits the 2nd switch. If I drop the 2nd switch, I can no longer ping 15.15.15.15 which is wrong since it shouldn't need the 2nd switch at all to get to 15.15.15.15.
Whenever I turn all the devices ON, I can ping 15.15.15.15 from any host for ex from host 10.153.1.19 far left. At first, traceroute indicates that the route goes to 10.153.1.1 which is right and then to 10.10.10.10 but as you can see, after few traceroutes, it goes to 10.153.1.1. then 10.153.0.3 (0.3 is the SW2 VLAN svi 5.) Why it is hitting that switch at all? It's an HSRP switch. I have SVI configured for each vlan on the 2ND switch. I have vlans configured with virtual IP machine both sides. I have no idea why it hits the 2nd switch. If I drop the 2nd switch, I can no longer ping 15.15.15.15 which is wrong since it shouldn't need the 2nd switch at all to get to 15.15.15.15.
The second issue I had before I found the above more concerning was that when both switches SW1 and SW2 are on, I can obviously ping across all VLANS but when I shut off SW1, I can STILL ping all vlans except, when I do "clear arp-cash" on the host, I can no longer ping any vlan.
I am guessing this all makes no sense and it might very well be a gns issue. This will be topology I will be implementing into a real network scenario.
HOST (PC1)
SWITCH 1
links f1/8 between the two core's are my hsrp links
SWITCH 2
 Whenever I turn all the devices ON, I can ping 15.15.15.15 from any host for ex from host 10.153.1.19 far left. At first, traceroute indicates that the route goes to 10.153.1.1 which is right and then to 10.10.10.10 but as you can see, after few traceroutes, it goes to 10.153.1.1. then 10.153.0.3 (0.3 is the SW2 VLAN svi 5.) Why it is hitting that switch at all? It's an HSRP switch. I have SVI configured for each vlan on the 2ND switch. I have vlans configured with virtual IP machine both sides. I have no idea why it hits the 2nd switch. If I drop the 2nd switch, I can no longer ping 15.15.15.15 which is wrong since it shouldn't need the 2nd switch at all to get to 15.15.15.15.
Whenever I turn all the devices ON, I can ping 15.15.15.15 from any host for ex from host 10.153.1.19 far left. At first, traceroute indicates that the route goes to 10.153.1.1 which is right and then to 10.10.10.10 but as you can see, after few traceroutes, it goes to 10.153.1.1. then 10.153.0.3 (0.3 is the SW2 VLAN svi 5.) Why it is hitting that switch at all? It's an HSRP switch. I have SVI configured for each vlan on the 2ND switch. I have vlans configured with virtual IP machine both sides. I have no idea why it hits the 2nd switch. If I drop the 2nd switch, I can no longer ping 15.15.15.15 which is wrong since it shouldn't need the 2nd switch at all to get to 15.15.15.15.The second issue I had before I found the above more concerning was that when both switches SW1 and SW2 are on, I can obviously ping across all VLANS but when I shut off SW1, I can STILL ping all vlans except, when I do "clear arp-cash" on the host, I can no longer ping any vlan.
I am guessing this all makes no sense and it might very well be a gns issue. This will be topology I will be implementing into a real network scenario.
HOST (PC1)
PC1#traceroute 15.15.15.15
Type escape sequence to abort.
Tracing the route to 15.15.15.15
1 10.153.1.1 24 msec 8 msec 12 msec
2 10.10.10.10 40 msec 108 msec 24 msec
PC1#traceroute 15.15.15.15
Type escape sequence to abort.
Tracing the route to 15.15.15.15
1 10.153.1.1 12 msec 20 msec 4 msec
2 10.10.10.10 16 msec 20 msec 16 msec
PC1#traceroute 15.15.15.15
Type escape sequence to abort.
Tracing the route to 15.15.15.15
1 10.153.1.1 44 msec 12 msec 52 msec
2 10.153.0.3 44 msec
10.10.10.10 68 msec
10.153.0.3 56 msec
PC1#traceroute 15.15.15.15
Type escape sequence to abort.
Tracing the route to 15.15.15.15
1 10.153.1.1 12 msec 8 msec 28 msec
2 10.153.0.3 24 msec 40 msec 68 msec
3 10.153.0.3 !H
10.10.10.10 24 msec 60 msec
PC1#cle
PC1#clear ar
PC1#clear arp-cache
PC1#traceroute 15.15.15.15
Type escape sequence to abort.
Tracing the route to 15.15.15.15
1 10.153.1.1 1040 msec 8 msec 20 msec
2 10.153.0.3 24 msec 40 msec
10.10.10.10 24 msec
PC1#traceroute 15.15.15.15
Type escape sequence to abort.
Tracing the route to 15.15.15.15
1 10.153.1.1 28 msec 12 msec 8 msec
2 10.153.0.3 40 msec
10.10.10.10 24 msec
10.153.0.3 32 msecSWITCH 1
links f1/8 between the two core's are my hsrp links
CORE#show standby br
P indicates configured to preempt.
|
Interface Grp Prio P State Active Standby Virtual IP
Vl1 15 150 P Active local 192.168.100.15 192.168.100.5
Vl5 15 150 P Active local 10.153.0.3 10.153.0.5
Vl6 15 150 P Active local 10.153.6.3 10.153.6.5
Vl8 15 150 P Active local 10.153.1.3 10.153.1.5
Vl9 15 150 P Active local 10.153.2.3 10.153.2.5
Vl10 15 150 P Active local 10.153.3.3 10.153.3.5
Vl12 15 150 P Active local 10.153.12.3 10.153.12.5CORE#show ip int br | ex un
Interface IP-Address OK? Method Status Protocol
Vlan1 192.168.100.1 YES NVRAM up up
Vlan5 10.153.0.1 YES NVRAM up up
Vlan6 10.153.6.1 YES NVRAM up up
Vlan8 10.153.1.1 YES NVRAM up up
Vlan9 10.153.2.1 YES NVRAM up up
Vlan10 10.153.3.1 YES NVRAM up up
Vlan12 10.153.12.1 YES NVRAM up upCORE#show run | i route
ip route 15.15.15.0 255.255.255.0 10.153.0.2SWITCH 2
GIG_SW#show standby br
P indicates configured to preempt.
|
Interface Grp Prio P State Active Standby Virtual IP
Vl1 15 100 Standby 192.168.100.1 local 192.168.100.5
Vl5 15 100 Standby 10.153.0.1 local 10.153.0.5
Vl6 15 100 Standby 10.153.6.1 local 10.153.6.5
Vl8 15 100 Standby 10.153.1.1 local 10.153.1.5
Vl9 15 100 Standby 10.153.2.1 local 10.153.2.5
Vl10 15 100 Standby 10.153.3.1 local 10.153.3.5
Vl12 15 100 Standby 10.153.12.1 local 10.153.12.5GIG_SW#show ip int br | ex un
Interface IP-Address OK? Method Status Protocol
Vlan1 192.168.100.15 YES NVRAM up up
Vlan5 10.153.0.3 YES NVRAM up up
Vlan6 10.153.6.3 YES NVRAM up up
Vlan8 10.153.1.3 YES NVRAM up up
Vlan9 10.153.2.3 YES NVRAM up up
Vlan10 10.153.3.3 YES NVRAM up up
Vlan12 10.153.12.3 YES NVRAM up upGIG_SW#show run | i route
ip route 15.15.15.0 255.255.255.0 10.153.6.2
1. Default gateway on hosts is wrong. You should never in traceroute get response from 10.153.1.3 or 10.153.1.1 .... you should always get response from 10.153.1.5 - virtual address should be your gateway.
2. You should also track status of reachability on your interfaces to ASA - to check is internet available. Otherwise - what will cause HSRP to Convert to other switch to be active if path to internet becomes unavailable?
2. You should also track status of reachability on your interfaces to ASA - to check is internet available. Otherwise - what will cause HSRP to Convert to other switch to be active if path to internet becomes unavailable?
ASKER
1. if I set my default- gateway on hosts to the virtual IP, will the host sometimes choose to go to SW2 rather then SW1? I would only want host going to 15.15.15.15 via SW1 unless SW1 is down. There will be no traffic balancing or anything of that sort right?
2. I initially thought that HSRP does this alone. So basically I need to configure IP SLA with tracking on the switches interfaces that go to each ASA? I thought that since HSRP is active, once SW1 fails, Virtual IP will kick in somehow and forward traffic via SW2 out.
thanks
2. I initially thought that HSRP does this alone. So basically I need to configure IP SLA with tracking on the switches interfaces that go to each ASA? I thought that since HSRP is active, once SW1 fails, Virtual IP will kick in somehow and forward traffic via SW2 out.
thanks
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
thanks for clearing things up for me. When I changed the hosts gateways to Virtual IP, I still get the SW1's vlans in traceroute though. Not sure why, and still the annoying 10.153.0.3 especially
This might be the ASA right? IP SLA not configured correctly?
PC6#traceroute 209.117.163.165
Type escape sequence to abort.
Tracing the route to 209.117.163.165
1 10.153.2.1 28 msec 68 msec 32 msec
2 209.242.21.169 36 msec
10.153.0.3 20 msec 92 msec
PC6#traceroute 209.117.163.165
Type escape sequence to abort.
Tracing the route to 209.117.163.165
1 10.153.2.1 8 msec 8 msec 16 msec
2 209.242.21.169 52 msec
10.153.0.3 28 msec 24 msecThis might be the ASA right? IP SLA not configured correctly?
ASKER
there was also a GNS issue as well
ASKER
SWITCH 1
Open in new window
SWITCH 2
Open in new window
ASA
Open in new window