Danny Verrazano
asked on
Powershell script to remove Active Directory groups
Back story of this request/Question can be found here:
https://www.experts-exchange.com/questions/28954302/Powershell-script-to-add-AD-groups-to-server-local-groups.html
What I need now is a separate script that will go back and remove specific Active Directory domain groups (by domain NetBIOS shortname and SID) from the server local groups. It would be helpful if the script can run against a list of servers.
So, for example:
$DomainName =
$DomainSID =
$ServerList =
The script should look at the local groups of the servers in $serverlist and find any groups with either $DomainName\groupname or $DomainSID\groupname (for example; find any groups belonging to the AD Domain Contoso OR the SID for Contoso (Contoso\AnyGroupsFound)) and remove only those groups leaving all others in place.
Would like to log any errors encountered in addition to noting the groups that were found and removed.
Thank you in advance!
Dan
https://www.experts-exchange.com/questions/28954302/Powershell-script-to-add-AD-groups-to-server-local-groups.html
What I need now is a separate script that will go back and remove specific Active Directory domain groups (by domain NetBIOS shortname and SID) from the server local groups. It would be helpful if the script can run against a list of servers.
So, for example:
$DomainName =
$DomainSID =
$ServerList =
The script should look at the local groups of the servers in $serverlist and find any groups with either $DomainName\groupname or $DomainSID\groupname (for example; find any groups belonging to the AD Domain Contoso OR the SID for Contoso (Contoso\AnyGroupsFound)) and remove only those groups leaving all others in place.
Would like to log any errors encountered in addition to noting the groups that were found and removed.
Thank you in advance!
Dan
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Can this be made to read a list of target computers from a file?
As I said: The script accepts an array of server names to process, either using the -ComputerName argument, or by pipeline.
So you can either use
.\Whatever.ps1 -ComputerName (Get-Content C:\Temp\servers.txt)
or
Get-Content C:\Temp\servers.txt | .\Whatever.ps1
So you can either use
.\Whatever.ps1 -ComputerName (Get-Content C:\Temp\servers.txt)
or
Get-Content C:\Temp\servers.txt | .\Whatever.ps1
ASKER
I apologize. you definitely did say that.
I am testing various scenarios today. Will update this question later with results.
I am testing various scenarios today. Will update this question later with results.
ASKER
Ok so I am seeing partial success. In some cases the script is skipping users/groups I THINK because of how the user and/or group is displayed.
This is a domain cleanup after a migration using ADMT. So, depending on whether the trust between domains still exists or is broken, there are some cases where the users and/or groups nested in a server's local groups will display as:
OldDomain\UserName
OldDomain\GroupName
OldDomain\SIDofUserOrGroup
SIDofOldDomain\UserName
SIDofOldDomain\GroupName
NewDomain\SIDofGroupFromOl
NewDomain\SIDofUserFromOld
I think in those cases everything is working ok.
However, there are some situations when the users and/or groups nested in the local server groups (for example; Administrators) will display such as this:
NewDomain\UserName (SIDofUserFromOldDomain)
NewDomain\GroupName (SIDofGroupFromOldDomain)
In those cases the script is not recognizing the SID being from the OldDomain and it is skipping those.
Here is a copy of the log file:
ComputerName Group Member Action Details
hrsvr Access Control Assistance Operators None Group empty
hrsvr Administrators WinNT://NewDomain/HRSVR/Ad
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://NewDomain/Domain Admins Skipped No match
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://NewDomain/User03 Skipped No match
hrsvr Administrators WinNT://NewDomain/User02 Skipped No match
hrsvr Administrators WinNT://NewDomain/User01 Skipped No match
hrsvr Administrators WinNT://NewDomain/G_Financ
hrsvr Administrators WinNT://NewDomain/G_Financ
hrsvr Administrators WinNT://NewDomain/D_finsvr
hrsvr Backup Operators None Group empty
hrsvr Certificate Service DCOM Access None Group empty
hrsvr Cryptographic Operators None Group empty
hrsvr Distributed COM Users None Group empty
hrsvr Event Log Readers None Group empty
hrsvr Guests WinNT://NewDomain/HRSVR/Gu
hrsvr Hyper-V Administrators None Group empty
hrsvr IIS_IUSRS WinNT://NT AUTHORITY/IUSR Skipped No match
hrsvr Network Configuration Operators None Group empty
hrsvr Performance Log Users None Group empty
hrsvr Performance Monitor Users None Group empty
hrsvr Power Users None Group empty
hrsvr Print Operators None Group empty
hrsvr RDS Endpoint Servers None Group empty
hrsvr RDS Management Servers None Group empty
hrsvr RDS Remote Access Servers None Group empty
hrsvr Remote Desktop Users None Group empty
hrsvr Remote Management Users None Group empty
hrsvr Replicator None Group empty
hrsvr Users WinNT://NT AUTHORITY/INTERACTIVE Skipped No match
hrsvr Users WinNT://NT AUTHORITY/Authenticated Users Skipped No match
hrsvr Users WinNT://NewDomain/Domain Users Skipped No match
hrsvr WinRMRemoteWMIUsers__ None Group empty
In the case of the items I made bold, they are listed in the server's local Administrators group as:
NewDomain/G_FinanceUsers (S-1-5-21-111111111-222222
NewDomain/G_FinanceAdmins (S-1-5-21-111111111-222222
NewDomain/D_finsvr_data_F (S-1-5-21-111111111-222222
So, the script is not looking at the SID in those cases and skipping them.
