smart Z
asked on
configuring ASA in my topology
Dear experts,
I am trying to figure out how users in vlan 10 and 20 will be able to access the IP 192.168.1.2. I have never configured ASA before and I need someone to help me in this lab.
My core is configured as layer 3 and SW1 is configured as layer 2 I want to pass the traffic over to the other side assuming the R2 belongs to internet.
core.rtf
hostname-SW1.docx
ASKER
Hi Akinsd,
Yes these are all private IP addresses. I actually want to connect a that router interface to my enterprise network and I want to see how the firewall will be configured. I did not purchase the ASA yet. Is this topology correct or does it need someone routers or switches.
The other thing is that I really want users in vlan 10 to access the ip address 192.168.1.2 and this IP could be a web portal or FTP server .
Yes these are all private IP addresses. I actually want to connect a that router interface to my enterprise network and I want to see how the firewall will be configured. I did not purchase the ASA yet. Is this topology correct or does it need someone routers or switches.
The other thing is that I really want users in vlan 10 to access the ip address 192.168.1.2 and this IP could be a web portal or FTP server .
ASKER
The inside interface of the ASA , 10.50.20.2 has a security level of 100 and the outside interface of the ASA 192.168.1.1 has a security level of 0. Will this work ?
ASKER
I just using my pad to configure this PIX and I need some suggestions if I am doing it correct.
asa1(config)# int g0
asa1(config-if)# ip address 10.50.20.2 255.255.255.0
asa1(config-if)#no shut
asa1(config-if)#nameif inside
asa1(config)# int g1
asa1(config-if)#ip address 192.168.1.1 255.255.255.252
asa1(config-if)#no shut
asa1(config-if)#name if outside
what I want to know is that the workstation in vlan 10 with ip 10.50.10.2 can it ping the IP 192.168.1.1 or 192.168.1.2. Do I need more configuration on the ASA or in the core to make it ping successfully.
asa1(config)# int g0
asa1(config-if)# ip address 10.50.20.2 255.255.255.0
asa1(config-if)#no shut
asa1(config-if)#nameif inside
asa1(config)# int g1
asa1(config-if)#ip address 192.168.1.1 255.255.255.252
asa1(config-if)#no shut
asa1(config-if)#name if outside
what I want to know is that the workstation in vlan 10 with ip 10.50.10.2 can it ping the IP 192.168.1.1 or 192.168.1.2. Do I need more configuration on the ASA or in the core to make it ping successfully.
The other thing is that I really want users in vlan 10 to access the ip address 192.168.1.2 and this IP could be a web portal or FTP server.Well that IP is the IP of the interface and you can't use duplicate IPs on the same network. The alternative is if the router is running the web service.
Ideally, lets assume that your Web server has an IP of 192.168.1.200 and your actual point to point IP is 198.168.1.1 and 198.168.1.2. lastly, we'll assume there's another interface on the router that is 192.168.1.1
You would create a static NAT statement on the router that will forward traffic to the web server
So if someone from the internet types 198.168.1.2:80 (the 80 won't be necessary as that is the default for http) in a browser, the traffic would be directed to 192.168.1.200
what I want to know is that the workstation in vlan 10 with ip 10.50.10.2 can it ping the IP 192.168.1.1 or 192.168.1.2. Do I need more configuration on the ASA or in the core to make it ping successfully.Because the security is set to 0, you will need an ACL to permit the traffic
eg
access-list outside_in extended permit ip 192.168.1.0 255.255.255.0 10.x.0.0 255.255.0.0
On the outside interface, apply the acl to the inward traffic.
This permits the traffic coming back in to the inside interface.
Remember that communication is a two way direction
ASKER
I agree with what you suggested. The websever to be 192.168.1.200 and one to one IP between the routers to be 192.168.1.1 -- 192.168.1.2
I really need your assistance in the NAT configuration and the ACL.
Thanks,
I really need your assistance in the NAT configuration and the ACL.
Thanks,
ASKER
ideally , the router R2 belongs to a different organizarion and I will not have access to it. I am just concern with the ASA configuration and I just want to restrict the access of the internal vlan to that webserver.
I agree with what you suggested. The websever to be 192.168.1.200 and one to one IP between the routers to be 192.168.1.1 -- 192.168.1.2If you noticed, I changed the IP on the point-to-point link to a public address instead (198.x.x.x)
This address would be assigned to you by your ISP.
If you have a direct cable connection from the ASA to the router (as your configuration depicts), you are not passing through the internet, meaning the router is part of your inside network (with a different name eg inside2). You can then set the security level to 100 since there's no traffic from the internet.
the router R2 belongs to a different organization and I will not have access to it.How you're connected to R2 determines on what to configure.
If R2 belongs to another organization, that means you have another interface to the internet unless you're connecting to the internet through the organization which means your connection is a LAN connection. If so, all you need like I mentioned would be to attach an ACL that permits the traffic back into your network.
If R2 belongs to the ISP, the IP address can never be a private address as you've shown.
The static NAT (port forwarding) would not be your responsibility as you won't have control over it.
May I suggest that you get the actual topology and work with that instead to avoid guessing.
Your current topology does not depict where the web server is. Based on the diagram above, and your comment that R2 is managed by someone else, and I'm assuming you can already access the internet, then there's nothing you can do with NAT on that web server. The NAT for the webserver would be on R2 based on what you've provided so far.
ASKER
I am sorry I did not mention the topology is as per what I am trying to achieve.
The router R2 is in the same facility that is shared with another firm. My access switch will connect to the ASA inside interface and R2 twill connect to ASA in the outside interface. The other firm has a local Web portal that the users in vlan 10 and 20 want to access.
About Internet access the users in vlan 10 and 20 get it from another WAN link which is connected to the core.
I hope I have explained the situation.
The router R2 is in the same facility that is shared with another firm. My access switch will connect to the ASA inside interface and R2 twill connect to ASA in the outside interface. The other firm has a local Web portal that the users in vlan 10 and 20 want to access.
About Internet access the users in vlan 10 and 20 get it from another WAN link which is connected to the core.
I hope I have explained the situation.
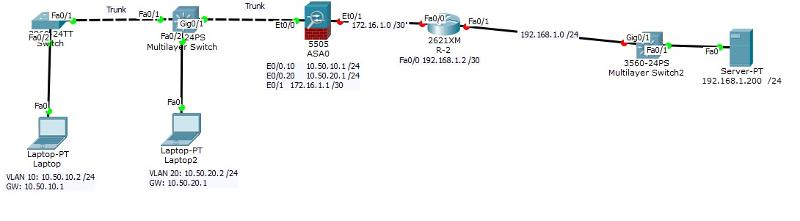
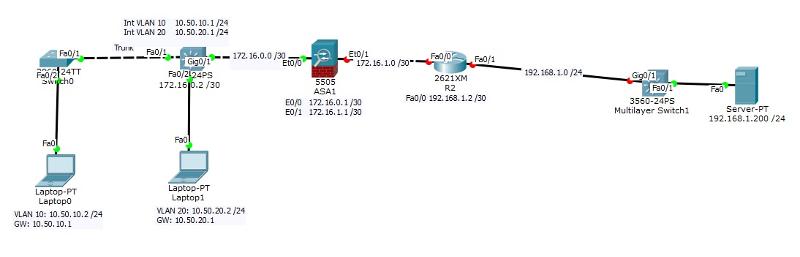
I see an interface on the ASA for VLAN 20, but not for VLAN 10.
You also have VLAN 10 attached to the 3560 which is connected to the 2960 via a trunk port.
This topology can't work. Answer the following questions and I'll refine it for you.
It's either there are subinterfaces on the firewall's interface connecting to the 2960 or the 2960 is distribution (which is not possible because it's a layer 2 switch) or the 3560 is the distribution (which also is not possible based on the diagram links).
I need a more accurate topology, otherwise we'll just be guessing stuff all over the place.
Are you modifying an existing network (if so, I need a diagram that represents current topology) or are you creating a new one.
Also, is the internal IP for the neighbor 192.168.1.0 /24?
See 2 workable examples below
(Note: Trunk port or sub-interfaces are both not supported on the ASA version available in packet tracer. To properly simulate the topologies, you will need to use a router but you won't have the nameif or security-level command. You'll be able to use those commands in a live ASA or GNS3).
You also have VLAN 10 attached to the 3560 which is connected to the 2960 via a trunk port.
This topology can't work. Answer the following questions and I'll refine it for you.
It's either there are subinterfaces on the firewall's interface connecting to the 2960 or the 2960 is distribution (which is not possible because it's a layer 2 switch) or the 3560 is the distribution (which also is not possible based on the diagram links).
I need a more accurate topology, otherwise we'll just be guessing stuff all over the place.
Are you modifying an existing network (if so, I need a diagram that represents current topology) or are you creating a new one.
Also, is the internal IP for the neighbor 192.168.1.0 /24?
See 2 workable examples below
(Note: Trunk port or sub-interfaces are both not supported on the ASA version available in packet tracer. To properly simulate the topologies, you will need to use a router but you won't have the nameif or security-level command. You'll be able to use those commands in a live ASA or GNS3).


ASKER
In a live production environment this Core is where all the SVIs are created what happens when another company put their our LAN and wants you to get a connection to one server. I can not make the core switch to work as layer 2.
What if I replace the ASA WITH A ROUTER? i dont care about the security levels for now I just want it to work with out changing the inside network.
What if I replace the ASA WITH A ROUTER? i dont care about the security levels for now I just want it to work with out changing the inside network.
In a live production environment this Core is where all the SVIs are created what happens when another company put their our LAN and wants you to get a connection to one server.Are you referring to the 3560 in your diagram as the core switch?
I can not make the core switch to work as layer 2.Layer 3 switches have all the capabilities of layer 2. The layer 3 is an additional feature
What if I replace the ASA WITH A ROUTER? i dont care about the security levels for now I just want it to work with out changing the inside network.I still don't know how your topology looks like. Let's lay the foundation (infrastructure) first before going any further. I didn't see any answer to my previous question
ASKER
Its okay I am doing my own research lab.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Interface security level change is all you probably need based on your configuration. Just set the security interface to 100
All the routes would be treated as connected routes so you won't really need to specify specific routes.
The addresses are private and won't need any NAT
You shouldn't need to configure an ACL, you can determine that by running a packet trace
packet-tracer input inside tcp 10.10.10.0 4444 192.168.1.2 4444 detailed
In real world, the internal interfaces would have a security level above 0, usually 100. These would be considered inside network. 192.168.1.1 would then be a gateway for the network to the internet
Lets assume the name of the interface 192.168.1.1 is outside and the actual int is E0/2
route outside 0.0.0.0 0.0.0.0 192.168.0.2
int e0/2
name if outside
security-level 0
Depending on you IOS version, you may be able to configure conventional route and if not you may need to use network objects to configure your NAT.
eg
nat (inside, outside) source dynamic any interface
Lastly, you will need to configure an access list to permit access on the outside interface since the security level is set to 0, meaning untrusted. 100 means trusted.