Winsoup
asked on
Cisco ASA 5505
We took over a small company that is using a Cisco ASA 5505 and we've noticed that their internet speeds we're slow.
They had their ISP come in and test and directly from the modem they are getting 200mbps down which is what they should get.
When we connect to the firewall then they are only getting 20mbps down.
I know that the 5505 probably isn't going to get 200mbps but shouldn't it be better than 20?
I'm not an expert on this firewall so I'm not really sure where to look to see if there are any policies that could be causing this or what to look for next. I've tried using different ports on the firewall as well. Speeds are set to auto but I did also try manually setting them but that didn't change anything. Any help on what to check would be appreciated.
I can send any logs and configs as requested.
Thank you!!
They had their ISP come in and test and directly from the modem they are getting 200mbps down which is what they should get.
When we connect to the firewall then they are only getting 20mbps down.
I know that the 5505 probably isn't going to get 200mbps but shouldn't it be better than 20?
I'm not an expert on this firewall so I'm not really sure where to look to see if there are any policies that could be causing this or what to look for next. I've tried using different ports on the firewall as well. Speeds are set to auto but I did also try manually setting them but that didn't change anything. Any help on what to check would be appreciated.
I can send any logs and configs as requested.
Thank you!!
Just to make sure, there isn't a mixup between Mbps and MBps is there?
Providers normally use mbps but a lot of software uses MBps.
Like GM GM said, have a look at your config (or post it here so we can have a look). The 5505 has 100mbps interfaces so you should be able to hit that (100mbps or 10MBps).
I have a 5505 at home (yeah, I know) with a 150mpbs internet connection and I am able to hit 10-11MBps with that. So my first guess would be that there is something in your config or hardware.
Providers normally use mbps but a lot of software uses MBps.
Like GM GM said, have a look at your config (or post it here so we can have a look). The 5505 has 100mbps interfaces so you should be able to hit that (100mbps or 10MBps).
I have a 5505 at home (yeah, I know) with a 150mpbs internet connection and I am able to hit 10-11MBps with that. So my first guess would be that there is something in your config or hardware.
ASKER
Your policy-map type... looks to be inspecting http. I was hoping you'll show a little more of your capture.
Send me capture of "show run | b policy-map" of everything.
show run class-map
show service-policy police
Send me capture of "show run | b policy-map" of everything.
show run class-map
show service-policy police
The 'service-policy' command on ASA that enabled to an interface thus control the amount of bandwidth.
look for "service-policy xxxx interface outside"
look for "service-policy xxxx interface inside"
to remove add "no" in front of it.
look for "service-policy xxxx interface outside"
look for "service-policy xxxx interface inside"
to remove add "no" in front of it.
ASKER
Here is the entire sh run log. (with IP's taken out of course)
This is the output from sh run class-map
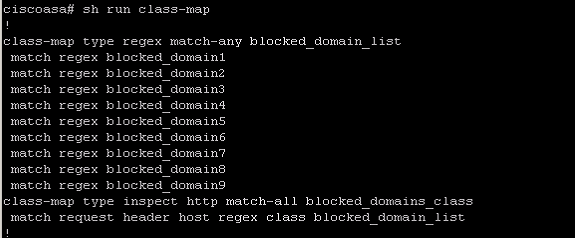
Sh service-policy police doesn't have any output
ciscoasa# sh run
: Saved
:
ASA Version 8.2(2)
!
!
interface Vlan1
nameif inside
security-level 100
ip address xxxxx
!
interface Vlan2
nameif outside
security-level 0
ip address xxxxxxx
!
interface Vlan3
no forward interface Vlan1
nameif dmz
security-level 50
<--- More --->
no ip address
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
regex blocked_domain5 "\.chartbeat\.net"
regex blocked_domain6 "\.foxsports\.com"
regex blocked_domain7 "\.mlb\.com"
regex blocked_domain8 "\.aolmedia\."
regex blocked_domain9 "\.xvideos\."
