astrix2
asked on
Exists a Flash Exe created with Zinc Decompiler?
Exists a Flash Exe created with Zinc Decompiler?
I test to decompile a flash exe created with Zinc 2.5 and not have result, for the moment, VB Decompiler Pro:
https://www.vb-decompiler.org/
He says that it may be compiled with Delphi...
I test with some delphi decompilers and says not are Delphi...
My intention is know if is secure - totally is impossible - a Flash Exe compiled with Zinc, my intention not is decompile programs, is for secure my code...
Any know a Flash Exe compiled with Zinc Decompiler?
Thanks in advance...
I test to decompile a flash exe created with Zinc 2.5 and not have result, for the moment, VB Decompiler Pro:
https://www.vb-decompiler.org/
He says that it may be compiled with Delphi...
I test with some delphi decompilers and says not are Delphi...
My intention is know if is secure - totally is impossible - a Flash Exe compiled with Zinc, my intention not is decompile programs, is for secure my code...
Any know a Flash Exe compiled with Zinc Decompiler?
Thanks in advance...
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
I download the program you write:
http://www.novirusthanks.org/products/upx-easy-gui/
But not see the window of your images, wath program are the program of the images???
For my the most important are be difficult to extract the flash swf file (are the hearth of the program and that swf are encrypted with SWFEncrypt -...
The delphi code are make by zinc, is possible the swf are in the resources...? I think...
Thanks...
http://www.novirusthanks.org/products/upx-easy-gui/
But not see the window of your images, wath program are the program of the images???
For my the most important are be difficult to extract the flash swf file (are the hearth of the program and that swf are encrypted with SWFEncrypt -...
The delphi code are make by zinc, is possible the swf are in the resources...? I think...
Thanks...
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ok, thanks, I have a Resource Hacker, but not know the other:
http://appnee.com/exescope/
At now I have...
Sinisa Vuk write:
/////////////////
I don't get - what you want to accomplished?
/////////////////
Well, I want to know if the flash exe's created with mdmd zinc are quite secure, not easy for decompile and retrieve the flash swf into...
Appear to be are almost quite secure, the total secure are impossible, but in VB are complete decompilers, VB Decompiler Pro let all the code almost in some seconds, not secure, flash exe make by mdm zoinc appear to be almost secure...
Sorry for my bad English...
http://appnee.com/exescope/
At now I have...
Sinisa Vuk write:
/////////////////
I don't get - what you want to accomplished?
/////////////////
Well, I want to know if the flash exe's created with mdmd zinc are quite secure, not easy for decompile and retrieve the flash swf into...
Appear to be are almost quite secure, the total secure are impossible, but in VB are complete decompilers, VB Decompiler Pro let all the code almost in some seconds, not secure, flash exe make by mdm zoinc appear to be almost secure...
Sorry for my bad English...
ASKER
Another thing, I not understand the fear PANIC in software companies with Flash...
In my opinion Flash are maybe the more better language make, easy, fast to program, much better quality in visual effects than html5, many more, and animations, are wonderfull, I know programa in C, VB, Flash, Javascript, but flash for my is the better language make...
But there is a complete attempt to eliminate!!!
I think it's because it is too good and the USA Software Companies not like that any person make a superprogram in graphic look with minimal time and code...
Well, Zinc 4.0 at now are free, and write in your web that in near time disappear:
www.multidmedia.com
The help web pages is possible dissapear, and I make today a complete copy - download pages with inet and VB6 - of all the Help of Zinc 4.0:
Thanks for your aid...!!! At all...
Another thing, if any manages to get the swf into the exe - www.astrodreams.com/downloads/Zodiac4.0TimeZones.rar -, please tell me in this post or in my email astrix@zodiacwin.com
Thanks...
In my opinion Flash are maybe the more better language make, easy, fast to program, much better quality in visual effects than html5, many more, and animations, are wonderfull, I know programa in C, VB, Flash, Javascript, but flash for my is the better language make...
But there is a complete attempt to eliminate!!!
I think it's because it is too good and the USA Software Companies not like that any person make a superprogram in graphic look with minimal time and code...
