Blacklisted due to outgoing spam SBS2011
IP Address 12.198.184.xxx is listed in the CBL. It shows signs of being infected with a spam sending trojan, malicious link or some other form of botnet.
It was last detected at 2015-06-18 13:00 GMT (+/- 30 minutes), approximately 7 hours, 30 minutes ago.
This IP is infected (or NATting for a computer that is infected) with a spam-sending infection. In other words, it's participating in a botnet. If you simply remove the listing without ensuring that the infection is removed (or the NAT secured), it will probably relist again.
I am using Exchange 2010 on SBS2011 and I would like to find out which email address is doing this. Is there a way for me to do that?
It was last detected at 2015-06-18 13:00 GMT (+/- 30 minutes), approximately 7 hours, 30 minutes ago.
This IP is infected (or NATting for a computer that is infected) with a spam-sending infection. In other words, it's participating in a botnet. If you simply remove the listing without ensuring that the infection is removed (or the NAT secured), it will probably relist again.
I am using Exchange 2010 on SBS2011 and I would like to find out which email address is doing this. Is there a way for me to do that?
It's actually more likely that you have a PC on your network that's infected that's causing this. All traffic from your network is probably going out on the same public IP address so you need to scan all your machines (including the server) for malware first.
ASKER
I went to Message Tracking on EMC and delivery reports after signing in as Admin. I looked through everyone's mailbox and do not see anything suspicious. Is this the correct way to do this or is there another way? Is it possible that spam could be sent out through someone's email account even though I dont see it in the delivery report?
ASKER
What type of malware scan do you recommend for the server?
I should add for clarification that it's probably not Exchange where the problem lies but you can also check the queue on your Exchange to see if you can see anything, but this is less likely.
Just use malwarebytes to start with on all machines. It is very possible (probable even) that it's not the server so you need to check all machines.
Looking at the Exchange server is a waste of time.
As already pointed out above, this is most likely a compromised workstation, and the workstation is sending email out directly.
