punkrawkdude99
asked on
Watchguard with Multiple wan connections
Im very new to Watchguard.... Ive only dealt with sonicwall and this is super easy to do
There are 2 wan connections...
Int 0 is a 25/5 TWC cable connection
Int 4 is a 5/5 Fiber connection
Currently all the phones are connected to 10.0.5.x wired
and the wifi clients get 192.168.0.1
however wired or wireless they all seem to go through the fiber connection
How do i force the wireless connections to use the INT 0 and the wired connections to use the INT 4??
The model number of the box is an XTM-25W
There are 2 wan connections...
Int 0 is a 25/5 TWC cable connection
Int 4 is a 5/5 Fiber connection
Currently all the phones are connected to 10.0.5.x wired
and the wifi clients get 192.168.0.1
however wired or wireless they all seem to go through the fiber connection
How do i force the wireless connections to use the INT 0 and the wired connections to use the INT 4??
The model number of the box is an XTM-25W
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
ok here are a few screenshots.... tried messing around by following that link and i dont have screens that look like that
Screenshot-2015-11-12-at-2.24.37-PM.png
Screenshot-2015-11-12-at-2.26.36-PM.png
Screenshot-2015-11-12-at-2.27.25-PM.png
Screenshot-2015-11-12-at-2.28.28-PM.png
Screenshot-2015-11-12-at-2.29.03-PM.png
Screenshot-2015-11-12-at-2.24.37-PM.png
Screenshot-2015-11-12-at-2.26.36-PM.png
Screenshot-2015-11-12-at-2.27.25-PM.png
Screenshot-2015-11-12-at-2.28.28-PM.png
Screenshot-2015-11-12-at-2.29.03-PM.png
Hi, punkrawkdude99. The reason your screen shots look different from the link is that you're using the Web UI instead of the Watchguard System Manager. It's just 2 different ways to do the same things. Some of us who've been working with Watchguard for a while still prefer the older interface (the System Manager) because in general it's a bit faster and we're used to it! At first glance, I think the problem may be that the 2 networks (the Trusted network and the wireless network) are bridged, but I'll take a closer look at your screen captures and see if I can noodle out what's happening.
ASKER
I believe that to be an issue as well..
I didn't want to Unbridge to test as they were having a meeting with some pretty higher ups yesterday
There is an option to create other wireless networks.. I created one as trusted but then just got tied up with other stuff after that
I didn't want to Unbridge to test as they were having a meeting with some pretty higher ups yesterday
There is an option to create other wireless networks.. I created one as trusted but then just got tied up with other stuff after that
OK - here's the explanation of what the bridge does, from the Watchguard documentation:
<<About LAN Bridges
A local area network bridge logically combines multiple interfaces to operate as a single network, with a single interface name and IP address. You configure the interface IP address and other interface settings in the bridge configuration, and then configure interfaces as members of the bridge. A bridge must include at least one interface, and can include any combination of physical, wireless, and link aggregation interfaces.
You can configure a bridge in the trusted, optional, or custom security zone. The configuration settings for a bridge are similar to the settings for any other trusted, optional, or custom network interface. For example, you can configure DHCP to give IP addresses to clients on a bridge, or use the bridge name as an alias in firewall policies.
To use a bridge, you must:
1.Create a Network Bridge Configuration.
2.Assign a Network Interface to a Bridge.
If you want all of the Firebox or XTM device interfaces to be on the same network, we recommend that you use bridge mode for your network configuration.>>
So, that explains why you're seeing all of the communication from the wireless network going through the same interface as the wired connections, because they're bridged together.
