Can't establish a Site to Site VPN connection between TZ170(Remote) and SonicWALL 2600(Central)
The main site is a sonicwall 2600 and the remote site is a sonicwall TZ 170. I am trying to configure a site to site VPN. I have configured and enabled the connection but I still not able to connect.
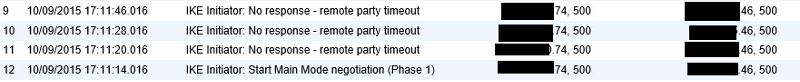
In the logs on both side I am getting IKE Initiator: Remote party timeout - Retransmitting IKE request. I am not sure why it is failing can someone tell me what I am doing wrong?
Please see attachment: Same on both sides.
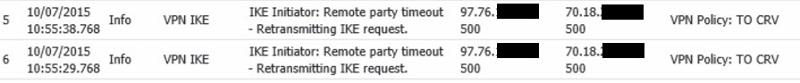

Thanks in advance.
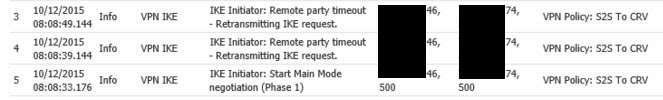
In the logs on both side I am getting IKE Initiator: Remote party timeout - Retransmitting IKE request. I am not sure why it is failing can someone tell me what I am doing wrong?
Please see attachment: Same on both sides.


Thanks in advance.
You need to check the external IP at each end and then to ensure the internal subnets are different. I cannot tell from the above screenshot. The IKE initiator message is an early message that indicates a connection is not being made.
Make sure the firewall rules on each end allow the other end to communicate (different external IP addresses).
Then make sure your tunnels are set for Site to Site and not Client to Gateway (this is a setting in my VPN tunnel setup).
Then check the Phase 1 and Phase 2 setups are the same at both ends. I do not think you are getting to Phase 2 at this point, so check the initial suggestions.
Make sure the firewall rules on each end allow the other end to communicate (different external IP addresses).
Then make sure your tunnels are set for Site to Site and not Client to Gateway (this is a setting in my VPN tunnel setup).
Then check the Phase 1 and Phase 2 setups are the same at both ends. I do not think you are getting to Phase 2 at this point, so check the initial suggestions.
ASKER
@Carlmd - Thank you for replying. I read the link you posted and made sure that both are in Main mode and phase 1 & 2 are the same along with the pershare key.
The difference in my setup and the KB is that I am using a SonicWALL TZ170(Remote Site) on one end and SonicWALL 2600(Central site). I can configure the Address Object on the 2600 but I do not have that option on the TZ170. (see figure1).
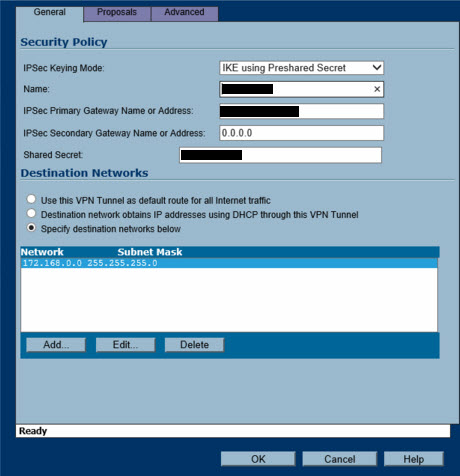
After making sure of everything in the KB is configure at my site I am still not able to get a connection.
Please advise.
Thanks!
The difference in my setup and the KB is that I am using a SonicWALL TZ170(Remote Site) on one end and SonicWALL 2600(Central site). I can configure the Address Object on the 2600 but I do not have that option on the TZ170. (see figure1).

After making sure of everything in the KB is configure at my site I am still not able to get a connection.
Please advise.
Thanks!
What do you mean you cannot configure the address object? This should/could be configured in Firewall -> Address Objects using the KB as an example for the settings.
