Citrix End Point Analysis - using session vs preauthentication policies
Hello all,
I have configured EPA using a preauthentication policy. This works however mobile devices are unable to connect and I expect this to become a problem sooner rather than later so am working on a solution. I configured the scan within the session action as suggested here by Punit: http://discussions.citrix.com/topic/337423-mobile-devices-and-epa-on-netscaler-gateway-101/
This seems to work however Windows machines are able to skip check and still gain access rather than being denied. And knowing that, on mobile devices I hit skip check to bypass. I am not sure: should I be seeing the EPA prompt at all on mobile devices and, if I am, does that mean that the 'REQ.HTTP.HEADER User-Agent' check in the session policy expression is failing?
So i have two questions. 1. Is there a better way to enable EPA but provide a bypass for mobile devices? and 2. how can I force a 'skip check' to = a failed scan and deny access?
Netscaler 10.5 52.11.nc
Xenapp 6.5
Session-Action.JPG
Session-Policy.JPG
I have configured EPA using a preauthentication policy. This works however mobile devices are unable to connect and I expect this to become a problem sooner rather than later so am working on a solution. I configured the scan within the session action as suggested here by Punit: http://discussions.citrix.com/topic/337423-mobile-devices-and-epa-on-netscaler-gateway-101/
This seems to work however Windows machines are able to skip check and still gain access rather than being denied. And knowing that, on mobile devices I hit skip check to bypass. I am not sure: should I be seeing the EPA prompt at all on mobile devices and, if I am, does that mean that the 'REQ.HTTP.HEADER User-Agent' check in the session policy expression is failing?
So i have two questions. 1. Is there a better way to enable EPA but provide a bypass for mobile devices? and 2. how can I force a 'skip check' to = a failed scan and deny access?
Netscaler 10.5 52.11.nc
Xenapp 6.5
Session-Action.JPG
Session-Policy.JPG
ASKER
Thanks mburdick. It sounds like I really am not looking for a pre-authentication policy after all.
In testing I was kind of leaning in that direction and configured a session policy to verify device type and provide the bypass for mobile device, then added the security checks to the session profile(please see attachments).
The problem is (and I apologize for adding two different questions to the same post) that the skip check option which appears when performing this function through the session profile allows access anyway. Would you know of a method of removing skip check or at least denying access if skip check is chosen?
In testing I was kind of leaning in that direction and configured a session policy to verify device type and provide the bypass for mobile device, then added the security checks to the session profile(please see attachments).
The problem is (and I apologize for adding two different questions to the same post) that the skip check option which appears when performing this function through the session profile allows access anyway. Would you know of a method of removing skip check or at least denying access if skip check is chosen?
ASKER
Actually I think I see the solution in your post. The SmartAccess policies if enabled correctly will deny access to specific xenapp published applications if the check fails, but by default allow access even if it does fail! I'll test this soon and post back the result. Please reply if I'm not on the right track.
ASKER
OK, tested by adding access control to one of our published apps and it is looking good. However I don't believe the user-agent check is working. On a test ipad using Receiver or Safari I still see the postepa session check and if I skip I do not see the app, which means the session check ran and failed. Looking at the policy expression attached can you see a reason why? Or any other cause?
EPA scanning is not supported on mobile devices.
Can you elaborate on the problem you are trying to solve? The more details, the better.
Can you elaborate on the problem you are trying to solve? The more details, the better.
ASKER
I am trying to configure Netscaler policies to:
1. Scan windows and mac machines for a few security parameters.
2. Allow mobile devices through without being scanned (since it fails as you say)
Based on your advice I looked into smart access using session policies and that does work so I will be using that process. But mobile devices are still being prompted for the EPA scan despite the user agent policy expression configured as attached.
1. Scan windows and mac machines for a few security parameters.
2. Allow mobile devices through without being scanned (since it fails as you say)
Based on your advice I looked into smart access using session policies and that does work so I will be using that process. But mobile devices are still being prompted for the EPA scan despite the user agent policy expression configured as attached.
I believe you're not identifying your user agents properly. I know with Safari, "Like Mac" is part of the string even on iOS devices. Here's a link to what appears to be a reasonably good list of user agent strings that you could use to either include Mac/Windows (which would miss Linux) or exclude iOS/Android/etc.
http://www.smali.net/configuring-session-policies-and-profiles-for-access-gateway/
http://www.smali.net/configuring-session-policies-and-profiles-for-access-gateway/
ASKER
Hello again,
Finally made it back to testing this . Here's where I stand right now. Please comment if I have anything wrong etc.
1. I read further and saw smart access requires secure browse be enabled for the profile action controlling mobile devices so I enabled it
2. Secure browse apparently allows iOS to access netscaler but requires itself clientless access mode be enabled with clientless access URL encoding set to Clear. I set both of these in the profile action.
I am now seeing the image below on iOS. Any ideas?
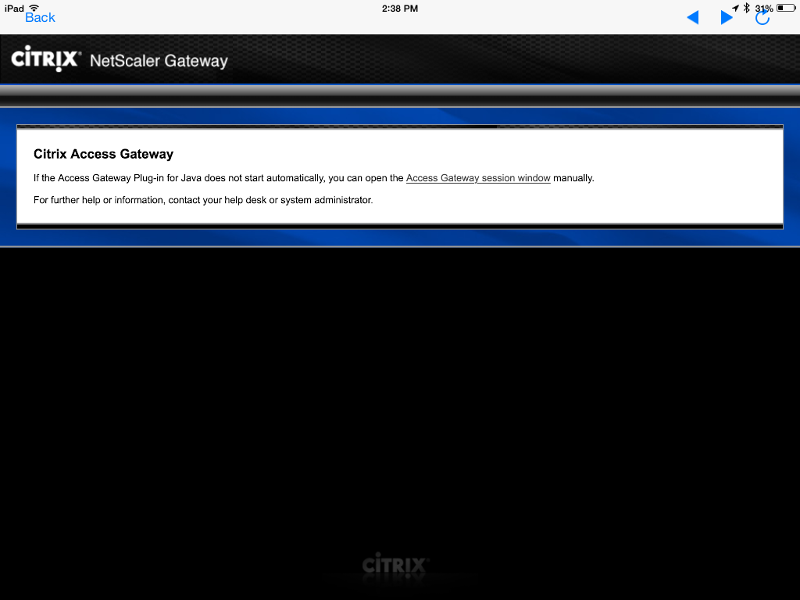
Finally made it back to testing this . Here's where I stand right now. Please comment if I have anything wrong etc.
1. I read further and saw smart access requires secure browse be enabled for the profile action controlling mobile devices so I enabled it
2. Secure browse apparently allows iOS to access netscaler but requires itself clientless access mode be enabled with clientless access URL encoding set to Clear. I set both of these in the profile action.
I am now seeing the image below on iOS. Any ideas?
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.
It's important to understand that these strings can be faked, so be cautious about how you go about doing it. And, you may want to have a session policy that kicks in as well.
Typically, these sort of policies are most useful when tied to a Gateway vServer because of SmartAccess Policy controls. There isn't usually a lot of value in determining that a workstation has anti-virus installed before allowing them to access a web site, for example, since they aren't transmitting content from the hard drive to the web site. In that scenario, you're better off using the Web Application Firewall to protect the application from known malicious hack attempts.