Before we look at removing the bridge, please take another screen capture of the firewall policies, similar to the one below from one of my networks. Please make sure to expand the From, To and Port columns (which I didn't do) so that we can see all the settings in those columns:
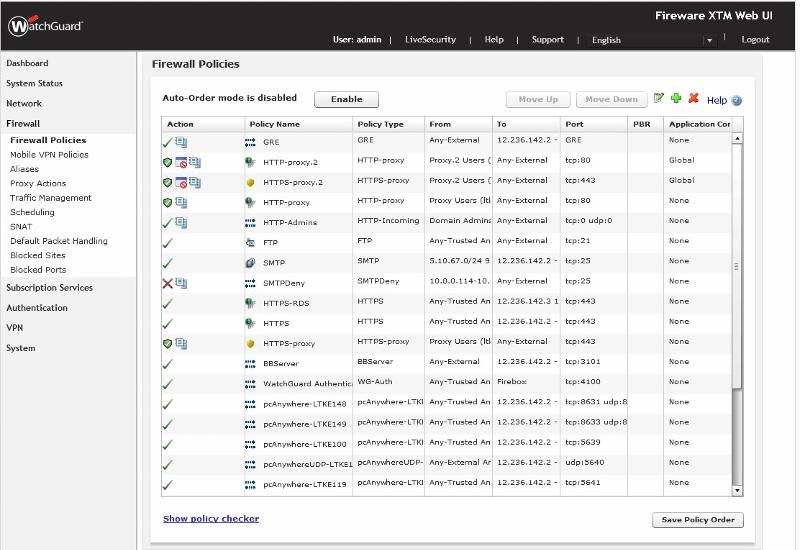
<<About LAN Bridges
A local area network bridge logically combines multiple interfaces to operate as a single network, with a single interface name and IP address. You configure the interface IP address and other interface settings in the bridge configuration, and then configure interfaces as members of the bridge. A bridge must include at least one interface, and can include any combination of physical, wireless, and link aggregation interfaces.
You can configure a bridge in the trusted, optional, or custom security zone. The configuration settings for a bridge are similar to the settings for any other trusted, optional, or custom network interface. For example, you can configure DHCP to give IP addresses to clients on a bridge, or use the bridge name as an alias in firewall policies.
To use a bridge, you must:
1.Create a Network Bridge Configuration.
2.Assign a Network Interface to a Bridge.
If you want all of the Firebox or XTM device interfaces to be on the same network, we recommend that you use bridge mode for your network configuration.>>
So, that explains why you're seeing all of the communication from the wireless network going through the same interface as the wired connections, because they're bridged together.
Before we look at removing the bridge, please take another screen capture of the firewall policies, similar to the one below from one of my networks. Please make sure to expand the From, To and Port columns (which I didn't do) so that we can see all the settings in those columns:

ASKER
I think I attached the fw policy... It's really basic
Pretty much allows everything outbound and ping as well
Pretty much allows everything outbound and ping as well
Ok - here's what I recommend:
1. Make a BACKUP of the current configuration on the Watchguard, just in case.
2. Remove the LAN bridge and the bridged wireless network.
3. Create a new network for the wireless network connection, making it an Optional network and using the same IP configuration. You'd do this from the Network/Interfaces page. Click the Optional network interface that corresponds to the physical interface on the Firebox where the wireless network is connected. Then click Configure to set it up with the correct IP range, etc. IF, however, the wireless network is set up using the Firebox's internal wireless capabilities, rather than creating an Optional network, you'd need to go to the Wireless network settings and make some changes there. Let me know if this is the case.
4. Edit the existing Outgoing policy so that the "To" is "External TWC Fiber" and the "From" is "Trusted."
5. Create a new Outgoing policy (i.e., "Outgoing-Wireless") using the "External 25 MB TWC Cable" as the "To" and the Optional (i.e., wireless) network as the "From."
Of course, you'll need to do this at a time when you can test the new configuration without interfering with user access to any resources they need either internally or externally.
1. Make a BACKUP of the current configuration on the Watchguard, just in case.
2. Remove the LAN bridge and the bridged wireless network.
3. Create a new network for the wireless network connection, making it an Optional network and using the same IP configuration. You'd do this from the Network/Interfaces page. Click the Optional network interface that corresponds to the physical interface on the Firebox where the wireless network is connected. Then click Configure to set it up with the correct IP range, etc. IF, however, the wireless network is set up using the Firebox's internal wireless capabilities, rather than creating an Optional network, you'd need to go to the Wireless network settings and make some changes there. Let me know if this is the case.
4. Edit the existing Outgoing policy so that the "To" is "External TWC Fiber" and the "From" is "Trusted."
5. Create a new Outgoing policy (i.e., "Outgoing-Wireless") using the "External 25 MB TWC Cable" as the "To" and the Optional (i.e., wireless) network as the "From."
Of course, you'll need to do this at a time when you can test the new configuration without interfering with user access to any resources they need either internally or externally.
