Techrunner
asked on
Cisco ASA Remote IPSec VPN Connected but no traffic
Hello Experts
I have Cisco 5510 running software version 9.1 (6). Below is my network setup. This is a brand new asa and I've configured IPSec Remote Access VPN
10.1.76.0/24 ---- inside-----ASA------outsid
I'm able to establish the VPN connection using IPSec VPN Client but no traffic is passing through the tunnel and in ASA logs I don't any traffic hitting the ASA.
This is my VPN configuration
I would appreciate any help.
I have Cisco 5510 running software version 9.1 (6). Below is my network setup. This is a brand new asa and I've configured IPSec Remote Access VPN
10.1.76.0/24 ---- inside-----ASA------outsid
I'm able to establish the VPN connection using IPSec VPN Client but no traffic is passing through the tunnel and in ASA logs I don't any traffic hitting the ASA.
This is my VPN configuration
ip local pool REMOTE-VPN-POOL 192.168.200.100-192.168.20<wbr ></wbr>0.254 mask 255.255.255.0
access-list SPLIT-TUNNEL-ACL standard permit 10.1.76.0 255.255.255.0
object network SUBNET-10.1.76.0
subnet 10.1.76.0 255.255.255.0
object network SUBNET-REMOTE-VPN
subnet 192.168.200.0 255.255.255.0
group-policy ra-vpn internal
group-policy ra-vpn attributes
vpn-tunnel-protocol ikev1
split-tunnel-policy tunnelspecified
split-tunnel-network-list value SPLIT-TUNNEL-ACL
tunnel-group ra-vpn type remote-access
tunnel-group ra-vpn general-attributes
default-group-policy ra-vpn
address-pool REMOTE-VPN-POOL
tunnel-group ra-vpn ipsec-attributes
ikev1 pre-shared-key rakey12345
crypto ikev1 policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 enable outside
!
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs group2
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-3DES-SHA
crypto map outside_map 65535 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map outside_map interface outside
nat (inside,outside) 1 source static SUBNET-10.1.76.0 SUBNET-10.1.76.0 destination static SUBNET-REMOTE-VPN SUBNET-REMOTE-VPN no-proxy-arp route-lookup
crypto isakmp nat-traversal 21
username vpntest password cisco privilege 0
username vpntest attributes
vpn-group-policy ra-vpnI would appreciate any help.
Change your NAT statement from "nat (inside,outside)" to "nat (inside,any)".
ASKER
Hi Joseph,
Thanks for your help.
I changed the nat statement as you suggested but still no luck
Thanks for your help.
I changed the nat statement as you suggested but still no luck
Sorry... that was kind of a "drive by" answer... I was walking away from my desk. LOL.
Let me look at your config and give you a better response....
Let me look at your config and give you a better response....
What version OS?
ASKER
Version 9.1(6)
Hi there,
The configuration seems to be fine.
Kindly share the below output once the VPN is connected.
i)
#sh crypto isakmp sa output from the ASA.
ii)
C:> route print output from the client workstation
The configuration seems to be fine.
Kindly share the below output once the VPN is connected.
i)
#sh crypto isakmp sa output from the ASA.
ii)
C:> route print output from the client workstation
Hi Pete,
That is one excellent link that you have posted.
That is one excellent link that you have posted.
Hi Ian - Cheer's that's 10 years answering forum questions there :)
ASKER
Hi Ian
I will provide the output
Hi Pete
I'm fan of your articles
That was first link I used I configured as below but still not working
crypto isakmp nat-traversal 21
I will provide the output
Hi Pete
I'm fan of your articles
That was first link I used I configured as below but still not working
crypto isakmp nat-traversal 21
My money is still on a nat problem :)
When connected with a VPN client do sh cry ipsec sa and post here.
I don't see ACL to allow traffic from your vpn pool to internal network.
I don't see ACL to allow traffic from your vpn pool to internal network.
ASKER
There is already SPLIT TUNNELING ACL and NAT EXEMPTION.
