markgal26
asked on
routing between two sonicwall NSA 2600's connected via patch cable on x2 port
Desperate to get route going between two NSA 2600's (connected via patch cable on x2 port on each). 2 different subnets, NSA 2600 A needs to be able to connect to and see devices on NSA 2600 B. Could I pay someone for an hour of your time? I can provide more details here as well. Thank you
Say SonicWALL A has X0 192.168.1.1/24
Say SonicWALL A has X2 192.168.2.1/24
Say SonicWALL B has X0 192.168.3.1/24
Say SonicWALL B has X2 192.168.2.2/24
On SonicWALL A add a static route
src = any
dst - 192.168.3.0/24
gw = 192.168.2.2
int = X2
On SonicWALL B add a static route
src = any
dst - 192.168.1.0/24
gw = 192.168.2.1
int = X2
Say SonicWALL A has X2 192.168.2.1/24
Say SonicWALL B has X0 192.168.3.1/24
Say SonicWALL B has X2 192.168.2.2/24
On SonicWALL A add a static route
src = any
dst - 192.168.3.0/24
gw = 192.168.2.2
int = X2
On SonicWALL B add a static route
src = any
dst - 192.168.1.0/24
gw = 192.168.2.1
int = X2
ASKER
Thank you for your reply!
I will try this and be back to you soon
I will try this and be back to you soon
ASKER
Ok, this is precisely what I've tried to do. Perhaps my configuration is wrong somewhere along the line? perhaps I created the address object incorrectly? I will come back and post screenshots if that is helpful?
which zone is X2?
did you create proper firewall rules?
e.g. if it's DMZ zone, you will need to add DMZ to LAN firewall rules.
did you create proper firewall rules?
e.g. if it's DMZ zone, you will need to add DMZ to LAN firewall rules.
ASKER
X2 is in a trusted zone along with X0 (lan)
it is not DMZ
I believe the firewall rules are OK as well (also as everything is in trusted zone aren't those rules created or observed automatically?)
it is not DMZ
I believe the firewall rules are OK as well (also as everything is in trusted zone aren't those rules created or observed automatically?)
depends on settings. I would check the firewall rules just in case.
screenshots would help.
screenshots would help.
ASKER
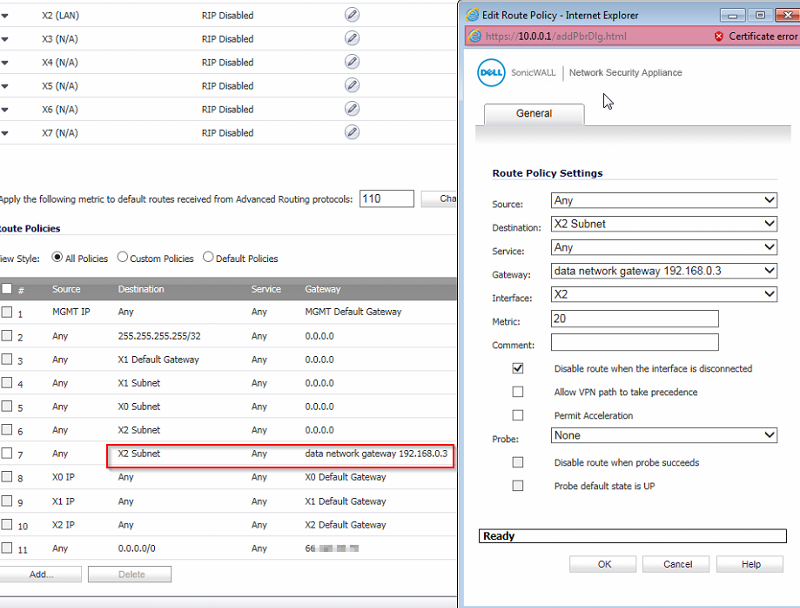
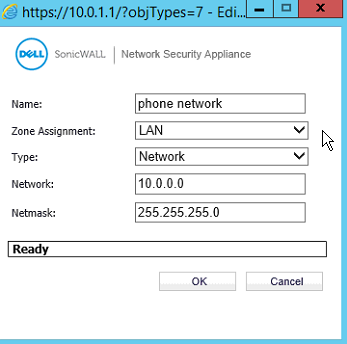
Ok,
First I'll upload "phone network" (one NSA 2600) then "data network" (the other NSA 2600)
in your example lets replace with:
phone network: 10.0.0.x / x2 interface ip: 192.168.0.2
data network: 10.0.1.x / x2 interface IP: 192.168.0.3
ideally the data network needs to see devices/servers on the phone network (other way around not necesssary)
right now each network can ping the firewall of the other network, but thats it..
phone network firewall
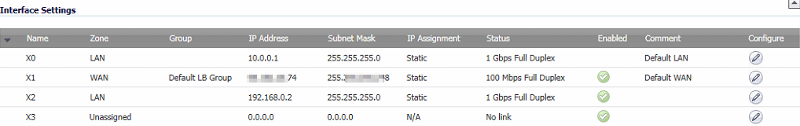
-----------------------