<--- More --->
regex blocked_domain1 "\.espn\.com"
regex blocked_domain2 "espn\."
regex blocked_domain3 "tinker\."
regex blocked_domain4 "\.howardstern\.com"
boot system disk0:/asa822-k8.bin
ftp mode passive
dns server-group DefaultDNS
domain-name xxxxxx
same-security-traffic permit inter-interface
object-group service DM_INLINE_TCP_1 tcp
port-object eq www
port-object eq https
object-group service RDP-Access tcp-udp
description Remote Desktop Protocol
port-object eq 3389
object-group protocol TCPUDP
protocol-object udp
protocol-object tcp
object-group service 8080 tcp
description 8080
port-object eq 8080
object-group service DM_INLINE_SERVICE_1
service-object tcp eq 6036
service-object udp eq 6036
<--- More --->
access-list outside_access_in extended permit tcp Postini 255.255.240.0 any eq smtp
access-list outside_access_in extended permit tcp any any object-group DM_INLINE_TCP_1
access-list outside_access_in extended permit object-group TCPUDP any interface outside eq www
access-list outside_access_in extended permit tcp any interface outside eq https
access-list outside_access_in extended deny object-group TCPUDP any interface outside object-group RDP-Access
access-list outside_access_in extended permit tcp any interface outside
access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_1 any interface outside
access-list outside_access_in extended permit tcp any interface outside eq 81
access-list Inside_access_out extended permit ip any any
access-list user-acl extended deny tcp host 10.0.0.203 any eq www
access-list user-acl extended permit tcp any any eq www
access-list user-acl extended permit tcp host 10.0.0.203 any eq www
pager lines 24
logging enable
logging asdm-buffer-size 512
logging asdm informational
mtu inside 1500
mtu outside 1500
mtu dmz 1500
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-625.bin
no asdm history enable
arp timeout 14400
nat-control
<--- More --->
global (outside) 1 interface
nat (inside) 1 0.0.0.0 0.0.0.0
static (inside,outside) tcp interface www 10.0.0.220 www netmask 255.255.255.255
static (inside,outside) udp interface www 10.0.0.220 www netmask 255.255.255.255
static (inside,outside) tcp interface https 10.0.0.220 https netmask 255.255.255.255
static (inside,outside) tcp interface 3389 10.0.0.220 3389 netmask 255.255.255.255
static (inside,outside) udp interface 3389 10.0.0.220 3389 netmask 255.255.255.255
static (inside,outside) tcp interface smtp 10.0.0.220 smtp netmask 255.255.255.255
static (inside,outside) tcp interface 6036 10.0.0.222 6036 netmask 255.255.255.255
static (inside,outside) udp interface 6036 10.0.0.222 6036 netmask 255.255.255.255
static (inside,outside) tcp interface 81 10.0.0.222 81 netmask 255.255.255.255
access-group Inside_access_out in interface inside
access-group outside_access_in in interface outside
route outside xxxxxxx
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-record DfltAccessPolicy
http server enable
http 10.0.0.0 255.255.255.0 inside
http 10.0.0.2 255.255.255.255 dmz
<--- More --->
http 10.0.0.1 255.255.255.255 inside
http 192.168.1.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
telnet 10.0.0.0 255.255.255.0 inside
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd auto_config outside
!
dhcpd address 10.0.0.120-10.0.0.200 inside
dhcpd dns xxxxxx interface inside
dhcpd domain xxxxx interface inside
dhcpd enable inside
!
threat-detection basic-threat
threat-detection statistics port
threat-detection statistics protocol
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
<--- More --->
webvpn
!
class-map type regex match-any blocked_domain_list
match regex blocked_domain1
match regex blocked_domain2
match regex blocked_domain3
match regex blocked_domain4
match regex blocked_domain5
match regex blocked_domain6
match regex blocked_domain7
match regex blocked_domain8
match regex blocked_domain9
class-map type inspect http match-all blocked_domains_class
match request header host regex class blocked_domain_list
!
