Publishing a service through ISA 2006
Hi all,
We configured an Alarm system (module IP) connected to the intranet network protected by a ISA server 2006.
The idea is to create a rule inside the ISA server to permit a connection from outside and activate/deactivate the Alarm system remotely. They (Alarm company) explain me that the system uses the port 2200 (TCP & UDP).
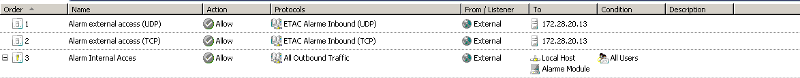
I configured then two non-web server protocol publishing rules as below:
- server rule name: Alarm external access (TCP)
- server IP to publish (module IP : 172.28.20.13)
- selected protocole: port 2200 TCP Inbound
- listener IP addresses: External
- server rule name: Alarm external access (UDP)
- server IP to publish (module IP : 172.28.20.13)
- selected protocole: port 2200 UDP Inbound
- listener IP addresses: External
When I applied these rules, the result is that my connection arrives to the ISA server on the external interface (initiated connection) and directly closed (closed connection). But impossible to reach the system module...
Do you have any suggestions or idea?
Thanks Guys!
Javier
We configured an Alarm system (module IP) connected to the intranet network protected by a ISA server 2006.
The idea is to create a rule inside the ISA server to permit a connection from outside and activate/deactivate the Alarm system remotely. They (Alarm company) explain me that the system uses the port 2200 (TCP & UDP).
I configured then two non-web server protocol publishing rules as below:
- server rule name: Alarm external access (TCP)
- server IP to publish (module IP : 172.28.20.13)
- selected protocole: port 2200 TCP Inbound
- listener IP addresses: External
- server rule name: Alarm external access (UDP)
- server IP to publish (module IP : 172.28.20.13)
- selected protocole: port 2200 UDP Inbound
- listener IP addresses: External
When I applied these rules, the result is that my connection arrives to the ISA server on the external interface (initiated connection) and directly closed (closed connection). But impossible to reach the system module...
Do you have any suggestions or idea?
Thanks Guys!
Javier
carefully check if any other DENY rules override these two rules in higher priority?
ASKER
Hi,
Just verify but these rules have high priorities...
Javier
Just verify but these rules have high priorities...
Javier
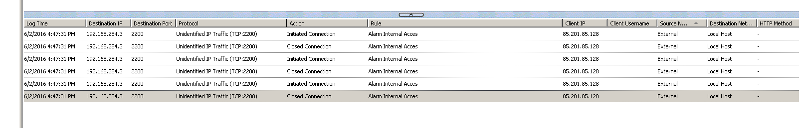
can you please post the log line that shows the connection closed and the firewall rules of ISA2K6? screenshots preferred.
thanks for posting the screenshots.
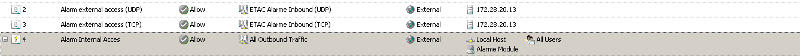
can you kindly let me know the column names of the rules listed in the 2nd screenshot? I don't have a ISA2K6 in the lab and haven't touched it for years. :)
can you kindly let me know the column names of the rules listed in the 2nd screenshot? I don't have a ISA2K6 in the lab and haven't touched it for years. :)
thanks for positing the screenshot again.
what is the IP of 172.28.20.13? and 192.168.254.3? which one is the internal IP of Alarm Module? which one is the WAN IP of ISA2K6?
if 192.168.254.3 is the WAN IP of ISA2K6, how could the external IP 85.20.85.128 reach this private IP? is there an extra firewall in the middle?
the destination (To) IP for rule (1) and (2) should be an internal IP of the Alarm Module.
what is the IP of 172.28.20.13? and 192.168.254.3? which one is the internal IP of Alarm Module? which one is the WAN IP of ISA2K6?
if 192.168.254.3 is the WAN IP of ISA2K6, how could the external IP 85.20.85.128 reach this private IP? is there an extra firewall in the middle?
the destination (To) IP for rule (1) and (2) should be an internal IP of the Alarm Module.
ASKER
Ok, I'm going to explain you.
172.28.20.13 is the alarm module IP and 192.168.254.3 the WAN interface of the ISA2006.
The provider's router has the fixed IP 91.183.62.234 and I configured a port forwarding from this IP to the 192.168.254.3 (NAT config) and sure the port 2200.
85.20.85.128 is my public IP (home) from where I'm testing a telnet to the 91.183.62.234:2200
172.28.20.13 is the alarm module IP and 192.168.254.3 the WAN interface of the ISA2006.
The provider's router has the fixed IP 91.183.62.234 and I configured a port forwarding from this IP to the 192.168.254.3 (NAT config) and sure the port 2200.
85.20.85.128 is my public IP (home) from where I'm testing a telnet to the 91.183.62.234:2200
thanks for the clarification.
the 3rd rule is confusing me. its protocol suggests the rule is against OUTBOUND traffic but the direction is from EXTERNAL to INTERNAL. if you have restricted control against all outbound traffic, say by default no access for all unknown outgoing traffic, then your 3rd rule won't work as expected.
the 3rd rule is confusing me. its protocol suggests the rule is against OUTBOUND traffic but the direction is from EXTERNAL to INTERNAL. if you have restricted control against all outbound traffic, say by default no access for all unknown outgoing traffic, then your 3rd rule won't work as expected.
ASKER
Yes, I made these rule for testing purpose but without it I have directly a denied connection...
tried reversing the 3rd rule's direction and see any change?
the log already shows that the denied connections were controlled by the DEFAULT RULE, NOT the rules you defined for the alarms.
ASKER
How can I see which one is the default rule?
see the last log you posted, the "default rule" under "rule".
This question needs an answer!
Become an EE member today
7 DAY FREE TRIALMembers can start a 7-Day Free trial then enjoy unlimited access to the platform.
View membership options
or
Learn why we charge membership fees
We get it - no one likes a content blocker. Take one extra minute and find out why we block content.