This address object is the local network on the lan side of the Sonicwall that is accessible from the other end of the tunnel. So you have to do this on both Sonicwall's and use those in your tunnel configuration.
So on the 2600 you define it as the ip range that is accessible on the 170 and do the opposite on the 170.
This address object is the local network on the lan side of the Sonicwall that is accessible from the other end of the tunnel. So you have to do this on both Sonicwall's and use those in your tunnel configuration.
So on the 2600 you define it as the ip range that is accessible on the 170 and do the opposite on the 170.
ASKER
What I mean was on the 2600 I am able to configure Address Object it comes with that feature in the Network tab. On the TZ170 it does not have Address Object in the Network tab. The only place to put the LAN information for the Central Site is in the Destination Network section on the example above. So I am only assuming that this represents the Address Object in the SonicWALL TZ170.
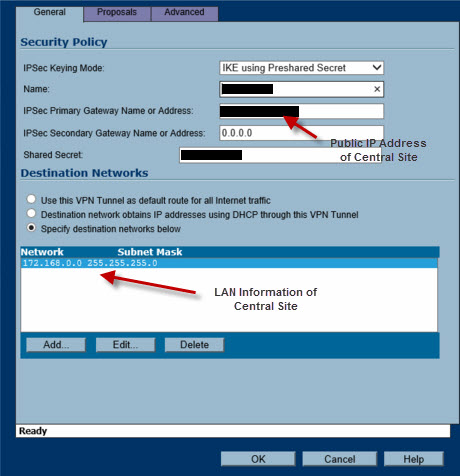
The setup is quite different from what I use. The destination IP above is an internal IP. Is it possibly supposed to be the external IP. After all you are not making a connection.
There are two different addresses and sets of addresses.
The first two are the wan ip addresses of the respective firewalls. These go in the "IPsec Primary Gateway Address" of the General Tab.
The other two are the lan ip address range of the lan at the OTHER end of the tunnel. So for the 2600 it is the subnet on the lan side of the 170. For the 170 it is the subnet on the lan side of the 2600.
If you cannot define an Address Object using "Network" then define it using Firewall -> Address Objects. These both have the same effect.
The way you describe you have done it in your last post is not correct, and is the reason it will not connect.
The first two are the wan ip addresses of the respective firewalls. These go in the "IPsec Primary Gateway Address" of the General Tab.
The other two are the lan ip address range of the lan at the OTHER end of the tunnel. So for the 2600 it is the subnet on the lan side of the 170. For the 170 it is the subnet on the lan side of the 2600.
If you cannot define an Address Object using "Network" then define it using Firewall -> Address Objects. These both have the same effect.
The way you describe you have done it in your last post is not correct, and is the reason it will not connect.
ASKER
ASKER
@John - The destination network IP address is the LAN address of the Central Site. Once the connection is made the 172.168.0.0/255.255.255.0 is where I can go on that network.
In the newer sonicwall routers this is done in the Address Objects. On the TZ170 I think this is how we map where we go on the other side. Correct me if I am wrong.
Thanks!
In the newer sonicwall routers this is done in the Address Objects. On the TZ170 I think this is how we map where we go on the other side. Correct me if I am wrong.
Thanks!
With respect to your bottom screenshot:
1. Use external IP address instead of NAME.
2. Local site should be a subnet (probably) instead of single IP.
1. Use external IP address instead of NAME.
2. Local site should be a subnet (probably) instead of single IP.
ASKER
John I am confused as to where you want me to put the external IP address. I can't put it in the "Name" section as that will not give me a connection.
IP Primary gateway is where the "Public IP address" of the other side goes. I am not sure what you mean on #2 of your comment. Are you referencing the "IKE Authentication"?
IP Primary gateway is where the "Public IP address" of the other side goes. I am not sure what you mean on #2 of your comment. Are you referencing the "IKE Authentication"?