Well, Zinc 4.0 at now are free, and write in your web that in near time disappear:
www.multidmedia.com
This build can be used for any legacy projects you may need to support now or in the future
but will only remain available for a short time.
The help web pages is possible dissapear, and I make today a complete copy - download pages with inet and VB6 - of all the Help of Zinc 4.0:
//////////////////////////////////// ////////// //////
And here a Copy of All LiveDocs Archives of Zinc 4.0 - Script 4.0 API, Help Files and Command SDK -:
http://depositfiles.com/files/47ag9bp1g
Not are orderd and fault organize the Links, but how in Little Time is Possible Dissapear, here are the total htmls in:
http://www.multidmedia.com/support/livedocs/zinc/4.0/
A pity that excellent software like Flash and Zinc, these Big Software Companies - dirty game - wanted to eliminate because are too good ...
I hope someone will be useful ... I not understand why zinc have not made a chm help well ... I do not understand ...
//////////////////////////////////// ////////// //////
Thanks for your aid...!!! At all...
Another thing, if any manages to get the swf into the exe - www.astrodreams.com/downloads/Zodiac4.0TimeZones.rar -, please tell me in this post or in my email astrix@zodiacwin.com
Thanks...
You said:
manages to get the swf into the exe- but yout think get swf out of exe, I guess?
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
Ok, I check some exe's with the exescope and UPX Easy Gui, and, for example, HelpSmith:
http://www.helpsmith.com
The exe do this in exeScope and UPX Wasy GUI:
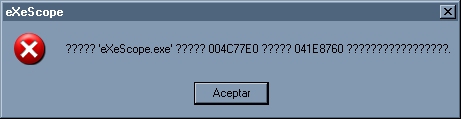
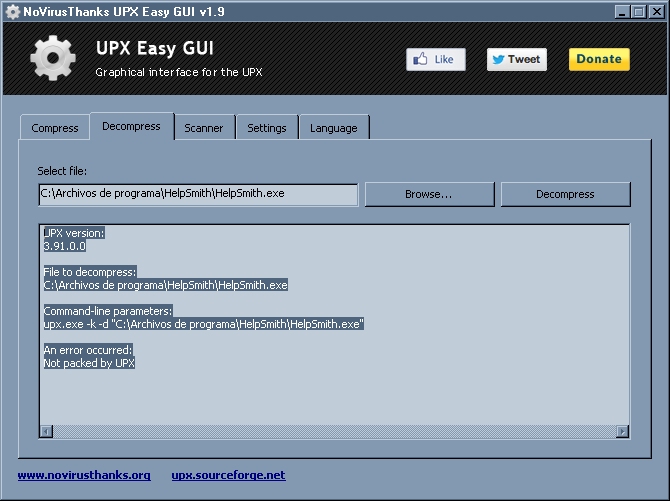
Appear to be are hard protect...
How to protect - totally is impossible - the maximum possible?
HelpSmith how protect the Exe, any know? At least a little as they have done...
Thanks another time, this topics of protect, are very interesting I believe... VB6 at begon, how have Native code Compilation, appear are good protection, but not are native if VB Decompiler extract all and let a Project VBP almost complete...
Not are a program that convert to pure machine code an exe?
Because in pure machine code - assembly at least, not know if assembler are the same of pure machine code - the variables and many are only 0 and 1, and yes, is possible know the code, but let many abtract and are a good protection, is difficult know how work the code if are in assembler or pure machine code, I believe...
Good day... Thanks for your answers...
http://www.helpsmith.com
The exe do this in exeScope and UPX Wasy GUI:


Appear to be are hard protect...
How to protect - totally is impossible - the maximum possible?
HelpSmith how protect the Exe, any know? At least a little as they have done...
Thanks another time, this topics of protect, are very interesting I believe... VB6 at begon, how have Native code Compilation, appear are good protection, but not are native if VB Decompiler extract all and let a Project VBP almost complete...
Not are a program that convert to pure machine code an exe?
Because in pure machine code - assembly at least, not know if assembler are the same of pure machine code - the variables and many are only 0 and 1, and yes, is possible know the code, but let many abtract and are a good protection, is difficult know how work the code if are in assembler or pure machine code, I believe...
Good day... Thanks for your answers...
ASKER
Sinisa Vuk write:
Yes, I want to know if are easy extract the swf from the exe created with Zinc 2.5 in the exe of the rar:
www.astrodreams.com/downloads/Zodiac4.0TimeZones.rar
Well, this appear to be strange, but I in the next months, 2 aprox, I believe - it seems crazy, yes - I demostrate that the Planets have Influence...
The actual world of Astrology are many fools and storytellers, but are a real Astrology, Scientific, that do VERIFIED RESULTS, for example, Andre Barbault - https://fr.wikipedia.org/wiki/Andr%C3%A9_Barbault - write in 1955 - and after i many books and TV interviews, articles, many many -, but in 1955 write this:
Original Book of 1955:
https://www.amazon.com/s/ref=nb_sb_noss?url=search-alias%3Daps&field-keywords=barbault+defense&rh=i%3Aaps%2Ck%3Abarbault+defense
Write - google translation -:
In 1973 be more specific and write that the change are between August to December of 1989, the Berlin Walk falls the 9 November 1989...
And are many evidences, I and others , but I predict in an article in 2001 that between 2008 to 2018 aprox are a Depression how the 1929 to 1935-36, write in Spanish, sorry:
http://www.astrodreams.com/mercurio3/img010b.jpg
http://www.astrodreams.com/mercurio3/img019b.jpg
And well, I know how to demostrate the Planets have Influence, but I not like the code are easy to know how is make... This is the reason for I search for many protection...
But I have a good protection in begin, with Arduino hardware and Relays the software that calculate important moments of the persons - this is the demostration, a software that hace succes predict pass moments in the life of the persons, not is make any how this - are in a Pc isolated - not wifi, not net -, and other Pc with wifi, when receive a purchase, save in a pendrive conected to the Arduino Hardware the data for calculating, and after with Arduino and Relays, disconect the PenDrive of the Pc with Wifi, and connect the PenDrive to the Pc isolated, the isolated Pc have another Arduino and Relays Hardware, detect the pendrive with data for calculations are conected, make the calculations, and do a result, save in second pendrive and with the 2 Arduino Hardware in the isolated Pc disconect the 2 pendrive and connect the 2 pendrive to the Pc with Wifi...
The Pc with Wifi after send an archive to the client with the results, the software that have the client not calculate...
With this, the software that make the calculatons are isolated, and is a good protection, but also I want to protect the main software send to the client...
Although it sounds crazy, if the planets do influence, are the more important thing in the life of the persons, in our life, and I not like storytellers take advantage and copy the code that proves...
Many WARNING with 2020 last Months, verify, are hard and complex - this is completely sure, the details are more difficult, but the general, last months of 2020, HARD, totally 120% sure -, is possible many conflicts, and Europe and USA is possible - Andre Barbault says this - lost the predominance that have from the 15 Century...
Good day, and, another time, sorry for my not very good English...
You said:
manages to get the swf into the exe
- but yout think get swf out of exe, I guess?
Yes, I want to know if are easy extract the swf from the exe created with Zinc 2.5 in the exe of the rar:
www.astrodreams.com/downloads/Zodiac4.0TimeZones.rar
Well, this appear to be strange, but I in the next months, 2 aprox, I believe - it seems crazy, yes - I demostrate that the Planets have Influence...
The actual world of Astrology are many fools and storytellers, but are a real Astrology, Scientific, that do VERIFIED RESULTS, for example, Andre Barbault - https://fr.wikipedia.org/wiki/Andr%C3%A9_Barbault - write in 1955 - and after i many books and TV interviews, articles, many many -, but in 1955 write this:
Original Book of 1955:
https://www.amazon.com/s/ref=nb_sb_noss?url=search-alias%3Daps&field-keywords=barbault+defense&rh=i%3Aaps%2Ck%3Abarbault+defense
Write - google translation -:
With the 1952-53 conjunction dies Stalin and the U.S.S.R. is in full metamorphosis, begins a new cycle that leads to 1989 capital change.
In 1973 be more specific and write that the change are between August to December of 1989, the Berlin Walk falls the 9 November 1989...
