How do I find source of account lockouts - event messages have spoofed machine names
Two or three times a day essentially all of my users are getting their account locked out. I suspect someone on my network has a virus that is trying to brute force passwords on my users. The trouble I am having is identifying the machine(s) that are involved in this. They are somehow spoofing the machine name so the security event shows a NetBIOS name that does not exist in my network.
I am running primarily Windows 7 workstations and laptops; and Windows 2008 R2 servers and domain controllers.
Any guidance on how to locate the source of this chaos will be much appreciated!
I am running primarily Windows 7 workstations and laptops; and Windows 2008 R2 servers and domain controllers.
Any guidance on how to locate the source of this chaos will be much appreciated!
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Have you tried Advance Audit Policy ?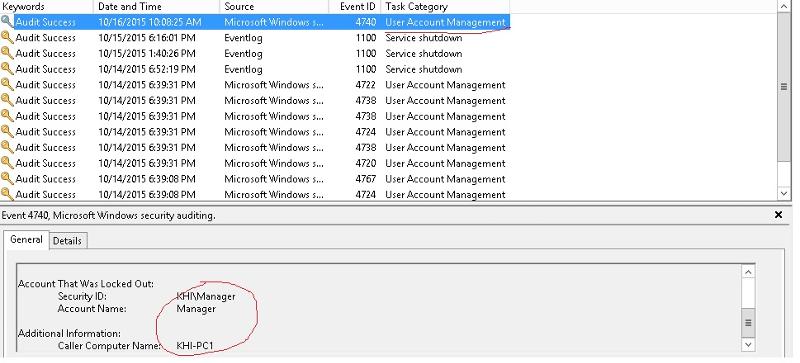 Audi_Lockout.jpg
Audi_Lockout.jpg
 Audi_Lockout.jpg
Audi_Lockout.jpg
Netwrix account lockout examiner is free and gives plenty of information to nail down the problem...I had a Conflicker infection a couple a years ago and i managed to find the workstation which was causing this havoc with the help of this tool...
You can get it here
You can get it here
ASKER
Thanks everyone for the input.
John, I am already running the (free version of) Netwrix ALE and it is less than useful at locating offending devices when the workstation name is spoofed or blank.
Muhammed - I have not set up the advanced auditing, but will look into that.
Arnold - The EventCombMT tool helped to narrow it down. It turned out that one of the firewall administrators had left our disaster recovery site essentially open to the Internet - and everyone was having fun.
Lockouts went away after closing the firewall. Will be having folks checking equipment there for any hint of a compromise.
Thanks again
John, I am already running the (free version of) Netwrix ALE and it is less than useful at locating offending devices when the workstation name is spoofed or blank.
Muhammed - I have not set up the advanced auditing, but will look into that.
Arnold - The EventCombMT tool helped to narrow it down. It turned out that one of the firewall administrators had left our disaster recovery site essentially open to the Internet - and everyone was having fun.
Lockouts went away after closing the firewall. Will be having folks checking equipment there for any hint of a compromise.
Thanks again
Here is a ref what you need to do with the tool included...
Here is a link where it explains things http://social.technet.microsoft.com/wiki/contents/articles/4585.account-locked-out-troubleshooting-eventcombmt.aspx