-------------------------
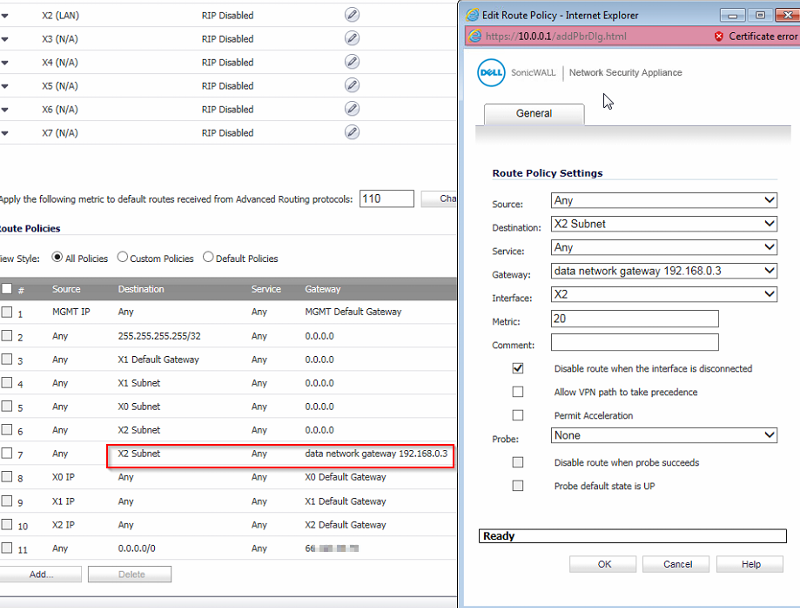
--------------------------
data network firewall
--------------------------
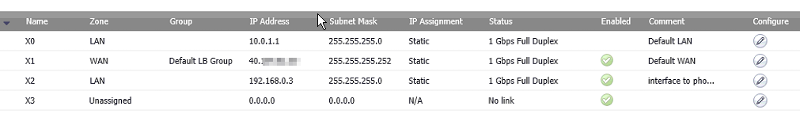
--------------------------
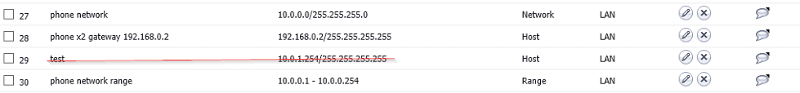
--------------------------
First I'll upload "phone network" (one NSA 2600) then "data network" (the other NSA 2600)
in your example lets replace with:
phone network: 10.0.0.x / x2 interface ip: 192.168.0.2
data network: 10.0.1.x / x2 interface IP: 192.168.0.3
ideally the data network needs to see devices/servers on the phone network (other way around not necesssary)
right now each network can ping the firewall of the other network, but thats it..
phone network firewall

-----------------------

-------------------------

--------------------------
data network firewall
--------------------------

--------------------------

--------------------------

SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I believe we are good! looks like its working so far. Can't thank you enough :-)
what can I do to say thanks? don't want to break any rules can you send an email address? or is that no no..
what can I do to say thanks? don't want to break any rules can you send an email address? or is that no no..
if the case is solved, please mark the answer as solving your case :)
ASKER
jspoor is awesome - thank you!

View example configurations and the SonicWALL webui and features on http://livedemo.sonicwall.com or http://ngfw-demo.com
Multiply the effectiveness of your APT Sandbox, stop unknown and zero-day attacks at the gateway. See a demo on http://apt-demo.com or http://atp.demo.com
You can also view the Next-Generation Firewalls via
http://next-generation-firewall.com or http://next-generation-firewall-demo.com