ASKER
Man something went terribly wrong....
i think part of the problem is the TWC cable connect was setup wrong
i think part of the problem is the TWC cable connect was setup wrong
ASKER
okay so i messed with a bunch of crap.... now everything seems to go out the fiber interface and nothing goes out the twc cable one
the twc cable interface is dhcp :( not sure the firebox will play well with that
before wireless would get a 192.168.0.x address....
now the cable modem is giving out that address
so i moved wireless to 192.168.1.0
at this point wireless and cabled both get 10.0.5.0 addresses
the second wireless network does get a 192.168.99.0 address but doesnt route anywhere
Screenshot-2015-11-19-at-5.01.50-PM.png
Screenshot-2015-11-19-at-5.02.32-PM.png
Screenshot-2015-11-19-at-5.05.01-PM.png
Screenshot-2015-11-19-at-5.05.41-PM.png
Screenshot-2015-11-19-at-5.05.46-PM.png
Screenshot-2015-11-19-at-5.05.52-PM.png
the twc cable interface is dhcp :( not sure the firebox will play well with that
before wireless would get a 192.168.0.x address....
now the cable modem is giving out that address
so i moved wireless to 192.168.1.0
at this point wireless and cabled both get 10.0.5.0 addresses
the second wireless network does get a 192.168.99.0 address but doesnt route anywhere
Screenshot-2015-11-19-at-5.01.50-PM.png
Screenshot-2015-11-19-at-5.02.32-PM.png
Screenshot-2015-11-19-at-5.05.01-PM.png
Screenshot-2015-11-19-at-5.05.41-PM.png
Screenshot-2015-11-19-at-5.05.46-PM.png
Screenshot-2015-11-19-at-5.05.52-PM.png
The wireless interface type is "Optional," which would essentially create a bridge to an optional interface, but there is no optional interface enabled on one of the 4 Firebox interfaces. You need to re-enable the Firebox interface 1, configure it as an Optional interface using the 192.168.1.1 network, and enable the DHCP server for that network, and then the wireless interface will connect to it. IOW, the wireless interface has to have a physical port on the Firebox to connect to, even though the connection is wireless rather than physical. You will need to give the wireless interface a different IP address, say 192.168.1.2/24, and then the Optional network can take over 192.168.1.1/24. For the DHCP range, you want to exclude those two addresses so that only 192.168.1.3 and above can be used by other devices on that network.
At that point, your policy directing outgoing traffic from Any-Optional to the cable connection should take effect. BTW, you should have your policies in order so that the priority policies are at the top. That is, the two "Outgoing" policies should probably be at the top of the list.
At that point, your policy directing outgoing traffic from Any-Optional to the cable connection should take effect. BTW, you should have your policies in order so that the priority policies are at the top. That is, the two "Outgoing" policies should probably be at the top of the list.
Also - when you say the TWC cable interface is DHCP, do you mean that it's configured to assign private IP addresses to internal devices? Also, I forgot to say specifically - you need to have DHCP enabled only on either the Optional or the Wireless side of the network, not both...Now that I think about it, it's probably better to have it enabled on the Wireless interface rather than the Optional one, since the wireless devices (I assume workstations) will be connecting to that first.
ASKER
Yeah the two cable modem is also acting like a nat device itself
So it's giving the firewall essentially a 192.168.0 address
Eth1 was set to bridge so you want me to set that as opt and to give out Dhcp but not to bridge to connect between wireless to the eth0?
So it's giving the firewall essentially a 192.168.0 address
Eth1 was set to bridge so you want me to set that as opt and to give out Dhcp but not to bridge to connect between wireless to the eth0?
