To WAN connections and BGP peering on Cisco 3945 Routers
I'm moving into a new datacenter, and they are providing me two WAN links, with each WAN connection I get a separate /29 block, and I also get a /24 public IP block that will be advertised between the two connections. Now I don't have my own ASN. They said this is fine and we will just use a private ASN and do BGP peering, and a default route.
I have two Cisco 3945 routers - one router will connect to WAN link 1, and the other will connect to WAN link 2. See diagram below:
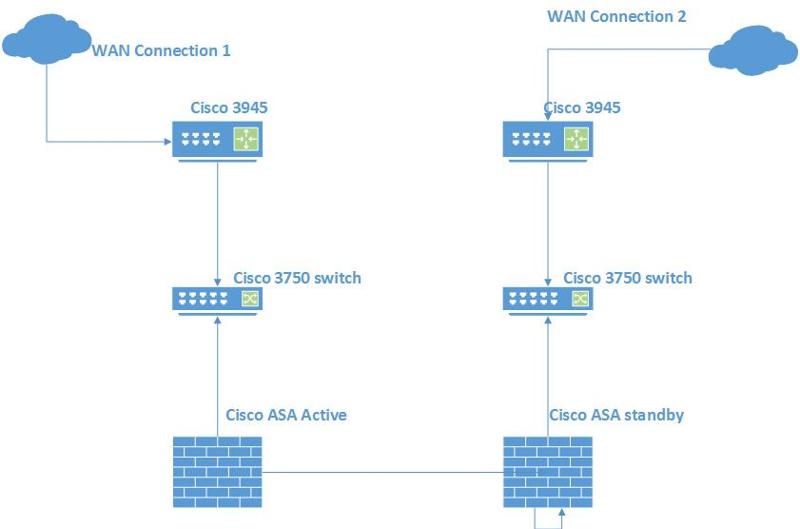
Can someone provide me with a sample configuration of what the BGP configuration on the routers would look like in my scenario. Thanks.
I have two Cisco 3945 routers - one router will connect to WAN link 1, and the other will connect to WAN link 2. See diagram below:

Can someone provide me with a sample configuration of what the BGP configuration on the routers would look like in my scenario. Thanks.
Are you set on this physical connection scheme and is it your plan to use one provider only and failing over to the other provider when there are problems with the first?
Just use OSPF if that's the private circuit between the two.
If you can provide /29 ip's I can write the command for you.
If you can provide /29 ip's I can write the command for you.
ASKER
HI Jan,
Yes, everything will go out the primary, and the secondary is this scenario will only be used when the primary fails.
Yes, everything will go out the primary, and the secondary is this scenario will only be used when the primary fails.
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
This is the best way to ensure failover through all devices.