This is confusing with two people telling you what to do. I suggest you take a look at the following, concentrating on the first section "Troubleshooting VPN Tunnel dropping or not initializing"
https://support.software.dell.com/sonicwall-tz-series/kb/sw7570
https://support.software.dell.com/sonicwall-tz-series/kb/sw7570
Your setup is different than mine (substantially different).
NAME may be just that and there is an IPsec Gateway address below that. It should be an external IP.
Think of the following approach.
Main site: IP Address of VPN router -> Main site External IP -> Internet <- Remote Site External IP <- IP Subnet of remote site.
So long as you have a setup like this, you should get a connection, and that should let you know if Phase 1 is working.
NAME may be just that and there is an IPsec Gateway address below that. It should be an external IP.
Think of the following approach.
Main site: IP Address of VPN router -> Main site External IP -> Internet <- Remote Site External IP <- IP Subnet of remote site.
So long as you have a setup like this, you should get a connection, and that should let you know if Phase 1 is working.
ASKER
John that is how I got it setup. But still no connection. Still getting "IKE Initiator: Remote party timeout - Retransmitting IKE request."
Let me suggest going through the link that carlmd supplied to see if that sheds light and respond to that. Also check firewall settings and that remote IP requests from the other site are not blocked.
With that error check the following:
Network connectivity between the units. (Hint: Try to access remote unit HTTPS management console from a host behind the local unit)
‘Disable this SA’ box is not checked in SA of IKE Responder.
IPSec Gateway address in Initiator SA specifies WAN address of IKE Responder
IPSec Gateway Name (if used) resolves to WAN address of IKE Responder
IKE Access Rules are enabled on both SonicWALLs.
No other firewalls in path blocking IKE (UDP 500) or IPSec (IP 50) protocols.
Contact ISP to see if they are blocking IKE (UDP 500) or IPSec (IP 50) protocols.
Network connectivity between the units. (Hint: Try to access remote unit HTTPS management console from a host behind the local unit)
‘Disable this SA’ box is not checked in SA of IKE Responder.
IPSec Gateway address in Initiator SA specifies WAN address of IKE Responder
IPSec Gateway Name (if used) resolves to WAN address of IKE Responder
IKE Access Rules are enabled on both SonicWALLs.
No other firewalls in path blocking IKE (UDP 500) or IPSec (IP 50) protocols.
Contact ISP to see if they are blocking IKE (UDP 500) or IPSec (IP 50) protocols.
ASKER
With that error check the following:
Network connectivity between the units. (Hint: Try to access remote unit HTTPS management console from a host behind the local unit) I was able to connect to central site using https://IP address
‘Disable this SA’ box is not checked in SA of IKE Responder. Where do I do this? VPN Advanced?
IPSec Gateway address in Initiator SA specifies WAN address of IKE Responder Where do I do this? And do I do it on both sides?
IPSec Gateway Name (if used) resolves to WAN address of IKE Responder
IKE Access Rules are enabled on both SonicWALLs. Where do I do this?
No other firewalls in path blocking IKE (UDP 500) or IPSec (IP 50) protocols. Nothing is blocking.
Contact ISP to see if they are blocking IKE (UDP 500) or IPSec (IP 50) protocols.
Network connectivity between the units. (Hint: Try to access remote unit HTTPS management console from a host behind the local unit) I was able to connect to central site using https://IP address
‘Disable this SA’ box is not checked in SA of IKE Responder. Where do I do this? VPN Advanced?
IPSec Gateway address in Initiator SA specifies WAN address of IKE Responder Where do I do this? And do I do it on both sides?
IPSec Gateway Name (if used) resolves to WAN address of IKE Responder
IKE Access Rules are enabled on both SonicWALLs. Where do I do this?
No other firewalls in path blocking IKE (UDP 500) or IPSec (IP 50) protocols. Nothing is blocking.
Contact ISP to see if they are blocking IKE (UDP 500) or IPSec (IP 50) protocols.
ASKER
Nothing is working still getting same messages. TZ170 is out of support so at this point we are at a lost.
Those errors mean to me that you are not making a basic connection.
Any way of trying a different router?
Any way of trying a different router?
ASKER
No these are the only two I have.
Setup 2600
General
Name {S2S TC107}
Ipsec Primary gateway name or address {Z107 Wan ip}
Shared Secret {both sides the same password}
local IKE ID: IPv4 Address {NSA2600 WAN Address}
peer IKE ID: IPv4 address {TZ107 Wan ip}
Network
Local Networks {choose local network NSA2600 side you want to have access to}
Remote Networks {choose remote network behind TZ107}
Proposals
IKE
Exchange Main Mode
Dh Group 2
encryption 3DES
Auithentication SHA1
Life Time 28800
IPSEC
Protocol ESP
encryption 3DES
Authentication SHA1
set enable perfect forwared security
DH Group 2
life time 28800
Advanced
Set option enable keep Alive
besure the option suppress automatic access rules creation for vpn police is not set
TZ107 side
Name {S2S NSA 2600}
Ipsec Primary gateway name or address {NSA2600 Wan ip}
Shared Secret {both sides the same password}
set radio button Specify networks below
add the network that is behind the NSA2600
Proposels
do exact the same as above
youre tunnel should come up now
General
Name {S2S TC107}
Ipsec Primary gateway name or address {Z107 Wan ip}
Shared Secret {both sides the same password}
local IKE ID: IPv4 Address {NSA2600 WAN Address}
peer IKE ID: IPv4 address {TZ107 Wan ip}
Network
Local Networks {choose local network NSA2600 side you want to have access to}
Remote Networks {choose remote network behind TZ107}
Proposals
IKE
Exchange Main Mode
Dh Group 2
encryption 3DES
Auithentication SHA1
Life Time 28800
IPSEC
Protocol ESP
encryption 3DES
Authentication SHA1
set enable perfect forwared security
DH Group 2
life time 28800
Advanced
Set option enable keep Alive
besure the option suppress automatic access rules creation for vpn police is not set
TZ107 side
Name {S2S NSA 2600}
Ipsec Primary gateway name or address {NSA2600 Wan ip}
Shared Secret {both sides the same password}
set radio button Specify networks below
add the network that is behind the NSA2600
Proposels
do exact the same as above
youre tunnel should come up now
ASKER
what is there before the sonicwalls ? is there a router or something ?
ASKER
I have a comcast router on the TZ side and a Brighthouse router on the 2600 side.
Please note that on the 2600 router I have 3 other S2S running it only this one that is not working.
On the TZ170 router, I put the comcast router in bridge mode and it still didn't work. This is the only S2S on the tz 170.
Please note that on the 2600 router I have 3 other S2S running it only this one that is not working.
On the TZ170 router, I put the comcast router in bridge mode and it still didn't work. This is the only S2S on the tz 170.
ASKER
From the tz170 I can connect to the 2600 from a browser(https:wanip) but that is it.
You should enable ping on the WAN of both Sonicwalls, and then use ping (under diagnostics) to ping the other Sonicwall from the opposite one, and then the opposite. Do you get a ping response from either or both?
i have the strong feeling the comcast router is blocking ipsec traffic on port 500 udp.
is it posible to put a switch between the comcast router and the tz107 and run whireshark.
we need to know if the ipsec traffic is allowed in this path
is it posible to put a switch between the comcast router and the tz107 and run whireshark.
we need to know if the ipsec traffic is allowed in this path
Ping is not the problem. i have seen many times. that routers even when they are in bridge mode. thinking that ipsec traffic if for them. or block the traffic. let CervisTECH first make a packet trace.
ASKER
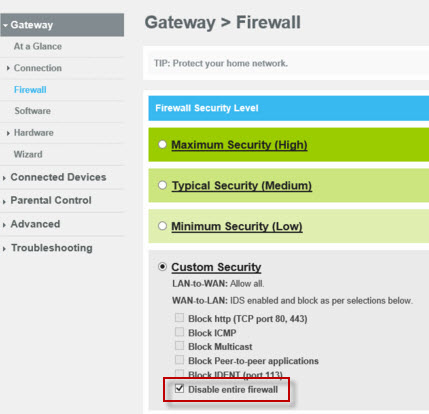
@Benjamine,
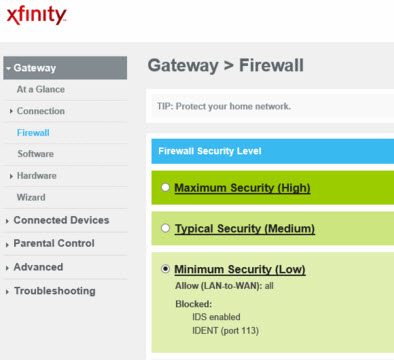
Here is the comcast firewall config. The only port that is being blocked is port 113. I will find a switch and plug the router into it and see how that works.
@Carlmd,
Where do I go to enable ping on the 2600 and tz170?
Here is the comcast firewall config. The only port that is being blocked is port 113. I will find a switch and plug the router into it and see how that works.
@Carlmd,
Where do I go to enable ping on the 2600 and tz170?
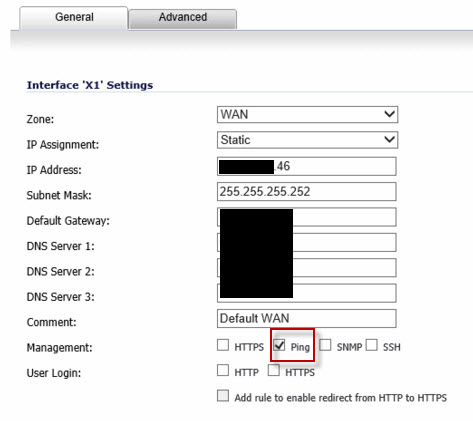
enable ping on a sonicwall is a interface property
You would enable ping on the Network settings for X1, General Tab.
Diagnostics are found under System, and then under Diagnostic Tools.
Diagnostics are found under System, and then under Diagnostic Tools.
ASKER
please make the packet capture, then we know what the problem is :)
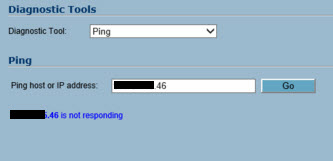
Ok, so that proves there is something blocking access to the 2600.
On the same diagnostics screen from the TZ170 do a traceroute to the 2600 and post the result.
On the same diagnostics screen from the TZ170 do a traceroute to the 2600 and post the result.
ASKER
I downloaded wireshark how do I configure it to get the information you need?
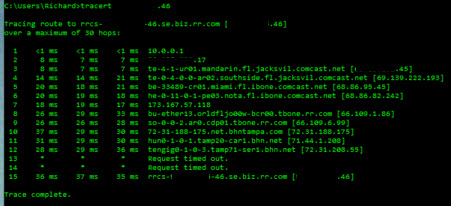
From the traceroute the last place it gets to is 72.31.208.55. Is that on your network, and if so, what is it?
For the next test I suggest you turn off the Xfinity Gateway Firewall. Yes I see that it indicates only one thing blocked, but lets be sure. Or, did you ever get a chance to bypass it with a switch?
For the next test I suggest you turn off the Xfinity Gateway Firewall. Yes I see that it indicates only one thing blocked, but lets be sure. Or, did you ever get a chance to bypass it with a switch?
ASKER
ASKER
Yes I did put a NetGear Switch between the tz170 and the xfinity router. I am getting the same results.
Since the problem appears to be on the 2600 end, I need you turn off the firewall on that end assuming you have the same service there. Since you can ping the 170, that end would not be the problem. Something is stopping you from getting to the 2600 from the 170.
