Dell SonicWALL VPN Error Message
Hi All,
We currently have a VPN setup between our HQ and data center. More recently, we've noticed that there have been intermittent issues where the VPN drops. Upon review of the logs, this is the error message that I've found... "Remove IPSec SaNode". I've only briefly looked this up; however, I didn't come up with anything solid on how to solve this problem. Has anyone encountered this problem before and so, how did they fix it?
We are currently using a Dell SonicWALL NSA 3600.
Any help on this would be greatly appreciated.
-Anthony
We currently have a VPN setup between our HQ and data center. More recently, we've noticed that there have been intermittent issues where the VPN drops. Upon review of the logs, this is the error message that I've found... "Remove IPSec SaNode". I've only briefly looked this up; however, I didn't come up with anything solid on how to solve this problem. Has anyone encountered this problem before and so, how did they fix it?
We are currently using a Dell SonicWALL NSA 3600.
Any help on this would be greatly appreciated.
-Anthony
ASKER
Hi Diverseit, I read your article and it was extremely informative.
We are running two SonicWALL Fiewalls, one is an NSA3600 and the other is an NSA4600. We have a Site to Site VPN with IKE using a Preshared Secret, no SSL VPN.
We just had the firmware upgraded on both firewalls last night in hope that would help solve the problem; however, we are still encountering the issue today.
I will try to do the packet capture for you and post the results.
-Anthony
We are running two SonicWALL Fiewalls, one is an NSA3600 and the other is an NSA4600. We have a Site to Site VPN with IKE using a Preshared Secret, no SSL VPN.
We just had the firmware upgraded on both firewalls last night in hope that would help solve the problem; however, we are still encountering the issue today.
I will try to do the packet capture for you and post the results.
-Anthony
Can you screenshot or otherwise post your config for the VPN tunnel? Provided that the setups match on both ends, I'm specifically interested in Advanced tab of the VPN Policy (Keep Alive settings) and the VPN > Advanced page settings.
ASKER
Sorry for not getting back to everyone sooner. Yes, I can screenshot the settings. I will send them over now.
I have an underlying feeling it might be an ISP problem.
I have an underlying feeling it might be an ISP problem.
ASKER
Here is the screenshot.
ASKER
Sorry, forgot the file.
NSA3600_SS.png
NSA3600_SS.png
ASKER
Hi, I'm still dealing with this issue without resolve. We've replaced two switches in our office and that has not solved the problem. Can someone recommend some form of software that will allows me to fully identify the routes that an IP address is taking from one site to another site?
ASKER
Hi Bing, it looks like our issue might come down to the ISP itself. I have a quick question, on the currently active VPN tunnels, we have 5 tunnels up as of now between our HQ and our datacenter. For two of the tunnels it says the tunnel was created at 8:18 this morning and the other three were created at 10:05 this morning (Eastern Standard Time). Originally the three tunnels said they were created at 8:18, does the fact that the time is advanced mean that it re-created the VPN tunnels since we have failover from our main Fios line to the Optimum line?
-Anthony
-Anthony
if only one end shows a different establishment time AND the end is behind a VIRTUAL (shared, fault-tolerant) IP, it may sound like that.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Hi Anthony,
Just for clarification, you already said you replaced two switches and it did nothing?
Do you have switches upstream from the Firewalls? Not sure how replacing switches would matter with a S2S VPN connection. If the switches are downstream from the Firewall this wouldn't affect this kind of VPN at all.
Thanks!
Just for clarification, you already said you replaced two switches and it did nothing?
Do you have switches upstream from the Firewalls? Not sure how replacing switches would matter with a S2S VPN connection. If the switches are downstream from the Firewall this wouldn't affect this kind of VPN at all.
Thanks!
ASKER
Hi Diverseit,
We did replace two switches previously; however, those were replaced in the HQ and not the data center. Everyone believed the switches in the data center were good because they were fairly new; however, upon replacing two fairly new switches with brand new ones- all of the our VPN errors disappeared. We also replaced all of the cables that were used to connect between the firewall and those switches as well.
We had Dell working on this with us for about 3 weeks before we tried replacing the two switches in our data center. Once we made the switch, all of our issues went away including all of the VPN error log entries.
-Anthony
We did replace two switches previously; however, those were replaced in the HQ and not the data center. Everyone believed the switches in the data center were good because they were fairly new; however, upon replacing two fairly new switches with brand new ones- all of the our VPN errors disappeared. We also replaced all of the cables that were used to connect between the firewall and those switches as well.
We had Dell working on this with us for about 3 weeks before we tried replacing the two switches in our data center. Once we made the switch, all of our issues went away including all of the VPN error log entries.
-Anthony
They must be Core switches then upstream from your firewall...otherwise it doesn't make sense as downstream switches have no bearing on an S2S VPN.
Thanks!
Thanks!
ASKER
The issue ended up being hardware related, after trying all requested solutions.
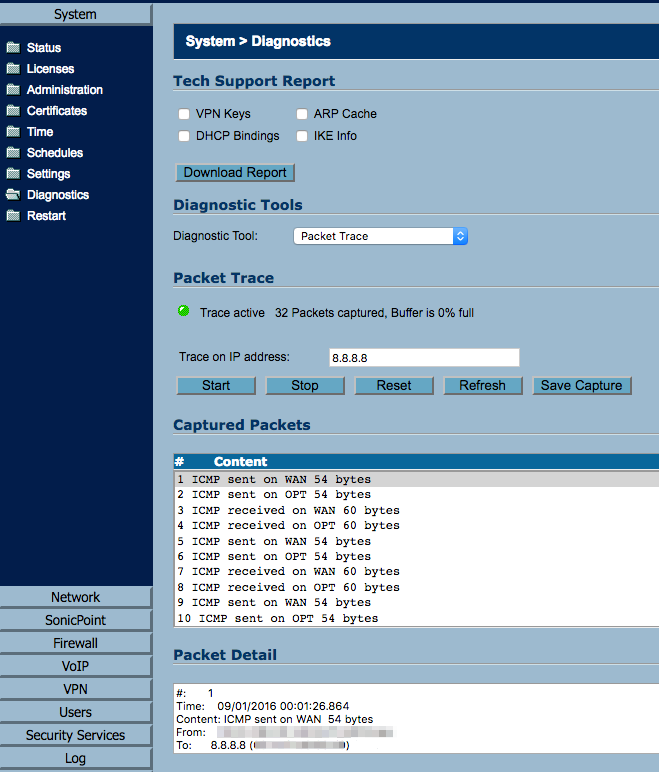
Follow this article I wrote to size your MTU accordingly.
Is this a S2S VPN, SSL-VPN or a GVC VPN? If S2S, what's the make/model of the other firewall...is it possibly a Cisco?
Run a packet capture and post some of the results.
With this error I see it typically being that the IPSec (ESP) packet was dropped by the other end receiving an IPSEC SA delete request. Then the SonicWALL performs accordingly and deletes the request.
Once I understand which type of VPN we are dealing with I'll be able to drill down into this for you in more detail.
Let me know how it goes!