I hope I have explained this well enough. If not, ask me for whatever info you need.
Thanks very much!
This is a domain cleanup after a migration using ADMT. So, depending on whether the trust between domains still exists or is broken, there are some cases where the users and/or groups nested in a server's local groups will display as:
OldDomain\UserName
OldDomain\GroupName
OldDomain\SIDofUserOrGroup
SIDofOldDomain\UserName
SIDofOldDomain\GroupName
NewDomain\SIDofGroupFromOl
NewDomain\SIDofUserFromOld
I think in those cases everything is working ok.
However, there are some situations when the users and/or groups nested in the local server groups (for example; Administrators) will display such as this:
NewDomain\UserName (SIDofUserFromOldDomain)
NewDomain\GroupName (SIDofGroupFromOldDomain)
In those cases the script is not recognizing the SID being from the OldDomain and it is skipping those.
Here is a copy of the log file:
ComputerName Group Member Action Details
hrsvr Access Control Assistance Operators None Group empty
hrsvr Administrators WinNT://NewDomain/HRSVR/Ad
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://NewDomain/Domain Admins Skipped No match
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://S-1-5-21-111111111
hrsvr Administrators WinNT://NewDomain/User03 Skipped No match
hrsvr Administrators WinNT://NewDomain/User02 Skipped No match
hrsvr Administrators WinNT://NewDomain/User01 Skipped No match
hrsvr Administrators WinNT://NewDomain/G_Financ
hrsvr Administrators WinNT://NewDomain/G_Financ
hrsvr Administrators WinNT://NewDomain/D_finsvr
hrsvr Backup Operators None Group empty
hrsvr Certificate Service DCOM Access None Group empty
hrsvr Cryptographic Operators None Group empty
hrsvr Distributed COM Users None Group empty
hrsvr Event Log Readers None Group empty
hrsvr Guests WinNT://NewDomain/HRSVR/Gu
hrsvr Hyper-V Administrators None Group empty
hrsvr IIS_IUSRS WinNT://NT AUTHORITY/IUSR Skipped No match
hrsvr Network Configuration Operators None Group empty
hrsvr Performance Log Users None Group empty
hrsvr Performance Monitor Users None Group empty
hrsvr Power Users None Group empty
hrsvr Print Operators None Group empty
hrsvr RDS Endpoint Servers None Group empty
hrsvr RDS Management Servers None Group empty
hrsvr RDS Remote Access Servers None Group empty
hrsvr Remote Desktop Users None Group empty
hrsvr Remote Management Users None Group empty
hrsvr Replicator None Group empty
hrsvr Users WinNT://NT AUTHORITY/INTERACTIVE Skipped No match
hrsvr Users WinNT://NT AUTHORITY/Authenticated Users Skipped No match
hrsvr Users WinNT://NewDomain/Domain Users Skipped No match
hrsvr WinRMRemoteWMIUsers__ None Group empty
In the case of the items I made bold, they are listed in the server's local Administrators group as:
NewDomain/G_FinanceUsers (S-1-5-21-111111111-222222
NewDomain/G_FinanceAdmins (S-1-5-21-111111111-222222
NewDomain/D_finsvr_data_F (S-1-5-21-111111111-222222
So, the script is not looking at the SID in those cases and skipping them.
I hope I have explained this well enough. If not, ask me for whatever info you need.
Thanks very much!
If Windows identifies them as being from the new domain, then, in all likelihood, these groups are from the new domain.
So why do you want to have these groups removed?
As per your request, the script only removes members that either
1. Can still be resolved as being members form the old domain
2. Can not be resolved anymore (because they were deleted or the trust was broken) and start with the domain SID you specified.
Are you working with SidHistory?
So why do you want to have these groups removed?
As per your request, the script only removes members that either
1. Can still be resolved as being members form the old domain
2. Can not be resolved anymore (because they were deleted or the trust was broken) and start with the domain SID you specified.
Are you working with SidHistory?
ASKER
Let me have a closer look at whats going on. I will get back to you again shortly. Thank you!
ASKER
Ok so here is what I have found to be going on:
Names are changed to protect the innocent. They are used as examples only.