Just to verify, you do have some number of fixed ip addresses from your ISP at the 2600 end, correct? What type of service is this, DSL, fios, leased line, or something else.
Just to verify, you do have some number of fixed ip addresses from your ISP at the 2600 end, correct? What type of service is this, DSL, fios, leased line, or something else.
ASKER
Did we throw in the towel on this one?
A question...
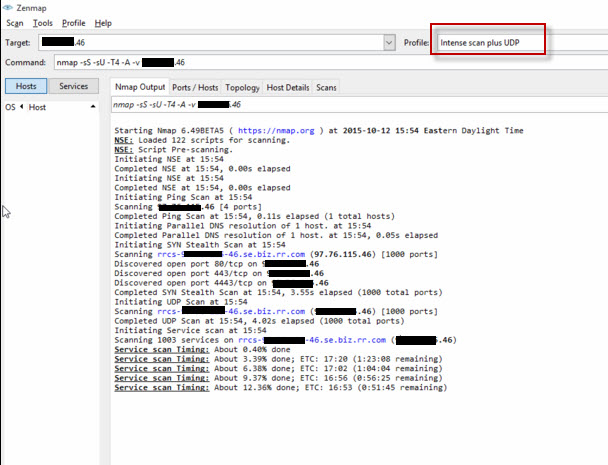
On the 2600 end we can't ping or traceroute to the Sonciwall, and you scan does not show anything.
So, how are you getting to the admin login at the 2600?
On the 2600 end we can't ping or traceroute to the Sonciwall, and you scan does not show anything.
So, how are you getting to the admin login at the 2600?
ASKER
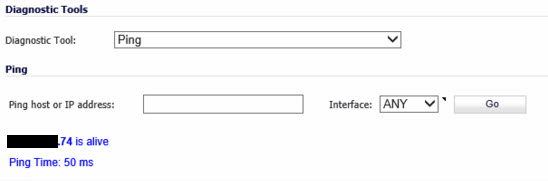
I can now ping from both sides but I am still not able to get a connection.
@Carlmd, do you know the command I can type in wireshark to test UDP port 500 to see if it is open or not on either end?
@Carlmd, do you know the command I can type in wireshark to test UDP port 500 to see if it is open or not on either end?
What did you do to be able to ping the 2600 end?
The following will tell you how to test port usage.
https://ask.wireshark.org/questions/378/using-wireshark-to-determine-port-usage
It does not appear that you ever stated how you created the site to site vpn tunnel? Since we have gone around with this for a while, one thing you can try is to just start over. Leave what you have in place and use the wizard to create the tunnel. If you are willing to do this use the following:
https://support.software.dell.com/kb/sw4102
The following will tell you how to test port usage.
https://ask.wireshark.org/questions/378/using-wireshark-to-determine-port-usage
It does not appear that you ever stated how you created the site to site vpn tunnel? Since we have gone around with this for a while, one thing you can try is to just start over. Leave what you have in place and use the wizard to create the tunnel. If you are willing to do this use the following:
https://support.software.dell.com/kb/sw4102
ASKER
I created the S2S first manually and then using the wizard with the same results using both. I called my ISP(Comcast) to see if UDP port 500 was being blocked on their end and it is not. So now I am kind of stuck as to where to go on this.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Wasn't really able to resolve this issue but this provided me with the best answers and troubleshooting tips.
Thanks!
Thanks!


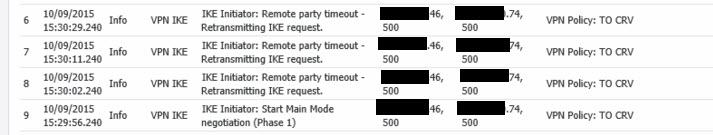





Do both ends have a fixed ip address?
If yes, take a took at:
https://support.software.dell.com/kb/sw5857
If no, what is the configuration?