Here is the output of crypto ipsec sa
I've changed the IP of outside interface on ASA. 192.168.16.4 255.255.255.252
Here is the lab setup
inside 10.1.76.x-----ASA--------o
Here is the output of crypto ipsec sa
I've changed the IP of outside interface on ASA. 192.168.16.4 255.255.255.252
Here is the lab setup
inside 10.1.76.x-----ASA--------o
ASA# sh crypto ipsec sa
interface: outside
Crypto map tag: SYSTEM_DEFAULT_CRYPTO_MAP, seq num: 65535, local addr: 192.168.16.4
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (192.168.200.100/255.255.255.255/0/0)
current_peer: 192.168.18.86, username: vpntest
dynamic allocated peer ip: 192.168.200.100
dynamic allocated peer ip(ipv6): 0.0.0.0
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#TFC rcvd: 0, #TFC sent: 0
#Valid ICMP Errors rcvd: 0, #Invalid ICMP Errors rcvd: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 192.168.16.4/0, remote crypto endpt.: 192.168.18.86/0
path mtu 1500, ipsec overhead 58(36), media mtu 1500
PMTU time remaining (sec): 0, DF policy: copy-df
ICMP error validation: disabled, TFC packets: disabled
current outbound spi: 1DCCFFF9
current inbound spi : A89F5CB0
inbound esp sas:
spi: 0xA89F5CB0 (2829016240)
transform: esp-3des esp-sha-hmac no compression
in use settings ={RA, Tunnel, IKEv1, }
slot: 0, conn_id: 57344, crypto-map: SYSTEM_DEFAULT_CRYPTO_MAP
sa timing: remaining key lifetime (sec): 28516
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001
outbound esp sas:
spi: 0x1DCCFFF9 (499974137)
transform: esp-3des esp-sha-hmac no compression
in use settings ={RA, Tunnel, IKEv1, }
slot: 0, conn_id: 57344, crypto-map: SYSTEM_DEFAULT_CRYPTO_MAP
sa timing: remaining key lifetime (sec): 28516
IV size: 8 bytes
replay detection support: Y
Anti replay bitmap:
0x00000000 0x00000001There is already SPLIT TUNNELING ACL and NAT EXEMPTION.
What about interface ACL? You are coming in on outside interface...
When you ping, does decaps count increase?
ASKER
When I ping from the VPN Client to Internal Host, encaps increase but when I do vice versa decaps doesn't increase
So if you get decaps it means traffic is getting to the firewall. Again, ACL on outside interface. Do you permit traffic from your VPN pool to internal network?
ASKER
But the traffic from VPN client is not getting to firewall. No traffic appears in logs.
At least the traffic should get to firewall!
At least the traffic should get to firewall!
ASKER
Another thing to be noted, I have configured the Anyconnect SSL VPN on the same box and its absolutely working fine no issue.
Thanks
Thanks
I ask for a simple thing but I get a ton of resistance from you every time. This would be my last time responding to your threads.
The implicit deny at the end of acl doesn't generate messages. If you want it to produce logs, you need to add deny statement manually. This could be the reason why you don't see anything but w/e.
The implicit deny at the end of acl doesn't generate messages. If you want it to produce logs, you need to add deny statement manually. This could be the reason why you don't see anything but w/e.
ASKER
So I'd create an ACL and on inbound outside interface with VPN subnet as source and destination internal network
Sorry for any confusion.
Sorry for any confusion.
ASKER
I created the ACL and applied on outside interface inbound
access-list outside_access_in line 1 extended permit ip object SUBNET-REMOTE-VPN object SUBNET-10.1.76.0
But still I don't see anything in the log and there is no hit on the ACL
access-list outside_access_in line 1 extended permit ip object SUBNET-REMOTE-VPN object SUBNET-10.1.76.0
But still I don't see anything in the log and there is no hit on the ACL
ASKER
Also i created implicit deny rule, but there is no message hitting the firewall from VPN client as a source.
Thanks
Thanks
Hi there,
Kindly delete the VPN config and reapply the same again.
Configuration wise it seems to be fine.
Have you verified the output that was asked in the previous post??
Kindly delete the VPN config and reapply the same again.
Configuration wise it seems to be fine.
Have you verified the output that was asked in the previous post??