!
policy-map type inspect http http_inspection_policy
parameters
match request method connect
drop-connection log
class blocked_domains_class
reset log
policy-map global_policy
!
<--- More --->
service-policy global_policy global
prompt hostname context
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
Cryptochecksum:9b773fccf1832b9d232b27ad7d823cca
: end
ciscoasa# exit
LogoffThis is the output from sh run class-map

Sh service-policy police doesn't have any output
I don't see anything that would throttle your bandwidth.
Two approaches that I would try. But first be sure you perform a backup config.
1. " no service-policy global_policy global" Turn off your http and blocked domains inspection, global applies the policy map to all interfaces. Then check your speed to isolate.
2. Open a ticket with your ISP, configure your uplink interface to static. Be sure you have them on phone and then to implement. I have seen/experienced even though your show interface is Auto-Duplex (Full-duplex), Auto-speed(100 Mbps) it still cause issue.
interface Ethernet0/0
speed 100
duplex full
Two approaches that I would try. But first be sure you perform a backup config.
1. " no service-policy global_policy global" Turn off your http and blocked domains inspection, global applies the policy map to all interfaces. Then check your speed to isolate.
2. Open a ticket with your ISP, configure your uplink interface to static. Be sure you have them on phone and then to implement. I have seen/experienced even though your show interface is Auto-Duplex (Full-duplex), Auto-speed(100 Mbps) it still cause issue.
interface Ethernet0/0
speed 100
duplex full
ASKER
I have done step 2 already with their ISP and it didn't make a difference for us.
Issue I have with making too many changes to the firewall is that I am in Minnesota and they are in Florida so if I get disconnected then I can't get back in.
I guess I could just not write the change and have them restart the firewall if necessary
Issue I have with making too many changes to the firewall is that I am in Minnesota and they are in Florida so if I get disconnected then I can't get back in.
I guess I could just not write the change and have them restart the firewall if necessary
Perform after hours. Reload will not save config, don't "wr mem" until you're certain. For remote network changes it is best to use 'reload' as a backdoor so even if you're disconnected, you'll wait a few minutes.
The following example reloads ASA in 10 minutes:
ASA5505#reload in 10
To aborts scheduled reload:
ASA5505#reload cancel
The following example reloads ASA in 10 minutes:
ASA5505#reload in 10
To aborts scheduled reload:
ASA5505#reload cancel
ASKER
I removed the global policy and tested but it's still getting 20Mbps
The 5505 is rated up to a maximum of 150Mbps under ideal conditions. Realized throughput can/will be much less depending on the traffic in and out of your networks. VPN throughput is considerably less. I would expect you could realistically expect the 50-75Mbps for IMIX.
What type of internet service do you have and from whom? You are paying for 200Mbps+?
harbor235 ;}
What type of internet service do you have and from whom? You are paying for 200Mbps+?
harbor235 ;}
ASKER
There is no VPN set up on there as of right now. They only have about 20 PC's connected to it.
Not sure on the type as I haven't been there and this is a pretty new acquisition for us. I believe it's Brighthouse and yes the service being paid for is 200Mbps.
They had a tech come in and test it with the firewall out of the picture and they were getting 170+ but as soon as the firewall was back in the picture it dropped back down to 20.
Not sure on the type as I haven't been there and this is a pretty new acquisition for us. I believe it's Brighthouse and yes the service being paid for is 200Mbps.
They had a tech come in and test it with the firewall out of the picture and they were getting 170+ but as soon as the firewall was back in the picture it dropped back down to 20.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I would also ask how performance was tested, The 5505 cannot sustain a maximum of 5k connections per second. realistically it is much less. Also, firewalls in general do not handle small packets well either. So it is important to know how the test was performed.