If your server was compromised then you would see a lot of garbage in the queue, as the spammer's lists are not very clean.
The best way to find the source is to use your router (if you have a decent one). Block port 25 outbound for all addresses but Exchange and watch the logs. The compromised system will quickly show up in the logs and you can then look at removing the culprit.
Simon.
As already pointed out above, this is most likely a compromised workstation, and the workstation is sending email out directly.
If your server was compromised then you would see a lot of garbage in the queue, as the spammer's lists are not very clean.
The best way to find the source is to use your router (if you have a decent one). Block port 25 outbound for all addresses but Exchange and watch the logs. The compromised system will quickly show up in the logs and you can then look at removing the culprit.
Simon.
ASKER
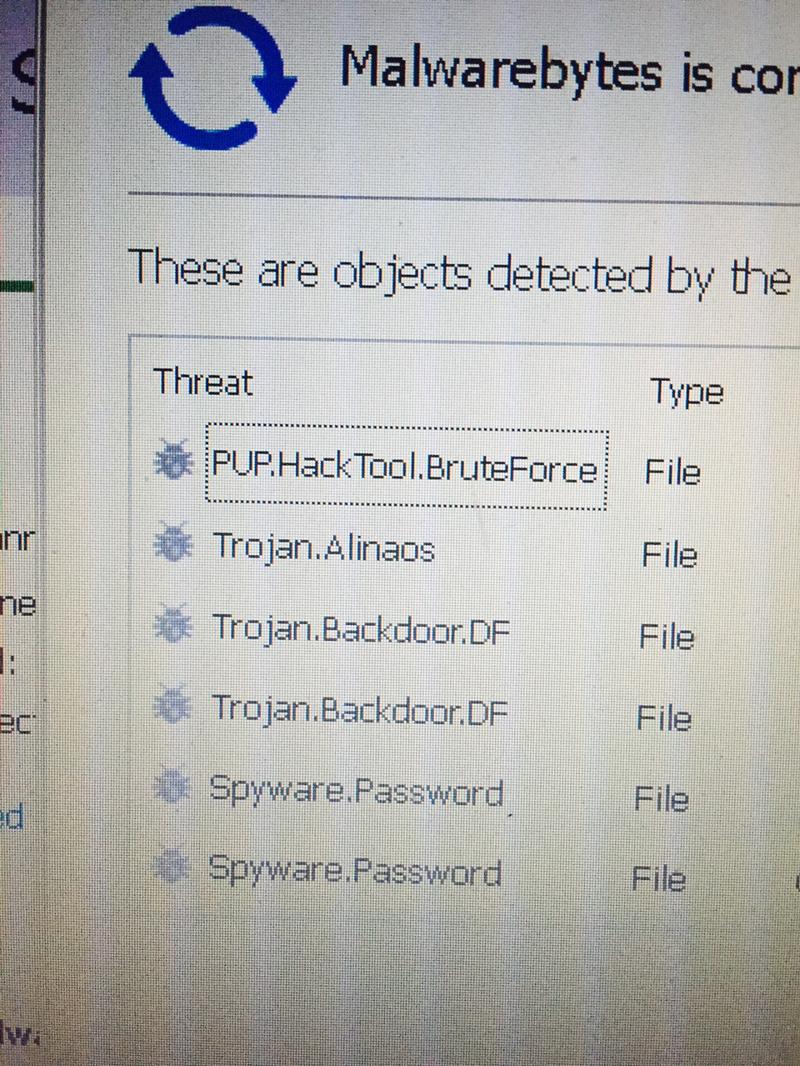
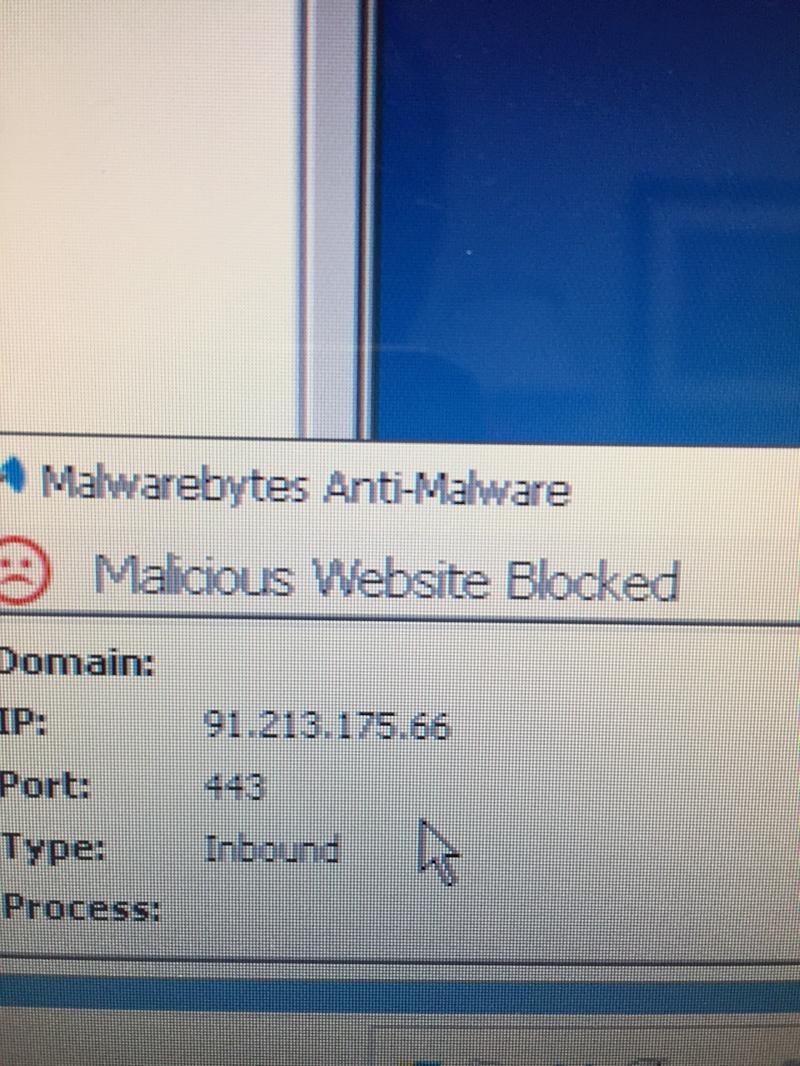
Found this on the server.
ASKER
By the way I scanned all workstations for viruese and malware and changed all passwords. I tightened the firewall to only allow outbound emails on the server IP.
The IP address is from the Ukraine. I presume you aren't in the Ukraine?
Go through the IIS logs, but I suspect you have a compromised account.
Were the files found in server locations, or in user shares?
Simon.
Go through the IIS logs, but I suspect you have a compromised account.
Were the files found in server locations, or in user shares?
Simon.
ASKER
sysadmin account. I suspect this is from an old migration. This is account is no where to be found in AD
I don't understand what you are saying.
Was something found under "sysadmin" ?
Look in the section marked "Builtin" for the user account as well.
Simon.
Was something found under "sysadmin" ?
Look in the section marked "Builtin" for the user account as well.
Simon.
ASKER
Location of the malware was inside the sysadmin user folder.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Deleting this folder stopped the attack pop-up from Malwarebytes.
Scanning all workstations and changing all passwords stopped the server's IP from becoming blacklisted again.
Scanning all workstations and changing all passwords stopped the server's IP from becoming blacklisted again.