And are many evidences, I and others , but I predict in an article in 2001 that between 2008 to 2018 aprox are a Depression how the 1929 to 1935-36, write in Spanish, sorry:
http://www.astrodreams.com/mercurio3/img010b.jpg
http://www.astrodreams.com/mercurio3/img019b.jpg
And well, I know how to demostrate the Planets have Influence, but I not like the code are easy to know how is make... This is the reason for I search for many protection...
But I have a good protection in begin, with Arduino hardware and Relays the software that calculate important moments of the persons - this is the demostration, a software that hace succes predict pass moments in the life of the persons, not is make any how this - are in a Pc isolated - not wifi, not net -, and other Pc with wifi, when receive a purchase, save in a pendrive conected to the Arduino Hardware the data for calculating, and after with Arduino and Relays, disconect the PenDrive of the Pc with Wifi, and connect the PenDrive to the Pc isolated, the isolated Pc have another Arduino and Relays Hardware, detect the pendrive with data for calculations are conected, make the calculations, and do a result, save in second pendrive and with the 2 Arduino Hardware in the isolated Pc disconect the 2 pendrive and connect the 2 pendrive to the Pc with Wifi...
The Pc with Wifi after send an archive to the client with the results, the software that have the client not calculate...
With this, the software that make the calculatons are isolated, and is a good protection, but also I want to protect the main software send to the client...
Although it sounds crazy, if the planets do influence, are the more important thing in the life of the persons, in our life, and I not like storytellers take advantage and copy the code that proves...
Many WARNING with 2020 last Months, verify, are hard and complex - this is completely sure, the details are more difficult, but the general, last months of 2020, HARD, totally 120% sure -, is possible many conflicts, and Europe and USA is possible - Andre Barbault says this - lost the predominance that have from the 15 Century...
Good day, and, another time, sorry for my not very good English...
Do you have any further query - pardon me as I am kinda of lost in your post.
The principle of protection of exe has to do with that extra layer (like how UPX is done but probably is to use other encryptor or packer as compared to UPX packer) on top of the Zinc MDM doing which is that packed binary is unpacked then I will say it may be possible for SWF extraction from Zinc MDM compiled exe though I have not delve deeper or so far done to my best knowledge.
The principle of protection of exe has to do with that extra layer (like how UPX is done but probably is to use other encryptor or packer as compared to UPX packer) on top of the Zinc MDM doing which is that packed binary is unpacked then I will say it may be possible for SWF extraction from Zinc MDM compiled exe though I have not delve deeper or so far done to my best knowledge.
I suggest upx scrambler before... Get another upx gui with scrambler included... Apply it on upx compressed exe.
UPX is common so if there is an unpacker, it is expected.
ASKER
Thanks Sinisa for the other UPX...
btan write:
///////////////////
UPX is common so if there is an unpacker, it is expected.
///////////////////
Yes, I search - or similar - for a program that convert to assembly an exe, pack are know and not do any real protection...
Is possible exists, HelpSmith appear to be have good protection... But how??? That's is the question...
Thanks...
btan write:
///////////////////
UPX is common so if there is an unpacker, it is expected.
///////////////////
Yes, I search - or similar - for a program that convert to assembly an exe, pack are know and not do any real protection...
Is possible exists, HelpSmith appear to be have good protection... But how??? That's is the question...
Thanks...
ASKER CERTIFIED SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
btan, Good programs, PELock, appear to be, is very good for protect, only have a problem, very expensive!!! 499 US$... Many...
Multiextractor I not know why, but not do prices, It seems as if they had abandoned the project???
http://www.multiextractor.com/license.html
Not appear nothing, only the email at bottom of the page...
???
At least in my firefox page appears blank... Only header and bottom... rest, white...
Multiextractor I not know why, but not do prices, It seems as if they had abandoned the project???
http://www.multiextractor.com/license.html
Not appear nothing, only the email at bottom of the page...
???
At least in my firefox page appears blank... Only header and bottom... rest, white...
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
ASKER
The problem with multiextractor are my firefox, not know why but not appear the prices, in IExplorer appear...
The price of multiextractor are reasonable...
I test your other links... Very thanks for your information, are very good, You saved me a lot of time searching... Many thanks...
The price of multiextractor are reasonable...
I test your other links... Very thanks for your information, are very good, You saved me a lot of time searching... Many thanks...
ASKER
Very interesting btan the page of PELock about other programs...
Another question, php in web is almost secure???
The owner of the server, evident, can access to the archives, and is sure microsoft and others big companies know how to download the php files, but for the rest are almost secure not?
Anyway, the more secure system are the idea I have, the software that calculate in an isolated pc, managing with arduinos hardware conecting desconneting between 2 pc's 2 pendrives, and only do results, not the functions of calculations... In the case of my software...
Another question, php in web is almost secure???
The owner of the server, evident, can access to the archives, and is sure microsoft and others big companies know how to download the php files, but for the rest are almost secure not?
Anyway, the more secure system are the idea I have, the software that calculate in an isolated pc, managing with arduinos hardware conecting desconneting between 2 pc's 2 pendrives, and only do results, not the functions of calculations... In the case of my software...
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
SOLUTION
membership
This solution is only available to members.
To access this solution, you must be a member of Experts Exchange.
I never thought PELock was so popular, I'm using it to protect my AutoIt bots, it's pretty handy utility to apply licensing to any application even without touching its source codes and works like a charm, what more can I say, great product that does the job right, highly customizable too.
ASKER
Well, very, sincere, very thanks for all the answers, in this question many comments are very usseful for my, many thanks at all for all the info, sincerely...
I not like close the topic, is possible in near time another person have some "?"...
My best wishes at all, very good answers...!!!
I not know if is possible for my do points to some persons that do excellent answers... If are any method for do points, please write how... And, another time, many many many thanks for the VERY GOOD info...
I not like close the topic, is possible in near time another person have some "?"...
My best wishes at all, very good answers...!!!
I not know if is possible for my do points to some persons that do excellent answers... If are any method for do points, please write how... And, another time, many many many thanks for the VERY GOOD info...
ASKER
BSpecialist write:
///////////////////
I never thought PELock was so popular, I'm using it to protect my AutoIt bots, it's pretty handy utility to apply licensing to any application even without touching its source codes and works like a charm, what more can I say, great product that does the job right, highly customizable too.
///////////////////
Too bad it is so expensive, will be good PELock may have an option to charge for protecting one program, for example, 10 US$ for only protect one program ... Apart from the general option to purchase whole life at 999 US$... Is possible with this service of protect one programa earn many money, because pay 999US$ inmediately, are difficult... In global world the little prices have many success... Envato - www.envato.com - for example It was and is a big deal, I bought aprox 6000 euros in the last years in envato, but because as the codes are 10-20US$, if you need something at some time, pay easily 10 to 20 US$ ... 999US$ in one time, is difficult pay...
Overalls because at the beginning is possible one programmer not know if the program will be successful, but, if in the begining is possible protect by little price, and after, if the program have success, after is possible pay the 999US$ for future updates... I think PELock will be good do this service for beginners programmers...
I not test, but PECompact are also good, but I believe have a fail, do 30 days test-trial, but if any open a virtual machine, install and protect any exe, any person is possible have infinite 30 days test-trial... PELock show a Windows that the protection are made with a demo version of PELock, PEcompact not do this message, but I not test if after 30 days the protection of PECompact not work... But if a program protected with PECompact demo 30 days trial work infinite, I think is a big error of the programmer of PECompact not show any window that inform the program is protected with a trial-demo version...
///////////////////
I never thought PELock was so popular, I'm using it to protect my AutoIt bots, it's pretty handy utility to apply licensing to any application even without touching its source codes and works like a charm, what more can I say, great product that does the job right, highly customizable too.
///////////////////
Too bad it is so expensive, will be good PELock may have an option to charge for protecting one program, for example, 10 US$ for only protect one program ... Apart from the general option to purchase whole life at 999 US$... Is possible with this service of protect one programa earn many money, because pay 999US$ inmediately, are difficult... In global world the little prices have many success... Envato - www.envato.com - for example It was and is a big deal, I bought aprox 6000 euros in the last years in envato, but because as the codes are 10-20US$, if you need something at some time, pay easily 10 to 20 US$ ... 999US$ in one time, is difficult pay...
Overalls because at the beginning is possible one programmer not know if the program will be successful, but, if in the begining is possible protect by little price, and after, if the program have success, after is possible pay the 999US$ for future updates... I think PELock will be good do this service for beginners programmers...
I not test, but PECompact are also good, but I believe have a fail, do 30 days test-trial, but if any open a virtual machine, install and protect any exe, any person is possible have infinite 30 days test-trial... PELock show a Windows that the protection are made with a demo version of PELock, PEcompact not do this message, but I not test if after 30 days the protection of PECompact not work... But if a program protected with PECompact demo 30 days trial work infinite, I think is a big error of the programmer of PECompact not show any window that inform the program is protected with a trial-demo version...
You can still add comments and click on the "object" and then follow up as desired to award points accordingly.
For PELock demo version, there are the following limitation you should note especially on the expiry of the protected application
For PELock demo version, there are the following limitation you should note especially on the expiry of the protected application
Protected applications displays information message box at the startup
Protected applications expires in 7 days since the date of protection
Project files opening and saving is disabled
Many of the protection features are unavailable
Following SDK encryption macros are disabled:
CRYPT_START
CLEAR_START
FILE_CRYPT_START
UNPROTECTED_START
UNPROTECTED_START
Sample generator is unavailable
PECompact is technically a Windows executable compressor only, but plug-ins are available for it that offer protection against reverse-engineering (some sold separately by third-parties). Its PE+ (PE64) support is still pending as it requires a massive rewrite of the loader (decompression stub).
It is primarily a compressor compared to PELock. It do take note not to compress the
- icons needed for use by the shell so your shell view icons don’t disappear.
- version and manifest information
- any other type of resource you desire to be kept uncompressed.
It is primarily a compressor compared to PELock. It do take note not to compress the
- icons needed for use by the shell so your shell view icons don’t disappear.
- version and manifest information
- any other type of resource you desire to be kept uncompressed.
ASKER
Yes, I know, PELock it's very good, but need to have intermediate prices, with 999US$ have all life for protect - nothing is 100% protected in computers, is impossible the 100%, but many, ok - all programs any person like in all life...
But are very expensive, if do other options for only one program, I think is much better for PELock Bussiness...
I not pay 6.000 euros to Envato in the last years if have big prices, but with little prices, are 6.000 aprox I pay in the last years... I not believe purchase PELock at 999US$, one reason is why I have my proper more secure system of protection, I am making a program that DEMOSTRATE the Real Astrology - 99.99% of those who say Astrology are storytellers or hallucinated, but are a real astrology and I know how to demostrate, If someone laughs, I leave what he said all his life the greatest banker of all time https://www.google.es/?gws_rd=ssl#newwindow=1&q=%27J.+P.+Morgan%27+Astrology “Millionaires don't use Astrology, billionaires do.” -, but the program I sell not have the functions that calculate into it, I make a database that have the results of functions calculations, and is in my proper server in my house with optical fiber, the more better possible protection, and the program that make the calculations not are conected to wifi, net or any thing, is complete isolated and with arduinos I connect-disconnet pendrives that comunicate with the main pc that do the result to the clients...
But if PELock gave the option to protect one single program for a reasonable price, I would use in any of my programs - or in many of my programs -, but 999US$? No way ...
In my opinion programmers need to understand that big prices are for the world before 2004 aprox, at now the computers not are a thing special, Now is an appliance, and the high prices not are good marketing in a global world with minimum one Pc or Mobile in all the Houses...
But this is the problem of the PELock owner...
But are very expensive, if do other options for only one program, I think is much better for PELock Bussiness...
I not pay 6.000 euros to Envato in the last years if have big prices, but with little prices, are 6.000 aprox I pay in the last years... I not believe purchase PELock at 999US$, one reason is why I have my proper more secure system of protection, I am making a program that DEMOSTRATE the Real Astrology - 99.99% of those who say Astrology are storytellers or hallucinated, but are a real astrology and I know how to demostrate, If someone laughs, I leave what he said all his life the greatest banker of all time https://www.google.es/?gws_rd=ssl#newwindow=1&q=%27J.+P.+Morgan%27+Astrology “Millionaires don't use Astrology, billionaires do.” -, but the program I sell not have the functions that calculate into it, I make a database that have the results of functions calculations, and is in my proper server in my house with optical fiber, the more better possible protection, and the program that make the calculations not are conected to wifi, net or any thing, is complete isolated and with arduinos I connect-disconnet pendrives that comunicate with the main pc that do the result to the clients...