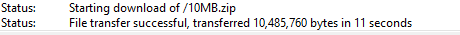
A good test for you to perform is a FTP from inside your network to outside your network.
FTP provides a summary of the application throughput when completed, can you provide that information?
harbor235 ;}
A good test for you to perform is a FTP from inside your network to outside your network.
FTP provides a summary of the application throughput when completed, can you provide that information?
harbor235 ;}
ASKER
Any certain FTP application I should use to be able to see the summary?
No, typically I believe all of them provide the summary information on completion.
e.g. X bytes transferred in X seconds, from that we can get application throughput and then approximate reasonable network performance.
harbor235 ;}
e.g. X bytes transferred in X seconds, from that we can get application throughput and then approximate reasonable network performance.
harbor235 ;}
ASKER
So that is ~4-5Mbps for that single ftp flow , not sure if anything else is going through that firewall at the time? and what the interface stats look like?
show interface <enter external interface here> when doing the xfer, looking for the rate or bps fields
harbor235 ;}
show interface <enter external interface here> when doing the xfer, looking for the rate or bps fields
harbor235 ;}
ASKER
Not much traffic, I would need to see how your network is put together, hard to tell from what we have here.
harbor235 ;}
harbor235 ;}
is youre connection symetric. if not put youre interface on half duplex, this wil fix youre issue
ASKER
We got a switch and put it between the ISP and the Firewall and the speed went up to about 94bps so that worked!
Thanks everyone for your responses.
Thanks everyone for your responses.
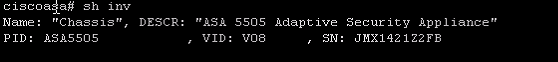
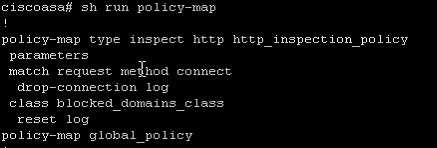
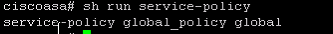
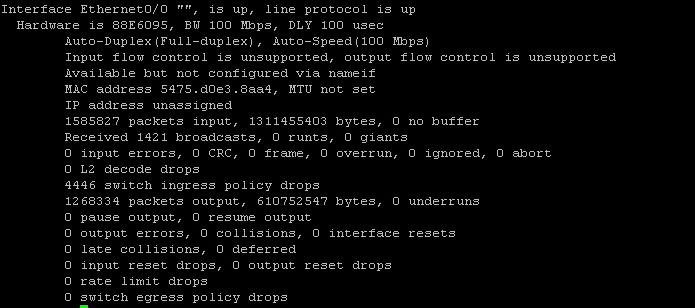

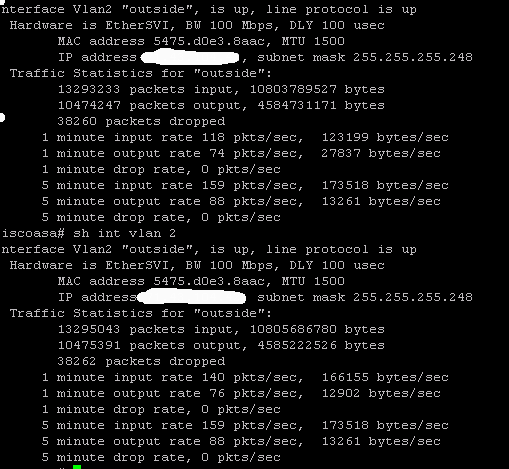
"show eth0/1" you will see Auto-duplex, auto-speed(100Mbps).
"show run policy-map" Do you see ?
police output 2000000
police input 2000000
"show run policy-map" and confirm that you do not have any police or shape commands (double check the global policy) do a "show run service-policy" a confirm that you do not have any service policies applied to any interfaces.
Reference bandwidth limit article.
http://matthewcmcmillan.blogspot.com/2013/03/bandwidth-limits-for-guest-wifi-on-asa.html