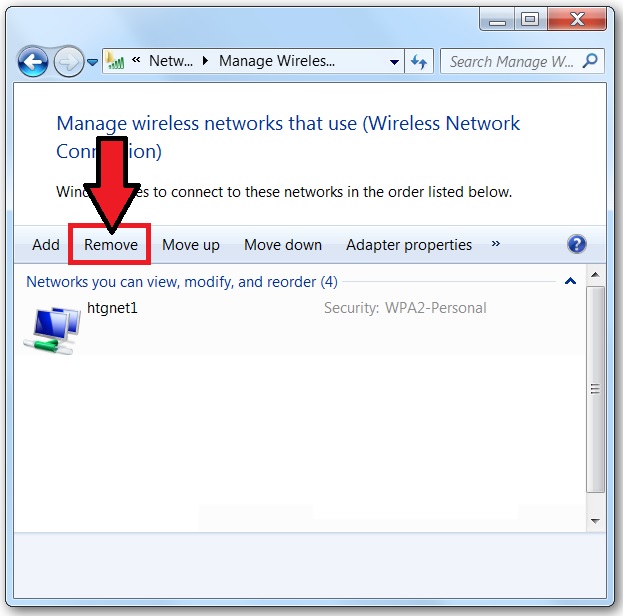
Locking down Wireless Profile
We have 2 wireless networks in our company, one hidden SSID which is the company network and the other one is the Public network for guests (not hidden) I have an employee that constantly keeps removing the wireless profile already set on her computer (the hidden one), after doing so she ends up connecting to our public Wi-Fi (not hidden) and keeps blaming that the computer is the problem. This is the 4th time that is happening and I need to "lock down" the actual profile hidden profile that was initially created so that she can't hit the "Remove" option on top but still be able to add other networks (e.g Starbucks, Hotel Wi-Fi) if she decides to take the work computer home or travel. Does anyone have any idea how to address this? Can GPO fix this or perhaps a PowerShell script can do the trick? I really need to grey out the

ASKER
Testing as we speak... thank you so much!
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Adam any chance to revert back the permission issue in the registry? The implicit deny is there and now I can't revert the change.
Unless you set deny all permission for the user's group (Which is not what I recommended), you should be able to open the folder and set the permission. Otherwise, you'll have to use PSExec or a similar utility to open Regedit in the System context to modify the permissions.
ASKER
Craig you mentioned that GPO would be much easier than Adam's approach doing it through the Registry, can you please elaborate on the steps on how to do so?
thank you,
thank you,
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Thank you, Craig. Now if I use this GPO setting will the user be able to delete the profile or will it lock it down?
Depending on how you configure the GPO you can choose how much control you want the user to have. You can lock it down if you choose.
Best answer chosen
HKLM\SOFTWARE\Microsoft\Wi
and change the permissions on that folder and subfolders that denies delete permission to that user. She'll be able to create new profiles, but will not be able to delete any.