Server1 exists in OldDomain
Server1 has local group called Administrators (of course)
OldDomain\GlobalGroup1 is nested as member of Server1\Administrators
OldDomain\DomainLocalGroup
OldDomain\User1 is nested as a member of Server1\Administrators
OldDomain GlobalGroup1 and DomainLocalGroup1 are migrated to NewDomain using ADMT with SID History
OldDomain User1 is migrated to NewDomain using ADMT with SID History
Server1 is migrated to NewDomain using ADMT (security translation first then computer migration)
Trust is removed
SID filtering re-enabled
Post migration, Server1 has the following members in Local Administrators
NewDomain\GlobalGroup1
NewDomain\GlobalGroup1(s-1
NewDomain\DomainLocalGroup
NewDomain\DomainLocalGroup
NewDomain\User1
NewDomain\User1(s-1-5-21-S
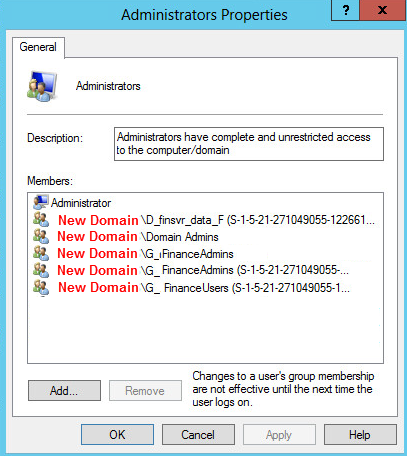
I am attaching a screenshot of the server's local administrators group. The SIDs shown are those of the OldDomain.
Basically I think the script is not expecting the OldDomain SID in parentheses of the user or group accounts.
I will build out another test environment to validate all of this step by step again. I am not sure why the members of the local administrators group which originally showed as OldDomain\GroupName would now be listed the way they are with a SID in parenths. I've never seen that before.
Any thoughts?
Names are changed to protect the innocent. They are used as examples only.
Server1 exists in OldDomain
Server1 has local group called Administrators (of course)
OldDomain\GlobalGroup1 is nested as member of Server1\Administrators
OldDomain\DomainLocalGroup
OldDomain\User1 is nested as a member of Server1\Administrators
OldDomain GlobalGroup1 and DomainLocalGroup1 are migrated to NewDomain using ADMT with SID History
OldDomain User1 is migrated to NewDomain using ADMT with SID History
Server1 is migrated to NewDomain using ADMT (security translation first then computer migration)
Trust is removed
SID filtering re-enabled
Post migration, Server1 has the following members in Local Administrators
NewDomain\GlobalGroup1
NewDomain\GlobalGroup1(s-1
NewDomain\DomainLocalGroup
NewDomain\DomainLocalGroup
NewDomain\User1
NewDomain\User1(s-1-5-21-S
I am attaching a screenshot of the server's local administrators group. The SIDs shown are those of the OldDomain.
Basically I think the script is not expecting the OldDomain SID in parentheses of the user or group accounts.
I will build out another test environment to validate all of this step by step again. I am not sure why the members of the local administrators group which originally showed as OldDomain\GroupName would now be listed the way they are with a SID in parenths. I've never seen that before.
Any thoughts?

That's due to the SID history - after all, it is specifically designed so that the clients will identify accounts of the new domain as belonging to the old domain.
Your textual description doesn't match the screen shot - according to the text, every group that has the old domain attached also has a "normal" new domain entry, which is what I'd expect. Is that an error when editing the screen shot?
Anyway, once the migration is fully(!) finished, re-enabling SID filtering is not enough, you have to remove the SID history as well (note: this can not be undone - the SID history can only be set during a migration, or be removed; read the warnings in the article below).
Once SID history is removed, the duplicate entries should disappear.
How To Remove SID History With PowerShell
https://blogs.technet.microsoft.com/ashleymcglone/2011/11/23/how-to-remove-sid-history-with-powershell/
Your textual description doesn't match the screen shot - according to the text, every group that has the old domain attached also has a "normal" new domain entry, which is what I'd expect. Is that an error when editing the screen shot?
Anyway, once the migration is fully(!) finished, re-enabling SID filtering is not enough, you have to remove the SID history as well (note: this can not be undone - the SID history can only be set during a migration, or be removed; read the warnings in the article below).
Once SID history is removed, the duplicate entries should disappear.
How To Remove SID History With PowerShell
https://blogs.technet.microsoft.com/ashleymcglone/2011/11/23/how-to-remove-sid-history-with-powershell/
ASKER
Still looking deeper into this. I appreciate the help and patience.
I should have more info over the weekend.
Thanks!
I should have more info over the weekend.
Thanks!
ASKER
I believe the expert's solution and explanation is perfectly correct. The script provided will work perfectly. Once again I appreciate the input/solution offered!
Dan
Dan
ASKER