firewall rules
hello,
I am using pfsense as my firewall. I set it up on an old computer, and it has two NIC's - one for lan and one for wan traffic. It is working fine, and I am using the "block all traffic" method of firewalls, then just poking holes in the firewall as needed.
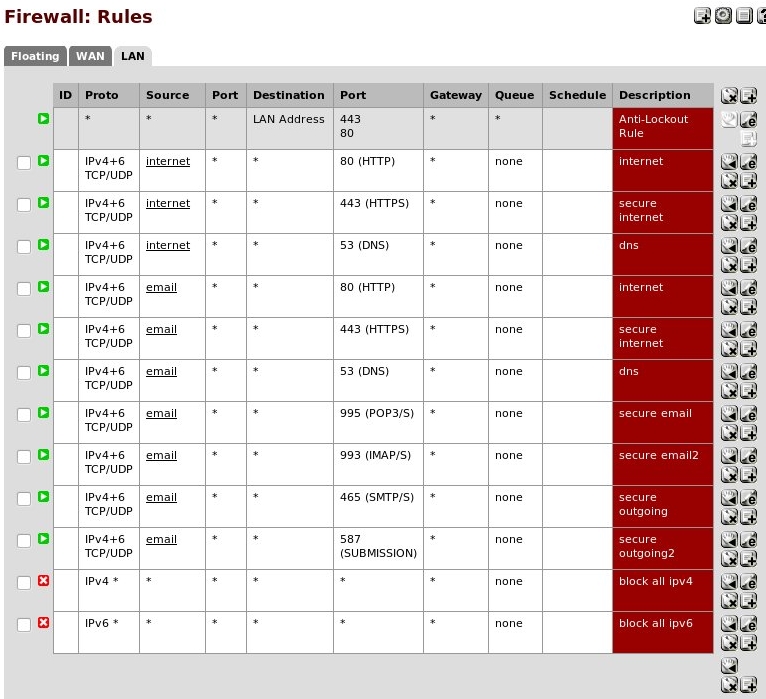
That is also working fine, so my rules look like this
I was reading about the ideal firewall setup, and saw something that said a firewall should block any local traffic that doesn't originate from the lan. I take that to mean if a malicious computer tries spoofing you IP address or MAC address and tries to send traffic on your network, but even though the malicious computer has a valid MAC address, the traffic would still be coming from the wan, or outside of the lan.
So my question is, is there a way to test and confirm that your firewall will block this type of traffic. If there isn't a good way to test it, how about just confirming that the firewall would block this type of traffic?
I am using pfsense as my firewall. I set it up on an old computer, and it has two NIC's - one for lan and one for wan traffic. It is working fine, and I am using the "block all traffic" method of firewalls, then just poking holes in the firewall as needed.
That is also working fine, so my rules look like this

I was reading about the ideal firewall setup, and saw something that said a firewall should block any local traffic that doesn't originate from the lan. I take that to mean if a malicious computer tries spoofing you IP address or MAC address and tries to send traffic on your network, but even though the malicious computer has a valid MAC address, the traffic would still be coming from the wan, or outside of the lan.
So my question is, is there a way to test and confirm that your firewall will block this type of traffic. If there isn't a good way to test it, how about just confirming that the firewall would block this type of traffic?
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER