nflynn85
asked on
Installing new SSL/HTTPS certificates on Win Server 2008 R2/IIS
Is there anything additional I need to do besides just importing the certs into certmgr.msc? I've imported all the new certs in to the certmgr.msc but my website still sees the old certs when I view the cert through web browser (I haven't removed them yet, do I need to remove the old certs?). First time having to go through this process so help would be appreciated.
Have you updated the certificates in IIS
ASKER
I don't know what i'm doing here, so i'm going to need to have someone walk me through the whole process. I have three separate .crt files that I uploaded in to certmgr.msc
two from the CA, one for the site
how do I import the .crt in to IIS?
two from the CA, one for the site
how do I import the .crt in to IIS?
I'm working on something for you hold on another minute
ASKER
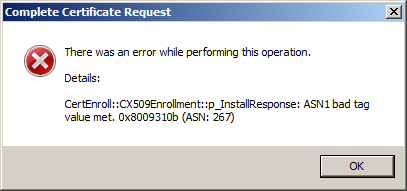
Okay. I've gotten this far. I found where I need to import the certificate in to IIS, but I keep getting this error that I don't know how to fix/resolve (assuming i'm doing this right.)
I go to server certificates at the server level, click complete certificate request, select the cert for my site, and get this error:
There was an error while performing this operation.
Details:
CertEnroll::CX509Enrollmen
I go to server certificates at the server level, click complete certificate request, select the cert for my site, and get this error:
There was an error while performing this operation.
Details:
CertEnroll::CX509Enrollmen
Create the Certificate Signing Request:
Click on the Start menu, go to Administrative Tools, and click on Internet Information Services (IIS) Manager.
Click on the name of the server in the Connections column on the left. Double-click on Server Certificates.
In the Actions column on the right, click on Create Certificate Request...
Enter all of the following information about your company and the domain you are securing and then click Next.
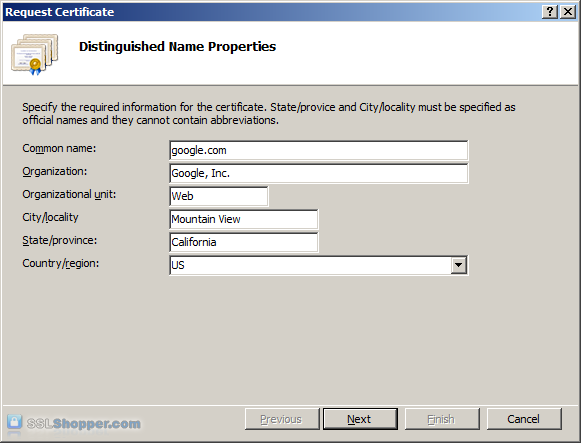
Leave the default Cryptographic Service Provider. Increase the Bit length to 2048 bit or higher. Click Next.
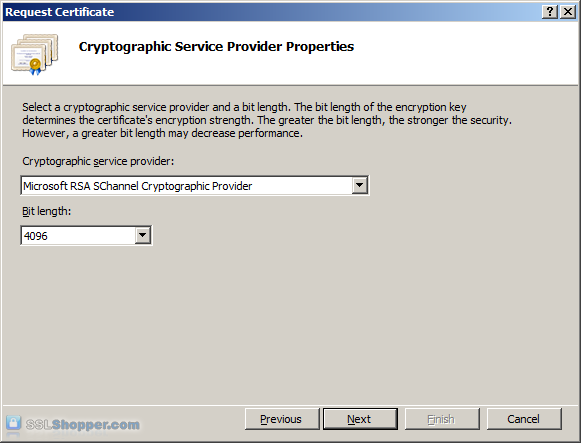
Click the button with the three dots and enter a location and filename where you want to save the CSR file. Click Finish.
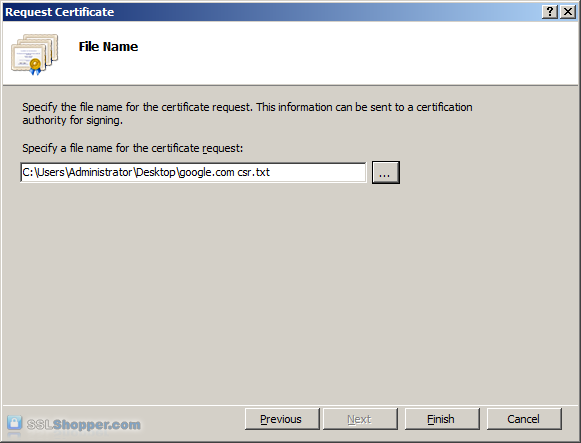
Once you have generated a CSR you can use it to order the certificate from a certificate authority. If you don't already have a favorite, you can compare SSL features from each provider using our SSL Wizard or by comparing cheap SSL certificates, Wildcard Certificates, or EV certificates. Once you paste the contents of the CSR and complete the ordering process, your order is validated, and you will receive the SSL certificate file.
----
Install the Certificate:
**To install your newly acquired SSL certificate in IIS 7, first copy the file somewhere on the server and then follow these instructions:
Click on the Start menu, go to Administrative Tools, and click on Internet Information Services (IIS) Manager.
Click on the name of the server in the Connections column on the left. Double-click on Server Certificates.
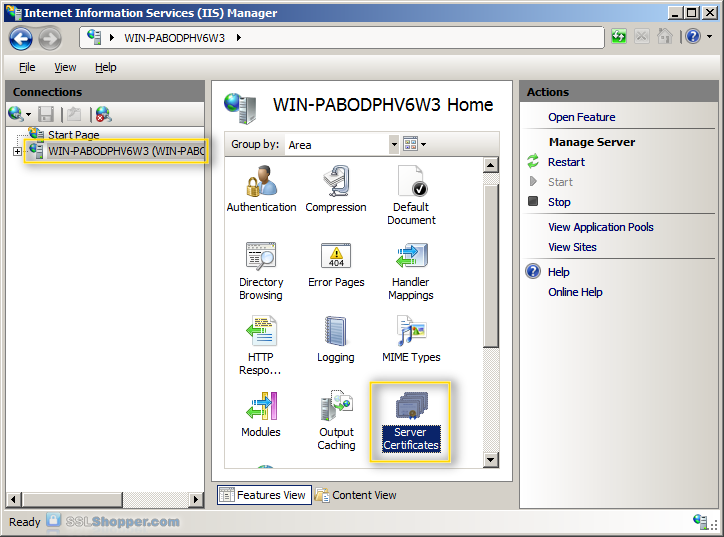
In the Actions column on the right, click on Complete Certificate Request...
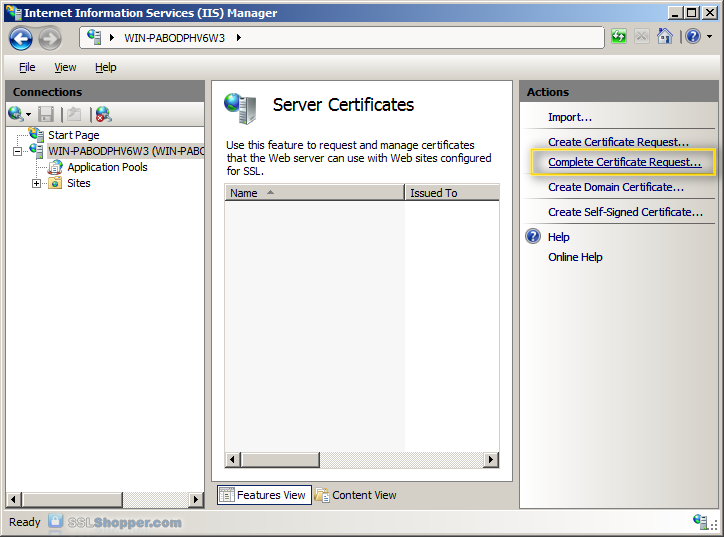
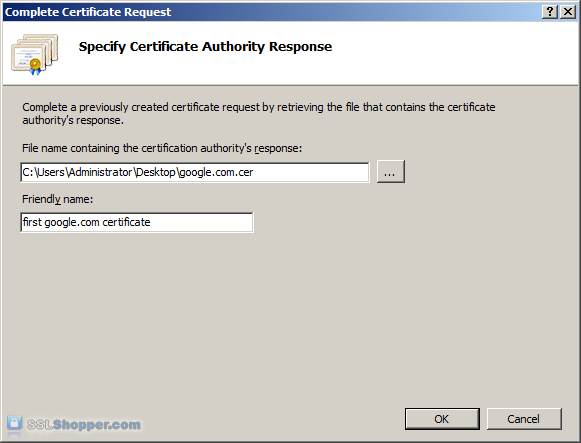
Click the button with the three dots and select the server certificate that you received from the certificate authority. If the certificate doesn't have a .cer file extension, select to view all types. Enter any friendly name you want so you can keep track of the certificate on this server. Click OK.
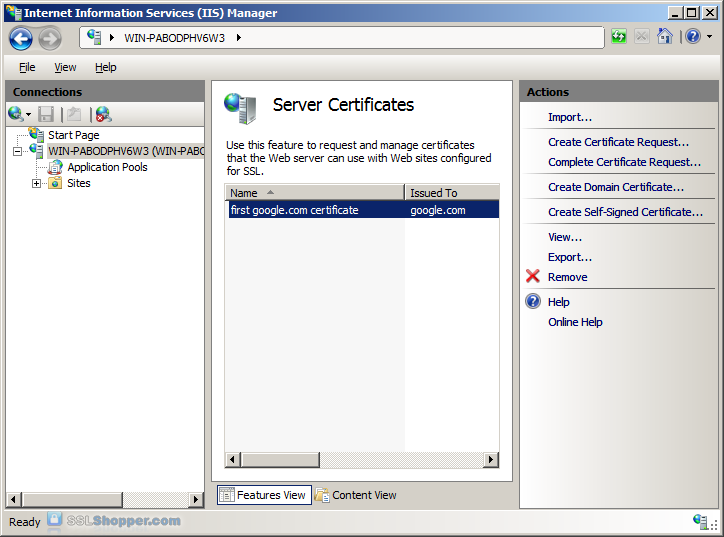
If successful, you will see your newly installed certificate in the list. If you receive an error stating that the request or private key cannot be found, make sure you are using the correct certificate and that you are installing it to the same server that you generated the CSR on. If you are sure of those two things, you may just need to create a new Certificate Request and reissue/replace the certificate. Contact your certificate authority if you have problems with this.
------
Bind the Certificate to a website:
In the Connections column on the left, expand the sites folder and click on the website that you want to bind the certificate to. Click on Bindings... in the right column.
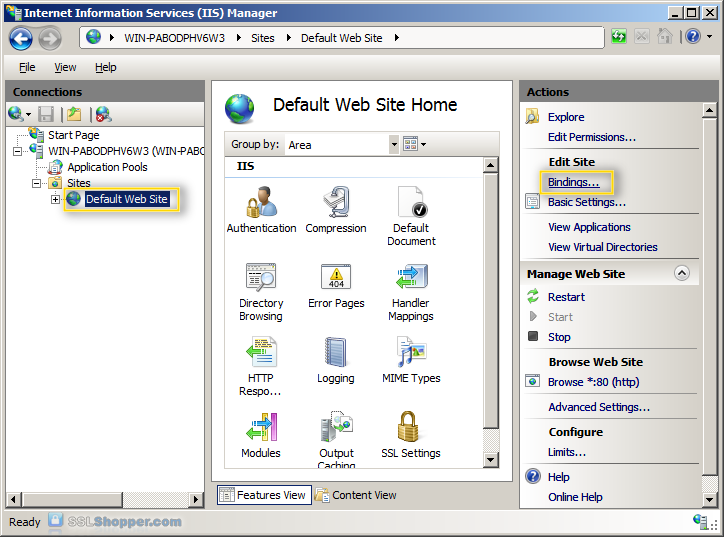
Click on the Add... button.
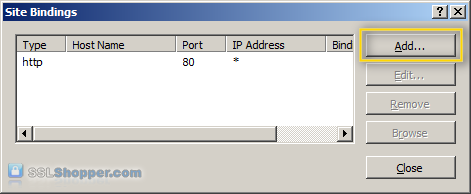
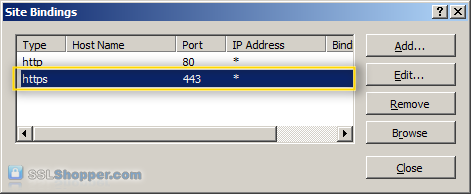
Change the Type to https and then select the SSL certificate that you just installed. Click OK.

You will now see the binding for port 443 listed. Click Close.
-------
Install any Intermediate Certificates:
Most SSL providers issue server certificates off of an Intermediate certificate so you will need to install this Intermediate certificate to the server as well or your visitors will receive a Certificate Not Trusted Error. You can install each Intermediate certificate (sometimes there is more than one) using these instructions:
Download the intermediate certificate to a folder on the server.
Double click the certificate to open the certificate details.
At the bottom of the General tab, click the Install Certificate button to start the certificate import wizard. Click Next.
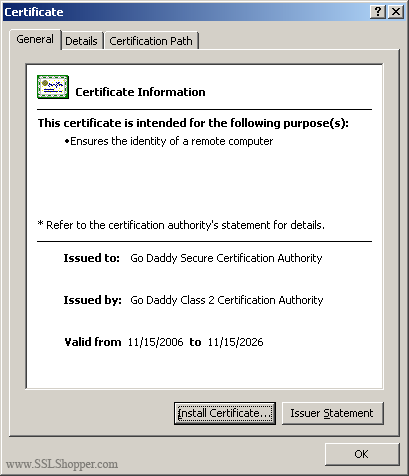
Select Place all certificates in the following store and click Browse.
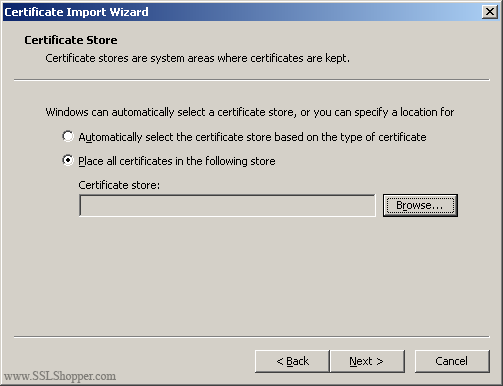
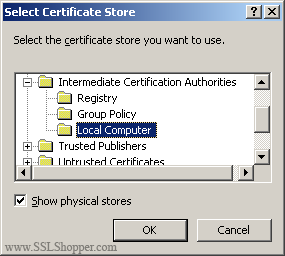
Check the Show physical stores checkbox, then expand the Intermediate Certification Authorities folder, select the Local Computer folder beneath it. Click OK. Click Next, then Finish to finish installing the intermediate certificate.
You may need to restart IIS so that it starts giving out the new certificate. You can verify that the certificate is installed correctly by visiting the site in your web browser using https instead of http or using this SSL Checker.
Click on the Start menu, go to Administrative Tools, and click on Internet Information Services (IIS) Manager.

Click on the name of the server in the Connections column on the left. Double-click on Server Certificates.

In the Actions column on the right, click on Create Certificate Request...

Enter all of the following information about your company and the domain you are securing and then click Next.


Leave the default Cryptographic Service Provider. Increase the Bit length to 2048 bit or higher. Click Next.

Click the button with the three dots and enter a location and filename where you want to save the CSR file. Click Finish.

Once you have generated a CSR you can use it to order the certificate from a certificate authority. If you don't already have a favorite, you can compare SSL features from each provider using our SSL Wizard or by comparing cheap SSL certificates, Wildcard Certificates, or EV certificates. Once you paste the contents of the CSR and complete the ordering process, your order is validated, and you will receive the SSL certificate file.
----
Install the Certificate:
**To install your newly acquired SSL certificate in IIS 7, first copy the file somewhere on the server and then follow these instructions:
Click on the Start menu, go to Administrative Tools, and click on Internet Information Services (IIS) Manager.
Click on the name of the server in the Connections column on the left. Double-click on Server Certificates.

In the Actions column on the right, click on Complete Certificate Request...

Click the button with the three dots and select the server certificate that you received from the certificate authority. If the certificate doesn't have a .cer file extension, select to view all types. Enter any friendly name you want so you can keep track of the certificate on this server. Click OK.

If successful, you will see your newly installed certificate in the list. If you receive an error stating that the request or private key cannot be found, make sure you are using the correct certificate and that you are installing it to the same server that you generated the CSR on. If you are sure of those two things, you may just need to create a new Certificate Request and reissue/replace the certificate. Contact your certificate authority if you have problems with this.

------
Bind the Certificate to a website:
In the Connections column on the left, expand the sites folder and click on the website that you want to bind the certificate to. Click on Bindings... in the right column.

Click on the Add... button.

Change the Type to https and then select the SSL certificate that you just installed. Click OK.

You will now see the binding for port 443 listed. Click Close.

-------
Install any Intermediate Certificates:
Most SSL providers issue server certificates off of an Intermediate certificate so you will need to install this Intermediate certificate to the server as well or your visitors will receive a Certificate Not Trusted Error. You can install each Intermediate certificate (sometimes there is more than one) using these instructions:
Download the intermediate certificate to a folder on the server.
Double click the certificate to open the certificate details.
At the bottom of the General tab, click the Install Certificate button to start the certificate import wizard. Click Next.

Select Place all certificates in the following store and click Browse.

Check the Show physical stores checkbox, then expand the Intermediate Certification Authorities folder, select the Local Computer folder beneath it. Click OK. Click Next, then Finish to finish installing the intermediate certificate.

You may need to restart IIS so that it starts giving out the new certificate. You can verify that the certificate is installed correctly by visiting the site in your web browser using https instead of http or using this SSL Checker.
Okay...
So I saw you checked Win Svr 8, so this is for IIS 7.0, IIS 8 is similar to this but may have some slight differences.
Try and work through all of this and let me know where you stand.
So I saw you checked Win Svr 8, so this is for IIS 7.0, IIS 8 is similar to this but may have some slight differences.
Try and work through all of this and let me know where you stand.
ASKER
So I already had a CSR generated by the place we host our server at which is why I have two certs from a CA and the 3rd cert for the website.
I go to server certificates at the server level, click complete certificate request, select the cert for my site, and get this error:
There was an error while performing this operation.
Details:
CertEnroll::CX509Enrollmen
I go to server certificates at the server level, click complete certificate request, select the cert for my site, and get this error:
There was an error while performing this operation.
Details:
CertEnroll::CX509Enrollmen
Solution 1:
According to Verisign support, their recommendation seems to be to replace the certificate with a new one. This method has worked for at least one of my customers in this place with a GoDaddy certificate. All they had to do was make a new certificate request (CSR text file), log into the the Godaddy web interface and re-key (we chose re-key rather than re-issue) their certificate. The new file processed fine.
-------
Solution 2:
Begin by importing the .crt file into the Personal certificate store for the local computer. (Start button > Run: MMC > File Menu > Add/Remove Snap-in > highlight Certificates snap-in and click the ADD button > select Computer Account and click Finish > Click OK > drill into Personal > Certificates > right-click and select All Tasks > select Import > guide to the .crt file.) At this point your certificate is basically a half-certificate. It is still missing its private key.
Second, double-click the crt certificate file you just imported, select the Details tab, scroll all the way down to Thumbprint and highlight Thumbprint. In the lower pane, block and copy all the letters of the thumbprint. Paste the thumbprint characters into notepad. Open the command prompt and run this command: Certutil /?
The command you’ll want to run is:
When you see the response: “CertUtil: -repairstore command completed successfully” you should have a private key associated with the .crt file in the personal store. There should no longer be any need to run through the “Complete Certificate Request…” wizard. The certificate should show up in the IIS Manager’s list of server certificates at this point. It should also be available in the SSL Certificates drop-down list when attempting to edit the https binding for a website.
According to Verisign support, their recommendation seems to be to replace the certificate with a new one. This method has worked for at least one of my customers in this place with a GoDaddy certificate. All they had to do was make a new certificate request (CSR text file), log into the the Godaddy web interface and re-key (we chose re-key rather than re-issue) their certificate. The new file processed fine.
-------
Solution 2:
Begin by importing the .crt file into the Personal certificate store for the local computer. (Start button > Run: MMC > File Menu > Add/Remove Snap-in > highlight Certificates snap-in and click the ADD button > select Computer Account and click Finish > Click OK > drill into Personal > Certificates > right-click and select All Tasks > select Import > guide to the .crt file.) At this point your certificate is basically a half-certificate. It is still missing its private key.
Second, double-click the crt certificate file you just imported, select the Details tab, scroll all the way down to Thumbprint and highlight Thumbprint. In the lower pane, block and copy all the letters of the thumbprint. Paste the thumbprint characters into notepad. Open the command prompt and run this command: Certutil /?
The command you’ll want to run is:
certutil -repairstore my “{insert all of the thumbprint characters here}”[When you see the response: “CertUtil: -repairstore command completed successfully” you should have a private key associated with the .crt file in the personal store. There should no longer be any need to run through the “Complete Certificate Request…” wizard. The certificate should show up in the IIS Manager’s list of server certificates at this point. It should also be available in the SSL Certificates drop-down list when attempting to edit the https binding for a website.
ASKER
been there done that already, didn't work
ASKER
Solution 2 anyways, I guess i'll have to reach back out to the CA and go for solution 1
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
As I mentioned previously, the above did not work.
I will have to reach out to my vendor and have them re-key their CSR
I will have to reach out to my vendor and have them re-key their CSR
I know how frustrating these SSL certificates can be man.
I just went through a big ordeal with our SSL certificates expiring b/c the owner of the company wouldn't give me access to our GoDaddy acct, so I couldn't renew when I saw a month left of validity.
Also, the emails from GoDaddy went to his email acct and he "forgot to bring it up" when he saw the first email and he was on vacation for two weeks when they expired.
We lost our Lync Auto-Attendant & Exchange...
I just went through a big ordeal with our SSL certificates expiring b/c the owner of the company wouldn't give me access to our GoDaddy acct, so I couldn't renew when I saw a month left of validity.
Also, the emails from GoDaddy went to his email acct and he "forgot to bring it up" when he saw the first email and he was on vacation for two weeks when they expired.
We lost our Lync Auto-Attendant & Exchange...
ASKER
yeah it's definitely a PITA - this is my first time having to deal with this (I didn't even know the certs were expiring). Luckily, my internal IT team saw it was about to expire and notified me so we could start the renewal.
I re-opened my ticket with my vendor that hosts the server to re-issue the CSR and let them know about the issue we're having.
From there, I have to hand the CSR back off to my internal IT group and then they take that over to our CA
This issue seems well documented so I'm hoping it's something we can resolve quickly
I re-opened my ticket with my vendor that hosts the server to re-issue the CSR and let them know about the issue we're having.
From there, I have to hand the CSR back off to my internal IT group and then they take that over to our CA
This issue seems well documented so I'm hoping it's something we can resolve quickly
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Sorry for the delayed response. I've been out of the state.
I'm glad to hear you were also able to upgrade your OS. Nice.
Are you still having the network issue? If so, what's go on?
I'm glad to hear you were also able to upgrade your OS. Nice.
Are you still having the network issue? If so, what's go on?
ASKER
It was just a ID 10 T error - typed the gateway incorrectly so luckily no big deal
Got the certs from my CA and they took to the server. Updated the bindings and good to go! Thanks for your help. Great thread and a lot of good info in here
Got the certs from my CA and they took to the server. Updated the bindings and good to go! Thanks for your help. Great thread and a lot of good info in here
ASKER
Older server version was the problem, nothing was wrong with the certs