ASKER
okay so i have it to the point where i can only get it to route out one gateway.... im not sure why but when i enable the fw policy to send optional outbound through the twc cable gateway it just stops
i have to go to the other outbound policy and add optional to it for the internet to work over wireless
i was able to switch the TWC cable modem into pass through so now its just acting like a modem and getting a public ip
i have to go to the other outbound policy and add optional to it for the internet to work over wireless
i was able to switch the TWC cable modem into pass through so now its just acting like a modem and getting a public ip
ASKER
okay so after messing with it all day i finally got a few things as an outcome
1. eth0 is now in pass through mode and has a public ip'
2. both wireless networks work however do different things
wireless network1 aka onyx 2.4 is set to give out ip addresses in the 192.168.0.x range but gives out ips in the 10.0.5.x range and continues to go out through the fiber 5meg gateway
wireless network2 aka onyx2 is giving out ips of 192.168.99x and routes out the twc 50meg gateway
i dunno wth to do next :/
Screenshot-2015-11-20-at-4.17.23-PM.png
Screenshot-2015-11-20-at-4.19.55-PM.png
Screenshot-2015-11-20-at-4.20.08-PM.png
Screenshot-2015-11-20-at-4.20.29-PM.png
1. eth0 is now in pass through mode and has a public ip'
2. both wireless networks work however do different things
wireless network1 aka onyx 2.4 is set to give out ip addresses in the 192.168.0.x range but gives out ips in the 10.0.5.x range and continues to go out through the fiber 5meg gateway
wireless network2 aka onyx2 is giving out ips of 192.168.99x and routes out the twc 50meg gateway
i dunno wth to do next :/
Screenshot-2015-11-20-at-4.17.23-PM.png
Screenshot-2015-11-20-at-4.19.55-PM.png
Screenshot-2015-11-20-at-4.20.08-PM.png
Screenshot-2015-11-20-at-4.20.29-PM.png
ASKER
a little more in depth
I figured out how to route some of the traffic out of different gateways
i have 2 external interfaces
int0 50/10mb cable and
int4 5/5mb fiber
i have one wired interface
int3 10.0.5.x
i have two wireless interfaces
ath1 192.160.0.x and
ath2 192.168.99.x
both set to optional
i have 2 firewall policies
1. any traffic from 10.0.5.x network goes out the fiber connection
2. any traffic out of either ath1 or ath2 goes out the TWC cable connection
so far everything is all 10.0.5.x traffic goes out the fiber connection
all 10.0.99.x wireless2 traffic goes out the twc cable connection
the one issue is ath1 seems to pick up dhcp from 10.0.5.x instead of 192.168.0.x
it also sends traffic out of the wrong gateway
I figured out how to route some of the traffic out of different gateways
i have 2 external interfaces
int0 50/10mb cable and
int4 5/5mb fiber
i have one wired interface
int3 10.0.5.x
i have two wireless interfaces
ath1 192.160.0.x and
ath2 192.168.99.x
both set to optional
i have 2 firewall policies
1. any traffic from 10.0.5.x network goes out the fiber connection
2. any traffic out of either ath1 or ath2 goes out the TWC cable connection
so far everything is all 10.0.5.x traffic goes out the fiber connection
all 10.0.99.x wireless2 traffic goes out the twc cable connection
the one issue is ath1 seems to pick up dhcp from 10.0.5.x instead of 192.168.0.x
it also sends traffic out of the wrong gateway
Good work! Let me take a look at your latest screen caps and I'll get back with any thoughts and ideas.
How are the devices that are using ath1 getting their IP addresses? It looks like they're being assigned addresses by the DHCP server on the Trusted network (Phone GW) rather than getting them from either the ath1 wireless network itself with DHCP server configured or a configured Optional network with ath1 bridged to that network.
ASKER
There is no bridge network...
I can't seem to figure out why ath2 works properly and ath1 doesn't..
They are both set as optional and both setup with Dhcp servers..
I guess I can just disable the wireless on ath1 and set leave ath2 on and change the name and network name and Dhcp scope the same as ath1 was... Since it works properly
I can't seem to figure out why ath2 works properly and ath1 doesn't..
They are both set as optional and both setup with Dhcp servers..
I guess I can just disable the wireless on ath1 and set leave ath2 on and change the name and network name and Dhcp scope the same as ath1 was... Since it works properly
You could certainly try that! One thing that could be operating here is that ath1 was originally bridged to the Trusted (10.0.5.x) network. So, there may still be some setting in the properties of ath1 that's maintaining that connection - check it carefully. Make sure that all changes you've made have been saved too, of course. You also might try restarting the Watchguard firewall to see if that corrects the problem. Or as I suggested above, reconfigure the eth1 network as an Optional network in the 192.168.0.x network and bridge ath1 to eth1.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Its the actual solution.....
No one picked up in the screenshots that to needed to be any external and not the direct external interface
No one picked up in the screenshots that to needed to be any external and not the direct external interface
ASKER
i dont know watchguard well at all