joukiejouk
asked on
A domain user account constantly getting locked out.
Each day, a particular user constantly get locked out of his computer. We always need to unlock his domain account to allow him to log in. I believe he has a session somewhere on another machine, where we need to log him out. This happened after he changed his domain password.
I use a lockout tool to trace the source:
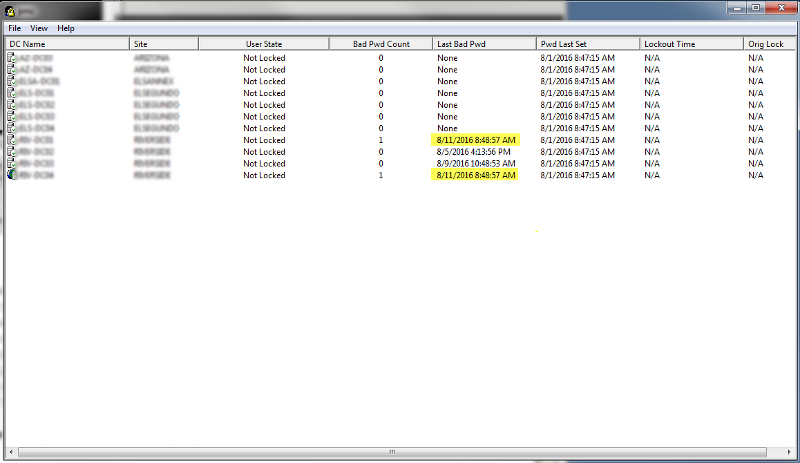
I then check the DC security log, and the client address (highlighted) points to an Exchange server. However, the user would not have access to log into our server. So, I am thinking that maybe he needs to set his new password on a mobile device (cell phone). However, the user mention that he does not use email on his cell. I know the lock out is occuring somewhere within email, but cannot trace exactly where. Anything I can try to resolve this issue?
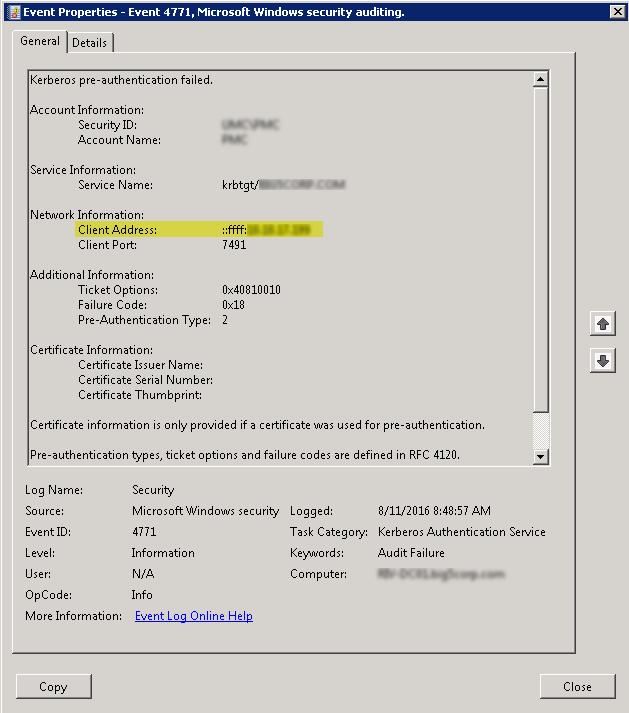
I use a lockout tool to trace the source:

I then check the DC security log, and the client address (highlighted) points to an Exchange server. However, the user would not have access to log into our server. So, I am thinking that maybe he needs to set his new password on a mobile device (cell phone). However, the user mention that he does not use email on his cell. I know the lock out is occuring somewhere within email, but cannot trace exactly where. Anything I can try to resolve this issue?

ASKER
I am not an Exchange guy. I know enough to get by. We use Office365. Anything I can check there? The user does not use any mobile device. I was inform he usually log into Office365 from home (and never signed out), Would that cause the issue? If this is the case, how would I sign him out of Office365? Again. I am not solid in Exchange/Email administration. Our Exchange admin is out on vacation.
The DC logs pointed the unsuccessful authentication from an Exchange server... was it a local server? do you have an hybrid environment with O365 and On-primases exchange servers?
ASKER
Yes, we have a hybrid environment (local Exchange server directing to O365).
cool, so anyway, if the events are coming from the local server. We need to change the exchange connection logs (IIS Logs), and then check from where the connections are coming from.
ASKER
So I checked IIS logs on the local AD SYNC server, and here is what i see for the user (those in bold text has been changed to hide our info).
2016-08-11 11:48:57 10.10.xx.xxx POST /autodiscover/autodiscover
2016-08-11 16:47:10 10.10.xx.xxx POST /Autodiscover/Autodiscover
The 10.10.xx.xxx is our subnet. Not so sure about the 173.51.116.242. Does this help? What should I check next?
2016-08-11 11:48:57 10.10.xx.xxx POST /autodiscover/autodiscover
2016-08-11 16:47:10 10.10.xx.xxx POST /Autodiscover/Autodiscover
The 10.10.xx.xxx is our subnet. Not so sure about the 173.51.116.242. Does this help? What should I check next?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
You can use this freeware: https://www.netwrix.com/account_lockout_examiner.html
To check the locked out account.
To check the locked out account.
ASKER
Sorry, been out for a while (personal matter). The user is still experiencing the lock out. Last thing i tried was the below:
On his workstation go to
Control Panel
User Accounts
on the left Manage your credentials
Remove or edit all credentials linked to outlook "MS.Outlook"
I only edit his password to his newly changed domain password. He is still experiencing lock out issues. I think what I will try next is to remove credentials linked to outlook "MS.Outlook".
On his workstation go to
Control Panel
User Accounts
on the left Manage your credentials
Remove or edit all credentials linked to outlook "MS.Outlook"
I only edit his password to his newly changed domain password. He is still experiencing lock out issues. I think what I will try next is to remove credentials linked to outlook "MS.Outlook".
My original suggestion was to remove the stored credentials next time you open outlook remember to tick 'Remember password'
DirkMare
DirkMare
Have you checked the other software which may cache the credentials like:
iTunes, iPhone and perhaps any other software which uses the AD authentication for Proxy connection ?
iTunes, iPhone and perhaps any other software which uses the AD authentication for Proxy connection ?
ASKER
This user continues to get locked out, and when checking DC logs, the source of the lock out still point to the Sync server for Exchange. We have a hybrid environment with 0365 and On-primases exchange servers.
I tried removing all stored credentials in Credential Manager, and even gone as far as recreating a new Windows profile for the user, but he continues to get locked out. This is annoying.
I tried removing all stored credentials in Credential Manager, and even gone as far as recreating a new Windows profile for the user, but he continues to get locked out. This is annoying.
ASKER
Will recreating the AD account resolve the issue? Is there any other free tool that might help troubleshoot this? The only tool I've used so far is lockoutstatus.exe. Can I check anything in O365 EMC? Logs?
Check on each domain controller for latest security event ID 4740 which can tell you the source compter from where attempt were happening with wrong password and account is getting locked.
Then check all those computers for presense of wrong password such as service, schedule tasks, any application and possible virus infections if any
Then check all those computers for presense of wrong password such as service, schedule tasks, any application and possible virus infections if any
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
Windos 'run as service; stores clear password and makes guesses on password change.
ASKER
Mahesh,
I checked all DC for Event 4740, and it still trace back to our AD Sync server. The user does not have access to RDP or log into that server.
Amit,
I want to try your method, but if I change the SAM account name, what would be impacted? His email is still using the current SAM account name. Will this impact his email access?
I checked all DC for Event 4740, and it still trace back to our AD Sync server. The user does not have access to RDP or log into that server.
Amit,
I want to try your method, but if I change the SAM account name, what would be impacted? His email is still using the current SAM account name. Will this impact his email access?
Renaming will not cause any profile issue. Only thing is change, user now need to login using User1.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
i, ve suffered similar issues and I always
import exchange activesync log files to an excel sheet
order by username and find http status codes 4xx
use a mac vendor lookup web page to get the lockout source hardware vendor
punish the worker whom cell phone was "stolen" last year and his daughter is using today.
im sorry fory bad english
import exchange activesync log files to an excel sheet
order by username and find http status codes 4xx
use a mac vendor lookup web page to get the lockout source hardware vendor
punish the worker whom cell phone was "stolen" last year and his daughter is using today.
im sorry fory bad english
Renaming user sam account name is the only option to resolve this issue.
Don't forget to check user's windows credentials manager.
ASKER
I had no choice but to rename the SAM account, which resolved the user's issue.
I had a similar issue every time a particular user would connect to his Outlook after logging on, his account wouldn’t let him connect to his email. I could unlock his account and then he could connect to his email from then on until the next day. The error messages on the server pointed to the email system as the lockout cause. I renamed “JOHN” to “JOHN1” and the problem stopped. Then I renamed the account back to “JOHN” and it still works.
Does it also mean that he is not using a Tablet (Active Sync), an (Outlook) Client from a PC or MAC?
If it does not appear with information from the user, you will need to check the IIS logs on the Exchange server that corresponds to the connection (Outlook Anywhere, Active Sync, EWS, etc).