But if PELock gave the option to protect one single program for a reasonable price, I would use in any of my programs - or in many of my programs -, but 999US$? No way ...
In my opinion programmers need to understand that big prices are for the world before 2004 aprox, at now the computers not are a thing special, Now is an appliance, and the high prices not are good marketing in a global world with minimum one Pc or Mobile in all the Houses...
But this is the problem of the PELock owner...
Strike a balanced in your investment and the quality that you need then.
ASKER
Strike a balanced in your investment and the quality that you need then.
///////////
Because I have the more better protection possible, my server in my proper house and the pc that have the real software functions calculations, isolated and only communicate with the main server with Arduinos and Relays with Pendrives, because this, I not need PELock in reality, only comment that I think have poor marketing actions in a global world... And, if have middle options is possible, in any of my programs I use, for confort...
My Phater was professor of marketing in one of the most recognized marketing companies in Spain, almost all medium and large businesses in Spain in the 1960-80's received courses of my phater, in 1979 Venezuela created a ministry called "Ministry for the Development of Intelligence", and the Minister go to Spain to Search my Phater, My father's brother was Director of Sales of the American Express Card for the whole Northern Spain, I believe I know any about Marketing and Sell...
PELock need to do middle options, but if the owner like, is your bussiness and is your problem and is your decision...
But I think is possible the author of PELock wants not have many programs protected with your program, because, if popularized, it would be easier that some hacker hack...
///////////
Because I have the more better protection possible, my server in my proper house and the pc that have the real software functions calculations, isolated and only communicate with the main server with Arduinos and Relays with Pendrives, because this, I not need PELock in reality, only comment that I think have poor marketing actions in a global world... And, if have middle options is possible, in any of my programs I use, for confort...
My Phater was professor of marketing in one of the most recognized marketing companies in Spain, almost all medium and large businesses in Spain in the 1960-80's received courses of my phater, in 1979 Venezuela created a ministry called "Ministry for the Development of Intelligence", and the Minister go to Spain to Search my Phater, My father's brother was Director of Sales of the American Express Card for the whole Northern Spain, I believe I know any about Marketing and Sell...
PELock need to do middle options, but if the owner like, is your bussiness and is your problem and is your decision...
But I think is possible the author of PELock wants not have many programs protected with your program, because, if popularized, it would be easier that some hacker hack...
Thanks for sharing though I am trying to understand your writing to appreciate your viewpoint and gist of sharing. The product feedback cam be helpful to the support team if you have any. Hope we have closed and conclude this question as required.
ASKER
Yes, my english is not very good, I study French in the School, an error in Spain, big error of the Dictatorship of General Franco, but I think more or less understood me...
I not think it's postive close messages, can arise ideas in some time, it is one of the reasons why this month has been the last I pay, I do not like that matters are closed and can not be eventually bring new ideas or comments... Is little creative I think...
But, Good day btan, and thank you very much...
I not think it's postive close messages, can arise ideas in some time, it is one of the reasons why this month has been the last I pay, I do not like that matters are closed and can not be eventually bring new ideas or comments... Is little creative I think...
But, Good day btan, and thank you very much...
You can still share comment even after closure or create another new questions. Cheers and thanks for sharing your thoughts.
As per advised with option to diagnose and unlock cum protect the application
ASKER
Well, Trid do this:
Open in new window
The rest can not decom[ile nothing, is a good notice...I not know the free swf decompiler:
https://www.free-decompiler.com/flash/features/
Thanks...
I attempt to decompile, but nothing...
An exe make with Zinc 2.5 are here, for if any want to check if get decompile:
www.astrodreams.com/downloads/Zodiac4.0TimeZones.rar
Is make by me, is original... And do all rights to attempt to decompile...
Thanks btan and Geert Gruwez...
The exe not need external dll's, is complete, only have secundary swf's for look of the program, but the main swf are totally into the exe...
Good day...