Giving non IT Admin access to Citrix AppCenter (Delivery Services Console) on XenApp 6.5
Client using XenApp 6.5 on Server 2008 R2.
It would like to give a non IT Admin in an outlying office access to the Citrix AppCenter (Delivery Services Console) so they may reset users having issues in that office.
We have followed How to Create Custom Delivery Services Console with Windows Administration Components on XenApp.
However, when the user tries to launch it they get:
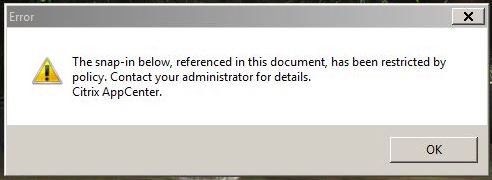 This is down to the XenApp User Policy setting in place:
This is down to the XenApp User Policy setting in place:
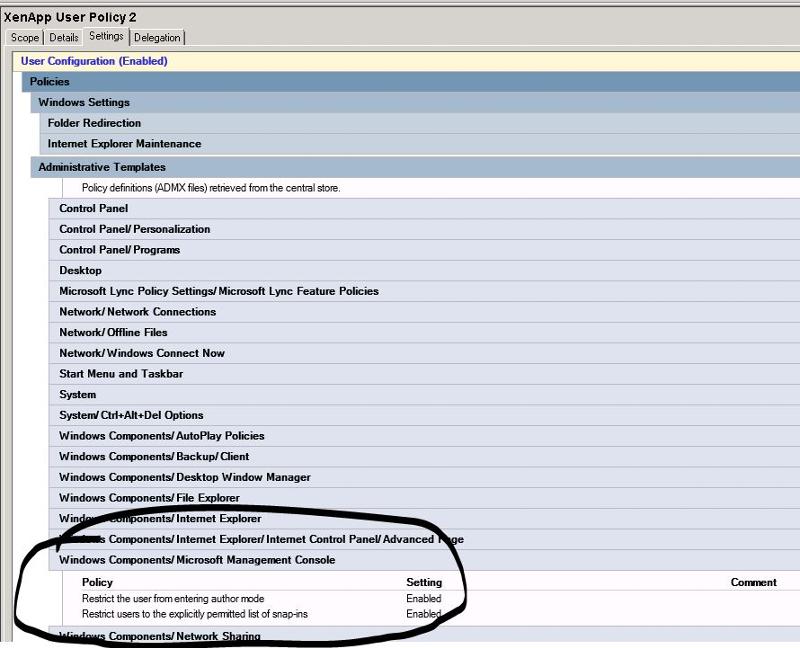
So, I went into that policy setting to enable the snap-in but its not listed. Is it possible to add it into GPO?
Thanks
Mark
It would like to give a non IT Admin in an outlying office access to the Citrix AppCenter (Delivery Services Console) so they may reset users having issues in that office.
We have followed How to Create Custom Delivery Services Console with Windows Administration Components on XenApp.
However, when the user tries to launch it they get:
So, I went into that policy setting to enable the snap-in but its not listed. Is it possible to add it into GPO?
Thanks
Mark
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Hi
thanks for that. I have:
Will test tomorrow and advised how that goes.
Thanks
Mark
thanks for that. I have:
- created a new GPO under the XenApp Servers OU
- imported the new reg collection
- made the Link Order so that the new GPO is above (i.e. lower link number) the existing GPO (which currently blocks the Snap-Ins)
- applied the new GPO to only the user that needs access
Will test tomorrow and advised how that goes.
Thanks
Mark
ASKER
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ah, but which one :-)
The only 'Folder' one I can find is 'Folder Redirection'.
The only 'Folder' one I can find is 'Folder Redirection'.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I had seen that.
So, where do I import this - as in, for what user? Do I import it into a GPO that affects my domain admin account and will then be able to add the snap-in for Citrix AppCenter to the list of allowed Snap-Ins for my XenApp users?