ASKER
Hi Ian
I've already reconfigured the setup twice but no luck
This was the output I shared earlier
here is the route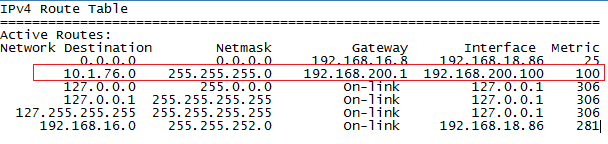 print
print
I've already reconfigured the setup twice but no luck
This was the output I shared earlier
here is the route
 print
print
Hi cciedreamer,
i guess your ASA is someway mixing up nat statements in wrong order.
The easiest way to overcome this problem is to create 2 brand new objects which will not overlap in nat statements, precisely local and remote subnets.
It has always worked fine for me so far.
Basically, do this:
object network obj-local
subnet 10.1.76.0 255.255.255.0
object network obj-remote
subnet 192.168.200.0 255.255.255.0
no nat (inside,outside) 1 source static SUBNET-10.1.76.0 SUBNET-10.1.76.0 destination static SUBNET-REMOTE-VPN SUBNET-REMOTE-VPN no-proxy-arp route-lookup
nat (inside,outside) source static obj-local obj-local destination static obj-remote obj-remote
I'm pretty sure it will work
hope this helps
max
i guess your ASA is someway mixing up nat statements in wrong order.
The easiest way to overcome this problem is to create 2 brand new objects which will not overlap in nat statements, precisely local and remote subnets.
It has always worked fine for me so far.
Basically, do this:
object network obj-local
subnet 10.1.76.0 255.255.255.0
object network obj-remote
subnet 192.168.200.0 255.255.255.0
no nat (inside,outside) 1 source static SUBNET-10.1.76.0 SUBNET-10.1.76.0 destination static SUBNET-REMOTE-VPN SUBNET-REMOTE-VPN no-proxy-arp route-lookup
nat (inside,outside) source static obj-local obj-local destination static obj-remote obj-remote
I'm pretty sure it will work
hope this helps
max
ASKER
Hi Max
Thanks for your help
I tried removing the nat statements and entered as mentioned above but no luck still the same issue.
Thanks for your help
I tried removing the nat statements and entered as mentioned above but no luck still the same issue.
this issue might happen as well if you have multiple ip addresses configured on the nic card of your PC, as the packets from firewall get back on wrong ip. Can you please check ?
max
max
ASKER
Hi Max
I agree but the anyconnect SSL VPN connection is working fineon the same machine
I can ping to internal IP after the establishing VPN
I agree but the anyconnect SSL VPN connection is working fineon the same machine
I can ping to internal IP after the establishing VPN
It might be a peculiar problem of ipsec client. Do you have multiple IPs onto your nic card?
max
max
ASKER
No Max, no multiple IPs
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Hi There,
Sorry for the delayed response.
The route print output indicates that you are connected to the VPN and to reach the corporate network, it prefers the VPN interface IP.
Have you tried the reachability to other servers in LAN?
Do share the access-list configured for the same.
Sorry for the delayed response.
The route print output indicates that you are connected to the VPN and to reach the corporate network, it prefers the VPN interface IP.
Have you tried the reachability to other servers in LAN?
Do share the access-list configured for the same.
ASKER
Excellent Max
I used Shrew VPN Client and now I can ping the my internal hosts from the VPN client machine
So what could be the issue ? What makes the difference between Legacy Cisco VPN Client and Shrew ?
Appreciating your help.
I used Shrew VPN Client and now I can ping the my internal hosts from the VPN client machine
So what could be the issue ? What makes the difference between Legacy Cisco VPN Client and Shrew ?
Appreciating your help.
Great...That's really strange.....probably an issue with the client out here....
hi cciedreamer,
what i figured out in the past is that the problem lies into the nic of the PC's operating system, which sometimes keeps wrong parameters when changing network and ip address routes. The virtual nic created by a vpn client resides onto the tcp ip stack of the physical nic and ... shit happens.
glad you solved your issue
cheers
max
what i figured out in the past is that the problem lies into the nic of the PC's operating system, which sometimes keeps wrong parameters when changing network and ip address routes. The virtual nic created by a vpn client resides onto the tcp ip stack of the physical nic and ... shit happens.
glad you solved your issue
cheers
max
Tx Max for the KT.
ASKER
This is the guide here for how to configure shrew client for Cisco ASA VPN Server,
Might be helpful for others
Might be helpful for others
ASKER
Thank You everyone for extending support